Nine years ago, I published a cyber-thriller, "Babel Minute Zero". The story was simple: an authoritarian country facing economic crunch and the risk of political destabilization would launch cyber-attacks against the US in order to deflect attention and increase nationalist support. Today, I realize I've made two major mistakes when I wrote "Babel Minute Zero".…
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
Over 100 million cars sold by Volkswagen since 1995 are susceptible to hacking due to security flaws in keyless entry systems, researchers have revealed. Two UK-based computer experts at the University of Birmingham, Flavio Garcia and David Oswald, have published a paper showing how they were able to clone VW keyless systems by intercepting signals when drivers press their fobs to get into their vehicles. "Major manufacturers have used insecure schemes over more than 20 years," the research paper asserts. Vehicles that are at risk to the attack include most Audi, VW, Seat and Skoda models sold since the mid-90s and roughly 100 million VW Group vehicles. The landmark paper, which also included input from German engineering firm Kasper & Oswald, revealed two main vulnerabilities. The first could give hackers the ability to remotely break into nearly every car VW has sold since 2000. The second impacts 'millions' more vehicles such as Ford, Peugeot, Citroen and Ford. As outlined in the paper, both attacks rely on "widely available" hardware that costs as little as $40 (£31) which can then be used to intercept and clone signals from victim's car fobs. Of course, at this point, cryptography becomes involved, but the experts found ways to crack that too. "We discovered that the RKE [remote keyless entry] systems of the majority of VW Group vehicles have been secured with only a few cryptographic keys that have been used worldwide over a period of almost 20 years," the researchers wrote.
Philippe J DEWOST's insight:
Beyond a bad year for Das Auto , this new episode in #carhacking shows that beyond a CDO, carmakers need real tech CTOs , and need them rather now.
What occurred with the recently disclosed breach of the Democratic National Committee servers, and the dumping of stolen data on a WordPress site, is more than an act of cyber espionage or harmless mischief. It meets the definition of an act of cyberwar, and the US government should respond as such.
The claims by “Guccifer 2.0”—that a lone hacker carried out this attack—are not believable. Of course, anything is possible, but the attack looks to be an operation conducted by Russian intelligence services. Had this been a “normal” operation—that is, covert intel gathering by Russia's Foreign Intelligence Service or any other foreign intelligence service (as the Chinese have done in past election seasons)—it would be business as usual. To be honest, the US government would not really be justified in denouncing it, as it does the same thing. But what makes this attack very different—and crosses the line—is the Russian team’s decision to dump the Clinton campaign’s opposition strategy on the public Web, presumably for the dual purpose of both spreading misinformation about the party responsible for the breach and interfering with the Clinton campaign.
Philippe J DEWOST's insight:
"Elections are critical infrastructure that should be hands-off for governments." - The new faces of cyberwar
A Chinese supercomputer built using domestic chip technology has been declared the world's fastest. The news highlights China's recent advances in the creation of such systems, as well the country's waning reliance on US semiconductor technology.the taihulight is capable of 93 petaflopsThe Sunway TaihuLight takes the top spot from previous record-holder Tianhe-2 (also located in China), and more than triples the latter's speed. The new number one is capable of performing some 93 quadrillion calculations per second (otherwise known as petaflops) and is roughly five times more powerful than the speediest US system, which is now ranked third worldwide.The TaihuLight is comprised of some 41,000 chips, each with 260 processor cores. This makes for a total of 10.65 million cores, compared to the 560,000 cores in America's top machine. In terms of memory, it's relatively light on its feet, with just 1.3 petabytes used for the entire machine. (By comparison, the much less powerful 10-petaflop K supercomputer uses 1.4 petabytes of RAM.) This means it's unusually energy efficient, drawing just 15.3 megawatts of power — less than the 17.8 megawatts used by the 33-petaflop Tianhe-2.More significantly than its specs, though, is the fact that the TaihuLight is built from Chinese semiconductors. "It’s not based on an existing architecture. They built it themselves," Jack Dongarra, a professor at the University of Tennessee and creator of the measurement system used to rank the world's supercomputers, told Bloomberg. "This is a system that has Chinese processors."
Philippe J DEWOST's insight:
So the fastest supercomputer is chinese again. Now that the Longsom chips have dethroned Intel, what is the next step ? Running ChinaOS on top of it maybe ?Most surprising to me is Europe silence in this race for digital sovereignty; let's hope we will accelerate on https://riscv.org/
Le système mondial de virement SWIFT a recommandé mardi à ses 11.000 banques clientes dans le monde de relever leur niveau de sécurité. L'agence d'investigation FireEye a authentifié des menaces de cyber-attaques similaires à celles ayant visé la banque centrale du Bangladesh.Le cyber-braquage de la Banque centrale du Bangladesh, qui s'est vu dérober 81 millions de dollars en février au travers du système de transfert de fonds Swift, n'était qu'un avant goût. Les pirates informatiques s'en prennent à d'autres institutions financières. Le centre nerveux du système financier mondial a en effet recommandé mardi à ses 11.000 banques clientes de relever leur niveau de sécurité quand elles passaient par ses réseaux.
Philippe J DEWOST's insight:
Le Bengladesh n'était-il qu'un bêta-test ?
FOR MOST OF the past six weeks, the biggest story out of Silicon Valley was Apple’s battle with the FBI over a federal order to unlock the iPhone of a mass shooter. The company’s refusal touched off a searing debate over privacy and security in the digital age. But this morning, at a small office in Mountain View, California, three guys made the scope of that enormous debate look kinda small.
Philippe J DEWOST's insight:
Rage against the machine, at scale. How will governments react ?
ZeroNet, a serverless P2P network that uses Bitcoin cryptography and BitTorrent technology, may be the first real, usable prototype of a decentralized web.BitTorrent users can download files directly from other users, without needing a central server. The BitTorrent technology for distributed file storage and peer-to-peer transfers, one of the biggest developments in Internet technology since the Web itself, opens the way to a distributed, fully decentralized Internet.A decentralized Internet would be much more resilient than today’s framework of central servers, in spite of the associated piracy often in the news headlines. There isn’t much the authorities can do to prevent BitTorrent users from exchanging files. But users need to know that downloadable files are available, and then search torrents on centralized torrent sites such as The Pirate Bay. The centralized torrent sites are vulnerable to copyright enforcement countermeasures, ranging from domain seizure to actual server seizure.
Philippe J DEWOST's insight:
It's getting complicated as they say...
Overall, the FBI's request could be seen as a testament to just how good encryption is. The FBI can't attack the iPhone's encryption directly, and it can't bypass the firmware signature mechanism. There's no existing backdoor to the crypto.But what the iPhone does have is software lockouts, and the security of those lockouts is entirely up to Apple. Apple's signing key gives the company wide power over the software-level protections built in to iOS. The FBI knows this, and that is why it's demanding the company's assistance.
Philippe J DEWOST's insight:
Great and clear post explaining that the FBI vs. Apple case is both simpler and more complex than some judgements expressed by the Kommentariat recently. Worth a full read even if the title is voluntarily ambiguous.
A Message to Our Customers:"The Need for EncryptionSmartphones, led by iPhone, have become an essential part of our lives. People use them to store an incredible amount of personal information, from our private conversations to our photos, our music, our notes, our calendars and contacts, our financial information and health data, even where we have been and where we are going.All that information needs to be protected from hackers and criminals who want to access it, steal it, and use it without our knowledge or permission. Customers expect Apple and other technology companies to do everything in our power to protect their personal information, and at Apple we are deeply committed to safeguarding their data.Compromising the security of our personal information can ultimately put our personal safety at risk. That is why encryption has become so important to all of us.For many years, we have used encryption to protect our customers’ personal data because we believe it’s the only way to keep their information safe. We have even put that data out of our own reach, because we believe the contents of your iPhone are none of our business."
Philippe J DEWOST's insight:
Interesting, bold statement endorsed by Tim Cook himself that puts the encryption debate in the right light. Inbetween I am happy to be (and stay) on iOS
Sécurité : L'attaque par déni de service (DDoS) de la semaine dernière contre la BBC a peut-être été la plus grande dans l'histoire de la sécurité informatique. Via Raphael Lecoq
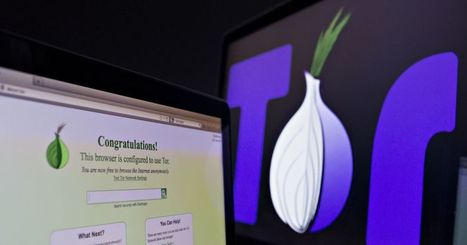
If you still assume you don't forfeit the right to privacy by going online, there are very few truly secure OS options.The best one might be the Linux flavor called Tails, recommended by none other than Edward Snowden. Its encrypted apps include email and messaging clients, a web browser, and of course, the anonymizing Tor network.The folks behind the open-source program have just launched version 2.0, with a new UI and numerous security fixes.
Philippe J DEWOST's insight:
In French we say "cache cache"...
All technology impacts our individual daily lives one way or another—but perhaps no technology makes us question our collective humanity as much as artificial intelligence.Ray Kurzweil, inventor and futurist, spoke to an audience during a session last summer about a few of the political and philosophical implications of AI when he was asked, “In a world where AI passes the Turing test, who gets to vote? Does democracy make sense?”Kurzweil describes a fictional scenario where an advanced AI sues for its rights as a citizen. While that alone may seem strange, the implications of granting rights to AI are even more bizarre. One major difference between living people and aware machines? The ability to count one human mind and individual person is easy. Not so much for interconnected, intelligent machines.“In the world of computation in which an intelligence is just a process, you can run 100 processes on one computer or you can have a million computers that are one process,” Kurzweil says, “It’s very fluid—how are you going to count them? They don’t come in these discrete enclosures which are countable and you can keep track of them and say: ‘OK, you have voting rights; but you’re too young, you don’t have it.’”
Philippe J DEWOST's insight:
First, such decision belongs to the people, not the machines.Second, we better have people (re)read Asimov before even thinking about making such a decision
A few weeks ago I was on a blockchain panel, organised by the World Economic Forum, discussing amongst many things use of blockchains as a digital identity store, when someone from the audience asked me about the implications of quantum computing on confidentiality of data stored on blockchains. My answer was somewhat under par. Indeed, quantum computing will break many existing cryptographic algorithms - making today's secret data public, but with quantum computing comes quantum cryptography, or more precisely quantum key distribution, which is immune to quantum computing attacks. After the panel was over, the lady who asked me that question came over, thanked me for being on the panel, and asked a follow up question - what would happen to all that data encrypted with quantum un-safe algorithms already stored on blockchain? A big thank you to her for being so polite and not embarrassing me on the panel because I suspect the answer was obvious to her, and yet it's implications escaped me. Data already stored on blockchain with current quantum un-safe algorithms will become public, even if all data encrypted with quantum safe techniques will be kept secure going forwards. Cryptography relies on scrambling data using a very long secret random number, and the only way to unscramble that data is by knowing that secret. There are no mathematical tricks to shortcut the working out of that number, so the only way to un-scramble the data is to guess, in a brute force fashion, the secret number - impractical using today's computers, as secret number range is so big that that it takes almost an infinite amount of time to guess it. However, how do you safely share that secret safely over a public network? To solve this problem, public key cryptography was invented. You create two keys, public and private, which are mathematically linked - any data encrypted with a private key can only be decrypted with public key and vice versa. If you keep the private key safe, and send out your public key, then people can send you confidential messages by encrypting data with your public key, safe in the knowledge that only you, as the sole keeper of the private key, can read that message i.e. no need to secretly pre-share a key over some private transfer method that reduces the risk of eavesdropping. However, this link between private and public key introduces a tiny vulnerability - there is now a mathematical shortcut that allows you guess the linked private key much more quickly that when trying to guess a random secret key. Using today's computers though it still takes almost an infinite amount of time to guess the private key, even with the shortcut. However, quantum computing relies on many different states of quantum particles to perform millions of calculations all at once, allowing you to guess the private key in short enough time compared to today, breaking confidentiality. On the hand, even with quantum computers, it is still likely to take unpractically long time to guess a shared secret key, as there is no public key to exploit. Lucky for us, quantum key distribution, an implementation of quantum cryptography, uses the same very principles that allows super fast calculations to break today's popular public-key cryptography algorithms for a different purpose - you can do away in some cases with public and private keys and simply share quantum-safe secret keys over public networks without a possibility of interception, as it is impossible to copy quantum encoded data and any eavesdropping changes the state of data, making intrusion highly detectable. This may go some way to mitigating against quantum attacks.
Philippe J DEWOST's insight:
Are you quantum-safe ? Long yet instructive post by Alex Battlin that introduces the notion and applies it to Blockchains |
With a vigorous national debate underway on whether Sweden should enter a military partnership with NATO, officials in Stockholm suddenly encountered an unsettling problem: a flood of distorted and outright false information on social media, confusing public perceptions of the issue.
Philippe J DEWOST's insight:
Worth a (re)read. Very documented and well written article on (dis)information as a tool / weapon,
If you feel (really) secure about your password, don't change it....
Philippe J DEWOST's insight:
And if not, the post contains a link towards the proper way of generating a secure password.
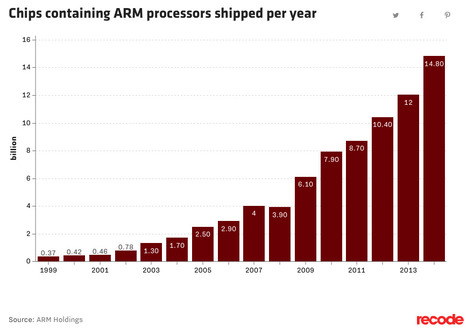
Japan’s SoftBank is buying U.K.-based chip design firm ARM Holdings for about $32 billion, according to the FT.
Philippe J DEWOST's insight:
As Brexit has removed ARM from Europe, will it be left as the impotent witness of what we shall call an ARM's race ? This news echoes the announcement of World's new #1 Supercomputer, that is chinese again, but more interestingly no longer features any Intel processor inside but domestic LongSoon chips. The Silicon race is on its way to a US - Asia bipolar configuration, with Europe being left alone due to the combined effect of Brexit and ARMXit : time for investi(gati)ng (in) open source hardware architectures such as RISC-V ... 
Philippe J DEWOST's curator insight,
July 18, 2016 1:14 AM
ARM takeover by SoftBank is the Tech Brexit of this summer. This thunderstrike in a blue ocean (pardon me, sky) might trigger a war where we will all of a sudden remember how important it is having a war chest. There are underlying geopolitics ongoing as evidenced by the progress made by the LongSoon chinese processor now powering world #1 Supercomputer. It might also signal the beginning of the end of the ARM era, and should have more people focusing on open source silicon architectures such as RISC-V
Recent Intel x86 processors implement a secret, powerful control mechanism that runs on a separate chip that no one is allowed to audit or examine. When these are eventually compromised, they'll expose all affected systems to nearly unkillable, undetectable rootkit attacks. I've made it my mission to open up this system and make free, open replacements, before it's too late.The Intel Management Engine (ME) is a subsystem composed of a special 32-bit ARC microprocessor that's physically located inside the chipset. It is an extra general purpose computer running a firmware blob that is sold as a management system for big enterprise deployments.When you purchase your system with a mainboard and Intel x86 CPU, you are also buying this hardware add-on: an extra computer that controls the main CPU. This extra computer runs completely out-of-band with the main x86 CPU meaning that it can function totally independently even when your main CPU is in a low power state like S3 (suspend).On some chipsets, the firmware running on the ME implements a system called Intel's Active Management Technology (AMT). This is entirely transparent to the operating system, which means that this extra computer can do its job regardless of which operating system is installed and running on the main CPU.The purpose of AMT is to provide a way to manage computers remotely (this is similar to an older system called "Intelligent Platform Management Interface" or IPMI, but more powerful). To achieve this task, the ME is capable of accessing any memory region without the main x86 CPU knowing about the existence of these accesses. It also runs a TCP/IP server on your network interface and packets entering and leaving your machine on certain ports bypass any firewall running on your system.While AMT can be a great value-add, it has several troubling disadvantages. ME is classified by security researchers as "Ring -3". Rings of security can be defined as layers of security that affect particular parts of a system, with a smaller ring number corresponding to an area closer to the hardware. For example, Ring 3 threats are defined as security threats that manifest in “userspace” mode. Ring 0 threats occur in “kernel” level, Ring -1 threats occur in a “hypervisor” level, one level lower than the kernel, while Ring -2 threats occur in a special CPU mode called “SMM” mode. SMM stands for System-Management-Mode, a special mode that Intel CPUs can be put into that runs a separately defined chunk of code. If attackers can modify the SMM code and trigger the mode, they can get arbitrary execution of code on a CPU.Although the ME firmware is cryptographically protected with RSA 2048, researchers have been able to exploit weaknesses in the ME firmware and take partial control of the ME on early models. This makes ME a huge security loophole, and it has been called a very powerful rootkit mechanism. Once a system is compromised by a rootkit, attackers can gain administration access and undetectably attack the