Your new post is loading...
 Your new post is loading...

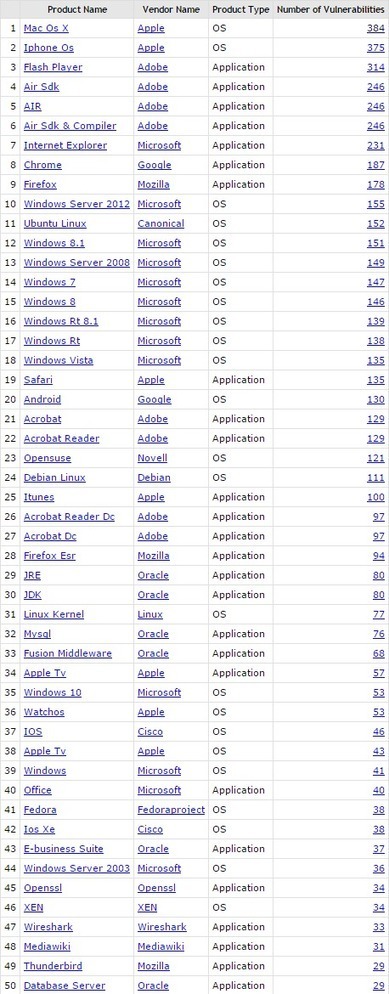
|
Scooped by
Gust MEES
March 17, 2016 10:46 AM
|

|
Rescooped by
Gust MEES
from 21st Century Learning and Teaching
January 1, 2016 5:13 PM
|

|
Scooped by
Gust MEES
November 2, 2015 7:00 PM
|

|
Scooped by
Gust MEES
October 5, 2015 1:50 PM
|

|
Scooped by
Gust MEES
September 20, 2015 12:48 PM
|

|
Scooped by
Gust MEES
August 27, 2015 7:45 AM
|
Bösartige Apps können sich auf iOS-Geräten festbeißen und selbst wenn man sie über den Task-Manager schließt weiter Daten abfischen.
Über eine Ins0mnia getaufte Schwachstelle können Angreifer mit präparierten Apps Apples Vorgaben zum Schließen von Drittanbieter-Anwendungen umgehen und im Hintergrund dauerhaft Informationen abgreifen. Das gelingt auch, wenn Nutzer Apps über den Task-Manager schließen, berichten die Entdecker der Lücke von FireEye. Die Schwachstelle wurde mit der Veröffentlichung von iOS 8.4.1 geschlossen.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=Ins0mnia

|
Scooped by
Gust MEES
June 20, 2015 9:55 AM
|
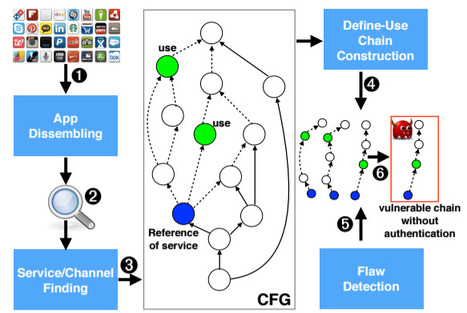
It’s become almost axiomatic that Apple devices and the apps on them are more secure than the competition. But researchers continue to blow up that notion and today a group of academics have ripped apart the securityprotections in Mac OS X and iOS to show it’s not only possible to create malware and get it onto the App Store, but it’s also feasible to launch “devastating” attacks using rogue software to steal the most sensitive personal data around, from iCloud passwords and Evernote notes to dodgy selfies and more.
The attacks, known as unauthorized cross-app resource access or XARA, expose design flaws that allow a bad app to access critical pieces of data in other apps. As a result, Apple has struggled to fix the issues, according to apaper released today from Indiana University Bloomington, Peking University and the Georgia Institute of Technology.
En savoir plus / Merhr erfahren / Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=XARA

|
Scooped by
Gust MEES
June 17, 2015 6:28 PM
|
"Note that all the attack apps were successfully released by the Apple Stores. So, the security threats are indeed realistic."
So, it's a serious problem. And, as yet, not fixed.
The university researchers say that they first reported the vulnerability to Apple on October 15 2014, and contacted them again in November 2014 and early this year. They claimed that Apple told them that because of the complex nature of the security issue, six months' grace would be required to develop a solution.
Unfortunately, that fix has still not emerged and the researchers have chosen to go public with their findings.
For now, until a proper solution is discovered, the most secure approach might be to exercise caution about what apps you download onto your Macs and iOS devices, even if they are listed in the official iOS and Mac App Store — stick with apps from known developers.
Learn more:
.

