Your new post is loading...
 Your new post is loading...
A quarterly threat report found password-stealing Trojans on the rise... PC malware had its "busiest quarter in recent history," according to McAfee's quarterly security report released Wednesday. The security company registered the biggest increase in malware in four years during the first quarter of this year, bringing the total number of samples to 83 million. Fake antivirus programs declined in popularity, but software with faked security signatures, rootkits and password-stealing Trojans rose. ===> New malware for the Mac exploded in the second quarter of 2011 <=== Read more: http://www.networkworld.com/news/2012/052312-mcafee-reports-big-spike-in-259575.html?source=nww_rss
Via Gust MEES

|
Rescooped by
Gerrit Bes
from Social Media and its influence
May 22, 2012 2:02 AM
|
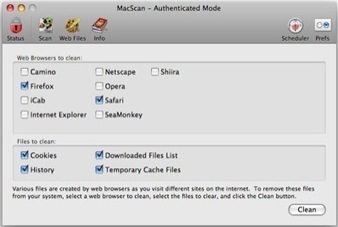
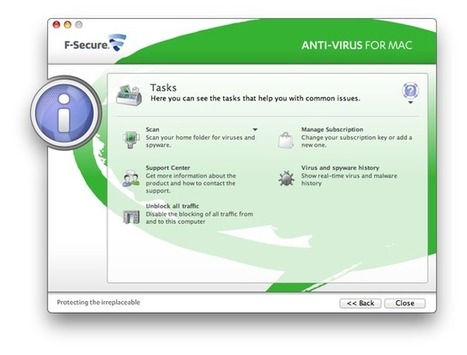
SecureMac released MacScan 2.9.3, which features tracking cookie detection and cleaning for Google’s Chrome browser. MacScan is the premier Macintosh security program, protecting you against the latest malware and privacy threats for Apple Mac OS X, offering protection against keystroke loggers, trojan horses, and other spyware. Read more...
Via Gust MEES

|
Rescooped by
Gerrit Bes
from ICT Security Tools
May 14, 2012 10:54 PM
|
So Mac invulnerability to malware is a myth, at least according to security researchers from Kaspersky Lab. And although such a blunt statement may be a blow to the ego of some Mac users, it remains true. Security researchers from all walks have long argued that it was only a matter of time before the Mac became popular enough that virus, malware, and spyware makers would come calling, and the recent Flashback scare has only served as a reminder that overconfidence precedes carelessness. Especially when it comes to technology. Read more...
Via Gust MEES
"Creativity is driven by Social dynamics.
Creativity is the result of a set of relationships with a strong social dimension and emotional. It is a collaborative environment (and this is where HR can play a significant role), hence the change of focus towards the organizational culture and transformation in design organizations.” “We need an inclusion in this dialogue from artists, from poets, from writers — from ===> people who can bring a human element into this discussion. <==== Because I believe that this world of data is going to be transformative to us.” Read more...
Via Karen Steffensen, michel verstrepen, Joao Brogueira, Gust MEES
Apple has released OS X Lion 10.7.4.The update includes performance improvements as well as a bunch of fixes, including the FileVault bug that was re... Read more...
Via Gust MEES
Flashback Malware Robs Google of $10,000/Day in Ad Revenue The authors of MacOS malware 'Flashback' are reaping an estimated $10,000 a day by through an additional component, Symantec reports. Read more...
Via Gust MEES
A trojan that hijacks how your computer accesses the Internet could cut off thousands of machines this summer. There’s a trojan out there that tricks computers — both PCs and Macs — into redirecting all their Internet traffic through malicious servers. Even though the trojan’s creators have been stopped and arrested, millions of PCs could still be infected. ===> For those machines, the Internet will cease to exist on July 9. <=== Read more...
Via Gust MEES
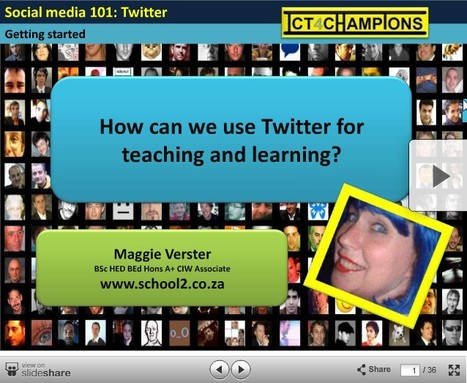
Key Questions Answered
- Why should a teacher or education administrator use Twitter?
- How do I set up an account? (step-by-step instructions included!) - What questions should I always ask myself when I follow someone? - How do I tweet? How do I retweet? What the heck is a retweet?! - How do I find good people to follow? Fellow teachers? People interested in what I like? - What’s privacy like on Twitter? - What should my profile photo be? - What are the drawbacks of Twitter? Read more...
Via Gust MEES