computer.On systems newer than the Core2 series, the ME cannot be disabled. Intel systems that are designed to have ME but lack ME firmware (or whose ME firmware is corrupted) will refuse to boot, or will shut-down shortly after booting.There is no way for the x86 firmware or operating system to disable ME permanently. Intel keeps most details about ME absolutely secret. There is absolutely no way for the main CPU to tell if the ME on a system has been compromised, and no way to "heal" a compromised ME. There is also no way to know if malicious entities have been able to compromise ME and infect systems.A large portion of ME's security model is "security through obscurity", a practice that many researchers view as the worst type of security. If ME's secrets are compromised (and they will eventually be compromised by either researchers or malicious entities), then the entire ME security model will crumble, exposing every recent Intel system to the worst rootkits imaginable.Around 2013, we figured out some of the nitty-gritty details regarding how the ME firmware was packaged up into a blob. The ME firmware is verified by a secret boot ROM embedded in the chipset that first checks that the SHA256 checksum of the public key matches the one from the factory, and then verifies the RSA signature of the firmware payload by recalculating it and comparing to the stored signature. This means that there is no obvious way to bypass the signature checking, since the checking is done by code stored in a ROM buried in silicon, even though we have the public key and signature. However, there still might be an exploitable bug in the ROM bootloader.We also discovered that the critical parts of the ME firmware are stored in a non-standard compressed format, which gets decompressed by a special hardware decompressor. My initial attempts to brute-force the decompression scheme failed miserably. Another group had better success and they have now completed a working decompression routine for all versions of ME up to but not including version 11. Kudos to them!Our goal is to implement a completely libre software replacement for ME. When the implementation of such a security-critical component is available for scrutiny, it will be peer-reviewed and audited by persons around the world. This generally results in stronger security.Our goal isn't to replace Intel's ME, but to provide a minimal libre alternative firmware for users who choose to use it. Unfortunately, since the firmware is protected by RSA 2048, we currently have no way to execute our own code on the ME hardware because it fails validation. We have no way to move forward, even if we wanted to.This is scary. Most digital handcuffs are so easy to break that it's not an issue how to break it, more so an issue of the penalty one might face for actually breaking it. In this case, it is impossible to break unless you have a way to factorize semi-primes with approximately 600 decimal digits in a reasonable time. (At the time of writing this article, pretty much impossible in one human lifetime for anyone with the biggest supercomputer).So in conclusion, Intel has so far stopped anyone from tinkering with ME firmware in practice, and there is no way to trust the code running on your ME because it's proprietary. So we are back to the days of the Sony Playstation, but for general purpose computers based on Intel x86. Matters only get worse now that Intel has squeezed a whole system into a chip, SoCs. We have no physical separation between the components that we can trust and the untrusted ME components, so we can't even cut them off the mainboard anymore.Below is a highly simplified diagram describing how some of the older ME hardware fits into a system:Personally, I would like if my ME only did the most basic task it was designed for, set up the bus clocks, and then shut off. This way, it would never be able to talk out of the network card with some of my personal data. I refer to the ME as the Damagement Engine, since it is a hardware add-on that damages your security.(Banner: PIC12C508-HD, ZeptoBars, CC-BY; Diagram, CC0)Who really hacked the DNC?056c026d-1c66-4d42-9fae-a8e96df290c5-1020x1117Earlier this week Crowdstrike, a security company hired by the Democratic National Committee, announced that the party’s servers had been deeply penetrated by hackers working for the Russian government, who had made off with many sensitive files, including the DNC’s Trump oppo research spreadsheet.READ THE RESTGet a 2-Pack of Two-Meter MFi-Certified Lightning Cables, Now 77% offWe all love our iPhones and iPads. But if there’s one thing about them we don’t like, it’s their dang charging cables. It seems like they’re barely out of the box before they’re peeling, frayed, and ultimately unusable. Replacing any Apple product – even charging cables – usually comes at a premium price. Thankfully, we’re looking out […]READ THE REST
Philippe J DEWOST's insight:
Another challenge on "security through obscurity" approaches, and the question of silicon auditability.
CBS's 60 Minutes created something of a stir over the weekend when it reported on a vulnerability in the worldwide mobile exchange system that continues to allow hackers to access others' wireless data using nothing but a phone number. But if U.S. operators are terrified about any dangers the flaw may represent to their customers, they don't seem to be showing it.The reported weakness lies in SS7, or Signaling System Seven, which is a set of telephony signaling protocols that serves to broker information between wireless networks. Hackers can exploit the vulnerability with the phone number of the user they're targeting to listen to phone calls, read text messages and track the user's location.The hack first came to light in 2014 when security researcher Karsten Nohl demonstrated it at a convention in Germany. Nohl recently demonstrated it again for 60 Minutes during a broadcast that aired Sunday, using the flaw to track a new iPhone that had been given to U.S. Rep. Ted Lieu (D-Calif.). Lieu, who holds a degree in computer science from Stanford, agreed to sue the phone to talk to his staff knowing it would be hacked.
Philippe J DEWOST's insight:
Vulnerability at (massive) scale ?
A confidential FBI alert shows that government hackers are still roaming through US government networks..../...The FBI wouldn’t comment on the alert, only saying that it was just another example of a routine notice to private partners, “provided in order to help systems administrators guard against the actions of persistent cyber criminals.”This group of “persistent cyber criminals” is especially persistent. The group is none other than the “APT6” hacking group, according to sources within the antivirus and threat intelligence industry. There isn’t much public literature about the group, other than a couple of old reports, but APT6, which stand for Advanced Persistent Threat 6, is a codename given to a group believed to be working for the Chinese government.“This is one of the earlier APTs, they definitely go back further than 2011 [...] more like 2008.”
Philippe J DEWOST's insight:
5 to 8 years is a very long time especially for insiders...
The possibility of a cyberattack on critical infrastructure such as America’s electric power worries National Security Agency (NSA) Director Admiral Michael Rogers, who told a cyber security conference that it’s a “matter of when, not if” hackers successfully attack America’s power grid.The US eventually will suffer a cyber assault like the one that knocked out power in the Ukraine, Rogers told an audience at the RSA Conference in San Francisco in early March. During that attack hackers used the Black Energy cyber weapon to literally turn the lights out on more than 200,000 people across the region.
Philippe J DEWOST's insight:
Without overreacting, worth a read...
Backdoors For Good Guys Only is pliable material for chest-thumping politicians, but legitimate leaders must have the courage to tell the plain truth: It won’t work, it’ll only hurt good people.
Philippe J DEWOST's insight:
Great, clear and well documented analysis by Jean-Louis Gassee on what is at stake when it comes to "official" backdoors #MondayNote
La sécurité informatique en transformation: tendances, caractéristiques, économies… Par Fabrice Epelboin, expert FrenchWeb. Via Didier Tranchier
Philippe J DEWOST's insight:
Je me demande ce qu'en pense @Philippe Gaillard...
On my last morning in Davos, I spotted one of those telepresence robots — the kind Sheldon uses in Big Bang Theory and the kind Edward Snowden has used for interviews and speeches — and fantasized about hacking into it to enable Snowden himself to appear in the halls of the annual meeting of the World Economic Forum.That would be be appropriate, for this struck me as the post-Snowden Davos. It took a few years to sink in, but the results of Snowden’s work and his name — although mostly mumbled or hushed — came up time and again during last week’s do. Trust, transparency, surveillance, encryption, security — his impact echoed in subject after subject. To me, this is further evidence that Edward Snowden is no spy, no traitor, no hacker, no criminal, and more than a whistleblower. Edward Snowden is a policymaker as influential as most anyone invited to the clubhouse of the rich and powerful.
Philippe J DEWOST's insight:
"Edward Snowden is a policymaker as influential as most anyone invited to the clubhouse of the rich and powerful." writes the author of this fascinating post...
Autonomous weapons experts sounded the alarm last week at the World Economic Forum in Davos, Switzerland, cautioning that unless governments act to limit these weapons’ risks, it may be too late.Autonomous weapons haven’t surfaced in the mainstream but loom on the horizon as the technology behind them is young, but rapidly advancing. Based on existing technology, the weapons could be able to independently find and kill enemies, so that a country doesn’t put its humans in harm’s way. The weapons may arrive in a variety of forms, including small drones or robot soldiers.“Being attacked by an army of Terminators is a piece of cake when compared to being attacked by this kind of weapon,” said Stuart Russell, a computer science professor at the University of California-Berkeley. “We’re [talking] about systems that weigh less than an ounce, that can fly faster than a person can run, can blow holes in their heads with one gram of shape-charge explosive, and can be launched in the millions.”Russell and Angela Kane, a senior fellow at the Vienna Center for Disarmament and Non-Proliferation, warned that time is running out to prevent us from opening Pandora’s Box. They estimate that the problem needs to be addressed within two years to prevent a global arms race toward autonomous weapons. The fear is that autonomous weapons could become akin to a new, more powerful AK-47 — an affordable, easily obtained weapon of global destruction. These weapons wouldn’t require rare and expensive materials, which help to limit access to nuclear weapons. Russell and Kane called for scientists, governments and the artificial intelligence industry to convene quickly.“Do we really want to put the power to wipe out everyone in New York City in the hands of individuals who just need to be able to afford to buy those weapons?,” said Russell, who described autonomous weapons being capable of of targeting individuals based on their age or style of clothing.That is one reason experts are calling for an autonomous weapons convention similar to what the world did to address biological and chemical weapons. Russell’s group, the Future of Life Institute, hopes a ban on the weapons will head off a global arms race to develop autonomous weapons.So far little has been done to address the risk."You ave a very glacial pace of international negotiations. They haven’t even really started,” said Kane, who previously was a U.N. representative for disarmament affairs, and struggled to get states to tackle the issue. “The pace at looking at this issue in terms of international law is far behind [the technology].”Roger Carr, chairman of weapons manufacturer BAE Systems, who joined the panel discussion in Davos, cautioned that governments are in over their heads when it comes to the cutting edge of technology.“The people who have the job of making the judgment as to whether it should be something we legislate for, very often do not have a full understanding of where we are in the process, and the risk, and how close it is to becoming a reality,” Carr said.While some may take solace in the fact that autonomous weapons aren’t fully developed, Russell is concerned that some bad actors won’t care.“Do you think ISIS needs their drones to be that reliable in discriminating civilians from soldiers? No,” Russell said, “80 percent is pretty good for military equipment. So I think that would be very easily achievable with present-day technology.”https://www.washingtonpost.com/news/innovations/wp/2016/01/25/if-killer-robots-arrive-the-terminator-will-be-the-least-of-our-problems/
Philippe J DEWOST's insight:
More and more inclined to think Elon Musk was right when he first raised the flag
When a baby boy was born on August 4, 1961, the local newspaper announced his birth, as it did many others. More than a declaration of happy news by his parents, those few lines of information were part of a long-lasting tradition -- using the local daily to register, at a set point in time, the addition of a new person to society. Seemingly inconsequential timestamps like these occur every day and, as it turns out, play a key role in ensuring more fair and just societies. It's not just limited to births. Kidnappers take photos of hostages holding the front page of a recent newspaper to act as proof that they are still alive. Governments often require entrepreneurs to publish the establishment of their new company in a local newspaper. Beyond newspapers, a postmark confirms to a government that taxpayers filed their taxes on time. A patent helps inventors to prove that they developed an invention first. But when we depend on private companies to manage this task, we have the potential for exposing ourselves to abuse. Manipulation of the chronological order -- as when banks process a customer's largest cheque first rather than their most recent to increase the likelihood of it bouncing -- creates a less just world. Similar to the internet's facilitation of instant, global communication, a combination of time-stamped and digitally signed transactions hosted on an accessible ledger could play an important role. They could help governments reduce friction and increase transparency associated with important transactions. How might this be accomplished? Ironically, Bitcoin, an idea that was once thought to be anti-government, could end up a key platform for governments to achieve these goals.
Philippe J DEWOST's insight:
Another well written text piece if you want to embrace the blockchain in its genericity |











![Ray Kurzweil on Giving Future AI the Right to Vote [Video] - Singularity HUB | Digital Sovereignty & Cyber Security | Scoop.it](https://img.scoop.it/qxuhBzzyLC_XQXKT8Zphjzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
















Must read as recent cyber events unveil a new key and vulnerable infrastructure : elections ...