 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
November 25, 2014 8:33 AM
|

|
Scooped by
Gust MEES
November 24, 2014 9:41 AM
|

|
Scooped by
Gust MEES
November 23, 2014 12:52 PM
|
An advanced piece of malware, known as Regin, has been used in systematic spying campaigns against a range of international targets since at least 2008. A back door-type Trojan, Regin is a complex piece of malware whose structure displays a degree of technical competence rarely seen. Customizable with an extensive range of capabilities depending on the target, it provides its controllers with a powerful framework for mass surveillance and has been used in spying operations against government organizations, infrastructure operators, businesses, researchers, and private individuals.
It is likely that its development took months, if not years, to complete and its authors have gone to great lengths to cover its tracks. Its capabilities and the level of resources behind Regin indicate that it is one of the main cyberespionage tools used by a nation state.
As outlined in a new technical whitepaper from Symantec, Backdoor.Regin is a multi-staged threat and each stage is hidden and encrypted, with the exception of the first stage. Executing the first stage starts a domino chain of decryption and loading of each subsequent stage for a total of five stages. Each individual stage provides little information on the complete package. Only by acquiring all five stages is it possible to analyze and understand the threat.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO
- https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/

|
Scooped by
Gust MEES
August 19, 2014 12:36 AM
|
Über den eingebauten Bewegungssensor von Smartphones – das Gyroskop – können Hacker Gespräche mithören. Da er sich nicht abschalten lässt, ist prinzipiell jedes Smartphone gefährdet.

|
Scooped by
Gust MEES
August 1, 2014 10:21 AM
|

|
Scooped by
Gust MEES
July 30, 2014 5:59 PM
|
C’est dans un message diffusé sur le blog du système d’anonymisation TOR que l’on apprend, du moins que nous avons la confirmation, du piratage du système TOR. Comme nous vous l’indiquions sur zataz, voilà une dizaine de jours, nous nous étonnions de la disparition d’une conférence dédiée à la surveillance de TOR lors du Black Hat 2014 de Las Vegas. La conférence de d’Alexander Volynkin et Michael McCord devait revenir sur les moyens de rendre beaucoup moins anonymes les utilisateurs du système. TOR, donc, via son blog explique que ce “4 juillet, nous avons trouvé un groupe de relais dont le but supposé était de contourner l’anonymat des utilisateurs. Il semble qu’ils ciblaient les internautes qui utilisent Tor pour accéder ou exploiter des services cachés. Les attaques entraînaient la modification des en-tête de Tor pour s’effectuer.” Bref, nous revoilà avec le coup de 2007 et la lecture des données passant par les ordinateurs permettant à TOR de fournir l’anonymat tant recherché. Une technique d’espionnage démontrée par Dan Egerstad qui avait permis de révéler des centaines de données sensibles d’ambassades ou encore du Dalaïlama.
Article original appartenant à zataz.com : ZATAZ Magazine » Piratage de TOR confirmé par… TOR http://www.zataz.com/piratage-de-tor-confirme-par-tor/#ixzz38zXP7urA
Follow us: @zataz on Twitter

|
Scooped by
Gust MEES
July 3, 2014 3:14 PM
|

|
Scooped by
Gust MEES
June 6, 2014 7:34 PM
|
Wires allow agencies to listen to or record live conversations, in what privacy campaigners are calling a 'nightmare scenario'
Vodafone, one of the world's largest mobile phone groups, has revealed the existence of secret wires that allow government agencies to listen to all conversations on its networks, saying they are widely used in some of the 29 countries in which it operates in Europe and beyond.