|
Scooped by
Gust MEES
June 10, 2015 4:50 PM
|
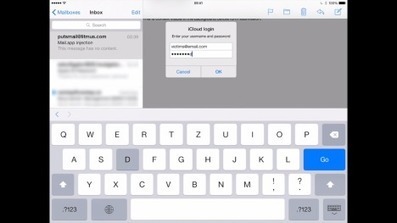
Der Sicherheitsexperte Jan Soucek hat einen äußerst gefährlichen Bug in der E-Mail-App von Apples iOS entdeckt. Ein Angreifer kann darüber eine Fake-Abfrage der Apple-ID einblenden - und so das Passwort abgreifen.
CHIP Online meint:
Auch wenn nicht jeder glücklich darüber sein dürfte, dass Soucek seinen Programm-Code mit der Veröffentlichung auch möglichen Angreifern bereitstellt, trifft die eigentliche Schuld Apple. Es ist eine äußerst fragwürdige Politik, eine Sicherheitslücke derartigen Ausmaßes einfach ein halbes Jahr zu ignorieren. Hier muss Apple nun unbedingt in kürzester Zeit nachbessern - spätestens mit der Veröffentlichung von iOS 8.4 Ende Juni.
Mehr erfahren/ Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Rescooped by
Gust MEES
from 21st Century Learning and Teaching
April 27, 2015 12:55 PM
|
"No iOS Zone" denial-of-service vulnerability could lead to your iPhone or iPad constantly crashing.
The researchers say that they first informed Apple of the problem in early October 2014, and that iOS 8.3 appears to resolve some of the issues they uncovered.
Chances are that this won’t be the last time that a serious denial of service flaw is found in iOS. Just last month, Apple released iOS 8.2 which fixed a flaw that allowed hackers to restart iPhones by sending them a maliciously-crafted Flash SMS.
More details of the “No iOS Zone” flaw can be found in the slide deck of the presentation given at the RSA conference.

|
Scooped by
Gust MEES
April 25, 2015 6:29 AM
|
At least 25,000 iOS apps available in Apple's App Store contain a critical vulnerability that may completely cripple HTTPS protections designed to prevent man-in-the-middle attacks that steal or modify sensitive data, security researchers warned.
1,500 IOS APPS HAVE HTTPS-CRIPPLING BUG. IS ONE OF THEM ON YOUR DEVICE?
Apps downloaded two million times are vulnerable to trivial man-in-the-middle attacks.
As was the case with a separate HTTPS vulnerability reported earlier this week that affected 1,500 iOS apps, the bug resides in AFNetworking, an open-source code library that allows developers to drop networking capabilities into their iOS and OS X apps. Any app that uses a version of AFNetworking prior to the just-released 2.5.3 may expose data that's trivial for hackers to monitor or modify, even when it's protected by the secure sockets layer (SSL) protocol. The vulnerability can be exploited by using any valid SSL certificate for any domain name, as long as the digital credential was issued by a browser-trusted certificate authority (CA).

|
Scooped by
Gust MEES
February 19, 2015 12:01 PM
|
Five months on from the release of iOS 8, and following six rounds of bugfixes, Apple's flagship mobile platform that powers almost three out of four iPhone and iPads is still riddled with bugs.
I'm just going to come out and say it - this is a mess. If we were talking about cosmetic stuff like a badly laid out user interface or poor selection of wallpapers then I could overlook the issues, but they aren't. These are bugs relating to core systems such as Wi-Fi, cellular connectivity, Bluetooth, and stability and performance.
These are show-stopping bugs. These are bugs that quite frankly should have been sorted before iOS 8 was released, and definitely should have been pinned down after the first couple of updates.
But they aren't.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
February 5, 2015 7:25 AM
|
|

|
Scooped by
Gust MEES
March 16, 2016 4:06 PM
|

|
Scooped by
Gust MEES
December 9, 2015 10:46 AM
|
Après Microsoft qui a publié un Patch Tuesday bien fourni en correctifs critiques, c’est au tour d’Apple de mener un grande vague de mises à jour de sécurité sur plusieurs produits. Les OS de la firme de Cupertino sont bien évidement aux premières loges.
Différentes versions de Mac OS X sont concernées : OS X El Capitan 10.11.2, OS X Yosemite 10.10.5, et Mavericks 10.9.5. Au total, la Security Update 2015-008 corrige 54 vulnérabilités dans des services et des composants tel qu’App Sandbox, Bluetooth, Compression, Configuration Profiles, CoreGraphics, CoreMedia Playback, EFI, File Bookmark, Hypervisor, ImageIO, Intel Graphics Driver, IOAcceleratorFamily, IOHIDFamily, IOKit SCSI, Kernel, Keychain Access, OpenGL, Sandbox, Security, etc. A noter que la moitié des failles découvertes sont critiques, car elles peuvent permettre à des pirates d’exécuter du code arbitraire à distance.
Learn more / Mehr erfahren / En savoir plus :
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=Patch+Tuesday+made+in+Apple
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
November 2, 2015 6:52 PM
|
Apple devices are generally considered by security experts to be safe, and rather difficult to hack. But difficult doesn’t mean impossible.
Over the weekend someone proved just how possible it is to hack at least one of these devices, the iPhone.
The hack came about as part of a challenge issued in September by bug bounty startup Zeriodium, which offered up a million dollar bounty for “an exclusive, browser-based, and untethered jailbreak for the latest Apple iOS 9 operating system and devices” that was set to expire on October 31.
This new hack has implications far exceeding the million dollar bounty.
Learn more:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=ZERODIUM

|
Scooped by
Gust MEES
September 20, 2015 1:36 PM
|

|
Scooped by
Gust MEES
August 31, 2015 7:01 PM
|
Cybercriminals have reportedly stolen over 225,000 Apple ID account credentials from jailbroken iOS devices, using a type of malware called, “Keyraider”. The criminals have been using the stolen credentials to make in-app purchases with user accounts. Keyraider poses as a downloadable app, but once it’s on the user’s phone, it steals the user’s account login credentials, device GUID (globally unique identifier), Apple push notification service certificates and private keys, and iTunes purchase receipts. These attacks happened mainly in China, but jailbreaking is not exclusive to China. Jailbreaking is practiced by iOS users all over the world.
Jailbreaking your device is a security risk!
This news is a timely reminder about the downside to jailbreaking your Apple iOS device. It sounds like a great idea, in theory, but what many often overlook is that while jailbreaking allows Apple users to bypass many iOS operating system restrictions they might consider burdensome, for example being only able to download apps from the Apple iOS App Store, it also means that cybercriminals have much more freedom to attack the device.
One of the biggest reasons that jailbreaking puts your phone or tablet at risk is that it disables the “sandboxing” feature native in all Apple devices. Sandboxing keeps third party apps out of your operating system, and only allows those apps certain permissions to your information (which these apps “ask” for through pop-ups to be approved by the device user). Because these apps need your explicit permission to look through your photos, access your location, or look up your contacts, it’s highly unlikely that malicious code can get through to do damage or steal your information. Once you remove the sandbox, any app can access all of your private information, including malicious apps posing as legitimate apps.

|
Scooped by
Gust MEES
August 27, 2015 7:33 AM
|
Über die iOS-Sicherheitslücke Ins0mnia können bösartige Apps iPhone-Nutzer ausspionieren. Abhilfe schafft ein Update auf die neue Version 8.4.1 von Apples Betriebssystem.
Lauschangriff auf iPhone-Nutzer: Normalerweise ist es Drittanbieter-Apps unter iOS nicht gestattet, dauerhaft im Hintergrund ausgeführt zu werden. Das Betriebssystem schließt die Anwendungen automatisch nach 3 Minuten, falls diese nicht genutzt werden. Über die Sicherheitslücke Ins0mnia ist es laut Untersuchungen des Sicherheitsanbieters FireEye allerdings möglich, diese Beschränkung zu umgehen.
Dadurch sind bösartige Apps in der Lage, den Nutzer dauerhaft zu tracken und beispielsweise GPS-Standorte weiterzuleiten. Selbst das manuelle Beenden der App über den Task Switcher schafft keine Abhilfe.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=Ins0mnia

|
Scooped by
Gust MEES
June 18, 2015 7:22 AM
|
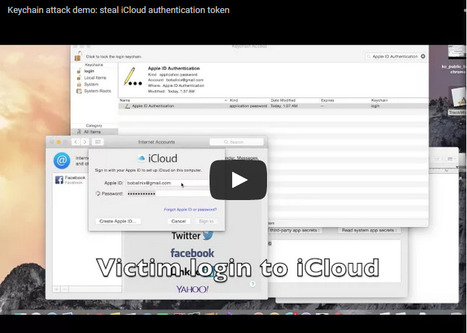
Plusieurs failles de sécurité ont été repérées par des chercheurs universitaires, celles-ci permettant de contourner la sécurité de l’application keychain, des sandbox des programmes ou encore les mesures de sécurité sur l’App Store. La famille Xara Et ce type de failles se retrouve un peu partout : selon les auteurs de l’étude, qui ont testé 200 applications choisies au hasard sur l'App Store, la grande majorité d'entre elles se révèlent vulnérables face à ces failles de sécurité. Si l’exemple de Keychain est le plus parlant, les chercheurs notent que ce type de vulnérabilités peut être utilisé pour accéder à de nombreux services et applications sur iOS et OSX. Au total, les chercheurs estiment que 88,6% des applications proposées sur l’Apple Store seraient vulnérables à ce type d’attaques.
En savoir plus / Merhr erfahren / Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security/?tag=XARA

