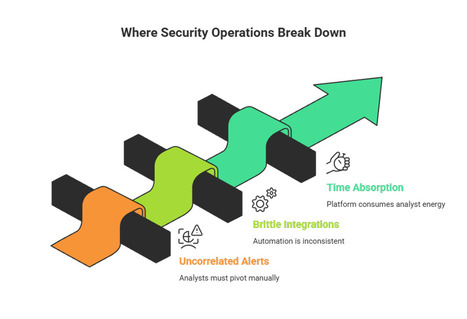
Here’s why we need to apply zero-trust principles to our workloads, not just our users.

|
Scooped by
JC Gaillard
onto Cybersecurity Leadership June 23, 2025 12:57 AM
|





 Your new post is loading...
Your new post is loading...