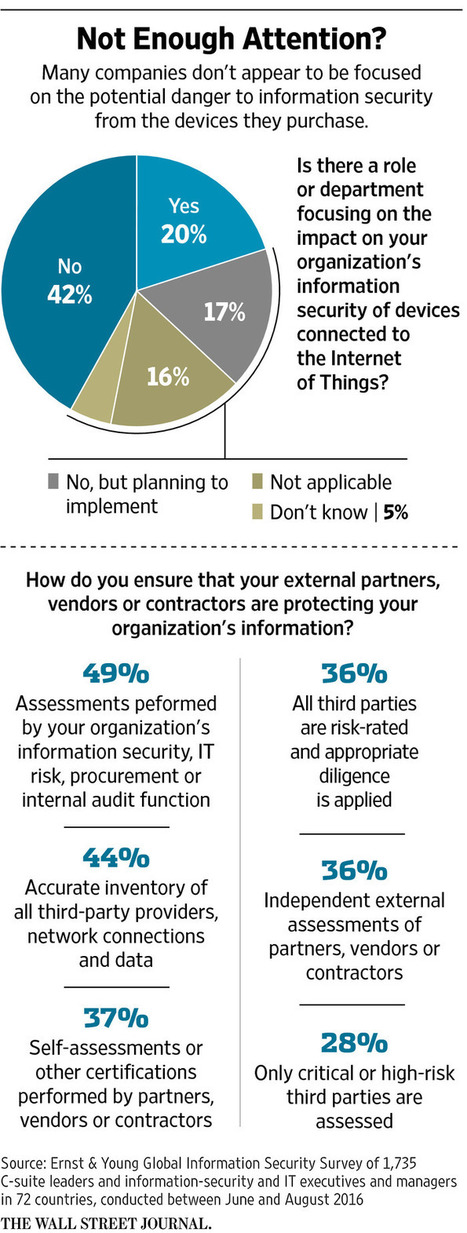
A majority of internet users can answer fewer than half the questions correctly on a difficult knowledge quiz about cybersecurity issues and concepts.
Follow, research and publish the best content
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login

Cybersecurity Leadership
24.5K views |
+6 today
Follow
Filter by date
Tags
A reference resource for the CIO and the CISO on cyber security, looking beyond the technology horizon into leadership, management, culture, governance, resilience and the real dynamics of security transformation
Curated by
JC Gaillard
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
As cyberthreats grow in numbers and complexity, the future of cybersecurity increasingly depends on an open, trusting CISO-board relationship.
93% of respondents will use sensitive data in an advanced technology (defined as cloud, software as a service or SaaS, big data, IoT and container).
New report shows that most of the few women in cybersecurity jobs felt some discrimination. Industry needs to change mindset in order to make the most of different minds.
Something as simple as an uncharacteristic turn of phrase can clue people into an email’s illegitimacy.
Johanna Vazzana knew the job she’d applied for was a stretch. Vazzana, now a cybersecurity strategist working at Mitre, was interviewing early in her
If business leaders and directors continue to view cybersecurity as mainly a matter for the IT department, they will leave their companies exposed to significant risks.
An effective Information Security Governance Framework is one essential piece of the jigsaw. It should distribute roles and responsibilities clearly amongst all stakeholders
As cyber security breaches become increasingly common, a security consultant explores how recent headline breaches have impacted company valuations
Chris Drake, CEO at Armor, talks about the frustration that he sees in the cybersecurity industry as he continues to meet CIOs and CISOs in the field.
Companies that are smart about security ask a lot of questions before buying workplace technology.
To combat cyberattacks, companies need to understand both hackers’ tactics and their mindsets.
In several articles last year, we explored how to organise InfoSec for success and how to best establish the reporting line of the CISO. |
Leveraging the cloud for security applications is becoming increasingly accepted – and required – as we move into a 24/7 digital world.
New standards and regulations are beginning to govern how companies protect customers' data. Companies ignore this vital issue at their peril, both financially and legally.
The Cybersecurity Disclosure Act of 2017 (bill, S536) seeks to require a board level statement of cyber security expertise or practice in annual SEC filings.
No matter how well a company develops its technical cybersecurity defenses, if employee culture is not addressed, there will always be a weak link that cyber-criminals can exploit to devastating effect. How can a company develop an employee culture that respects cybersecurity?
It is easy to say that risk management should be embedded into business processes such as strategic planning. But is it that easy to accomplish in practice?
It's time to stop commissioning studies and get on with fixing the culture
BYOD challenges go way beyond virtualisation or containerisation, and are rooted in corporate culture, and issues of accountability and liability
It can be challenging to find the right on-demand internal expertise at your fingertips when you are in the thick of a security incident. This is why establishing a relationship in advance with a firm that specializes in incident response and forensics is a shrewd move.
Cyber insurance is growing in importance along with cyber security. But business leaders should look before they leap
Cybersecurity is at the top of boardroom agendas. Stephen Bonner of Deloitte asks whether boards need a member who is a dedicated cyber expert.
With organizations going through digital transformation,IT leaders must fundamentally change how information security services are delivered, and make security part of everyone's job.
What are some of the key insights a business could expect from a scenario showcasing cyber risks? |