|
Rescooped by
Gerrit Bes
from Social Media and its influence
April 22, 2012 3:29 AM
|
In our last blog, we discussed the importance of competence for fostering the trust you need as a manager to influence others. We stressed that management competence includes not just technical knowledge of the work but operational and political know-how as well. Here we want to focus on the other great component of trust — character — but by taking a different approach. So far we've argued that intentions — character — are the foundation of trust, that they must be supported by competence, and that you must take pains to reveal them. But we haven't addressed the question of your intentions themselves. Does it matter what your intentions are? Yes, of course it does. We don't trust anyone simply because they have clear intentions. Otherwise, we'd trust Hannibal Lector and other villains. ===> People trust us because we have the right intentions, which are those intentions people accept and agree with. What are "the right" intentions? <=== That's not an easy question to answer, especially for a boss, and it's the subject of our next blog. Read more, very interesting...
Via Professor Jill Jameson, Gust MEES
If you’re building elearning courses, then you should expect to have a graphics editing program as part of your tool chest. In a previous post I mentioned a few free (or low cost) graphic editors if you don’t already have one. There’s a difference between having a graphics application and being a professional graphics artist. Many of us work alone and have to do our own graphics. I find that what I do for graphics doesn’t require overly sophisticated skills. While we may be using different tools, there are some simple graphics editing we should all be able to do. Let’s review a few of the common image editing tasks. Read more...
Via Gust MEES
A week after the Flashback Trojan began running rampant on Macintosh computers, the malware appears to be in remission.
Via Gust MEES

|
Rescooped by
Gerrit Bes
from Social Media and its influence
April 15, 2012 12:26 PM
|
In today's college classrooms the sound of furious note-scribbling has been replaced by clacking on keyboards and tapping on tablets. Thanks to the ubiquity of WiFi on campuses, it's not just note-taking that's been given a 21st-century update.
Via Gust MEES
|

|
Rescooped by
Gerrit Bes
from Social Media and its influence
May 21, 2012 2:29 AM
|
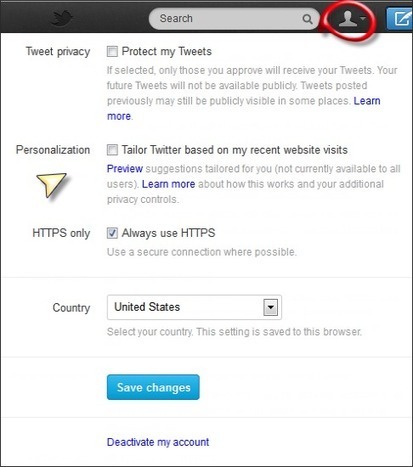
Twitter is without a doubt the best way to share and discover what is happening right now. What is “Do Not Track”? Do Not Track (DNT) is a privacy preference that users can set in their web browsers. The United States Federal Trade Commission has endorsed DNT as a simple way for users to inform integrated web services which offer content across the Internet (such as buttons, widgets, and other embedded features) that they do not want certain information about their webpage visits collected across websites when they have not interacted with that service's content on the page. The DNT browser setting is now supported by recent versions of major browsers, including Firefox 5+, Internet Explorer 9+, and Safari 5.1+. If you are using Chrome 17.0 or higher, there is a third-party extension that enables DNT. Read more...
Via Gust MEES