|
Scooped by
Gust MEES
June 2, 2014 7:14 PM
|
The US National Security Agency (NSA) has been collecting millions of images from the web and storing them in a database that can be mined by facial recognition software for identifying surveillanc...
According to the Times, the NSA's image-gathering program is now more sophisticated and far-reaching since the program began in 2010, and the NSA's software can identify faces even when the targets were wearing different hair styles and facial hair.
Et si je vous disais qu'il y a dans votre ordinateur un mouchard que vous ne pouvez pas enlever, qui a été mis en place par le constructeur, qui est sur les listes blanches de la plupart des antivirus et dont vous n'avez jamais entendu parler ? La société Kaspersky, spécialisée dans la détection et …
Via Frederic GOUTH, Gust MEES

|
Scooped by
Gust MEES
May 13, 2014 4:05 AM
|
Bereits Anfang des Jahres hatte Jacob Appelbaum behauptet, die NSA fange per Post versandte Geräte ab, um darauf Spyware zu installieren. Nun untermauert Glenn Greenwald diese Anschuldigung: Betroffen seien unter anderem Router und Server von Cisco.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA

|
Scooped by
Gust MEES
May 1, 2014 9:42 AM
|

|
Scooped by
Gust MEES
April 13, 2014 11:40 AM
|
White House officials: policy dates back to January 2014, during review process.
President Barack Obama has explicitly decided that when any federal agency discovers a vulnerability in online security, the agency should come forward, rather than exploit it for intelligence purposes, according to The New York Times, citing unnamed “senior administration officials.”
Learn more:
|

|
Scooped by
Gust MEES
November 24, 2014 2:20 PM
|

|
Scooped by
Gust MEES
November 24, 2014 9:28 AM
|
A sophisticated group known as Regin has targeted high-profile entities around the world. Regin is one of the most sophisticated attack platforms we have ever analysed. The ability to penetrate and...
For more than a decade, a sophisticated group known as Regin has targeted high-profile entities around the world with an advanced malware platform. As far as we can tell, the operation is still active, although the malware may have been upgraded to more sophisticated versions. The most recent sample we've seen was from a 64-bit infection. This infection was still active in the spring of 2014.
The name Regin is apparently a reversed "In Reg", short for "In Registry", as the malware can store its modules in the registry. This name and detections first appeared in anti-malware products around March 2011.
From some points of view, the platform reminds us of another sophisticated malware: Turla. Some similarities include the use of virtual file systems and the deployment of communication drones to bridge networks together. Yet through their implementation, coding methods, plugins, hiding techniques and flexibility, Regin surpasses Turla as one of the most sophisticated attack platforms we have ever analysed.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO
- https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/

|
Scooped by
Gust MEES
November 9, 2014 8:53 AM
|
Dubbed “AirHopper” by the researchers at Cyber Security Labs at Ben Gurion University, the proof-of-concept technique allows hackers and spies to surreptitiously siphon passwords and other data from an infected computer using radio signals generated and transmitted by the computer and received by a mobile phone. The research was conducted by Mordechai Guri, Gabi Kedma, Assaf Kachlon, and overseen by their advisor Yuval Elovici.
The attack borrows in part from previous research showing how radio signals (.pdf) can be generated by a computer’s video card (.pdf). The researchers in Israel have developed malware that exploits this vulnerability by generating radio signals that can transmit modulated data that is then received and decoded by the FM radio receiver built into mobile phones. FM receivers come installed in many mobile phones as an emergency backup, in part, for receiving radio transmissions when the internet and cell networks are down. Using this function, however, attackers can turn a ubiquitous and seemingly innocuous device into an ingenious spy tool. Though a company or agency may think it has protected its air-gapped network by detaching it from the outside world, the mobile phones on employee desktops and in their pockets still provide attackers with a vector to reach classified and other sensitive data.

|
Scooped by
Gust MEES
August 6, 2014 12:51 PM
|
The federal government has concluded there's a new leaker exposing national security documents in the aftermath of surveillance disclosures by former NSA contractor Edward Snowden, U.S. officials tell CNN.

