Cybercrime costs Britain £27bn a year, and it could cost you dear too if you don't take basic precautions. James Silver asked experts for their top tips
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
Bösartige Angreifer kapern Apache-Webserver und leiten deren Besucher auf Schad-Websites um. Die Tarnung der Malware ist fast perfekt.
Eine Hintertür, die von Administratoren nur schwer bemerkt werden kann, sorgt dafür, dass Internet-Anfragen an Apache-Server nicht in Logs aufgenommen werden. Die gesendeten http-Anfragen, die in Wirklichkeit einen Trojaner steuern, sind nicht ersichtlich. Der Rest des Angriffs läuft im Speicher ab, Bugfixes gibt es noch nicht.
29. April 2013 von Manfred Kohlen 0
Gust MEES's insight:
Sicherheitsexperten analysieren derzeit die Cyberattacken auf Südkorea und liefern die ersten Ergebnisse. Demnach wurde unter anderem eine Malware eingesetzt, die das Ziel hat, Linux-Rechner auszuschalten.
Gust MEES's insight:
Nobody is perfect! Any OS can be...
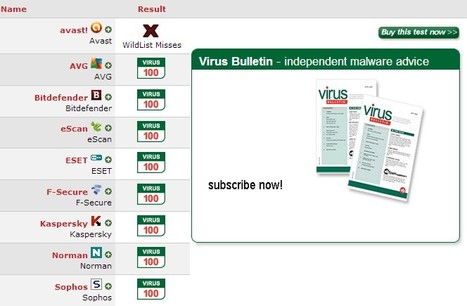
View the results of the Virus Bulletin VB100 anti-virus product comparisons
Gust MEES's insight:
A MUST check for Linux users!!!
Check also:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Nobody-is-perfect
- http://www.scoop.it/t/securite-pc-et-internet?q=Linux

Gust MEES's curator insight,
February 25, 2013 1:48 PM
A MUST check for Linux users!!!
Check also:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Nobody-is-perfect
- http://www.scoop.it/t/securite-pc-et-internet?q=Linux
Security researchers from antivirus vendor Trend Micro have uncovered a piece of backdoor-type malware that infects Java-based HTTP servers and allows attackers to execute malicious commands on the underlying systems.
Gust MEES's insight:
===> Be AWARE of the MALWARE! <===
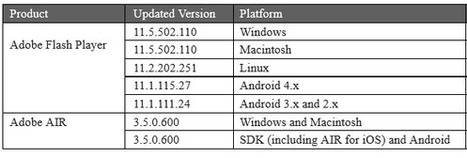
Adobe has released a critical security update for its Flash Player and Adobe AIR software that fixes at least seven dangerous vulnerabilities in these products.
===> Updates are available for Windows, Mac, Linux and Android systems. <===
Read more, a MUST and don't forget to update: http://krebsonsecurity.com/2012/11/adobe-ships-election-day-security-update-for-flash/
Adobe released an update for its Flash Player software on Monday, fixing 25 security holes in the commonly used product. The updates affect Flash running on Windows, Apple Mac and Linux systems in ...
Read more, a MUST:
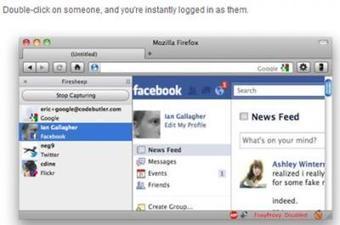
If you thought that capturing a user's social media session was only done by skilled hackers, now the Firesheep addon can allow even the truly clueless to become an Internet griefer.
Even if you were drunk and surfing at a Wi-Fi hotspot, you probably wouldn't stand up and shout your username and password for anyone who might want it. But an attacker does not need to find out your username and password. If you thought that capturing a user's social media session was only done by skilled hackers, now the Firesheep addon can allow even the truly clueless to become an Internet griefer.
If you were at a Wi-Fi hotspot, you probably would have no options and no encryption at all. Although many websites give lip service about how important their users' privacy and security is to them, very few have their entire site encrypted with HTTPS. Most sites encrypt the username and password during the login process, but most of those sites stop encrypting and protecting the user right there. As soon as a user moves on to a regular HTTP page on the site, an attacker can sniff and capture the user's cookie information.
Many of us are busy multitasking, so we log into Twitter or Facebook, or even Flickr, and then move on to surf other sites without first logging out of those accounts. If any of those future sites have a Twitter or Facebook widget, or even a Flickr image embedded, if you didn't log out of those sites before continuing to surf, then HTTP session jacking, also called "sidejacking," can happen and leak the user's cookie. Security researchers explained that if a person can steal the cookie, then they can steal your session and allow them to do anything the user could do on the site.
Gust MEES: a MUST READ for Mac, Linux and Windows users!!!
Read more:
Mobile variants of the commercial FinFisher trojan target BlackBerry, Windows Mobile, Symbian, Android and iOS devices.
The commercial FinFisher FinSpy spyware trojan was created by Gamma International, and its development is believed to take place in Germany. The company sells its trojan toolkit – which is thought to currently support all major operating systems including Linux, Mac OS X and Windows – to governments for use by security agencies. Until now, relatively little was known about the mobile variant of the trojan.
Dr Web, the Russian anti-malware company that did much to expose the growth of the Flashback botnet, has found the first Linux/OSX cross-platform trojan – which it calls BackDoor.Wirenet.1...
Read more:
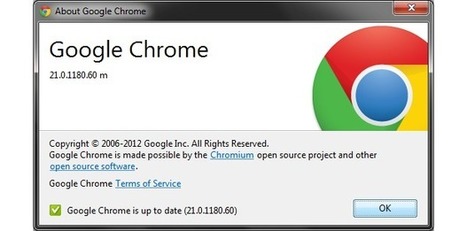
Summary: Google Chrome version 21.0.1180.60 (21.0.1180.57 for Mac and Linux) is out, fixing 15 security vulnerabilities in the search giant's browser.
===> Strictly from a security perspective, you should upgrade as soon as possible. <===
Read more: http://www.zdnet.com/google-chrome-21-is-out-7000001920/
Summary: A second cross-platform Trojan downloader has been discovered that detects if you're running Windows, Mac OS X, or Linux, and then downloads the corresponding malware for your platform.
Read more: http://www.zdnet.com/cross-platform-trojan-attacks-windows-intel-macs-linux-7000000872/
If allowed to run, a malicious Java applet checks the user's operating system and delivers a payload customized for that platform, whether it's Windows, Mac OS X, or Linux.
Read more: http://www.securityweek.com/multi-platform-java-exploit-targets-macs-linux-windows
|
From
www
Malware that hides itself from admins has been found in the wild, allowing attackers to compromise web servers and redirect users to sites hosting exploit kits.
Researchers at security firm ESET have dubbed the malware Linux/Cdorked.A and are calling it "the most sophisticated Apache backdoor" due to its ability to evade detection.
===> Apache web servers run about 50 percent of the world’s websites, according to UK-based internet security firm, Netcraft. <===
The researchers claim the malware has been installed on hundreds of compromised web servers, which have served up malicious redirects to thousands of visitors.
Gust MEES's insight:
===> Apache web servers run about 50 percent of the world’s websites, according to UK-based internet security firm, Netcraft. <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Apache-vulnerabilities

Gust MEES's curator insight,
May 1, 2013 9:27 AM
===> Apache web servers run about 50 percent of the world’s websites, according to UK-based internet security firm, Netcraft. <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Apache-vulnerabilities
There is a critical vulnerability in several current versions of the BIND nameserver software that could allow an attacker to knock vulnerable DNS servers offline or compromise other applications running on those machines. The bug is present in several versions of the ubiquitous BIND software and the maintainers of the application have released a patch for it ===> that they recommend users install as soon as possible. <===
===> The vulnerability is in BIND 9.7, 9.8, and 9.9 for Unix systems, but Windows versions are not affected. <===
The problem lies in the way that the software handles certain regular expressions, and an attacker who exploits the vulnerability could not only cause a denial-of-service condition on the server but also could potentially compromise other software on the machine.
