 Your new post is loading...
 Your new post is loading...
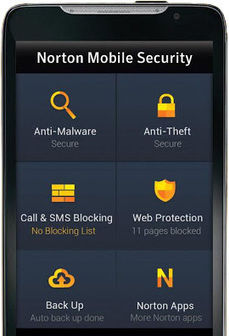
The new Norton Mobile Security with antivirus protects your Android phones and tablets from theft, loss, malware and viruses.
Remotely...

|
Scooped by
Gust MEES
August 27, 2012 4:56 AM
|

|
Scooped by
Gust MEES
July 17, 2012 8:51 AM
|
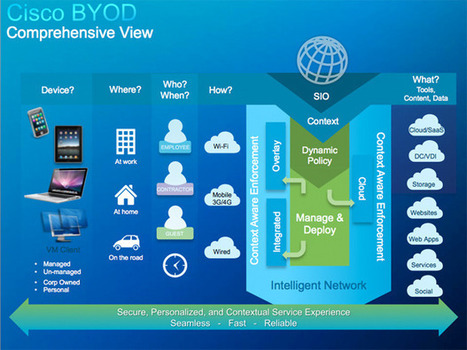
There are 50,538 smartphones and tablets in use at Cisco, which has 71,825 employees. Not only does that already comprise a ratio of one device per 1.4 employees, said Lance Perry, vice-president of IT customer strategy and success for Cisco, during an excellent presentation at the Consumerization of IT in the Enterprise (CITE) conference in San Francisco on Monday. But the 50,000+ device figure is also an increase of 52% from just 12 months earlier. Read more: the practice... http://www.forbes.com/sites/sap/2012/03/05/cisco-the-biggest-mobile-byod-deployment-around/

|
Rescooped by
Gust MEES
from ICT Security Tools
June 12, 2012 9:02 AM
|
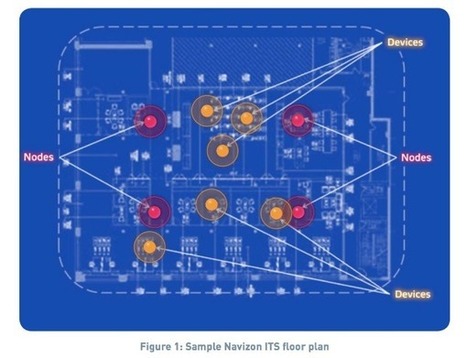
Navizon I.T.S. makes it easy to pinpoint Wi-Fi devices anywhere its listening nodes are installed.
” Mobile devices can expose users’ and
organizations’ valuable data to unauthorized people if
necessary precautions are not taken.

|
Scooped by
Gust MEES
April 24, 2012 8:35 AM
|
The Security, Privacy and Legal Implications of BYOD
Some organizations believe that BYOD will allow them to avoid significant costs. Other companies believe that company data on personal devices is inevitable.
Unfortunately, BYOD raises significant data security and privacy concerns, which can lead to potential legal and liability risk. Many companies are having to play catch-up to control these risks. ===> This blogpost identifies and explores some of the key privacy and security legal concerns associated with BYOD, including “reasonable” BYOD security, BYOD privacy implications, and security and privacy issues related to BYOD incident response and investigations. <=== Read more...
SecurEnvoy revealed details of its latest release that gives users full flexibility of the device they use, while ensuring complete security to the organization. At the click of a button users can have their authentication token as an SMS on a mobile, an app on a smartphone or tablet, or a soft token on a laptop – with the ability to swap between devices at will. Read more...
Organizations are failing to respond to the culture of employees using their own mobile devices for work and are opening up their systems to security risks. These are the preliminary findings of a survey by PwC and Infosecurity Europe.
82% of large organisations reported security breaches caused by staff, including 47% who lost or leaked confidential information.
Only 39% of large organisations encrypt data downloaded to smart phones and tablets
54% of small businesses (38% of large organisations) don’t have a security awareness programme
While 52% of small businesses say social networking sites are important to their business, only 8% monitor what their staff post on those sites.
Some 75% of large organisations (and 61% of small businesses) allow staff to use smart phones and tablets to connect to their corporate systems and yet only 39% (24% of small businesses) apply data encryption on the devices. Read more...

|
Scooped by
Gust MEES
April 11, 2012 12:38 PM
|
A BYOD policy can eliminate a lot of the problems associated with bring your own device programs. Learn best practices for creating a BYOD policy. BYOD isn’t a synonym for “free for all.” Once an organization decides to let employees use their own mobile devices and PCs for work, it must put a BYOD policy in place to control this usage. ===> Requires Free Membership to View

|
Scooped by
Gust MEES
April 7, 2012 10:00 AM
|
Spotlight covers the intersections of technology and education, going behind the research to show how digital media is used in and out of classrooms to expand learning. “When I talk to colleagues in Finland, they say, how do you filter?” said Jim Klein, director of Information Services and Technology at the Saugus Union School District in Southern California. “They say, our kids’ filters are in their heads. You do this by giving them a safe environment to educate themselves instead of sticking your head in the sand and pretending these technologies don’t exist.”
|
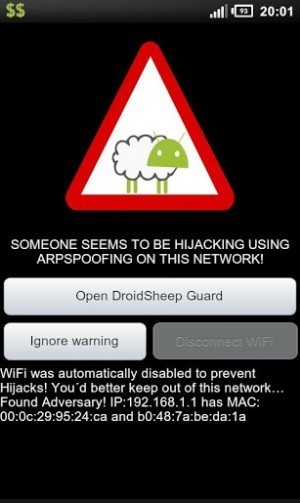
DroidSheep Guard protects your phone from DroidSheep, Faceniff & other hijackers DroidSheep Guard protects your phone from Tools like DroidSheep, Faceniff and other Se...

|
Scooped by
Gust MEES
July 17, 2012 9:09 AM
|

|
Scooped by
Gust MEES
June 5, 2012 8:14 AM
|

|
Scooped by
Gust MEES
May 30, 2012 8:04 AM
|
Considering BYOT / BYOD next year? Get started with this sample policy & answers to FAQs One of the best ways to prepare students to be prepared for the world is to help them use the tools of their world responsibly. Allowing students to bring their own devices is a terrific way to do just that, but even though some schools may have the wireless capacity and infrastructure, the admins / teachers may want to have a policy in place. Below is the policy shared with me by Tim Clark who serves as the Coordinator of Instructional Technology for Forsyth County, GA Schools. Read more: http://theinnovativeeducator.blogspot.com/2012/05/considering-byot-byod-next-year-get.html

|
Suggested by
Evolving Classroom
April 24, 2012 12:20 PM
|
Last week an educator asked the question, “What digital learning technology can my school district invest in that will not become obsolete?” The answer… teacher training technology! More specifically, professional development (PD) sessions that essentially deliver the knowledge, skills and competencies required for a successful transition from a 20th century schooling style to 21st century digital learning style. This is the critical component for success in any school technology initiative and implementation. Read more...

|
Scooped by
Gust MEES
April 24, 2012 8:40 AM
|
"iPhones, iPads, Androids, Tablets are pouring into organizations. In today's BYOD culture, AirTight often sees 3 times as many unmanaged personal devices in a customer's airspace than corporate devices. ===> The key to keeping your network secure is to manage those devices." <=== Read more...
Anti-Theft is an application for your mobile phone that provides a great way to protect it if it gets lost or stolen – and it’s FREE!
This is what you get:
- Easy to install and use
- Protects your confidential information against loss or theft
- Helps you locate your phone
Read more...
SC Magazine has various news articles and information for IT security professionals. Bring-your-own-device and cloud security are just some of the topics that add to the changing threat landscape of online security. Read more...

|
Suggested by
Evolving Classroom
April 18, 2012 8:03 AM
|
If you are making a technology plan for district funding today, it is wise to think where the mobile technology evolution will be in the next three to five years. This type of proactive thinking wi...

|
Scooped by
Gust MEES
April 11, 2012 10:35 AM
|
The explosion in development and adoption of smartphones and tablets for both personal and business use in the past two years is both a blessing and a curse to IT departments globally. Known as the Bring Your Own Device (BYOD) phenomenon, on one hand, there is an opportunity for greatly increased productivity and decreased costs. ===> On the other, there are increased security risks, management issues and even data and device ownership and governance issues. <===
|




 Your new post is loading...
Your new post is loading...



![Cisco: The Biggest Mobile BYOD Deployment Around? [Slides] | 21st Century Tools for Teaching-People and Learners | Scoop.it](https://img.scoop.it/979Kz0MNTSPBQDYgcyqzhzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)







![Mobile Security Firm Analyzes 1.7 Million Android Apps [Infographic] | 21st Century Tools for Teaching-People and Learners | Scoop.it](https://img.scoop.it/-U8bVTIhWiIVeL-h7oriNjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)














The new Norton Mobile Security with antivirus protects your Android phones and tablets from theft, loss, malware and viruses. The "Lite Version" is FREE!
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet