The Internet of Things may mean a bigger workload for infosec practitioners, but 2015's real challenges will be the rapidly changing political landscape and the shortage of skilled professionals.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=wearables
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO



 Your new post is loading...
Your new post is loading...





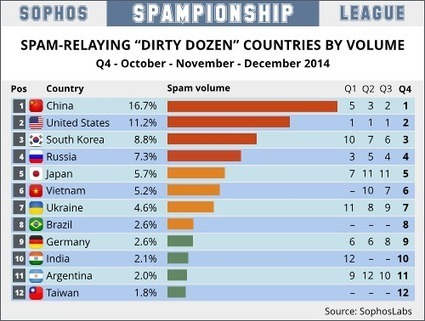



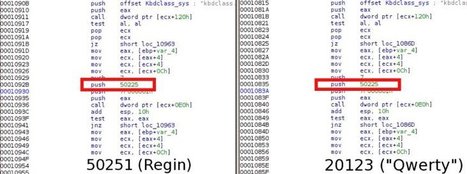






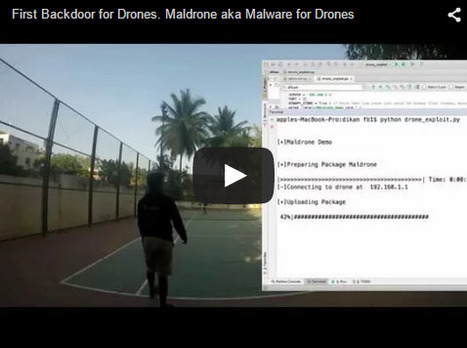

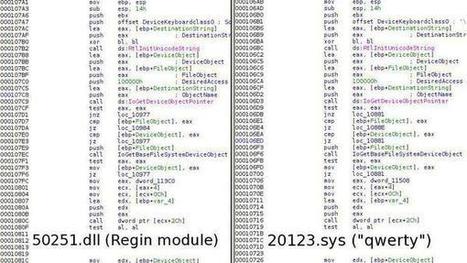










Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=wearables
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
- http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO