 Your new post is loading...
 Your new post is loading...
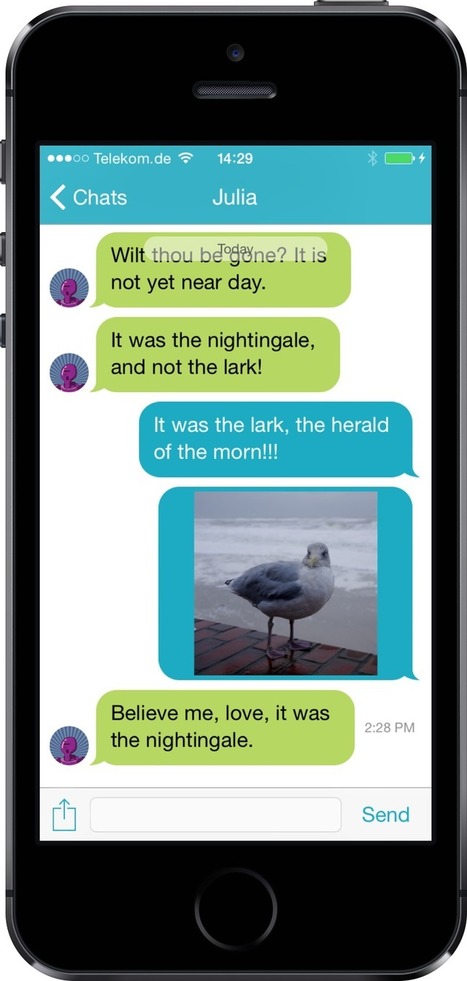
You want a guaranteed untappable way to communicate with your friends, family and coworkers or customers? Without any SMS charges? You want it to be fast and simple, and run within your own server environment too? With schmoose we offer you a reliable messaging app for sending encrypted messages. Exchange short messages, images, videos, photos, or documents between all kinds of recipients and end devices. Using end-to-end encryption – free of media breaks, uninvited guests, complications, or interruptions while moving between any desired end devices.
Via Gust MEES
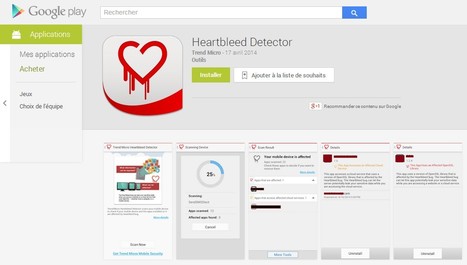
Trend Micro Heartbleed Detector scans your ANDROID mobile device for possible risk and helps you stay away from the Heartbleed bug.What does Heartbleed Detector check on yo...
Via Gust MEES

|
Rescooped by
Gerrit Bes
from ICT Security Tools
March 27, 2014 6:03 AM
|
A whirlwind guide to free network security, anti-virus products
Check them out!
Find out more:
Via Gust MEES

|
Rescooped by
Gerrit Bes
from Social Media and its influence
March 10, 2014 6:36 AM
|
I opted out of Klout years ago. Before I was ever listed, ranked, or nominated by Forbes, Huffington Post Tech, The Shorty Awards – before any of that. Before l
Via Gust MEES
1. Appoint a security lead
2. Review the data you intend to collect and maintain
3. Understand the differences between mobile platforms
4. Don’t rely on a platform alone to protect your users
5. Create secure user credentials
6. Encrypt any data that is transmitted
7. Exercise caution and use due diligence on libraries and other third-party code
8. Consider protecting data you store on a user’s device
9. Protect your servers, too
10. Don’t store passwords in plain text
11. You’re not done once you release your app. Stay aware and communicate with your users
12. If you’re dealing with financial data, health data, or kids’ data, make sure you understand applicable standards and regulations
If your app deals with kids’ data, health data, or financial data, ensure you’re complying with relevant rules and regulations, which are more complex. The FTC offers details on the regulations that your business needs to be aware of in the following guides:
Via Gust MEES
We've teamed up with Common Sense Media to compile some of the best resources for parents, teachers and administrators to guide students to become positive digital citizens and leaders. | See more about digital citizenship, internet safety and common sense.
Via Gust MEES

|
Rescooped by
Gerrit Bes
from 21st Century Learning and Teaching
February 3, 2014 5:12 AM
|
Introduction Blogging is not as simple as throwing up a few posts and hoping for the best… at least not if you want to start a blog that’s epic, draws in loyal readers, and makes money. Before you start a blog you need to figure out your niche and draw up a launch plan. It’s …
Via Gust MEES

|
Rescooped by
Gerrit Bes
from ICT Nieuws
February 1, 2014 4:40 AM
|

|
Rescooped by
Gerrit Bes
from Social Media and its influence
January 30, 2014 12:14 PM
|
Facebook today launched new features to help marketers reach people across devices and encourage them to take action. Custom Audiences now allows businesses to deliver targeted messages ...
Via Gust MEES
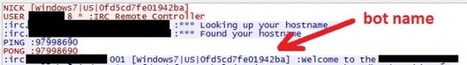
Multi-platform threat exploits old Java flaw, gains persistence. Researchers have uncovered a piece of botnet malware that is capable of infecting computers running Windows, Mac OS X, and Linux that have Oracle's Java software framework installed. The cross-platform HEUR:Backdoor.Java.Agent.a, as reported in a blog post published Tuesday by Kaspersky Lab, takes hold of computers by exploiting CVE-2013-2465, a critical Java vulnerability that Oracle patched in June. The security bug is present on Java 7 u21 and earlier. Once the bot has infected a computer, it copies itself to the autostart directory of its respective platform to ensure it runs whenever the machine is turned on. Compromised computers then report to an Internet relay chat channel that acts as a command and control server.
Via Gust MEES

