With just a little soldering and assembly, a 14-year-old built a device to wirelessly communicate with a vehicle's controller area network (CAN) and remotely start and unlock the vehicle.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cars



 Your new post is loading...
Your new post is loading...




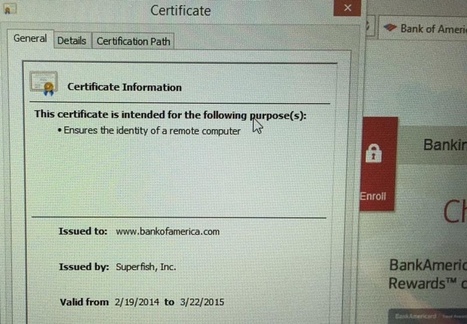


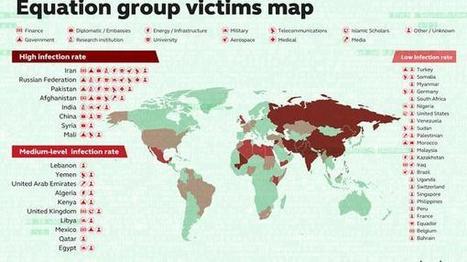




















Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
- http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cars