 Your new post is loading...
 Your new post is loading...
New measures to boost key competences and digital skills, as well as the European dimension of education
Brussels, 17 January 2018
To follow up on the Gothenburg Summit, the European Commission has today adopted new initiatives to improve key competences and digital skills of European citizens, to promote common values and pupils' awareness of the functioning of the European Union.
The new proposals come only two months after European Heads of State and Government discussed education, training and culture at the Gothenburg Summit in November 2017. They are intended to reduce socio-economic inequalities, whilst sustaining competitiveness in order to build a more united, stronger and more democratic Europe. 1. A Council Recommendation on Key Competences for Lifelong Learning: Building on the Recommendation on Key Competences adopted in 2006, this proposal brings forward important updates reflecting the rapid evolution of teaching and learning since then. It aims to improve the development of key competences of people of all ages throughout their lives and to provide guidance to Member States on how to achieve this objective. A particular focus is placed on promoting entrepreneurial drive and innovation-oriented mindsets in order to unlock personal potential, creativity and self-initiative. Moreover, the Commission is recommending steps to foster competences in science, technology, engineering and mathematics (STEM) and motivate more young people to embark on a career in these fields. The proposals made today should also be seen as part of the answer to urgently improve European education systems to face the many challenges highlighted in the latest PISA survey. More generally, the measures will support Member States in better preparing learners for changing labour markets and for active citizenship in more diverse, mobile, digital and global societies. 2. A Digital Education Action Plan that outlines how the EU can help people, educational institutions and education systems better adapt to life and work in an age of rapid digital change by: making better use of digital technology for teaching and learning; developing the digital competences and skills needed for living and working in an age of digital transformation; and improving education through better data analysis and foresight. Initiatives include supporting schools with high-speed broadband connections, scaling up a new self-assessment tool for schools on the use of technology for teaching and learning (SELFIE) and a public awareness campaign on online safety, media literacy and cyber hygiene. 3. A Council Recommendation on common values, inclusive education and the European dimension of teaching: This initiative proposes ways in which education can help young people understand the importance of and adhere to common values set out in Article 2 of the Treaty of the European Union. It aims at strengthening social cohesion and contributing to fight the rise of populism, xenophobia, divisive nationalism and the spreading of fake news. The proposal also strengthens inclusive education to promote quality education for all pupils as well as the European dimension of teaching, so children also learn about Europe's common heritage and diversity and get a good understanding of the functioning of the EU. To support these aims, the Commission will take steps to increase virtual exchanges among schools, notably through the successful e-Twinning network, and boost school mobility through the Erasmus+ programme. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=EU
Via Gust MEES
Successfully hiding messages in images has already been done, but is it possible to deliver an exploit in one - and run it?
Saumil Shah, founder and CEO of Net-Square, has demonstrated at the Hack in the Box Amsterdam 2015 that it's possible, and has posited that such attacks are more than likely to crop up in the near future, as he can't be the only one who thought about this, tried it and succeeded.
He is not the first one to try and hide exploits in images. But he created Stegosploit, a technology that lets attackers deliver executable JavaScript code via images, and trigger them, too.
The technology opens the door for attacks executed as simply as pointing users to sites containing a booby-trapped image or delivering the image via email. By virtue of simply viewing the image, the exploit code is triggered and can deliver malware on the victim's computer.
"A single file can be rendered as a perfectly valid HTML file, executed as a perfectly valid Javascript file, and displayed as a perfectly valid image, all at the same time," he explains.
"Stegosploit is the result of malicious exploit code hidden within pixels of the image carrying it. The image however, is a multi format container, which also contains the code required to decode the steganographically encoded pixels to execute the exploit."
This type of attack won't show in network traffic, he pointed out, be invisible to the naked eye, and the image will "autorun" in the browser.
In order to make the attack payload look harmless and not trigger defenses, Shah split it into two: dangerous pixel data (exploit code), and a safe decoder.