|
Scooped by
Gust MEES
June 17, 2015 11:44 AM
|
|Nach Angaben mehrerer Universitätsforscher sind das Sandboxing-System und die Schlüsselbundverwaltung von Apple nicht sicher. So soll es möglich sein, private Daten, Fotos und Passwörter zu klauen.
Forschern mehrerer Universitäten ist es gelungen, Sicherheitsmechanismen in Apple-Produkten zu umgehen. Sie entdeckten mehrere Lücken, über die sie von einer manipulierten App auf andere Anwendungen zugreifen konnten. Eigentlich sollte dies nicht möglich sein. Nach ihren eigenen Aussagen informierten sie Apple über die Lücken. Der Hersteller, der im vergangenen Quartal 13,6 Milliarden Dollar Gewinn machte, forderte sie auf, mindestens sechs Monate zu warten, reagierte dann aber nicht mehr. Deswegen entschieden sie sich, ihre Erkenntnisse in einem Whitepaper (PDF) zu veröffentlichen. . Learn more: . .

|
Scooped by
Gust MEES
May 26, 2015 9:36 AM
|
Das neue Sicherheitssystem "Rootless" soll einem Bericht zufolge den Zugriff auf bestimmte Dateien in iOS 9 sowie Mac OS X 10.11 verhindern – selbst für Nutzer mit Admin-Rechten.
Mit iOS 9 und Mac OS X 10.11 führt Apple größere neue Sicherheitsfunktionen ein, wie 9to5Mac unter Berufung auf informierte Kreise berichtet: Das auf Kernel-Ebene angelegte Schutzsystem "Rootless" solle künftig den Zugriff auf bestimmte geschützte Dateien generell verhindern – auch für Nutzer mit den Rechten eines Administrators. Die Funktion sei unter anderem als zusätzlicher Schutz vor Malware gedacht, sie bedeute aber auch einen "schweren Schlag" gegen die Jailbreak-Community, heißt es dort.
In Mac OS X lässt sich diese Rootless-Funktion möglicherweise deaktivieren, merkt 9to5Mac an – auch der gewohnte Zugriff auf das Dateisystem über den Finder soll weiterhin möglich sein.

|
Scooped by
Gust MEES
April 27, 2015 10:33 AM
|
CyberSecurity Researchers have uncovered around 25,000 iOS apps that use old versions of a popular networking library, leaving them open to attackers on the same network viewing encrypted traffic.
The bug affects Secure Sockets Layer (SSL) code in AFNetworking, a networking library developers can use to build components of iOS apps. The framework has been updated three times in the past six weeks, addressing numerous SSL flaws that leave apps vulnerable to man-in-the-middle attacks.

|
Scooped by
Gust MEES
April 13, 2015 7:47 AM
|
Wer die jüngsten Updates für iOS und OS X noch nicht installiert hat, sollte das schnellstens tun. Denn in den Betriebssystemen von Apple verbirgt sich eine Sicherheitslücke, über die Angreifer jedes Apple-Gerät zum Absturz bringen können.

|
Scooped by
Gust MEES
February 5, 2015 5:27 PM
|
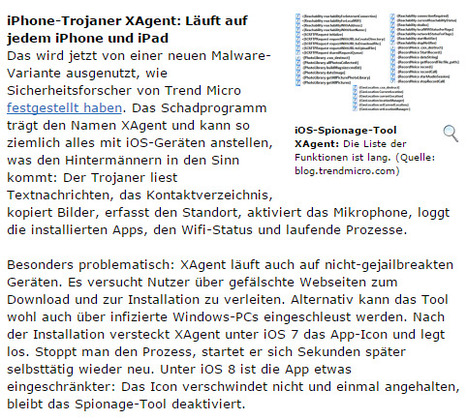
Kurz nachdem bekannt wurde, dass über Googles Play Store millionenfach Adware-Tools heruntergeladen wurden, erwischt es Apple-Nutzer: Sicherheitsforscher haben Spionagetools enttarnt, die iOS-User belauschen und ihre Daten kopieren. Eines der Programme läuft sogar auf vermeintliche sicheren iPhones, die nicht gejailbreakt wurden.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
|



 Your new post is loading...
Your new post is loading...