Gust MEES's insight:
The bug is present in several versions of the ubiquitous BIND software and the maintainers of the application have released a patch for it ===> that they recommend users install as soon as possible. <===
===> The vulnerability is in BIND 9.7, 9.8, and 9.9 for Unix systems, but Windows versions are not affected. <===
The problem lies in the way that the software handles certain regular expressions, and an attacker who exploits the vulnerability could not only cause a denial-of-service condition on the server but also could potentially compromise other software on the machine.
Check also:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Linux-Vulnerabilities
This bulletin was written by Vigil@nce : http://vigilance.fr/offer SYNTHESIS OF THE VULNERABILITY A local attacker can use the getsockopt() (...)
Gust MEES's insight:
Auf kompromittierten Linux-Systemen haben Sicherheitsexperten eine heimtückische Hintertür entdeckt, die sich über eine Bibliothek in den SSH-Dienst einklinkt.
Gust MEES's insight:
The Linux root kit targets 64-bit Linux platforms and uses advanced techniques to hide itself, and infects the websites hosted on attacked HTTP server working to launch drive-by download attacks.
“It's an outstanding sample, not only because it targets 64-bit Linux platforms and uses advanced techniques to hide itself, but primarily because of the unusual functionality of infecting the websites hosted on attacked HTTP server - and therefore working as a part of drive-by download scenario,” commented Marta Janus, a Kaspersky Lab Expert who examined the rootkit sample.
===> “This rootkit, though it's still in the development stage, shows a new approach to the drive-by download schema and we can certainly expect more such malware in the future.” <===
Read more: http://www.securityweek.com/linux-rootkit-found-launching-iframe-injection-attacks
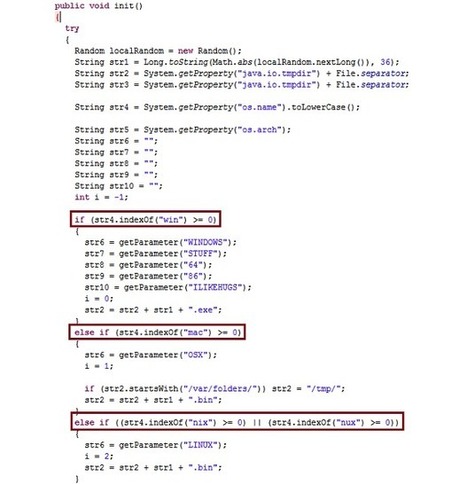
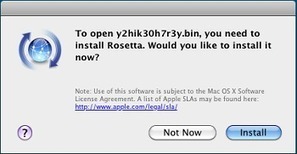
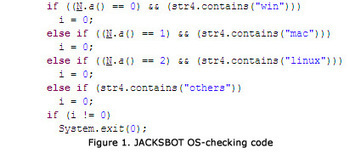
Two weeks ago, Mac security software company Intego discovered malware which it classified as "a new Java backdoor trojan called Java/Jacksbot.A.” New threats are discovered all the time, but Intego later concluded that even though Jacksbot is a variant of the Java remote access tool (RAT) created by the jailbreaking group Redpois0n, it can target multiple platforms.
The malware writers behind JACKSBOT may just be testing the waters for a successful multiplatform malware; however for now they appear to be unwilling to invest the time and resources to develop the code more completely.
===> It’s likely that the authors will continue to improve the code to fully support infection for OS X and Linux. <===
Read more, a MUST:
Hackers are using remote maintenance tool NetWire, which can be used to monitor computers running Windows, Mac OS X, Linux and Solaris, as a trojan. Anti-virus software companies have responded by identifying the program as malware.
