 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
May 27, 2018 10:52 AM
|
The Z-Wave wireless communications protocol used for some IoT/smart devices is vulnerable to a downgrade attack that can allow a malicious party to intercept and tamper with traffic between smart devices.
The attack —codenamed Z-Shave— relies on tricking two smart devices that are pairing into thinking one of them does not support the newer S-Wave S2 security features, forcing both to use the older S0 security standard.
The problem, as security researchers from Pen Test Partners have explained this week, is that all S0 traffic is secured by default with an encryption key of "0000000000000000."
An attacker that can trick a smart device into pairing with another device, a PC, or a smartphone app via the older S0 standard, can later decrypt all traffic exchanged between the two because the decryption key is widely known.
The Pen Test crew say they identified three methods that can be used to trick two devices into pairing via the old S0 instead of S2, even if both support the newer security standard.
Z-Shave attack is pretty dangerous
The Z-Shave attack is dangerous because devices paired via an older version of Z-Wave can become a point of entry for an attacker into a larger network, or can lead to the theft of personal property.
While this flaw might prove frivolous for some devices in some scenarios, it is a big issue for others —such as smart door locks, alarm systems, or any Z-Wave-capable device on the network of a large corporation. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
May 3, 2018 7:43 AM
|
Vulnerable in-vehicle infotainment systems have left some Volkswagen cars open to remote hacking, researchers warn. Over the last few years, automakers like Ford, Jeep, Nissan and Toyota have all suffered car-hacking vulnerabilities in their vehicles. Now, it looks like Volkswagen has been pulled into the mix after researchers discovered that in-vehicle infotainment (IVI) systems in certain Volkswagen-manufactured cars could be remotely hacked. Not only that, but it’s possible to pivot to more critical systems. Related PostsApril 25, 2018 , 11:30 am April 25, 2018 , 9:30 am April 19, 2018 , 1:17 pm The vulnerability was discovered in the Volkswagen Golf GTE and an Audi3 Sportback e-tron, which were both manufactured in 2015. Computest researchers Daan Keuper and Thijs Alkemade, who discovered the flaw, said that under certain conditions the IVI vulnerability could enable attackers to commandeer the on-board microphone to listen in on the conversations of the driver, turn the microphone on and off, and access the system’s complete address book and the conversation history. There is also a possibility of hackers tracking the car through the navigation system at any given time, they said. A Volkswagen spokesperson told Threatpost that the vehicles impacted are those produced with Discover Pro infotainment systems – Golf GTE and Audi A3 e-tron. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cars https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
April 17, 2018 3:22 PM
|
Microsoft präsentiert mit Azure Sphere eine neue Plattform zur Absicherung des Internet of Things (IoT). Dabei setzen die Redmonder auf ARM-Chipsets, Linux und die hauseigene Cloud.
Azure Sphere setzt sich aus speziellen Chipsets, einem Linux-Betriebssystem und Cloud-Diensten zusammen.
(Quelle: Microsoft )
Das Internet der Dinge stellt die IT-Sicherheit in Unternehmen vor gänzlich neue Herausforderungen. Die schiere Masse an vernetzten Endpunkten liefert eine breite Angriffsfläche für Cyberattacken und Malware-Infektionen. So wurden etwa 2016 im sogenannten Mirai-Botnet rund 100.000 IoT-Geräte kompromittiert und für DDoS-Angriffe auf den Web-Dienstleister Dyn missbraucht. Weitreichende Ausfälle von populären Internet-Diensten wie Twitter, Paypal, Netflix oder Spotify waren die Folge.
Dieser Problematik will Microsoft nun mit seiner neuen Azure Sphere begegnen, einer sicheren Plattform für IoT-Geräte. Dabei setzten die Redmonder auf ein mehrschichtiges Sicherheitskonzept, das sich aus einem Verbund aus Hardware und Software sowie der Cloud zusammensetzt. Zertifizierte ARM-Chipsets treffen auf ein Linux-basierte Azure Sphere OS und werden von Sicherheitsdiensten aus der Cloud unterstützt.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
March 1, 2018 9:48 AM
|
New Mirai variant named Mirai OMG
Fortinet has named this variant Mirai OMG —based on the OOMGA string found in some parts of the malware's source code where the term "Mirai" used to be— and this variant now joins a growing Mirai family that also includes variants such as Satori (Okiru), Masuta, and Akuma.
But while Fortinet has not analyzed the traffic flowing through the Mirai OMG network, in theory, it should not be any different from the regular type of traffic that malicious proxy networks have been relaying for years. This includes:
⠕ relaying traffic meant for malware C&C servers to hide their true location
⠕ acting as launching points for dictionary and brute-force attacks to bypass security solutions that limit the number of failed attempts per IP
⠕ launching SQL injection, CSRF, LFI, and XSS attacks to bypass geofencing rules and exploit other web applications
Since Mirai OMG still relies on the classic Mirai spreading technique of brute-forcing devices using weak passwords, changing any IoT equipment's default password should safeguard most users from having their device taken over for a crime spree.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot https://www.scoop.it/t/securite-pc-et-internet/?&tag=Mirai+Botnet

