From social networking to online shopping, banking, and surfing the web – precautions are needed to ensure our phones and our information are safe from malware attacks and cybercriminals. Learn more about smartphone security.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Gust MEES's curator insight,
June 23, 2013 10:28 AM
"This malware was found to have used a number of advanced techniques, which makes it interesting. The malware leverages Google Docs to perform redirection to evade callback detection." 
Jason Toy's curator insight,
June 23, 2013 11:04 AM
Interesting read. Looks like FireEye's sandboxing techniques paid off in this regard.

Gust MEES's curator insight,
February 25, 2013 1:44 PM
A MUST check for Linux users!!!
Check also:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Nobody-is-perfect
- http://www.scoop.it/t/securite-pc-et-internet?q=Linux
|

Gust MEES's curator insight,
June 26, 2013 5:42 PM
As Soghoian and other critics admit, the end-to-end encryption included with iMessage may make it impossible for Apple to decrypt conversations, at least in some circumstances. But in the absence of key details that Apple has steadfastly declined to provide, customers who are especially concerned about their privacy would do well to assume otherwise.
===> Nobody Is Perfect!!! <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

Gust MEES's curator insight,
June 26, 2013 5:50 PM
As Soghoian and other critics admit, the end-to-end encryption included with iMessage may make it impossible for Apple to decrypt conversations, at least in some circumstances. But in the absence of key details that Apple has steadfastly declined to provide, customers who are especially concerned about their privacy would do well to assume otherwise.
===> Nobody Is Perfect!!! <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

Gust MEES's curator insight,
February 25, 2013 1:24 PM
Check also:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
- http://www.scoop.it/t/securite-pc-et-internet?tag=Nobody-is-perfect
- http://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
- http://gustmees.wordpress.com/2013/01/23/is-your-professional-development-up-to-date/

Gust MEES's curator insight,
February 25, 2013 1:26 PM
Check also:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
- http://www.scoop.it/t/securite-pc-et-internet?tag=Nobody-is-perfect
- http://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
- http://gustmees.wordpress.com/2013/01/23/is-your-professional-development-up-to-date/ |






![Download with Caution! McAfee Identifies Risky Mobile App Sources [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/nlwfbsAWi3frp2_-nQ6pvTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

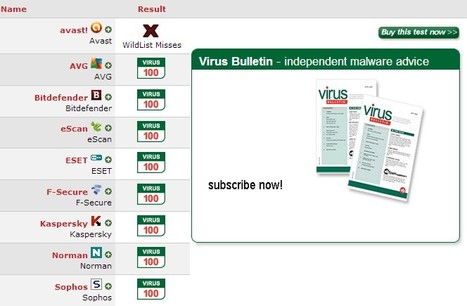

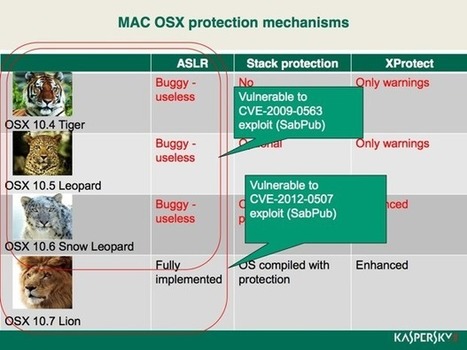





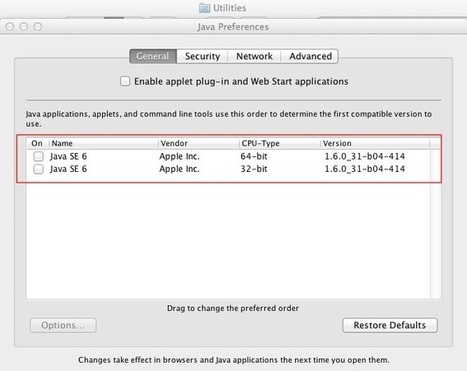





Why You Need Mac Antivirus Software.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security