Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
President Donald Trump blocked a Chinese-backed investor from buying Lattice Semiconductor Corp., casting a cloud over Chinese deals seeking U.S. security clearance and spurring a call for fairness from Beijing. It was just the fourth time in a quarter century that a U.S. president has ordered a foreign takeover of an American firm stopped on national-security concerns. Trump acted on the recommendation of a multi-agency panel, the White House and the Treasury Department said Wednesday. The spurned buyer, Canyon Bridge Capital Partners LLC, is a private-equity firm backed by a Chinese state-owned asset manager. The Trump administration has maintained a tough stance against Chinese takeovers of American businesses even as it seeks China’s help to resolve the North Korean nuclear crisis. Other deals under review include MoneyGram International Inc.’s proposed sale to Ant Financial, the financial-services company controlled by Chinese billionaire Jack Ma. The government is also examining an agreement by Chinese conglomerate HNA Group Co. to buy a stake in SkyBridge Capital LLC, the fund-management firm founded by Anthony Scaramucci, who was briefly Trump’s White House communications director. "Consistent with the administration’s commitment to take all actions necessary to ensure the protection of U.S. national security, the president issued an orderprohibiting the acquisition," Treasury Secretary Steven Mnuchin said in a statement. In Beijing, Ministry of Commerce spokesman Gao Feng said a media briefingThursday that China is concerned over the matter and that the U.S. should create a fair and transparent business environment. “Conducting security checks on a sensitive investment is a nation’s legitimate right, but it shouldn’t be used as a protectionist tool,” Gao said, adding that the acquisition is a corporate decision that the U.S. should evaluate objectively. MoneyGram shares fell as much as 4.4 percent in after-market U.S. trading, while Lattice shares sank as much as 1.7 percent. Shares of Genworth Financial Inc., which has a $2.7 billion sale to China Oceanwide Holdings Group Co. pending U.S. approval, fell 2.7 percent. Canyon Bridge said in a statement it was disappointed with the decision and would stay focused on other investment opportunities. Lattice said in a statement that the acquisition was being terminated after the president’s order. “The transaction with Canyon Bridge was in the best interests of our shareholders, our customers, our employees and the United States,” Lattice Chief Executive Officer Darin G. Billerbeck said in the statement. “We will continue to focus on initiatives that will contribute to Lattice’s long-term success.” Billerbeck came to Washington two weeks ago to make a last-ditch effort to persuade government officials to support the deal, Bloomberg News reported. Lattice and Canyon Bridge had proposed measures they said would address U.S. concerns while allowing the deal to proceed, according to that report. WebRep currentVote noRating noWeight
Philippe J DEWOST's insight:
4th US Presidential Block of Foreign Takeover in 27 years. #HardwareIsNotDead WebRep currentVote noRating noWeight
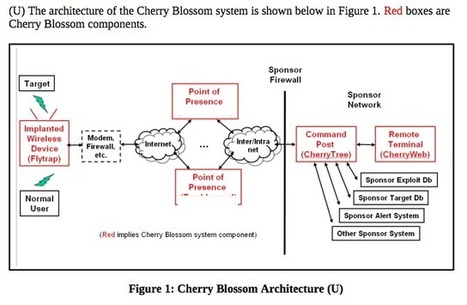
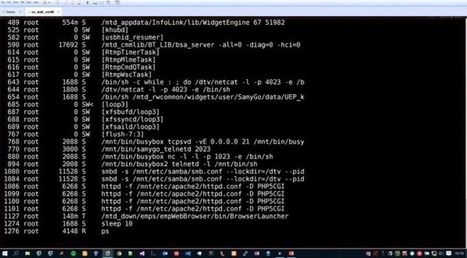
Routers sit at the front gate of nearly every network, offering total access and few security measures to prevent remote attacks. If you can compromise someone’s router, you’ve got a window into everything they’re doing online.According to new documents published by WikiLeaks, the CIA has been building and maintaining a host of tools to do just that. This morning, the group published new documents describing a program called Cherry Blossom, which uses a modified version of a given router’s firmware to turn it into a surveillance tool. Once in place, Cherry Blossom lets a remote agent monitor the target’s internet traffic, scan for useful information like passwords, and even redirect the target to a desired website.The document is part of a series of publications on CIA hacking tools, including previous modules targeting Apple products and Samsung Smart TVs. As with previous publications, the document dates to 2012, and it’s unclear how the programs have developed in the five years since.The manual describes different versions of Cherry Blossom, each tailored to a specific brand and model of router. The pace of hardware upgrades seems to have made it arduous to support each model of router, but the document shows the most popular routers were accessible to Cherry Blossom.“As of August 2012,” the manual reads, “CB-implanted firmwares can be built for roughly 25 different devices from 10 different manufacturers, including Asus, Belkin, Buffalo, Dell, DLink, Linksys, Motorola, Netgear, Senao, and US Robotics.”The manual also goes into detail on how CIA agents would typically install the modified firmware on a given device. “In typical operation,” another passage reads, “a wireless device of interest is implanted with Cherry Blossom firmware, either using the Claymore tool or via a supply chain operation.” The “supply-chain operation” likely refers to intercepting the device somewhere between the factory and the user, a common tactic in espionage operations. No public documents are available on the “Claymore tool” mentioned in the passage.It’s unclear how widely the implant was used, although the manual generally refers to use against specific targets, rather than for mass surveillance. There’s also reason to believe the NSA was employing similar tactics. In 2015, The Intercept published documents obtained by Edward Snowden that detailed efforts by the UK’s GCHQ to exploit vulnerabilities in 13 models of Juniper firewalls.
Philippe J DEWOST's insight:
This was back 5 years ago : how has it evolved by now ?
Refondons un Conseil National du Numérique Citoyen, Technologique et International. Alors qu'un nouveau quinquennat débute, sous le leadership d'un président jeune et innovant, le numérique peine à s'imposer comme priorité politique. Le Conseil national du numérique (CNNUm) est devenu une sorte de «machin» et ne remplit plus sa mission de moteur de la réflexion et de l'action dans le secteur du numérique. Pour ne pas abandonner après nous être tant engagés dans le secteur, il faut des propositions fortes (http://nouveaucnnum.wordpress.com) pour rénover cette institution et lui redonner un poids dans la vie de la cité. Le CNNum a été créé en avril 2011 avec l’idée de créer un organe consultatif du Gouvernement sur les questions du développement du numérique. Dans cet esprit il a accompagné nos politiques dans l’élaboration de la loi sous l’influence des nombreux effets de la révolution numérique. On constate aujourd’hui que malgré cet énorme travail, peu de gens connaissent l’action du CNNum hors du microcosme numérico-politique alors que son rôle est capital. Je propose donc aujourd’hui, au démarrage de ce nouveau quinquennat, de transformer le CNNum et de lui fixer un nouveau cap. Fort de mon expérience quotidienne auprès des start-up et d’échanges avec les acteurs de l’ecosystème je formule quelques propositions qui permettrait selon moi d’entreprendre cette mutation.