|
Scooped by
Gust MEES
December 7, 2017 4:06 AM
|
According to security researchers, a new IoT botnet has quietly hijacked more than 100,000 routers, readying them for paralysing distributed denial-of-service attacks against websites.
The botnet, which some researchers have dubbed “Satori” (a name given to supernatural mind-reading monsters in Japanese folklore), has increased its activity in recent days – propagating very quickly via a zero-day remote code execution vulnerability in Huawei Home Gateway or Huawei’s Echolife Home Gateway devices, and an already documented vulnerability in Realtek routers.
The exploitation of vulnerabilities allows the botnet to infect routers even when they have been secured with strong passwords.
Through the attack, an army of hundreds of thousands of routers are thought to have been commandeered into the botnet. Some commentators have even suggested that over 280,000 IP addresses have been compromised by the attack in just 12 hours.
Like the Reaper IoT botnet before it, Satori is built on the foundations of the notorious Mirai botnet which knocked major websites offline last year, and whose source code was released onto the internet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Satori+botnet https://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet https://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet&tag=Mirai+Botnet

|
Scooped by
Gust MEES
November 27, 2017 2:35 PM
|
The average home now has around three connected computers and four smart mobile devices. Hardly surprising, considering that 86 per cent of us check the Internet several times a day or more, and that’s outside of work. Chatting, shopping, banking, playing games, listening to music, booking travel and managing our increasingly connected homes. The risk of cyberattack can be the furthest thing from our mind. Every year, Kaspersky Lab’s experts look at the main cyberthreats facing connected businesses over the coming 12 months, based on the trends seen during the year. For 2018, we decided to extract some top predictions that also have big implications for everyday connected life. So what could the hackers be after in 2018? Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
October 24, 2017 9:43 AM
|

