Highly destructive malware creates "destructive events" at 3 Ukrainian substations.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
En créant OpenAI, une équipe de recherche à but non lucratif, Musk et Y Combinator espèrent limiter les risques de dérive en matière d’intelligence artificielle.Comme si le domaine de l’intelligence artificielle (IA) n’était pas déjà assez compétitif – avec des géants comme Google, Apple, Facebook, Microsoft et même des marques automobiles comme Toyota qui se bousculent pour engager des chercheurs –, on compte aujourd’hui un petit nouveau, avec une légère différence cependant. Il s’agit d’une entreprise à but non lucratif du nom d’OpenAI, qui promet de rendre ses résultats publics et ses brevets libres de droits afin d’assurer que l’effrayante perspective de voir les ordinateurs surpasser l’intelligence humaine ne soit pas forcément la dystopie que certains redoutent.
Philippe J DEWOST's insight:
Version française d'un article décrivant un des projets les plus ambitieux et les plus structurants du moment. Si comme je le vérifie chaque jour au contact des écosystèmes de la French Tech, "la seule limite est le talent", alors une telle démarche devrait nous inspirer en France et en Europe afin que nous ne soyions pas uniquement un "réservoir de talents" pour les unicornes américaines. Il me semble qu'il y a là une question de souveraineté...
*Update – Facebook has now restored the #OpISIS “Report ISIS Accounts” group without comment.Shortly before the massive coordinated terrorist attacks in Paris, which ISIS has claimed responsibility for, Facebook took down the primary Anonymous group responsible for unmasking and reporting thousands of social media accounts used by ISIS to spread propaganda and recruit.The main weapon used by ISIS to spread their extremist ideology has been social media, and regardless of your stance as to how the terror group was created or who created it, Twitter and Facebook have been the major tools for the growth of the Islamic State.In an effort to counter this massive ISIS social media presence, the Anonymous group Red Cult began an operation called #OpISIS as a means of combating the terrorist group in cyberspace.The idea that Facebook has removed a group calling itself “Report ISIS Accounts” is disconcerting and raises serious ethical questions. The Anonymous run group was removed from Facebook only hours prior to the Paris attacks, and the administrators from the group were banned.
Philippe J DEWOST's insight:
This is disturbing and raising many questions far beyond the influence of social networks in triggering mass emotional reactions such as the French flag overlay on profile pictures...
A system designed to reduce the number of casualties in terror attacks like the one of Paris on Nov…
This article focusses on attacks occurring in densely populated areas, in countries not in war situations, in countries with regulation forbidding possession and use of weapons by civilians. We address rampage attacks, were several independent teams of armed attackers scout the city, killing randomly, before targeting a location with a high number of potential victims. It can also apply, but with less impact, to situations where several team directly invest locations with high number of potential victims.A main hypothesis is that the perpetrators of the terrorist act pursue an objective of (i) maximum casualties and (ii) maximum communication impact. The second objective pushes them to create war-like situation in non-war zones, which generates a high number of crowdsourced images taken by the potential victims themselves. Those images are widely diffused on social media by their authors, which in turn creates a worldwide advertising for the events. This second objective is pursued with the rampage strategy were attackers show their face while they scout the city. The longest it lasts, the strongest is the impact on mainstream media such as television, and the highest the image impact on the general population.We believe that two main factors influence directly the number of casualties :Asymmetry of informationTime to counter-actionWe’ll cover both factors.
Philippe J DEWOST's insight:
Very pragmatic and interesting food for thought ... and for action #UnitedWeStand
Alors que les Etats recourent de plus en plus aux cyberattaques, l'encadrement de cette guerre électronique demeure flou, malgré des tentatives répétées pour le clarifier.Le ministère de la Défense récuse l’avoir organisé en urgence, mais ce colloque tombe à pic. Lundi et mardi, le nouveau site de Balard, «l’Hexagone», accueille une série de conférences sur le thème «Droit et Opex» (opérations extérieures, la guerre donc), autour de deux thèmes clés : la judiciarisation croissante des conflits et l’adaptation du droit aux nouvelles menaces, aux «zones grises». A l’instar des bombardements français en Syrie dont la légalité a soulevé de nombreuses questions.Ces bombardements se sont accompagnés d’actions d’un nouveau genre. Selon Le Monde, «une opération informatique du cybercommandement de l’état-major» a permis de «remonter jusqu’au groupe» visé. Soit une nouvelle application de la doctrine française en matière de «lutte informatique offensive», dans un cadre légal encore flottant.
