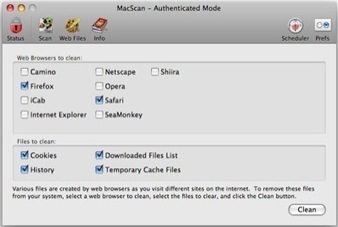
SecureMac released MacScan 2.9.3, which features tracking cookie detection and cleaning for Google’s Chrome browser.
MacScan is the premier Macintosh security program, protecting you against the latest malware and privacy threats for Apple Mac OS X, offering protection against keystroke loggers, trojan horses, and other spyware.
Read more...



 Your new post is loading...
Your new post is loading...