|
Scooped by
Gust MEES
October 23, 2017 12:22 PM
|

|
Scooped by
Gust MEES
October 11, 2017 12:04 PM
|

|
Scooped by
Gust MEES
September 19, 2017 12:11 PM
|
There are many forces that are shaping the future of the internet today, from artificial intelligence (AI) and cyberthreats to the internet of things (IoT) and the rising role of government—all of which impact key areas, including digital divides, personal freedoms and rights, as well as media and society.
The internet Society (ISOC)’s 2017 Global internet Report found for example that AI and IoT, for all of their benefits to people’s personal and work lives, could result in a “surveillance society.” Therefore, ethical considerations should steer technology development and guide its use.
The survey also found wide-ranging fears that there are significant forces at work that may undermine the promise of the internet for future generations. For example, many believe that internet freedom will continue to decline around the world due to widespread surveillance, internet shutdowns and content regulation. At the same time, cybersecurity issues will pressure governments to take decisions that could erode the open and distributed global governance of the internet. Measures that may be intended to secure cyberspace may undermine personal rights and freedoms. Without a change of course, online freedoms may be nearing a point of irreversible decline, ISOC found. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=AI http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
July 12, 2017 7:55 AM
|
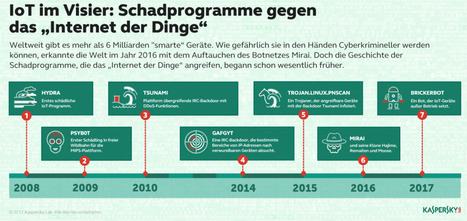
Im Jahr 2016 wurden einige Ereignisse publik, die das Interesse an dem Thema Sicherheit so genannter intelligenter Geräte spürbar verstärkt haben. Zu diesen Ereignissen zählten beispielsweise die bezüglich ihrer Durchschlagskraft rekordverdächtigen DDoS-Attacken auf das französiche Hosting-Unternehmen OVH und den amerikanische DNS-Provider Dyn. Es ist bekannt, dass sie mit Hilfe eines beeindruckenden Botnetzes aus Routern, IP-Kameras, Druckern und anderen Geräten durchgeführt wurden. Außerdem erfuhr die Welt Ende letzten Jahres von einem gigantischen Botnet (fast fünf Millionen Geräte), das sich aus Routern zusammensetzte. Mit dem Hack von Routern musste sich auch die Deutsche Telekom herumschlagen, deren Nutzergeräte mit dem Schädling Mirai infiziert waren. Die Angelegenheit beschränkt sich aber nicht ausschließlich auf Netzwerkausrüstung: Sicherheitsprobleme wurden auch in „intelligenten“ Geschirrspülern von Miele und in AGA-Kochherden gefunden. Den Vogel abgeschossen hat allerdings BrickerBot, der im Gegensatz zu seinen „Kollegen“ angreifbare Geräte nicht nur infizierte, sondern diese auch noch komplett außer Betrieb setzte. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Internet+of+things