|
Rescooped by
Gerrit Bes
from Social Media and its influence
May 18, 2012 2:23 AM
|
Twitter has announced a "do not track" feature. Twitter’s move comes after the FTC released a report in March calling on designers of Internet browsers to stop allowing websites to collect sensitive data about users. The other social media giant, Facebook, does not currently have a Do Not Track feature. Read more...
Via Gust MEES
InfoRapid KnowledgeMap is a complete Knowledge Management System suitable for use at home, at work or on the company intranet. The suite consists of two components: an image-editing (drawing) program for creating graphically sophisticated mindmaps, and the intelligent KnowledgeMap server, which analyzes text document content and integrates it with a knowledge map. Read more...
Via Gust MEES

|
Rescooped by
Gerrit Bes
from Social Media and its influence
May 10, 2012 10:38 PM
|
Twitter has just finalized a deal to hire the team and buy the technology of RestEngine, a personalized email marketing service, which could help Twitter deliver email digests of great tweets you've missed. Read more...
Via Gust MEES

|
Rescooped by
Gerrit Bes
from ICT Security Tools
May 3, 2012 11:34 PM
|
Clean your virus-infected computer - check out the Bitdefender library with free virus removal tools, plugins and applications for social media. Bitdefender USB Immunizer
Bitdefender USB Immunizer is a free and easy to use tool that helps make sure you transfer the files, not the viruses. It disables autorun-related threats before they access the computer.
===> Once installed, it constantly watches for newly inserted USB storage devices and immunizes them on the fly. <=== Read more and find more FREE tools...
Via Gust MEES
AVG: Android Malware Is Pushed via Twitter and Facebook... “We detected a big increase in the use of social networks such as Facebook and Twitter to target Android users. Cyber criminals are finding it very convenient to distribute their malware straight to a mobile device via these networks,” said Yuval Ben-Itzhak, chief technology officer at AVG. “The growth of the Android platform has been phenomenal, which has not gone unnoticed with cyber criminals who have discovered it to be a lucrative target for their malware. In 2011, Google had to remove over 100 malicious apps from the official Android market, Google Play.” Read more...
Via Gust MEES
Thumbnail descriptions of the thinking strategies commonly used by creative geniuses.
Via Gust MEES
How can parents support children’s internet safety? The challenge
Many stakeholders are working together to support children’s internet safety, including governments, teachers, industry providers and services, child welfare agencies, parents and children themselves.
Given the Safer Internet Day 2012 theme of Connecting Generations, we ask whether, instead of imposing restrictions, parents can support their children’s internet safety by sharing a positive experience of internet use with their children...
Read more...
Via Gust MEES
The Flashback malware threat for OS X is on a steep decline, but still underscores that Mac systems are not immune to threats. Read this blog post by Topher Kessler on MacFixIt.
Via Gust MEES
A new Trojan known as “Sabpab” could hurt Mac users who run Java and Microsoft Word. Security researchers are warning users to make sure their computers ===> have the latest software updates from both Apple and Microsoft, <=== and to use anti-virus software. In some cases, manual removal of Sabpab may be needed. Word about Sabpab comes on the heels of another nasty piece of malware, Flashback, that infected up to as many as 600,000 Macs, security experts said, by exploiting a vulnerability in Java software. Apple last week issued a software-base removal tool for that malware, which can be used by criminals to steal personal information, including passwords. Read more...
Via Gust MEES
April 15, 2012
By Dave Meister The first PHSprincipalBlog (changed to Director 4/1/2009) post was on 9/18/2007. (332 posts overall) I have been using Twitter for 4 years, 4 month... We still have a lot of work to do, but I feel more strongly than ever before that we are willing to meet the challenges to make our learning environments relevant and engaging. We have the unique opportunity to design and build a new school complex that will be both flexible and transparent and able to accommodate learning for today’s world and the challenges of tomorrow.
I AM SO GLAD I STARTED TO BLOG AND TWEET!
Read more...
Via Gust MEES
|



 Your new post is loading...
Your new post is loading...










![Twitter Implements 'Do Not Track' Feature [BREAKING] | Latest Social Media News | Scoop.it](https://img.scoop.it/rrL_26r8-VWHbmU3cQDPBzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)