Philippe J DEWOST's insight:
Lire "Babel Minute Zéro" peut aider à réfléchir à ces questions de doctrine et de souveraineté numérique.
From
qz
Sometimes old school is best. In today’s US Navy, navigating a warship by the stars instead of GPS is making a comeback.
Philippe J DEWOST's insight:
I served in the French Navy as navigation officer and learned how to use the sun and the stars to cross the atlantic ocean. At that time the first "portable" GPS were coming to market and they cost $3000 each. Interesting to see that the Navy of a cyber-superpower is reintroducing celestial navigation while almost every sailor now has a GPS in his/her pocket.
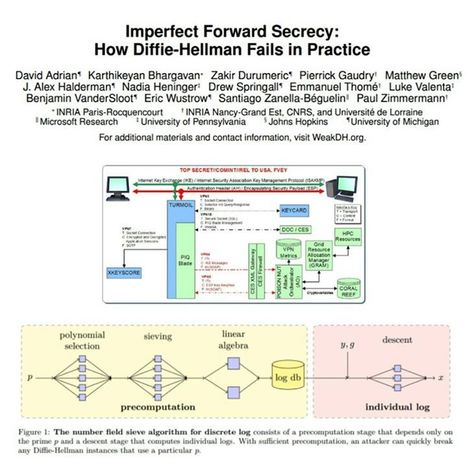
There have been rumors for years that the NSA can decrypt a significant fraction of encrypted Internet traffic. In 2012, James Bamford published an article quoting anonymous former NSA officials stating that the agency had achieved a “computing breakthrough” that gave them “the ability to crack current public encryption.” The Snowden documents also hint at some extraordinary capabilities: they show that NSA has built extensive infrastructure to intercept and decrypt VPN traffic and suggest that the agency can decrypt at least some HTTPS and SSH connections on demand. However, the documents do not explain how these breakthroughs work, and speculation about possible backdoors or broken algorithms has been rampant in the technical community. Yesterday at ACM CCS, one of the leading security research venues, we and twelve coauthors presented a paper that we think solves this technical mystery.
The key is, somewhat ironically, Diffie-Hellman key exchange, an algorithm that we and many others have advocated as a defense against mass surveillance. Diffie-Hellman is a cornerstone of modern cryptography used for VPNs, HTTPS websites, email, and many other protocols. Our paper shows that, through a confluence of number theory and bad implementation choices, many real-world users of Diffie-Hellman are likely vulnerable to state-level attackers. For the nerds in the audience, here’s what’s wrong: If a client and server are speaking Diffie-Hellman, they first need to agree on a large prime number with a particular form. There seemed to be no reason why everyone couldn’t just use the same prime, and, in fact, many applications tend to use standardized or hard-coded primes. But there was a very important detail that got lost in translation between the mathematicians and the practitioners: an adversary can perform a single enormous computation to “crack” a particular prime, then easily break any individual connection that uses that prime.
How enormous a computation, you ask? Possibly a technical feat on a scale (relative to the state of computing at the time) not seen since the Enigma cryptanalysis during World War II. Even estimating the difficulty is tricky, due to the complexity of the algorithm involved, but our paper gives some conservative estimates. For the most common strength of Diffie-Hellman (1024 bits), it would cost a few hundred million dollars to build a machine, based on special purpose hardware, that would be able to crack one Diffie-Hellman prime every year.