|
Scooped by
Gust MEES
July 11, 2017 8:48 AM
|

|
Scooped by
Gust MEES
April 27, 2017 9:52 AM
|
|

|
Scooped by
Gust MEES
May 3, 2018 8:46 AM
|
VW bugs: "Unpatchable" remote code pwnage
Two security researchers have excoriated Volkswagen Group for selling insecure cars. As in: hackable-over-the-internet insecure.
They broke into a recent-model VW and an Audi, via the cars’ internet connections, and were able to jump from system to system, running arbitrary code. Worryingly, they fully pwned the unauthenticated control bus connected to some safety-critical systems—such as the cruise control.
But VW has no way to push updates to its cars, and won’t alert owners to visit a dealer for an update.
Yes, it’s the internet of **** again: Potentially safety-critical bugs caused by the conflict between convenience and security. In this week’s Security Blogwatch, we prefer classic, analog vehicles.
Your humble blogwatcher curated these bloggy bits for your entertainment. Not to mention: Globfinity War…
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cars https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
May 3, 2018 7:25 AM
|
Selon Threat Post, deux chercheurs en sécurité de l'entreprise hollandaise Computest, Daan Keuper et Thijs Alkemade, ont découvert des vulnérabilités dans le logiciel embarqué de la Volkswagen Golf GTE et de l'Audi3 Sportback e-tron
Ces vulnérabilités offrent pas mal d'amusements aux pirates : ouvrir le microphone pour écouter les conversation à l'intérieur du véhicule, accéder au carnet d'adresses complet, à l'historique des conversations, tracer le véhicule à travers son système de navigation, modifier l'affichage de l'écran du système..
Ce n'est pas tout... Poussant leurs investigations, les chercheurs ont constaté qu'il est possible de lire n'importe quel fichier sur le disque du système et même d'exécuter du code arbitraire à distance.
Volswagen commente l'affaire ainsi auprès de Threatpost : "Nous sommes en contact avec Computest depuis la mi-2017", la correction de bugs - en d'autres termes, l'élimination de la vulnérabilité - avait déjà eu lieu début mai 2016."
Fort bien... Toutefois en ce qui concerne les corrections des bugs, les chercheurs sont beaucoup plus nuancés : "Le système que nous avons étudié ne peut pas être mis à jour par l'utilisateur final, un utilisateur doit se rendre chez un revendeur officiel pour recevoir une mise à jour. Cependant, d'après notre expérience, il semble que les voitures qui ont été produites auparavant ne sont pas automatiquement mises à jour lorsqu'elles sont réparées chez un concessionnaire, elles sont donc toujours vulnérables à l'attaque décrite. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cars https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
March 7, 2018 7:32 AM
|
A previously undisclosed flaw in Nike's website allowed anyone with a few lines of code to read server data like passwords, which could have provided greater access to the company's private systems.
An 18-year-old researcher Corben Leo discovered the flaw late last year and contacted Nike through the company's dedicated email address for reporting security flaws, which it advertises on its bug bounty page.
After hearing nothing back for more than three months, Leo contacted ZDNet, which also alerted the company to the vulnerability.
The bug exploited an out-of-band XML external entities (OOB-XXE) flaw that abused how Nike's website parses XML-based files, allowing the researcher to read files directly on the server. OOB-XXE flaws are widely seen as esoteric and difficult to carry out, but can be used to gain deep access to a server's internals. Gaining access to a server's files can disclose other avenues for exploitation, such as remote code execution or pivoting to other connected servers or databases. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=wearables https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
January 20, 2018 6:05 PM
|
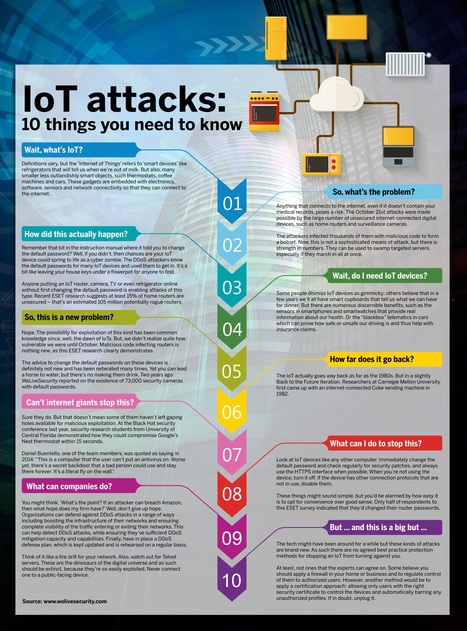
Most readers here have likely heard or read various prognostications about the impending doom from the proliferation of poorly-secured “Internet of Things” or IoT devices. Loosely defined as any gadget or gizmo that connects to the Internet but which most consumers probably wouldn’t begin to know how to secure, IoT encompasses everything from security cameras, routers and digital video recorders to printers, wearable devices and “smart” lightbulbs.
Throughout 2016 and 2017, attacks from massive botnets made up entirely of hacked IoT devices had many experts warning of a dire outlook for Internet security. But the future of IoT doesn’t have to be so bleak. Here’s a primer on minimizing the chances that your IoT things become a security liability for you or for the Internet at large. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
December 6, 2017 9:31 PM
|
A new massive IoT (Internet of Things) botnet dubbed Satori has emerged, which security researchers fear, can launch crippling attacks at any time. The botnet has reportedly already infected over 280,000 IP addresses in just 12 hours, enslaving hundreds of thousands of home routers by exploiting a recently discovered zero-day vulnerability.
Satori, which reportedly means "awakening" in Japanese, is actually the infamous Mirai botnet's successor. Since Mirai's authors made the botnet's source code public last year, cybercriminals have been pushing out new variants of Mirai. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet&tag=Mirai+Botnet

|
Scooped by
Gust MEES
November 18, 2017 6:36 PM
|
Les deux enceintes intelligentes de Google et Amazon, le Google Home et l’Amazon Echo, victimes de la faille Bluetooth BlueBorne.
Des chercheurs ont réussi à prouver que la faille Bluetooth BlueBorne impactait aussi les enceintes intelligentes Google Home et l’Amazon Echo. Révélées il y a quelques semaines, huit failles critiques de Bluetooth ont récemment étaient révélées. Elles affectent des milliards d’appareils Android, iOS, Windows et Linux. Voilà que les deux assistants des deux géants du web sont aussi impliqués dans cet énorme « merdier » numérique comme le confirme la société Armis. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=BlueBorne