Via Gust MEES
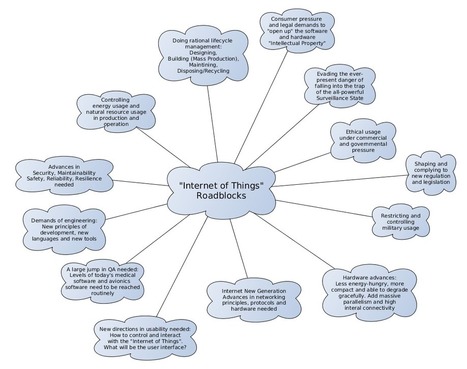
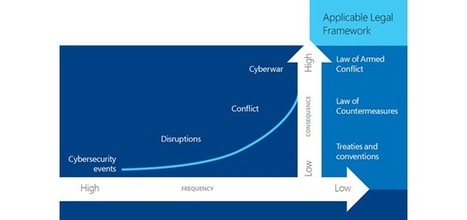
The Internet of Everything (IoE) represents the next “world-changing” revolution, after the Industrial Revolution of 1750 – 1900, and following the Computer & Internet revolution which started in the 1950’s. It is an exciting scenario in which objects, personal devices, even animals communicate, take Intelligent decisions, and autonomous actions on their own without human interaction. This revolution will completely transform industrial sectors and the entire world, for all of us, in ways as powerful as the Industrial Revolution and even more. It is our future, and it is happening now.
How is it happening? For an Evolution of Technologies, and with a Revolution of Minds… Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=smart-TV - http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things - http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things - http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/
Via Gust MEES, Lynnette Van Dyke
Le Conseil de gouvernement a adopté, ce mercredi 21 janvier, un projet d’arrêté grand-ducal destiné à fixer la gouvernance en matière de gestion de la sécurité de l’information et modifiant l’arrêté grand-ducal déterminant l’organisation et les attributions du CERT gouvernemental. Le projet propose la création d’une Agence nationale de la sécurité des systèmes d’information (ANSSI) pour le secteur public et les infrastructures critiques, avec, en parallèle, "une amélioration de la collaboration avec les services se trouvant en dehors du périmètre couvert par l’Agence, qui se traduira par la conclusion d’accords de coopération".
Via Gust MEES
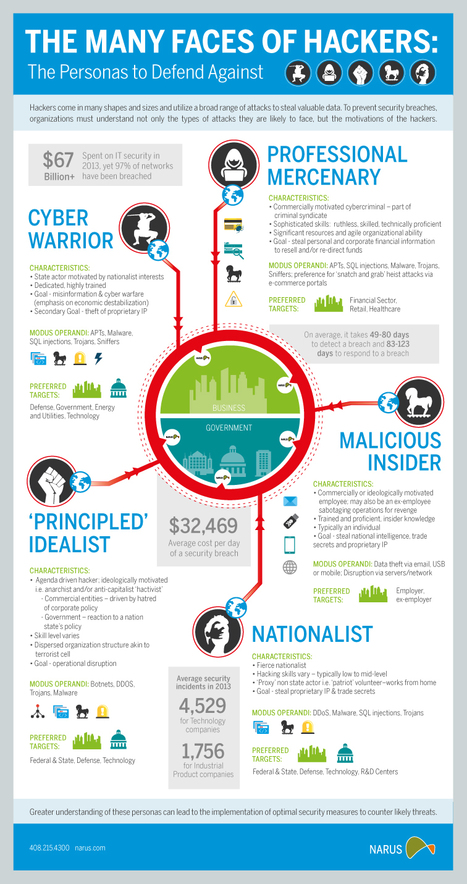
How many of these hacker personas are you dueling with in your organization?
Via Gust MEES, Next Level
|
Attackers have installed malicious firmware on nearly 200 Cisco routers used by businesses from over 30 countries.
Via Gust MEES
Vint Cerf is known as a "father of the Internet," and like any good parent, he worries about his offspring -- most recently, the IoT.
"Sometimes I'm terrified by it," he said in a news briefing Monday at the Heidelberg Laureate Forum in Germany. "It's a combination of appliances and software, and I'm always nervous about software -- software has bugs."
The Internet of Things will offer the ability to manage many of the appliances we depend on, acknowledged Cerf, who won the Turing Award in 2004. With its ability to continuously monitor such devices, it also promises new insight into our use of resources, he said.
Devices such as Google's Nest thermostat, for instance, can "help me decide how well or poorly I've chosen my lifestyle to minimize cost and my use of resources -- it can be an important tool," he said.
As with so many technological tools, however, there are plenty of potential downsides. Safety is one of them.
Cerf is now vice president and chief Internet evangelist at Google, but you won't find him enjoying any of the massage chairs the company provides for its employees. "I know they're run by software -- I worry they will fold up on me," he quipped.
As more such appliances are run by software, people will be increasingly reliant on programmers' ability to write good code, he pointed out.
"It's fraught with issues, some technical and some legislative," he said. "Who is liable when an appliance doesn't work the way it should, and what if that's a software question?"
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cars
Via Gust MEES
Um die Schüler auf die Arbeitsplätze von morgen optimal vorzubereiten, muss die Schule sich der modernen Informations- und Kommunikationstechnologien bedienen. Am Mittwoch stellte Bildungsminister Claude Meisch die Strategie "Digital (4) Education" vor, mit der die Schüler von heute, deren Lebenswirklichkeit bereits in weiten Teilen eine digitale ist, auf morgen vorbereitet werden sollen.
Via Gust MEES
Das Hilfsprogramm Enhanced Mitigation Experience Toolkit (EMET) versucht zu verhindern, dass Sicherheitsrisiken unter Windows ausgenutzt werden.
Via Gust MEES
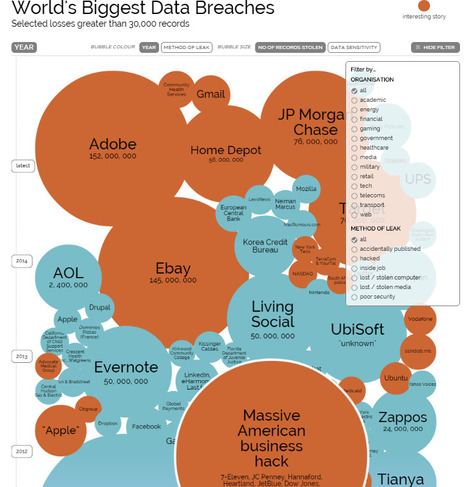
The 27001 Academy has produced an informative infographic that illustrates key details of the nearly 800 reported data breaches in the U.S. that occurred in 2014 - up about 20% from 2013.
Surprisingly, despite the sharp increase in the number of breaches seen last year, the actual number of records that were compromised was down more than
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=DATA-BREACHES
Via Gust MEES
The Internet has by and large been a cause for good, driving economic growth across developed and emerging economies, connecting individuals and communities to previously unattainable services, and propelling innovation online, as well as offline. Today, all over the world public utilities, banks, and governments use the Internet, cloud services, and mobile technology to enhance their productivity. Unfortunately, the benefits of greater connectivity have also brought about increased information
Via Gust MEES
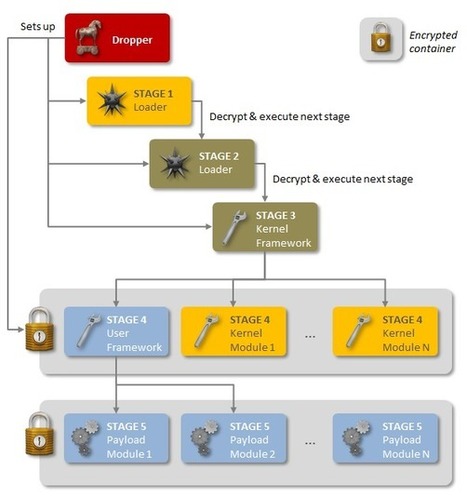
An advanced piece of malware, known as Regin, has been used in systematic spying campaigns against a range of international targets since at least 2008. A back door-type Trojan, Regin is a complex piece of malware whose structure displays a degree of technical competence rarely seen. Customizable with an extensive range of capabilities depending on the target, it provides its controllers with a powerful framework for mass surveillance and has been used in spying operations against government organizations, infrastructure operators, businesses, researchers, and private individuals.