|
Rescooped by
Gerrit Bes
from 21st Century Learning and Teaching
January 24, 2014 5:25 AM
|
Compliance, standards, a shortage in IT security skills and budgets are reasons behind the failure of cyber security, experts conclude at French information security conference
Via Gust MEES

|
Rescooped by
Gerrit Bes
from Best Freeware Software
January 19, 2014 8:35 AM
|

|
Rescooped by
Gerrit Bes
from 21st Century Learning and Teaching
January 18, 2014 4:57 AM
|
. . Cyber-Security And Privacy Knowledge As Skills In The 21st Century Are NOT Yet Enough Taught And Present, WHY!? . Did YOU realize already that WE are living in the 21st Century and that WE near...
Via Gust MEES
|

|
Rescooped by
Gerrit Bes
from ICT Nieuws
April 21, 2014 5:56 AM
|
At the UNESCO Mobile Learning Week 2014 I sat on a panel titled Emerging Trends and New Technology – considered in the context of mobile learning. Below are the notes of the key points that I made. Note: The issue of Emerging Trends and New Technology begs the question: for who? For students in California,…
Via Dr. Susan Bainbridge, Jeroen Rougoor
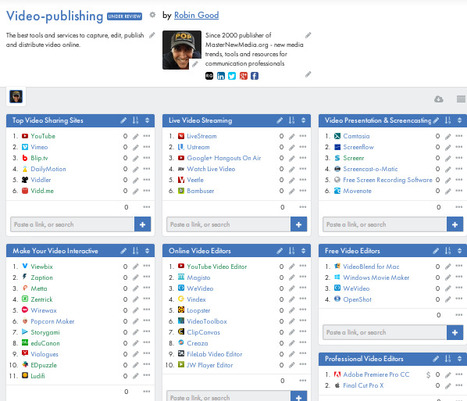
The best tools and services to capture, edit, publish and distribute video online.
Via Robin Good, Gust MEES

|
Rescooped by
Gerrit Bes
from ICT Security Tools
March 16, 2014 4:37 AM
|
Multi-device protection for a worry-free online life. Protect all your computers, smartphones and tablets with one simple solution.
Via Gust MEES
"The rise of Google, the rise of Facebook, the rise of Apple, I think are proof that there is a place for computer science as something that solves problems that people face every day." By Eric Sch...
Via Timo Ilomäki, Gust MEES

|
Rescooped by
Gerrit Bes
from Social Media and its influence
March 8, 2014 5:41 AM
|
Getty Images' vast library of award-winning professional photographs and illustrations is now at the disposal of every WordPress.com blogger.
Via Gust MEES

|
Rescooped by
Gerrit Bes
from 21st Century Learning and Teaching
February 2, 2014 3:31 AM
|
There is no doubt we now live in challenging times on Planet Earth. Our burgeoning human population is seven billion and rising. Resources are diminishing and our iconic species are disappearing ...
Via Gust MEES

|
Rescooped by
Gerrit Bes
from 21st Century Learning and Teaching
February 1, 2014 4:37 AM
|
Content curation is a great way to shine on the Web. But how do we make this easy and practical? At Scoop.it we're constantly amazed by the great work our awes
Via Gust MEES

|
Rescooped by
Gerrit Bes
from 21st Century Learning and Teaching
January 30, 2014 12:15 PM
|
Yes, everything you do online is being tracked. Your searches, the videos you watch, transactions, social events, even crime. Scandalous crimes. With a little help, especially with our guides, you're still able to remain anonymous on the Internet. But understanding how you're being tracked is an important lesson, as are the little things you can…
Via Gust MEES

|
Rescooped by
Gerrit Bes
from 21st Century Learning and Teaching
January 22, 2014 5:51 AM
|
Just like a tattoo, your digital reputation is an expression of yourself. It is formed and added to by you and others over time. In her Digital Tattoo presentation at ISTE 2013 (also in video forma... Managing your digital footprint starts with asking questions like: Who are you? What do you stand for? What are your passions and beliefs? The important lesson with managing your digital footprint is that ===> everything we do online should represent who we are and what we stand for and we must have the knowledge that this representation will stick with us potentially forever. <===
Via Gust MEES

|
Rescooped by
Gerrit Bes
from 21st Century Learning and Teaching
January 19, 2014 8:36 AM
|
Security researchers at Proofpoint have uncovered the very first wide-scale hack attack that involved television sets and at least one refrigerator.
Via Gust MEES
|



 Your new post is loading...
Your new post is loading...



























![You’re Being Watched Online [Infographic] | Latest Social Media News | Scoop.it](https://img.scoop.it/OvKQC9BrjFcGPU1tcsLHojl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)















You want a guaranteed untappable way to communicate with your friends, family and coworkers or customers? Without any SMS charges? You want it to be fast and simple, and run within your own server environment too? With schmoose we offer you a reliable messaging app for sending encrypted messages. Exchange short messages, images, videos, photos, or documents between all kinds of recipients and end devices. Using end-to-end encryption – free of media breaks, uninvited guests, complications, or interruptions while moving between any desired end devices.