Philippe J DEWOST's insight:
Evolution ou Refondation ? dans les deux cas une série de propositions à discuter et à débattre en vue d'accélérer et d'agir.
For years, automakers and hackers have known about a clever attack that spoofs the signal from a wireless car key fob to open a vehicle’s doors, and even drive it away. But even after repeated demonstrations—and real thefts—the technique still works on a number of models. Now a team of Chinese researchers has not only demonstrated the attack again, but also made it cheaper and easier than ever. A group of researchers at the Beijing-based security firm Qihoo 360 recently pulled off the so-called relay hack with a pair of gadgets they built for just $22. That’s far cheaper than previous versions of the key-spoofing hardware. The Qihoo researchers, who recently showed their results at Amsterdam’s Hack in the Box conference, say their upgrade also significantly multiplies the radio attack’s range, allowing them to steal cars parked more than a thousand feet away from the owner’s key fob. The attack essentially tricks both the car and real key into thinking they’re in close proximity. One hacker holds a device a few feet from the victim’s key, while a thief holds the other near the target car. The device near the car spoofs a signal from the key. That elicits a radio signal from the car’s keyless entry system, which seeks a certain signal back from the key before it will open. Rather than try to crack that radio code, the hacker’s devices instead copy it, then transmit it via radio from one of the hackers’ devices to the other, and then to the key. Then they immediately transmit the key’s response back along the chain, effectively telling the car the key is in the driver’s hand. “The attack uses the two devices to extend the effective range of the key fob,” says Jun Li, one of the researchers in the Qihoo group, who call themselves Team Unicorn. “You’re working in your office or shopping in the supermarket, and your car is parked outside. Someone slips near you and then someone else can open up and drive your car. It’s simple.” Watch the researchers demonstrate their attack in the video below (including a very dramatic soundtrack)
Philippe J DEWOST's insight:
Puzzling echo to the 20 M compromised VW Fobs last year : looks it may be worsening. See how in video...
Approximately half of adult Americans’ photographs are stored in facial recognition databases that can be accessed by the FBI, without their knowledge or consent, in the hunt for suspected criminals. About 80% of photos in the FBI’s network are non-criminal entries, including pictures from driver’s licenses and passports. The algorithms used to identify matches are inaccurate about 15% of the time, and are more likely to misidentify black people than white people.
Philippe J DEWOST's insight:
Maybe FBI could get some help from Facebook or Apple faces recognition in images to lower their 15% inaccuracy ? #AI #JustKidding #1984
A few announcements that came out of last week’s Open Compute Summit in Santa Clara and the Google Cloud Next conference in San Francisco however showed that while Intel’s lead may be massive, it’s under bigger threat than may have appeared.
Philippe J DEWOST's insight:
Wintel coming to an end. ARM's rise in the server space was forecasted yet totally misunderstood in France. Hoping that we will draw the lesson and look way more seriously into OpenRisc-V.
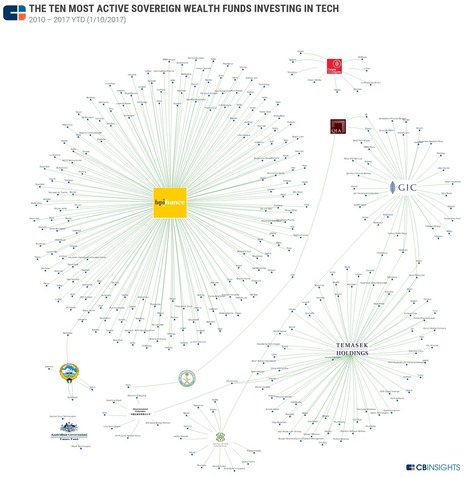
Over the last seven years, France’s Banque publique d’investissement, or Bpifrance, has been the world’s most active sovereign wealth fund investing in private tech companies. Bpifrance was originally set up as a sovereign investment fund in 2009. The government of Singapore owns the world’s second and third most active funds. These two funds are Temasek Holdings, which distributes dividends solely to Singapore’s Ministry of Finance, and GIC, the private equity investment arm of the government of Singapore Investment Corporation.
Philippe J DEWOST's insight:
Very proud to see our largest subsidiary deploying the "Investments For The Future" (the €35 Bn plan launched in 2011) funds across the french economy, and proud to see its Mother Company being also part of the ranking in such a prestigious crowd ! Disclosure : I work for Caisse Des Dépôts representing it as the sole LP in the Bpifrance funds managed for the IFF/PIA program. 
Philippe J DEWOST's curator insight,
January 26, 2017 5:52 AM
Very proud to see our largest subsidiary deploying the "Investments For The Future" (the €35 Bn plan launched in 2011) funds across the french economy, and proud to see its Mother Company being also part of the ranking in such a prestigious crowd ! Disclosure : I work for Caisse Des Dépôts representing it as the sole LP in the Bpifrance funds managed for the IFF/PIA program.
Numalis provides the very first software to validate and optimize numerical accuracy while improving performance To correct numerical deviations, engineers currently test the same mathematical formula in as many forms as possible to find the best, and then check whether it is sufficiently stable and accurate... but it can be quite a challenge to test everything in a given time frame. With Numalis, you can automatically detect any calculation issues during the development phase and then select the proposed correction in order to reduce numerical deviation and, consequently, optimize stability and performance. Embedded Software
From aeronautics to space and defense, numerical stability is a matter of concern. However, manual inquiries require a lot of expertise and a lot of time to be done properly. With Numalis, this expertise is available to anyone, with fast and comprehensive tools helping engineers write safer and more efficient code. Discover more about our :
Philippe J DEWOST's insight:
Even if the the Intel Pentium FDIV bug (a computer bug that affected the floating point unit (FPU) of the early Intel Pentium processors and induced rounding errors) is 12 years away from us now, checking the accuracy of code, especially in critical systems, will become key. This french startup has designed a smart code verification & optimization tool to adress this core issue. If "Code wins Argument" and even further, "Code is Law", we'd better have clean and checked code #TheDAO
Sécurité : La notification d'une attaque rend les relations entre les RSSI et leurs directions très tendues selon une étude Morar / Palo Alto Networks. Via Thierry Evangelista
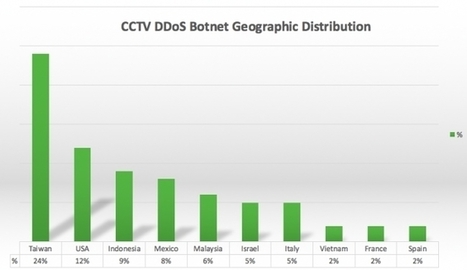
Habitué à être pris pour cible par des pirates, l’hébergeur français OVH a tout de même été surpris par l’ampleur et l’origine de la dernière attaque par déni de service distribuée (DDoS) dont il a été victime. Celle-ci s’est déroulée récemment, entre le 18 et le 23 septembre. Selon Octave Klaba, fondateur et directeur technique de la société, elle avait un débit supérieur au térabit par seconde et provenait d’un botnet constitué de 145.607 caméras connectés.
Philippe J DEWOST's insight:
"Big Brother is DDoSing you" : où comment les caméras IP peuvent (également) être utilisées pour du #crowdattacking a une échelle inédite...
Heard of that presidential election coming up? Russia has too. And that worries US officials. WHAT'S GOING ON?Yesterday, the head of the NSA told lawmakers that he's worried a foreign government (hint: rhymes with Shmussia) may be trying to undermine the US election. The FBI is investigating two recent cyber attacks on voter registration databases in Illinois and Arizona that were traced back to Russia. Officials think more states might have been targeted, but their lips are sealed because classified. WHY IS THIS HAPPENING?Unclear. But this comes after the Democratic party was hacked earlier this year by groups believed to have ties to zee Russian government. The Clinton campaign thinks Russia hacked the Dems to benefit GOP nominee Donald Trump, who has given props to Russian President Putin many times on the campaign trail. Trump says Putin's not helping him, but he wouldn't mind if Russia did some more digginginto Clinton's inbox. ANYTHING ELSE?Yesterday, Russian hackers leaked the medical records of US Olympic athletes…including Serena Williams and Simone Biles. These records show that both ladies got the OK from officials to use banned drugs for medical reasons. The hackers said these records proved the athletes played "well but not fair." Reminder: dozens of Russian athletes were banned from Rio thanks to a state-sponsored doping scandal. Not the same thing. theSKIMMMany think all of these hacks are aimed at hurting the credibility of the US on the world stage. And the idea that Russia – a major geopolitical player – may be trying to manipulate the credibility of the US presidential race has some wondering when and how the US will respond.
Philippe J DEWOST's insight:
Of USA, Russia, elections and hackers : interesting though not totally reassuring read
French newspaper “Le Monde” just published an article confirming that the US/NSA indeed hacked the Élysée Palace in 2012. ‘Quantum Insert’ has been used to hack the machines. This type of attacks was used in the GCHQ/NSA operation against employees of the Belgian telecom Belgacom (renamed Proximus today).
The malware was detected in May 2012 — between the two rounds of the Presidential election — and the help of the Technical Division of the DGSE was requested. Bernard Barbier — the Director of the DGSE Technical Division from 2006 to 2013 — came to the conclusion that the US/NSA was behind the hack.
The fact that the NSA spies on the French President has shocked a few people but Barbier is not too surprised. “In the Intelligence World, you have some allies. You don’t have friends.”
Philippe J DEWOST's insight:
"In intelligence world, you have some allies. You don't have friends" - Interesting reading on what happened 4 years ago, hoping lessons have been learned, as well as some interesting thinking about how to team up with some allies in scaling capacity. There is now a way, thanks to Ed Snowden, to detect "quantum insert" attacks : https://www.wired.com/2015/04/researchers-uncover-method-detect-nsa-quantum-insert-hacks/ |
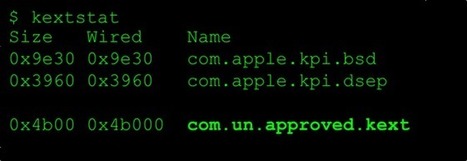
With each new release of macOS, Apple introduces new 'built-in' security enhancements...and macOS High Sierra (10.13) is no exception. In this blog post we'll take a brief look at High Sierra's somewhat controversial "Secure Kernel Extension Loading" (SKEL) feature. Unfortunately while wrapped in good intentions, in it's current implementation, SKEL merely hampers the efforts of the 'good guys' (i.e. 3rd-party macOS developers such as those that design security products). Due to flaws in its implementation, the bad guys (hackers/malware) will likely remain unaffected. While many respected security researchers, system administrators, and macOS developers have voiced this concern, here we'll prove this by demonstrating a 0day vulnerability in SKEL's implementation that decisively bypasses it fully:$ kextstatIndex Refs Size Wired Name 1 90 0x9e30 0x9e30 com.apple.kpi.bsd2 8 0x3960 0x3960 com.apple.kpi.dsep...130 0 0x4b00 0x4b000 com.un.approved.kext Documented in Apple's Technical Note TN2459, Secure Kernel Extension Loading, is "a new feature that requires user approval before loading new third-party kernel extensions." Other good overviews of SKEL include:"Kextpocalypse - High Sierra and Kexts in the Enterprise""Kernel extensions and macOS High Sierra"While we might initially assume that that the main attack vector SKEL attempts to thwart is the (direct) loading of malicious kernel extensions (i.e. rootkits), I believe this is not the case. First, observe that (AFAIK), we have yet to see any signed kernel-mode macOS malware! Since OS X Yosemite, any kexts have to be signed with a kernel code-signing certificate. And unlike user-mode Developer IDs, Apple is incredibly 'protective' of such kernel code-signing certificates - only giving out a handful to legitimate 3rd-party companies that have justifiable reasons to create kernel code. As security features are often costly to implement, they are generally introduced to reactively address widespread issues. (Unless they are introduced as a control mechanism, under the guise of a 'security feature' (*cough cough*)).
Philippe J DEWOST's insight:
Cupertino listens I hope
The ‘creator’ of Bitcoin, Satoshi Nakamoto, is the world’s most elusive billionaire. Very few people outside of the Department of Homeland Security know Satoshi’s real name. In fact, DHS will not publicly confirm that even THEY know the billionaire’s identity. Satoshi has taken great care to keep his identity secret employing the latest encryption and obfuscation methods in his communications. Despite these efforts (according to my source at the DHS) Satoshi Nakamoto gave investigators the only tool they needed to find him — his own words.
Using stylometry one is able to compare texts to determine authorship of a particular work. Throughout the years Satoshi wrote thousands of posts and emails and most of which are publicly available. According to my source, the NSA was able to the use the ‘writer invariant’ method of stylometry to compare Satoshi’s ‘known’ writings with trillions of writing samples from people across the globe. By taking Satoshi’s texts and finding the 50 most common words, the NSA was able to break down his text into 5,000 word chunks and analyse each to find the frequency of those 50 words. This would result in a unique 50-number identifier for each chunk. The NSA then placed each of these numbers into a 50-dimensional space and flatten them into a plane using principal components analysis. The result is a ‘fingerprint’ for anything written by Satoshi that could easily be compared to any other writing.
Philippe J DEWOST's insight:
Using the trove of data collected any millisecond around the whole globe, the #NSA can actually identify anybody and remove any mask. 