It is likely that its development took months, if not years, to complete and its authors have gone to great lengths to cover its tracks. Its capabilities and the level of resources behind Regin indicate that it is one of the main cyberespionage tools used by a nation state.
As outlined in a new technical whitepaper from Symantec, Backdoor.Regin is a multi-staged threat and each stage is hidden and encrypted, with the exception of the first stage. Executing the first stage starts a domino chain of decryption and loading of each subsequent stage for a total of five stages. Each individual stage provides little information on the complete package. Only by acquiring all five stages is it possible to analyze and understand the threat.
Via Gust MEES
|



 Your new post is loading...
Your new post is loading...

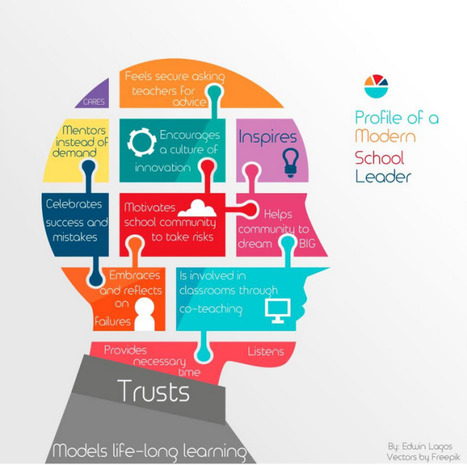































1. A Council Recommendation on Key Competences for Lifelong Learning: Building on the Recommendation on Key Competences adopted in 2006, this proposal brings forward important updates reflecting the rapid evolution of teaching and learning since then. It aims to improve the development of key competences of people of all ages throughout their lives and to provide guidance to Member States on how to achieve this objective. A particular focus is placed on promoting entrepreneurial drive and innovation-oriented mindsets in order to unlock personal potential, creativity and self-initiative. Moreover, the Commission is recommending steps to foster competences in science, technology, engineering and mathematics (STEM) and motivate more young people to embark on a career in these fields. The proposals made today should also be seen as part of the answer to urgently improve European education systems to face the many challenges highlighted in the latest PISA survey. More generally, the measures will support Member States in better preparing learners for changing labour markets and for active citizenship in more diverse, mobile, digital and global societies.
2. A Digital Education Action Plan that outlines how the EU can help people, educational institutions and education systems better adapt to life and work in an age of rapid digital change by:
making better use of digital technology for teaching and learning;
developing the digital competences and skills needed for living and working in an age of digital transformation; and
improving education through better data analysis and foresight.
Initiatives include supporting schools with high-speed broadband connections, scaling up a new self-assessment tool for schools on the use of technology for teaching and learning (SELFIE) and a public awareness campaign on online safety, media literacy and cyber hygiene.
3. A Council Recommendation on common values, inclusive education and the European dimension of teaching: This initiative proposes ways in which education can help young people understand the importance of and adhere to common values set out in Article 2 of the Treaty of the European Union. It aims at strengthening social cohesion and contributing to fight the rise of populism, xenophobia, divisive nationalism and the spreading of fake news. The proposal also strengthens inclusive education to promote quality education for all pupils as well as the European dimension of teaching, so children also learn about Europe's common heritage and diversity and get a good understanding of the functioning of the EU. To support these aims, the Commission will take steps to increase virtual exchanges among schools, notably through the successful e-Twinning network, and boost school mobility through the Erasmus+ programme.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=EU