Would this be worth it for an intelligence agency? Since a handful of primes are so widely reused, the payoff, in terms of connections they could decrypt, would be enormous. Breaking a single, common 1024-bit prime would allow NSA to passively decrypt connections to two-thirds of VPNs and a quarter of all SSH servers globally. Breaking a second 1024-bit prime would allow passive eavesdropping on connections to nearly 20% of the top million HTTPS websites. In other words, a one-time investment in massive computation would make it possible to eavesdrop on trillions of encrypted connections. NSA could afford such an investment. The 2013 “black budget” request, leaked as part of the Snowden cache, states that NSA has prioritized “investing in groundbreaking cryptanalytic capabilities to defeat adversarial cryptography and exploit internet traffic.” It shows that the agency’s budget is on the order of $10 billion a year, with over $1 billion dedicated to computer network exploitation, and several subprograms in the hundreds of millions a year. Based on the evidence we have, we can’t prove for certain that NSA is doing this. However, our proposed Diffie-Hellman break fits the known technical details about their large-scale decryption capabilities better than any competing explanation. For instance, the Snowden documents show that NSA’s VPN decryption infrastructure involves intercepting encrypted connections and passing certain data to supercomputers, which return the key. The design of the system goes to great lengths to collect particular data that would be necessary for an attack on Diffie-Hellman but not for alternative explanations, like a break in AES or other symmetric crypto. While the documents make it clear that NSA uses other attack techniques, like software and hardware “implants,” to break crypto on specific targets, these don’t explain the ability to passively eavesdrop on VPN traffic at a large scale.
Since weak use of Diffie-Hellman is widespread in standards and implementations, it will be many years before the problems go away, even given existing security recommendations and our new findings. In the meantime, other large governments potentially can implement similar attacks, if they haven’t already.
Philippe J DEWOST's insight:
This is just an hypothesis, yet a rather fascinating and so far coherent one. It also shows that the weakest points in cryptography are not necessary in the protocols but rather in their implementation. Very interesting paper any way curated thanks to Clement Epie. |
Database configuration issues expose 191 million voter recordsA misconfigured database has led to the disclosure of 191 million voter records. The database, discovered by researcher Chris Vickery, doesn't seem to have an owner; it's just sitting in the public – waiting to be discovered by anyone who happens to be looking.What's in the database?The database was discovered by researcher Chris Vickery, who shared his findings with Databreaches.net. The two attempted to locate the owner of the database based on the records it housed and other details. However, their attempts didn't pan out, so they came to Salted Hash for assistance.Never one to shy away from a puzzle, I agreed to help. the best place to start looking was the database itself. That's when Vickery sent me my personal voter record from the database. It was current based on the elections listed. My personal information was accurate too. Vickery discovered his own record as well, so I asked him about his initial reaction."My immediate reaction was disbelief," Vickery said."I needed to know if this was real, so I quickly located the Texas records and ran a search for my own name. I was outraged at the result. Sitting right in front of my eyes, in a strange, random database I had found on the Internet, were details that could lead anyone straight to me. How could someone with 191 million such records be so careless?"The database contains a voter's full name (first, middle, last), their home address, mailing address, a unique voter ID, state voter ID, gender, date of birth, date of registration, phone number, a yes/no field for if the number is on the national do-not-call list, political affiliation, and a detailed voting history since 2000. In addition, the database contains fields for voter prediction scores.
Philippe J DEWOST's insight:
Shouldn't Digital Sovereignty start with citizen's privacy by making it effective ?
It's really, really, really hard to make a router sound exciting, but the folks behind the Turris Omnia are betting the device's focus on keeping your sensitive data secure might grab you. The manufacturer's IndieGogo campaign still has 45 days to go, but it's already proved incredibly popular: over a thousand backers have pledged some $274,598 as of this writing. That's 275 percent higher than the threshold for funding the project. The router itself runs Turris' open source operating system (based on the OpenWRT project) which auto updates as soon as any type of vulnerability is discovered by its cadre of developers.That's pretty important considering most of us, myself included, don't think about our router unless something goes horribly awry. As an extension of the open nature of the device and its firmware is that there are quite a few add-ons that can tailor the gizmo to your specific use scenarios. Hell, you can even plug an external drive into the Turris and make it a DLNA or back-up server. Want to ensure against internet outages? There's an option to slide a SIM card into the device so you can harness LTE data if your hard connection dies. Beyond that, it's capable of handling gigabit traffic and home automation tasks. The pitch video below even boasts that you can set up traps for hackers with the device and watch as they get stuck in them. You know, in case you're the sadistic type.