Philippe J DEWOST's curator insight,
August 29, 2017 4:53 AM
The NSA can actually identify anybody... with style
At midnight, a week before last Christmas, hackers struck an electric transmission station north of the city of Kiev, blacking out a portion of the Ukrainian capital equivalent to a fifth of its total power capacity. The outage lasted about an hour—hardly a catastrophe. But now cybersecurity researchers have found disturbing evidence that the blackout may have only been a dry run. The hackers appear to have been testing the most evolved specimen of grid-sabotaging malware ever observed in the wild.Cybersecurity firms ESET and Dragos Inc. plan today to release detailed analyses of a piece of malware used to attack the Ukrainian electric utility Ukrenergo seven months ago, what they say represents a dangerous advancement in critical infrastructure hacking. The researchers describe that malware, which they’ve alternately named “Industroyer” or “Crash Override,” as only the second-ever known case of malicious code purpose-built to disrupt physical systems. The first, Stuxnet, was used by the US and Israel to destroy centrifuges in an Iranian nuclear enrichment facility in 2009.The researchers say this new malware can automate mass power outages, like the one in Ukraine’s capital, and includes swappable, plug-in components that could allow it to be adapted to different electric utilities, easily reused, or even launched simultaneously across multiple targets. They argue that those features suggest Crash Override could inflict outages far more widespread and longer lasting than the Kiev blackout.“The potential impact here is huge,” says ESET security researcher Robert Lipovsky. “If this is not a wakeup call, I don’t know what could be.”The adaptability of the malware means that the tool poses a threat not just to the critical infrastructure of Ukraine, researchers say, but to other power grids around the world, including America's. “This is extremely alarming for the fact that nothing about it is unique to Ukraine,” says Robert M. Lee, the founder of the security firm Dragos and a former intelligence analyst focused on critical infrastructure security for a three-letter agency he declines to name. “They’ve built a platform to be able to do future attacks.”BlackoutLast December's outage was the second time in as many years that hackers who are widely believed—but not proven—to be Russian have taken down elements of Ukraine's power grid. Together, the two attacks comprise the only confirmed cases of hacker-caused blackouts in history. But while the first of those attacks has received more public attention than the one that followed, the new findings about the malware used in that latter attack show it was far more than a mere rerun.Instead of gaining access to the Ukrainian utilities’ networks and manually switching off power to electrical substations, as hackers did in 2015, the 2016 attack was fully automated, the ESET and Dragos researchers say. It was programmed to include the ability to “speak” directly to grid equipment, sending commands in the obscure protocols those controls use to switch the flow of power on and off. That means Crash Override could perform blackout attacks more quickly, with far less preparation, and with far fewer humans managing it, says Dragos’ Rob Lee.“It’s far more scalable,” Lee says. He contrasts the Crash Override operation to the 2015 Ukraine attack, which he estimates required more than 20 people to attack three regional energy companies. “Now those 20 people could target ten or fifteen sites or even more, depending on time.”Like Stuxnet, attackers could program elements of Crash Override to run without any feedback from operators, even on a network that’s disconnected from the internet—what Lee describes as a "logic bomb" functionality, meaning it could be programmed to automatically detonate at a preset time. From the hacker’s point of view, he adds, “you can be confident it will cause disruption without your interaction.”Neither of the two security companies knows how the malware initially infected Ukrenergo. (ESET, for its part, notes that targeted phishing emails enabled the necessary access for the 2015 blackout attack, and suspects the hackers may have used the same technique a year later.) But once Crash Override has infected Windows machines on a victim's network, researchers say, it automatically maps out control systems and locates target equipment. The program also records network logs that it can send back to its operators, to let them learn how those control systems function over time.
Philippe J DEWOST's insight:
Interesting analysis of how "Crash Override" put the Ukrainian Power Grid on its knees last Christmas. This "Stuxnet 2.0" looks scary both from a technological and geopolitical point of view. #BabelMinuteZero
Dominique Ristori, European Commission, Director-General for Energy
Mr Ristori welcomed the speakers and the audience and thanked Mr Del Fante and Terna for hosting this important event. He stressed that we have to speak about one of the most important issues regarding energy and security. Additionally, the Ministerial Meeting of G7 will take place in Rome 9-10 April. Europe should not be seen as followers, but as leaders. In this context Mr Ristori passed two main messages.
First, cybersecurity and energy security go hand in hand and require a common approach of the energy and digital worlds. They are two sides of the same coin. Energy is vital for all our all economic and human activities. Ensuring energy security is one of the key European energy policy priorities. There is a clear need to increase the capacity to work together. This is an issue of international interest to accelerate the preparation for adequate response to these threats.
Secondly, we need to develop a cyber security response covering all stages of the energy cycle. Priority has to be given to all aspects of the energy grid – transmission and distribution grid. We need an EU power grid prepared to withstand any cyber-attack. We will examine all challenges, having all priorities in mind and build a bridge in this context between Energy Union and Digital Single Market.
Roberto Viola, European Commission, Director-General for Communications Networks, Content & Technology
Mr Viola welcomed speakers and audience and thanked Mr Del Fante for hosting the event. He stressed the importance of cyber security in energy for our society. He reminded the signing of the European Treaties 60 years ago in Rome, starting from a steel and coal Community and being also a community of digital services today. He underlined that there would not be any digital services without energy, and that 8 % of the US energy bill today is used for data centres. In 10 years from now, the energy bill for the US and Europe will be more than 50% for digital devices. Digital needs energy and energy needs digital. Mr Viola linked the digital autonomous driving to energy through e-mobility and stressed that the concept of industry 4.0 has a clear link to energy. He also pointed out the importance to work together on digital skills which are also needed in the energy sector.
Mr Viola explained that cyber security is key in the energy and transport sectors. The cyber risks for these sectors have to be prevented as the consequences could be devastating to our society. We have to take this discussion seriously and cooperate together, and the NIS directive is the key mechanism for such cooperation. In the next two years , the implementation of this directive will translate in various actions. The most important one is cooperation. This year, the main focus lies on the renewal of the ENISA mandate, on certification and labelling, internet of things and the revision of the EU Cyber Security Strategy.
Matteo Del Fante, CEO Terna Rete Elettrica, Italy
Mr Del Fante thanked the Directors General and welcomed the participants. He said the meeting was an important initiative and discussion, and that he was very happy to have Terna experts on cyber security along. His main lines were: The transport sector, the health sector and the energy sector are facing digitalisation. Cyber security has to be one of the top priorities. The multiplication of access points in our networks is creating the need for sharing information and best practices and strong links between companies and states. Terna in collaboration with institutions play a role at national level, but the challenge is a European one. The forum of today is very important. It might maybe easier to tackle and discuss at national level, as well as defending and share best practices at national level, but best practices have to be shared at European level. Establishing new standards and adopting new solutions have to be addressed at European level. Mr Del Fante welcomed Mr Laurent Schmitt and emphasised the importance of ENTSO-E. Referring to Terna, he explained that Terna has a security operational centre which is extremely well regarded, Terna does security monitoring of tangible and intangible assets, monitor incident response activities and continuously monitor the most suitable cyber defence technologies used in Italy and around the world. In order to guarantee the best coverage of Terna assets, information security at Terna defines specific guidelines and strategies in addition, to identifying correct behaviour of all employees. Terna does a lot of simulations of possible cyber intrusions. During 2016, the Terna information security competence centre has completed a review of the information security policies and information security framework aiming for gradual alignment with the NIS directive. Terna has adapted an operational program and information risk management an RIM under the direction of the chief security officer. The coordination belongs to the corporate protection directorate, which has allowed Terna to identify the top cyber security risks. There is a daily cyber report, and whenever there is an event at European level, it gets analysed and a simulation at the Terna network is launched. To conclude, Mr Del Fante emphasised that cyber security is a key issue for critical infrastructures and that Terna is identified in Italy as a critical operator. Mr Del Fante stressed the importance of putting cyber security considerations already at the planning stage of industrial plans – thus cyber security has to be embedded in R&D.
Guido Bortoni, President Autorità per l'Energia Elettrica e il Gas, Italy
Mr Bortoni emphasised that the security of power systems is highly complex and must be addressed without simplification. The Italian experience has brought some distinctions that are useful to be recalled. Firstly, it is important to distinguish between system adequacy and security. Adequacy has a preventive character and relates to the procurement of resources up to the extend to cover demand to a reasonable level. Security is the capability of the system to stay on, or rather to serve according to certain standards. Concerning risk management towards a secure system, it requires to manage enough resources in a preventive manner, along with operating the system by exploiting in a corrective manner the available resources. 100% security does not exist in nature. The concept of resilience is the capability of the system to serve or to recover from failures to a new equilibrium state. The main element of the resilient power system is the flexibility to adapt to an emergency beyond the security level to get services running or quick-start the service as quick as possible. Adequacy is guaranteed only by preventive measures, security by both – preventive and corrective measures, whereas resilience is merely corrective. For security the proper balance between preventive and corrective measures can only be assessed by the relation to the risk – to the two components of the risks, on the one hand the probability to occur and on the second hand the magnitude of the impact. We need a correct balance upon security that can be only realised with a proper risk assessment that goes beyond regulatory competences and requires further considerations at various political levels. Cyber security is a direct consequence of the present evolution of our power systems, especially in Europe. For the second roll-out of smart meters in Italy (starting end of 2017), cyber security is of utmost relevance. Cyber security introduces a new order of costs, but it also brings benefits to the system. Cyber security is founded on training and know-how of dedicated people involved. To conclude, traditional power systems have always been interconnected among themselves, digital or cyber is a strong dimension, which introduces the need for a cross sectorial connection between power and ICT (information and Communication Technologies).
Massimo Gaiani, Director General, Ministry of Foreign Affairs, Italy
Mr Gaiani stressed that our society is more complex, interconnected and digitalised. All these factors increase the flexibility, the performance of the system, while making it also more fragile and vulnerable. This applies to all sectors, but the energy sector plays a crucial role in our economy and our lives such that energy is vital to the functioning of the system as a whole. Security of infrastructures is a key element of security of supply. Electricity plays a central role, but security of supply must play an important role for all supply carriers including oil and gas pipelines. Cyber security is nowadays not to be merely understood as a defensive mechanism, but as a policy, a behaviour attitude that governments, private entities and citizens have to comply with. Working together is the only possible way for government and private undertakings to effectively address cyber issues. Cyber security is one of the main concerns to be talked by the Energy Union. A pan-European commitment is essential to mitigate cybercrime. Cybersecurity should become part of the most important fora, including IEA, G7 and G20. There is not enough awareness on cyber security, thus training and education must become part of effective forward looking prevention policies in the cyber space.
Rita Forsi, Director General, Ministry of Economic Development, Italy
Mrs Forsi – as the head of the Italian CERT – started with the challenges of cyber security in energy. Cyberattacks are increasingly targeting the energy sector, and we do not know who will be next and what attack will be used. Cyber-attacks could have catastrophic consequences. In 2014 in Rome, it was recalled amongst G7 members to protect the critical energy infrastructures, including from cyber-attacks. The G7 in Hamburg agreed to improve the commitment on cybersecurity in the energy sector. Last year the G7 in Japan stated that cyber security has become a crucial element for guaranteeing security of energy supply. The G7 countries will facilitate cross-regional and cross sectoral networking on cybersecurity in the energy sector among relevant stakeholders, including national CERTS/CSIRTS. G7 countries announced to share threat information and to cooperate for the improvement of cyber security for critical infrastructure with a specific reference to the energy sector. This commitment is perfectly in line with the NIS Directive. The development of energy specific cyber security solutions and defensive practices are essential. National security, economic prosperity, the well-being of our citizens depend on reliable energy infrastructure. The government should support private companies and private companies should take more res pons ibility at private-public partners hips . The ris k of human factors is of utmos t importance when it comes to cyber security. Therefore it is crucial for companies to invest in training of staff. The European Union has a key role to play to take cyber security forward.
Juhan Lepassaar, Head of Cabinet for European Commission Vice- President Andrus Ansip, Digital Single Market
Mr Lephassar gave an overview of the Commission initiatives in the field of cybersecurity highlighting the importance to address cybersecurity in a coherent manner. For this purpose, DG CNECT and DG ENER are cooperating on a number of initiatives related to cybersecurity in the energy sector (e.g. NIS Directive, Energy Expert Cyber Security Platform – Expert, Smart Grid Task Force). He finally announced the review of the EU Cybersecurity Strategy later this year that is expected to include the review of the ENISA mandate and a proposal on ICT security certification, as well as a trusted IoT (Internet of Things) label.
Session 1 - Panel: Expectations from energy operators on cyber security What role for Member States and Europe? Moderator: Laurent Schmitt, Secretary-General ENTSO-E
The European grids are heading forward on digitalisation, and ENTSO-E is committed to support this trend. The attacks today are of different nature, not only coming from individuals but also from organised entities. A lot of work has already been done by the Smart Grids Task Force. European grids are largely interconnected, thus we have to think on a broad basis.