|
Scooped by
Gust MEES
July 30, 2014 6:33 PM
|

|
Scooped by
Gust MEES
July 3, 2014 3:34 PM
|
Der ehemalige NSA-Mitarbeiter William Binney hat vor dem Bundestagsuntersuchungsausschuss ausgesagt. Er berichtete von Geheimverträgen zwischen den USA und deutschen Behörden.
Den Ansatz der NSA, alles wissen, alles sehen zu wollen, sich nicht nur für Organisationen, sondern für einzelne Menschen zu interessieren, sei totalitär, sagte er. Und dass dieses Wissen auch der Kontrolle der eigenen Bevölkerung diene.

|
Scooped by
Gust MEES
July 3, 2014 12:25 PM
|

|
Scooped by
Gust MEES
June 5, 2014 8:16 PM
|
It’s been one year since the Guardian first published the Foreign Intelligence Surveillance Court order, leaked by former NSA contractor Edward Snowden, that demonstrated that the NSA was conducting dragnet surveillance on millions of innocent people. Since then, the onslaught of disturbing revelations, from disclosures, admissions from government officials, Freedom of Information Act requests, and lawsuits, has been nonstop.
On the anniversary of that first leak, here are 65 things we know about NSA spying that we did not know a year ago:
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA

|
Scooped by
Gust MEES
May 22, 2014 8:16 AM
|

|
Scooped by
Gust MEES
May 13, 2014 5:30 AM
|
Today in a published excerpt of his forthcoming book, No Place to Hide,Glenn Greenwald reports, citing documents from 2010, that the NSA intercepts routers and servers being shipped from the United States overseas and compromises them.
Mets-en de côté, ça peut servir.
La NSA ne dévoile pas toujours les failles qu'elle découvre. Il aurait fallu être naïf pour croire le contraire, et de nombreux indices et révélations vont dans ce sens depuis des années. Cela dit, que la Maison blanche l'admette et se fende d'un billet de blog pour détailler les procédures menant à la divulgation ou à la rétention de failles, c'est nouveau.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
|



 Your new post is loading...
Your new post is loading...



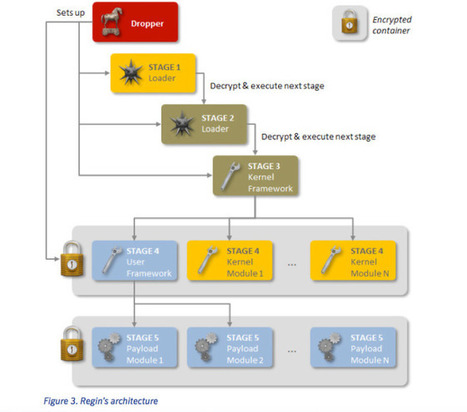
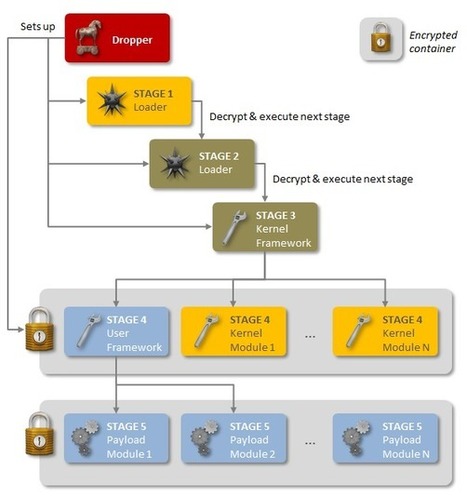



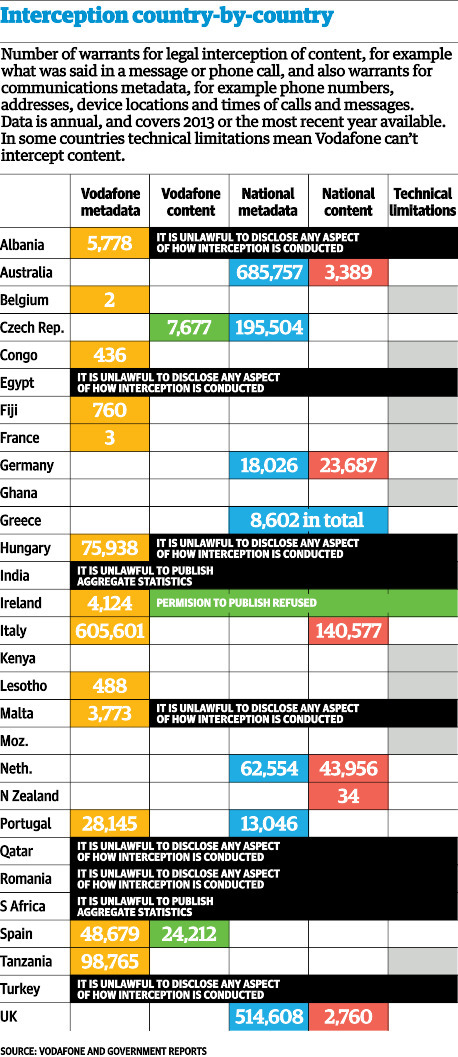

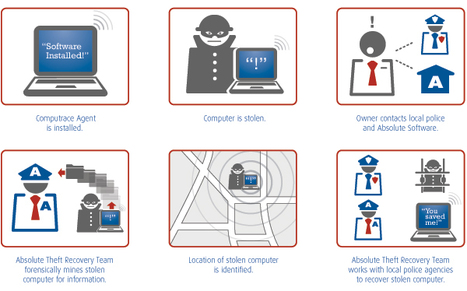





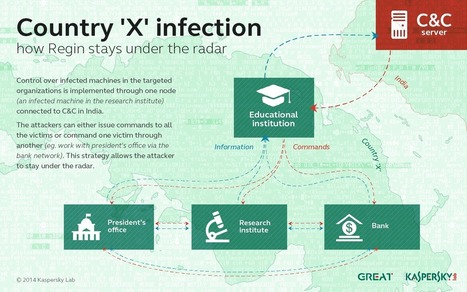
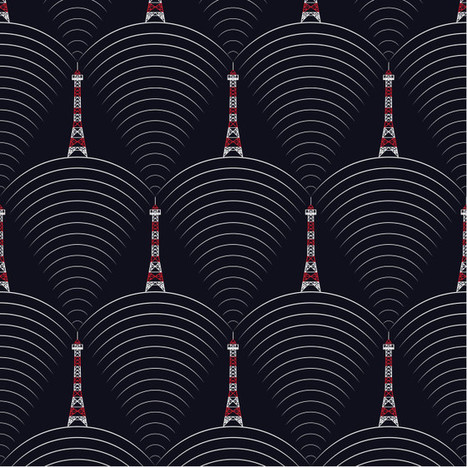

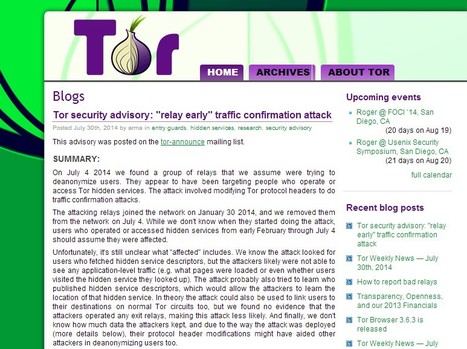



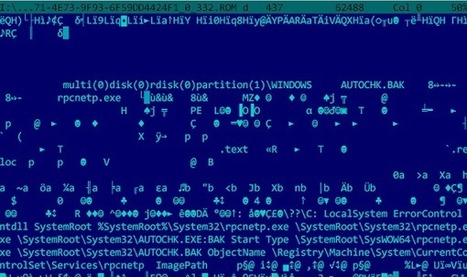








Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO
- https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/