Philippe J DEWOST's insight:
Built-in dynamic security is a nice option...
On Tuesday, University of Chicago professor László Babai presented a new algorithm that simplifies a long-standing, difficult problem in computer science.A professor’s claim to have created an algorithm that dramatically simplifies one of theoretical computer science’s most notorious problems has experts preparing to reconsider a long-established truth of their field. It is also seen as a reminder that similar algorithmic breakthroughs are possible that could weaken the tough-to-crack problems at the heart of the cryptography protecting the world’s digital secrets.
Philippe J DEWOST's insight:
Sommething worth keeping an eye on ?
Payer la rançon, cela ne marche pas forcément. Le service de mails chiffrés ProtonMail en a fait l’expérience cette semaine : victime d’une attaque DDoS d’ampleur les visant en premier lieu, mais touchant également des services tiers hébergés sur la même infrastructure, le service mail a expliqué dans une note de blog avoir accepté de payer la rançon exigée par le groupe de hackers, sous la pression d’autres sociétés. Malheureusement, le versement des 6000 dollars en bitcoin n’a pas suffi à mettre fin à l’attaque et l’hébergeur a été contraint de mettre le service mail hors ligne pour limiter l’impact.Le service ProtonMail compte environ 500.000 utilisateurs : celui-ci est basé en Suisse et entend apporter aux utilisateurs une solution supposée sécurisée et capable de mettre des bâtons dans les roues de la NSA et d’autres agences de renseignement.
Philippe J DEWOST's insight:
On est à couteaux (suisses) tirés...
Russian submarines and spy ships are aggressively operating near the vital undersea cables that carry almost all global Internet communications, raising concerns among some American military and intelligence officials that the Russians might be planning to attack those lines in times of tension or conflict.
The issue goes beyond old worries during the Cold War that the Russians would tap into the cables — a task American intelligence agencies also mastered decades ago. The alarm today is deeper: The ultimate Russian hack on the United States could involve severing the fiber-optic cables at some of their hardest-to-access locations to halt the instant communications on which the West’s governments, economies and citizens have grown dependent.
In private, however, commanders and intelligence officials are far more direct. They report that from the North Sea to Northeast Asia and even in waters closer to American shores, they are monitoring significantly increased Russian activity along the known routes of the cables, which carry the lifeblood of global electronic communications and commerce.Just last month, the Russian spy ship Yantar, equipped with two self-propelled deep-sea submersible craft, cruised slowly off the East Coast of the United States on its way to Cuba — where one major cable lands near the American naval station at Guantánamo Bay. It was monitored constantly by American spy satellites, ships and planes. Navy officials said the Yantar and the submersible vehicles it can drop off its decks have the capability to cut cables miles down in the sea.“The level of activity,” a senior European diplomat said, “is comparable to what we saw in the Cold War.”
Philippe J DEWOST's insight:
This NY Times news gives a radically different meaning to "cable war" and "cutting the cord" ...
Un groupe d'experts de l'industrie informatique, dont le « père de l'internet » Vint Cerf, ont demandé au régulateur américain d'obliger les constructeurs à rendre leurs firmwares open-source. S'ils parlent en priorité des routeurs Wi-Fi, le sujet pourrait s'étendre jusqu'aux firmwares des moteurs de voiture...
Philippe J DEWOST's insight:
Réouverture du débat sur l'open source sous un angle nouveau et extrêmement intéressant. |




















This is a major escalation, and unfortunately a new milestone in the history of cyber-warfare. It also continues to blur the line between espionage / sabotage / (potential) strategic actions. Key question that ESET (and NATO) should investigate: how far could the operators of Russia's BlackEnergy/KillDisk actually control their desired effects? .. at least, Stuxnet was designed to be self-contained, focused on one particular & limited action: destruction of P1 centrifuges for Uranium enrichment, and nothing else. With BlackEnergy, how extended was the potential range for havoc as can be understood in the design?