Boris Schucht, CEO at 50Hertz, Germany 50Hertz is one of the four Transmission System Operators (TSOs) in Germany located north- east of Germany, the region with the highest amount of intermitted renewable energies in the world. 50% of the consumption are covered by solar and wind. This region is also a big export region. In Germany there are 1.7 Million decentralised installations. System security has four challenges. - The first challenge is the real time IT and the SCADA system, which is physically disconnected thus not the biggest challenge. Every TSO in Europe has a different real time IT, thus if there is a problem another TSO can support and take over. We are on the right way with the ICT certification and policies that increase the awareness. - The Second part is the business IT. Due to the liberalised market, all schedules are made via the internet. It is a decentralised world where a central dispatch would still work today, but the future will raise challenges (in case the internet would be down). In the year 2012, a dDoS1 attack hit 50Hertz , blocking the internet access for two weeks. This was not the biggest problem, as they were well prepared. Mr Schucht drew the attention to a recent article he read on the hacking of Tesla. As he drives an electric car and uses remote control from his phone also for charging, he is concerned that this application could get hacked, especially if the number of electric cars increases. If hackers have control over the remote control and charge all cars at once, we will have a problem. - The major challenge will be all the applications. He does not think that the smart meter will be the main problem. The question is what happens behind the meter, while increasing appliances will have internet connection (like TVs). For example Samsung can switch off all their applications – thus it is hard to control. Not all attacks are unfriendly, but may stem from simple mistakes. He used the example of the converters of SME, which shut off at 50,2 hertz, not at 52 hertz as they should. This programming mistake was only found after 5 years. - The fourth challenge mentioned by Mr Schucht is data protection. The costumer is the owner of the data and it must be clear who collects the data. Nobody should be allowed to use the data for additionally businesses. He concluded with the request to the Commission that while the ongoing certification procedures are good, data protection needs more clarification regarding who can use what data and the big question is the growth of de-central devices behind the meter. The political attention needs to focus on this question to raise society awareness and to call upon the market participants to find solutions.
Philippe Monloubou, CEO of ENEDIS, France Mr Monloubou explained that risk is inclusively adapted to business and the new boarder of our business (compared to 60 year ago) is cyber security. It is not only a threat, but also a huge opportunity. We have to integrate all dimensions of cybersecurity in our business as it is our core business. We need to address cybersecurity from an offensive perspective, not from a defensive one. In France there are 400.000 photovoltaic (PV) generators on the network. The question is to be able to integrate data, data management and IT systems. Why is it our core business? Nowadays, Distribution System Operators (DSOs) are totally involved in real time, thus time-to-market. From a customer point of view, the way the DSO rolls out smart meters, should be the same the DSO addresses cyber security. Thus it is a DSO core business responsibility. As the president of the Smart Grids association, Mr Monloubou emphasised that this is a worldwide challenge. Other countries are waiting for our knowledge, but we have to be fast as there are also many competitors. We have to address the topic very quickly. We need new skills, certification, innovation, cooperation and talents to be able to address these new markets. Mr Monloubou stated that cyber security can also create jobs and that it needs to be understood as a part of the core business.
Q&A - Session Erikson: Certification is one way to ensure more resilience, but it does not solve the whole problem. What about certification and formal device management? Regarding the 400.000 PV generators in France, would it not be that your main assets coming forward would be an intelligent trusted cloud software, etc. that would control these generators? Answer: Device management does not solve the problem in itself; it only adds another level as a kind of responsible in-between. There is no clear view yet, how this will look in the future. Certification slightly increases the level, but does not solve it completely. We will need to have more control power and that needs to be as safe as possible, e.g. the internet must be completely separated. At the end of the day, it will be a combination of different measures. The speakers answered that there is also a challenge of sharing of own generation amongst neighbours. Cloud system could be a solution, because they are better than the existing systems. There will be cloud solutions, but cloud systems are not only a French consideration. What is the importance of data scientists and modelling? Sharing information in the energy sector like it happens in the aerospace sector and if that would be a solution. Answer: Sharing information is no question anymore, the awareness is there and we have to address it through innovation. The more IT specialists we have, the more hackers we have as well. "Competition on ideas" was raised as a good example – thus to raise standards, but also leave some ideas. Symantec: the ability to have access and share the information from outside Europe is extremely critical. Answer: TSO is implementing a new real time IT from Siemens, also the Californian DSO bought this real time IT. In some places penetration tests are conducted, providing capable hacking teams two weeks to get into the system. This approach means companies are on the right track, but this does not mean that they are 100% protected. IoT also means devices on our own networks. Conclusions Mr Laurent Schmitt: 2-3 years ago, cyber security was more a R&D innovation topic. This has changed now. Mr Schmitt also raised the importance of having in the near future a cyber security network code, which would be joint for DSOs and TSOs and which would basically fit all IoT devices which are critical for energy and which would clearly define what is a requirement from physical energy security point of view.
Session 2: Energy – Key elements for a Cyber Security Strategy Stephan Lechner, Director Euratom, Moderator
Hubert Tardieu, CEO advisor at Atos, France Mr Tardieu presented the technology supplier angle. All systems are taking into account the IT (information Technologies) and the OT (Operation Technologies) world. It is a very serious matter to shut 8 Million of smart meters by an IT command. From purely predictive (where we still are) we will go progressively into the prescriptive world where we will be able to intervene to the final systems. The first point Mr Tardieu stresses is that distributed architecture is not nice to have, but is becoming a must. As a second point he mentioned that it forces to mix the culture of the IT people and the culture of the OT people. Eventually, the OT people will win because they are closer to the real system. Atos is working closely with Siemens on a SOC (security operations centre) approach, which they manage now to regroup, meaning that the same security management is applicable to both the IT SOC and the OT SOC.
Bernd Kowalski, Head of Department, BSI, Germany Mr Kowalski emphasised that regulation plays an important role to push cyber security in all vertical sectors. Germany is one of the first nations that has already implemented the NIS directive, including the energy sector. The recommendations to the Commissions are to apply principles of security and privacy by design. There is no time to wait, as afterwards the costs will be higher. It is important not to only implement the NIS directive, but to connect to other existing regulations like the eIDAS regulation. We should also use the existing European standards. This would also be cost- effective. The European Commission should encourage the Member States to set up appropriate regulatory frameworks for the energy systems, to have agreements on basic principles using standards that already exist for long time. 30 years ago, a cyber security certification mechanism was created, but the European Commission forgot about this. Twelve Member States are using cyber security certification mechanisms nowadays and have no interest in a fragmented market. The BSI and the German Ministry would like to support the European Commission in bringing cyber security to the energy system.
Philippe Dewost, Deputy Director Investments for the Future Program @ Caisse des Dépôts, France He observes that in this digital space, speed is of the essence, and that we hence will not be able to cope with cybersecurity challenges if we do not accept the shift from centering cooperations around the most powerful (measured by relative GDP or population weight), to following the fast and nimble runners when it comes to s tructuring joint initiatives . He then noted that decentralisation is a key and core force in technology development : IT is shifting from the core to the edges, Blockchain technologies allows decentralization of transactions and assets tracking, while security now combines thickening dungeon walls with detecting and filling breaches as fast as possible and even sometimes from “outside” the systems: a recommendation to the European Commission could be thus to change the approach legally framing hackers turned into “white hats” and securing their legal. The second advice he gave is to think exponential at any decision level as Moore’s Law always leads us to overestimate the short term and underestimate the mid/long term when designing cybersecurity policies especially for IoT and industrial systems. Thirdly, we should no longer be naïve: cybersecurity often relies on mastering the full stack down to the silicon as evidenced by Russian and Chinese efforts to regain independence in terms of chip design. Hardware and microchip development could be mastered by Europe especiall y if we leverage Open Source architectures such as Risc-V. Regarding cyber security and energy infrastructures, he acknowledged this joint DG Energy / DG CNCT approach as these two domains can no longer remain disjointed, and raised Blockchain as an example and promising technology for operating and securing transactions across microgrids. His final recommendation was to invest in research and development, like blockchain or homomorphic encryption, and to visibly recognize such fields as EU wide sovereign priorities. He estimated that approximately €500 M of R&D funding should be allocated to Blockchain research over the next 3 years, combined with an equivalent €500 M to be deployed through investment vehicles in European Blockchain startups.
Q&A – session:
1) How far can we do a one-size-fits-all approach in terms of certification?
3) Mrs Spanou emphasised that the European Commission has not forgotten of certification and is currently working on it.
4) Luigi Rebuffi presented ECSO and the cPPP (contractual Public-Private-Partnership on cyber security).
5) Accenture: What is your point of view that people far away from the market work on frameworks? We need education also at CEO level. The workshop on Economy of data was mentioned and we need to be able to explain the concept to our CEOs.
6) Bto: Does it make more sense to cooperate more? It is not about the regulation, but who is enforcing the regulation. Talent should always come first, as small teams can make profound changes.
Summary - Stephan Lechner, Director Euratom, Moderator Mr Lechner summarised the event, underlining that cyber security never stops and we need to stay ahead of the game. He recalled key statements of the speakers: Director General Mr Ristori emphasised that Europe should take the lead and not just follow. Director General Mr Viola said that digital needs energy and energy needs digital. Mr Del Fante told that security needs to be integrated. Mr Bortoni said risk is something that needs to be balanced. Mr Gaiani stressed the international dimension. Mrs Forsi underlined the value of sharing. Mr Lepassaar stated that collaboration is the most important tool. Mr Schucht underlined that viruses could already come from the suppliers and that there are more devices behind the meter moving at a different pace than the part before the meter. The legacy is in and we got all the fast moving digital parts not being able to be formalised certified. The DSO perspective was similar, emphasising that the core business is cyber security. Atos said that we have prescriptive technologies coming in which means IT (information technology) ruling the OT (operations technology) of the grid. Mr Kowalski recalled that the technology solutions are already around and cyber security in the grid is not a research topic any more. Mr Devost emphasised the speed of digitalisation, Mr Lechner stated that security is a process, and that the issue of cyber security is here to stay. To conclude he identified three findings: firstly, the energy sector has its particularities. In our energy networks, traditional industrial control systems are being more and more connected, exposing them to new cyber threats. In addition, new and smart technologies are pushing in at the consumer end, and not all of them are designed with cyber security in mind. This combination of legacy and future technologies requires specific solutions in the energy system that cannot be copied from other areas with different needs (e.g. the internet). A concrete action on certification was also called. Secondly, we need to realise the importance of information technology suppliers. Both, power grid operators and consumers are bound to information technologies that are typically not produced by themselves, and very often originate from outside Europe (US, South-East Asia). Suppliers of information technologies to the EU energy system must be bound to clear obligations to provide their products and services at a well-defined, high level of cyber security. Thirdly, we need to strike a good balance between cyber security, data protection and economic growth. Cyber security is not a purpose of its own, but is required to create business opportunities, jobs and growth. Cyber security and data protection requirements must not hinder innovation or prevent businesses from settling in Europe, as data analysis is at the core of the future automated and smart energy system. The European market must be secure without decreasing competitiveness or banning business models based on big data analysis.
Mr Dominique Ristori, European Commission Director-General for Energy and Mr Roberto Viola, European Commission Director-General for Communications Networks, Content & Technology closed the meeting.
Philippe J DEWOST's insight:
At least there is growing sensitivity and increasing focus.
A new attack that uses terrestrial radio signals to hack a wide range of Smart TVs raises an unsettling prospect—the ability of hackers to take complete control of a large number of sets at once without having physical access to any of them.
Philippe J DEWOST's insight:
Smart now means prone for hacking. In the present case, "The infection was also able to survive both device reboots and factory resets". Scary.
Thiel's upstart has the info needed for a Muslim registry — Silicon Valley engineers will protest outside the headquarters of data analytics firm Palantir Technologies Wednesday, demanding greater transparency over how its databases may be used by the incoming Trump Administration."Palantir and Peter Thiel should be held accountable for potentially enabling Trump's efforts to deport three million immigrants and create a Muslim database," reads the Dobetter.tech website set up to organize the protest.Peter Thiel is cofounder of CIA-backed Palantir, and has become the main tech advisor to president-elect Trump following his public backing of the controversial businessman during the presidential campaign.Following Trump's promises to create a registry of Muslims living in America and persistent claims that he will put greater surveillance on them as a group – as well as prevent Muslims from certain countries entering the country at all – engineers in California are worried that Palantir's existing relationships with the federal authorities will be used to further those goals.As the website notes, Palantir is a highly sought-after company in Silicon Valley. "The company regularly beats out Google and Facebook when it comes to hiring Stanford's top CS students," it notes, adding that it "currently represents the gold standard of software engineering and data science rigor in Silicon Valley."However, two databases that the company runs and manages for the federal government have given cause for alarm.
Philippe J DEWOST's insight:
What about Palantir outside of the USA, like in France for instance ?
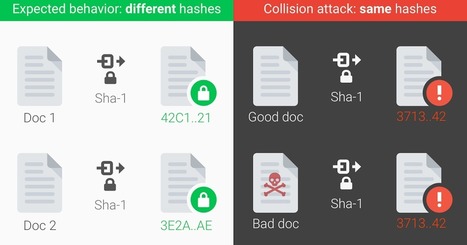
Cryptographic hash functions like SHA-1 are a cryptographer’s swiss army knife. You’ll find that hashes play a role in browser security, managing code repositories, or even just detecting duplicate files in storage. Hash functions compress large amounts of data into a small message digest. As a cryptographic requirement for wide-spread use, finding two messages that lead to the same digest should be computationally infeasible. Over time however, this requirement can fail due to attacks on the mathematical underpinnings of hash functions or to increases in computational power.
Philippe J DEWOST's insight:
This was anticipated yet the fact that it did happen is still a significant milestone. Hopefully we have SHA-256 and the question is now to frame how long this hash function will remain uncompromised. 
Philippe J DEWOST's curator insight,
February 23, 2017 10:11 AM
This was anticipated yet the fact that it did happen is still a significant milestone. Hopefully we have SHA-256 and the question is now to frame how long this hash function will remain uncompromised.
Could Samsung be the first big defection from ARM since the SoftBank takeover?
Philippe J DEWOST's insight:
X86 architecture gave Intel dominance of the large PC market before hitting the smartphone wall. Cortex architectures gave ARM dominance of the much larger smartphone market before hitting the SoftBank wall. RISC-V may be the next architecture for the even much larger IoT market (in volume at least). Intel is a US corporation, ARM was once a british company now under japanese flag : the nice thing with RISC-V is that it is an independent, open source, and royalty free architecture. This will have consequences over the next decade in the computing race between the US and Asia (think Loogson and now ARM), and may be an opportunity for Europeans to step in and avoid to remain as "The Pacific" of cyber tests. 
Philippe J DEWOST's curator insight,
November 30, 2016 1:19 AM
X86 architecture gave Intel dominance of the large PC market before hitting the smartphone wall. Cortex architectures gave ARM dominance of the much larger smartphone market before hitting the SoftBank wall. RISC-V may be the next architecture for the even much larger IoT market (in volume at least). Intel is a US corporation, ARM was once a british company now under japanese flag : the nice thing with RISC-V is that it is an independent, open source, and royalty free architecture. This will have consequences over the next decade in the computing race between the US and Asia (think Loogson and now ARM), and may be an opportunity for Europeans to step in and avoid to remain as "The Pacific" of cyber tests.
The flood of “fake news” this election season got support from a sophisticated Russian propaganda campaign that created and spread misleading articles online with the goal of punishing Democrat Hillary Clinton, helping Republican Donald Trump and undermining faith in American democracy, say independent researchers who tracked the operation. Russia’s increasingly sophisticated propaganda machinery — including thousands of botnets, teams of paid human “trolls,” and networks of websites and social-media accounts — echoed and amplified right-wing sites across the Internet as they portrayed Clinton as a criminal hiding potentially fatal health problems and preparing to hand control of the nation to a shadowy cabal of global financiers. The effort also sought to heighten the appearance of international tensions and promote fear of looming hostilities with nuclear-armed Russia. Two teams of independent researchers found that the Russians exploited American-made technology platforms to attack U.S. democracy at a particularly vulnerable moment, as an insurgent candidate harnessed a wide range of grievances to claim the White House. The sophistication of the Russian tactics may complicate efforts by Facebook and Google to crack down on “fake news,” as they have vowed to do after widespread complaints about the problem. There is no way to know whether the Russian campaign proved decisive in electing Trump, but researchers portray it as part of a broadly effective strategy of sowing distrust in U.S. democracy and its leaders. The tactics included penetrating the computers of election officials in several states and releasing troves of hacked emails that embarrassed Clinton in the final months of her campaign.
Philippe J DEWOST's insight:
We can expect France to be next on the list. We better get prepared to this.
Society doesn't work without trust Human being is the only species with trust. We trust hundreds of strangers without even thinking about it.
How do we enable trust?
How does security enable trust. How do we induce trust?
Trust: confidence, consistence, compliancy. It's about cooperation.
All complex ecosystems require cooperation. In any cooperative system, there is a way to subvert the system for personal interests.
These are called defectors in game theory. They are parasites. They can survive if they are contained. If too many parasites the body dies and the parasites die too.
Society doesn't work if everybody steals. Security can be defined as a tax on the honests.
Social species: individual competition plus group competition.
Security is to keep defection level at an acceptable minimum that is not zero.
NSA defector Edward Snowden raises moral debates but the point is that he is a defector. How group enforce the norm. Even mafia groups. It is about societal pressure.
4 types of societal pressure
Example: eBay feedback mechanism is a reputational security system that worked remarkably for years as the main security system.
How does technology affects us? Technology is what allows society to scale. It is neutral. Filesharing: social pressure vs technology Attackers have a first mover advantage and are more adaptive.
Mid 90's Internet going commercial: hackers used it immediately while it took 10 years to the police to figure out how to address it Such delay is the main security gap
Our society is at a point where technology is faster than social changes which means that the security gap widens. Before: buy this and you'll be safe Now: when you've been attacked, please talk to us and we'll help
It's the antivirus history Smart paradigm: detect unknown viruses including false positives Stupid paradigm: check for signatures and update once or twice a day
The stupid paradigm seems to have won.
So technology will always favor defectors? True, but large organizations can now use technology in a much more effective manner. Our society has the most technology and the largest institutions.
The battle is amplifying between agile defectors and slower yet more effective institutions. Losers are those of us in the middle.
To him it is not even clear how there is a balance nor how it will evolve.
As a conclusion
Philippe J DEWOST's insight:
Digiworld Summit 2016 is on "The Digital Trust Economy" - Time to remember Bruce Schneier's remarkable words of wisdom at USI 3 years ago - I have added my on the fly notes to the video link for those who prefer reading. 
Philippe J DEWOST's curator insight,
November 15, 2016 1:59 AM
Digiworld Summit 2016 is on "The Digital Trust Economy" - Time to remember Bruce Schneier's remarkable words of wisdom at USI 3 years ago - I have added my on the fly notes to the video link for those who prefer reading.
C'est un risque qui devient de plus en plus courant à mesure que les voitures embarquent encore un peu plus d'électronique : le piratage à distance. Ce lundi 19 septembre, le constructeur de voiture électriques Tesla en a fait l'expérience avec la prise de contrôle de sa Model S par une équipe d'informaticiens chinois.Dans une vidéo postée sur Youtube par l'équipe du Keen Security Lab, on découvre avec quelle facilité les informaticiens ont pu contrôler presque l'ensemble des fonctionnalités de la voiture, des clignotants en passant par les sièges jusqu'à la pédale de frein.Cette démonstration est d'autant plus impressionnante que le contrôle de la voiture peut se faire même sur une très grande distance. Ainsi, si la majorité des tests se déroulent alors que l'équipe du Keen Security Lab se trouve à quelques mètres, les informaticiens ont pu actionner le frein de la Model S à 19 kilomètres de la voiture. Et ce sans allumer les lumières de freinage, ce qui démultiplie les risques de collision.
Philippe J DEWOST's insight:
L'enjeu de la voiture (autonome) connectée est, au-delà de la nécessaire sécurisation des OS embarqués, lié à la détection des failles zero-day et de la capacité de gérer une flotte et sa mise à jour. Tesla dispose d'une certaine expérience en la matière depuis plusieurs années et maîtrise en interne l'OS de ses véhicules, les zero-day bounties et les mises à jour à distance (ce qui n'était pas le cas de GM l'été dernier) : cela suffira-t-il ?
Google Play services need constant location info
Philippe J DEWOST's insight:
Sometimes the Trojan Horse isn't where you think...
|