Eight years ago, Polish hacker Joanna Rutkowska was experimenting with rootkits—tough-to-detect spyware that infects the deepest level of a computer’s operating system—when she came up with a devious notion: What if, instead of putting spyware inside a victim’s computer, you put the victim’s computer inside the spyware? At the time, a technology known…
So Rutkowska flipped the game, this time in favor of the defenders. Four years ago her Warsaw-based firm, Invisible Things Lab, started developing its own operating system known as Qubes. The free open source OS lets users set up a collection of virtual machines on their PC, with a simple central interface to manage each quarantined system. Careful users can keep their personal online activities isolated in one virtual machine, for instance, while they do their work in another, and their banking in a third. (Rutkowska typically runs about 15.) Open a malicious email attachment or click on an infected website and the malware can’t break out of that one contaminated container.
If it works as promised, even NSA-level exploits would be contained to a single compartment in Qubes’ architecture, one that could be evaporated and re-created at will. Recovering from even the nastiest hacker attack, in other words, could soon be as easy as waking from a bad dream.



 Your new post is loading...
Your new post is loading...



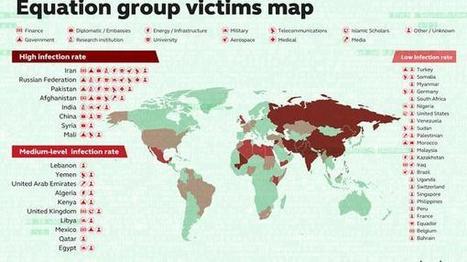

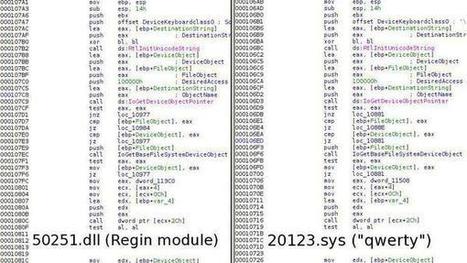
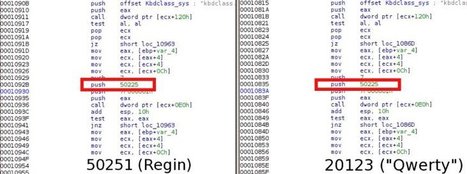


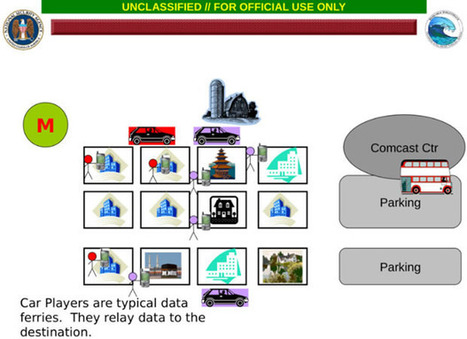



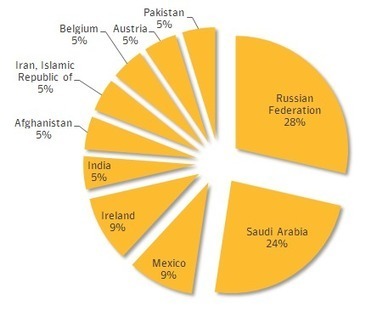


















Cyberspionagegruppe „Desert Falcons“, die sich gegen verschiedene hochrangige Organisationen und Einzelpersonen im Nahen Osten richtet [1]. Damit konnten die IT-Sicherheitsexperten erstmals eine Gruppe von Cybersöldnern aus dem arabischen Raum enttarnen, die offenbar über das komplette Spektrum von Cyberspionagemitteln verfügt.
Die Gruppe startete ihre Aktivitäten bereits im Jahr 2011, seit dem Jahr 2013 werden Rechner infiziert. Den Experten von Kaspersky Lab zufolge erreichte die Kampagne ihren Höhepunkt zu Beginn des Jahres 2015 [2].