Read more:
===> Malware writers are interested in Linux after all. <===
Russian security firm Dr Web has reported finding a shadowy Trojan that sets out to steal passwords on the open source platform as well as OS X.
Cross platform malware is rare but not unheard of, the usual technique being to hook into Java in search of victims using OS X. Malware specifically designed to steal credentials from Linux systems is almost unheard of but might, on the basis of this new discovery, become a little less so in future.
"We do not have explicit evidence that it uses Java. To my knowledge it does not. This file was received from Virustotal," Dr Web analyst Igor Zdobnov told Techworld.
Read more:
Une vulnérabilité, jugée très critique par les spécialistes en sécurité, vient d’être découverte dans la version 7 de Java. Windows, Linux et Mac OS X sont concernés.
En savoir plus :
Adobe and Microsoft each issued security updates today to fix critical vulnerabilities in their software. Adobe’s fixes include a patch for a Flash Player flaw that is actively being exploited to break into Windows computers. Microsoft’s Patch Tuesday release includes nine patch bundles — more than half of them rated critical — addressing at least 27 security holes in Windows and related software.
Nevertheless, the underlying vulnerability being targeted exists in Windows, Mac and Linux versions of the software. Windows and Mac users can grab the latest version (v. 11.3.300.271) via the Flash Player download center.
Be sure to uncheck the “free” software scans that Adobe loves to bundle with updates, such as McAfee‘s obnoxious Security Scan Plus, if you don’t want it. Linux users should update to v. 11.2.202.238, and Chrome users want to be at v. 11.3.330.270 (normally Chrome auto-updates Flash, but recently it’s been sluggish to do so: my Chrome installation is still at v. 11.3.31.225. I will update this post in a bit with the direct links to the Flash Player downloads.
Read more, a MUST for any "OS":
http://krebsonsecurity.com/2012/08/critical-security-fixes-from-adobe-microsoft/
The quickest way to temporarily convert your Windows PC into a Linux system is to use a Live CD. This involves burning an downloadable image file to a CD, inserting the disc into your computer, and rebooting. If this sounds difficult, don’t worry, it’s not.
Here’s a step-by-step guide that should get you up and running in no time flat, with Puppy Linux, an extremely lightweight and fast version of Linux. If you’d prefer to try another distribution, there are dozens to choose from.
Gust MEES: check also here to find more Live-CD's http://www.scoop.it/t/ict-security-tools?tag=LIVE-CD-LIST&amp;nbsp
Read more:
Der Webbrowser des eBook-Readers führt beim Besuch einer präparierten Webseite beliebige Shell-Befehle mit Root-Rechten aus. Die Jailbreak-Community setzt diese Lücke bereits zur Installation von nicht autorisierter Software ein.
Weiter lesen:
|


























The weakest link in a security chain is and still will be the human!!! A security by 100% doesn't exist!!!
===> Read the article, a MUST!!! <===> ALSO for MAC & Linux users!!! <===
Learn more:
- https://gustmees.wordpress.com/2012/11/29/cyber-hygiene-ict-hygiene-for-population-education-and-business/
- https://gustmees.wordpress.com/2012/11/05/naivety-in-the-digital-age/
- http://www.symantec.com/connect/articles/social-engineering-fundamentals-part-i-hacker-tactics?API1=100&API2=3640290
The weakest link in a security chain is and still will be the human!!! A security by 100% doesn't exist!!!
===> Read the article, a MUST!!! <===> ALSO for MAC & Linux users!!! <===
Learn more:
- https://gustmees.wordpress.com/2012/11/29/cyber-hygiene-ict-hygiene-for-population-education-and-business/
- https://gustmees.wordpress.com/2012/11/05/naivety-in-the-digital-age/
- http://www.symantec.com/connect/articles/social-engineering-fundamentals-part-i-hacker-tactics?API1=100&API2=3640290