|
Scooped by
Gust MEES
October 23, 2017 1:26 PM
|

|
Scooped by
Gust MEES
October 18, 2017 3:07 PM
|
BRUSSELS (Reuters) - Some smartwatches for children sold in Europe pose security risks, including potentially allowing hackers to take control of and track a watch, the EU’s main consumer lobby said on Wednesday, following a new report by one of its members.
The affected smartwatches, which use the Global Position System (GPS) to allow parents to track their child’s location and communicate with them through their mobile phones, do not have sufficient protection, or firewalls, to stop computer hackers, the Norwegian Consumer Council said.
The council also accused some manufacturers of violating EU data protection laws by not stating clearly the risks in their terms and conditions.
“These watches should not find their way into our shops,” Monique Goyens, the director general of the European Consumer Organisation BEUC - of which the Norwegian council is a member - said in a statement. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=wearables
With the IoT, we see everything has become internet-connected in some way. This has its benefits, but its dangers as well. Recently, hackers stole 10 gigabytes worth of data from a casino by hacking through a casino’s fish tank. The fish tank’s cleaner was connected to the internet to measure sensors, temperature and cleanliness, but left the door open for the casino’s network. This is only one example of the dangers of IoT, and there are still many issues out there that people need to be aware of. Today, we will go deeper problematic areas of the IoT so you can become aware of its dangers. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot
Via Ana Alonso, Oskar Almazan, Mark E. Deschaine, PhD

|
Scooped by
Gust MEES
September 8, 2017 10:29 AM
|
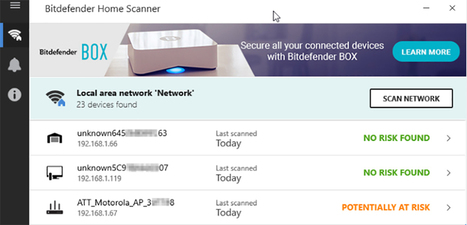
À l’heure où la sécurité des objets connectés fait toujours débat, l’éditeur de sécurité Bitdefender lance un outil gratuit permettant d’analyser l’intégralité des appareils connectés au réseau domestique. Un outil de prévention et de promotion pour les produits payants de l’éditeur, dont la récente Bitdefender Box. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
July 11, 2017 11:11 AM
|
The Internet of Things (IoT) market has begun to take off. Consumers can buy connected versions of nearly every household appliance available. However, despite its increasing acceptance by consumers, recent studies of IoT devices seem to agree that “security” is not a word that gets associated with this category of devices, leaving consumers potentially exposed.
To find out for ourselves how IoT devices fare when it comes to security, we analyzed 50 smart home devices that are available today. We found that none of the devices enforced strong passwords, used mutual authentication, or protected accounts against brute-force attacks. Almost two out of ten of the mobile apps used to control the tested IoT devices did not use Secure Sockets Layer (SSL) to encrypt communications to the cloud. The tested IoT technology also contained many common ulnerabilities.
All of the potential weaknesses that could afflict IoT systems, such as authentication and traffic encryption, are already well known to the security industry, but despite this, known mitigation techniques are often neglected on these devices. IoT vendors need to do a better job on security before their devices become ubiquitous in every home, leaving millions of people at risk of cyberattacks. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Internet+of+things

|
Scooped by
Gust MEES
May 11, 2017 9:29 AM
|
|



 Your new post is loading...
Your new post is loading...


















![The Hidden Dangers Of The Internet of Things [Infographic] | #SmartData #CyberSecurity | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/Ac_CI-oAQLvYlJrtR7xzBjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








The Z-Wave wireless communications protocol used for some IoT/smart devices is vulnerable to a downgrade attack that can allow a malicious party to intercept and tamper with traffic between smart devices.
The attack —codenamed Z-Shave— relies on tricking two smart devices that are pairing into thinking one of them does not support the newer S-Wave S2 security features, forcing both to use the older S0 security standard.
The problem, as security researchers from Pen Test Partners have explained this week, is that all S0 traffic is secured by default with an encryption key of "0000000000000000."
An attacker that can trick a smart device into pairing with another device, a PC, or a smartphone app via the older S0 standard, can later decrypt all traffic exchanged between the two because the decryption key is widely known.
The Pen Test crew say they identified three methods that can be used to trick two devices into pairing via the old S0 instead of S2, even if both support the newer security standard.
Z-Shave attack is pretty dangerous
The Z-Shave attack is dangerous because devices paired via an older version of Z-Wave can become a point of entry for an attacker into a larger network, or can lead to the theft of personal property.
While this flaw might prove frivolous for some devices in some scenarios, it is a big issue for others —such as smart door locks, alarm systems, or any Z-Wave-capable device on the network of a large corporation.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot