BitDefender has prepared this wonderful and a very informative Infographic on the history of computer viruses starting 1970. The history of malware is rife with incidents that allowed viruses to morph ...
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
Current selected tag: 'Cybersecurity'. Clear
Network Security and More
“Nowadays, you have to have a layer past the firewall that we didn’t have to deal with when we simply said no to user-owned devices,” he says. “Now all of a sudden, you have multiple points of entry at different levels of access, and that requires more diligence.” One key to maintaining adequate security, Knezek and other experts say, is to have multiple networks: one for Wi-Fi traffic, one for district business and for other secure information for teachers and administrators only, and one for students and outside users of the district’s Web site.
Tips to help you and your family become safer online. Online Safety Tips.
===> Share this please! <===
Video on how financial botnets like #Zeus infect computers and steal your account info...
Gust MEES: a very good video who explains the way that everybody understands... A MUST WATCH!!!
Check out also:
- http://gustmeesen.wordpress.com/2012/03/16/beginners-it-security-guide/
- http://gustmeesen.wordpress.com/2012/02/13/why-ict-security-why-the-need-to-secure-a-computer/
- http://gustmeesen.wordpress.com/2012/01/05/pc-security-howto-secure-my-pc/ ;
===> ICT-Security + Cyber-Security are part of Learning in 21st Century!!! <===
Bringing together two separate pieces of security research reveals vulnerability to cybercrime on an alarming scale.
When trying to get a handle on cybercrime today, consider this: In millions of homes across America, unencrypted company information is sitting on unprotected desktops and laptops – in the hands of employees who have had no security training.
At the same time, we see software being deployed that can stealthily and remotely scan the hard drives of those machines for specific data, and secretly transmit it back to the scanner.
Use self-interest and propaganda to change employees' attitudes about endpoint security.
|
Positioning the Security Team Through Influence Part 1
|

|
Rescooped by
Gust MEES
from ICT Security-Sécurité PC et Internet
March 27, 2012 12:41 PM
|
Cyber Security Centre...
Cyber security is an increasingly important requirement for global business and modern society. We exist in a data-centric world, where information technology and associated communications networks and services pervade every aspect of our lives.
This makes the protection of our digital assets and activities in cyberspace of critical importance, whether for individual life experience or a prosperous and sustainable society. But the challenge to understand cyber risk and deliver effective and accessible security becomes harder as technology continues to rapidly evolve and our systems become ever more complex.
We are increasingly dependent upon such information and communications infrastructures and the threats we face are organised and evolving the skills to exploit our dependency to further their interests.

|
Scooped by
Gust MEES
March 26, 2012 7:50 PM
|
Apple’s iOS mobile platform, like its desktop-and-notebook sibling Mac OS X, has garnered a reputation for strong security.
===> But as new holes in iOS's security crop up, this reputation may be exposed to less-than-friendly fire. <===
GM: NOBODY is perfect!

|
Rescooped by
Gust MEES
from Apple, Mac, MacOS, iOS4, iPad, iPhone and (in)security...
March 26, 2012 6:33 PM
|
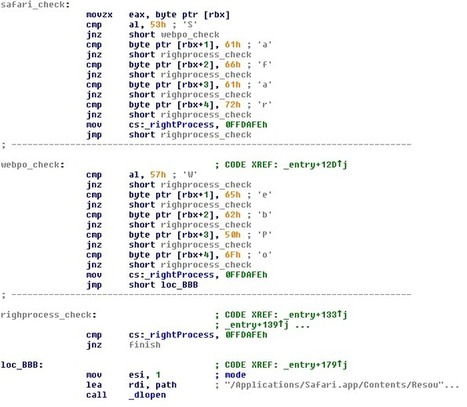
On Monday, I provided steps on how to avoid your Mac being compromised by the Flashback trojan. Today I will provide information on how to locate a Flashback infection.
To better understand the steps below, it is better to also know a bit about Flashback. It's an OS X malware family that modifies the content displayed by web browsers. To achieve this, it interposes functions used by the Mac's browsers.
The hijacked functions vary between variants but generally include CFReadStreamRead and CFWriteStreamWrite: read more...

|
Rescooped by
Gust MEES
from Social Media and its influence
March 21, 2012 5:12 PM
|
"For parents trying to raise kids and give them the technology to be successful, yet also protect them, there's a sense that no one's there to tell folks what steps to take," said Marian Merritt, Internet safety advocate at Symantec.
But laying the responsibility for teaching digital citizenship solely at families' feet would be a mistake, Warren said. "It also has to be a part of ongoing education," she added, noting that kids as young as 2 now commonly use smartphones and other technological devices.
"I hope schools are distributing information and educating (families), ===> but ultimately, parents have a huge role to play (in the process)." <===
Via Gust MEES

|
Scooped by
Gust MEES
March 9, 2012 12:09 PM
|
According to a Google advisory, the zero-day flaws related to universal cross-site scripting (UXSS) and bad history navigation.
===> UPDATE NOW! <===
**************#itsecurity #updates in a Topic called "21st Century Learning and Teaching"? YES, #itsecurity and #cybersecurity as well as #privacy are part of 21st Century Learning and Teaching!***************






![How financial botnets like #Zeus infect computers [video] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/MbtSwAqGO7HtRl8YHo0Fzzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)