 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
October 11, 2019 4:50 AM
|

|
Scooped by
Gust MEES
October 6, 2019 9:29 AM
|
What could be more horrifying than knowing that a hacker can trick the plane's electronic systems into displaying false flight data to the pilot, which could eventually result in loss of control?
Of course, the attacker would never wish to be on the same flight, so in this article, we are going to talk about a potential loophole that could allow an attacker to exploit a vulnerability with some level of "unsupervised" physical access to a small aircraft before the plane takes off.
The United States Department of Homeland Security's (DHS) has issued an alert for the same, warning owners of small aircraft to be on guard against a vulnerability that could enable attackers to easily hack the plane's CAN bus and take control of key navigation systems.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Airlines

|
Scooped by
Gust MEES
September 16, 2019 8:18 AM
|
PERSONAL DATA ABOUT ALMOST EVERY ECUADOREAN CITIZEN HAS BEEN FOUND EXPOSED ONLINE.
Names, financial information and civil data about 17 million people, including 6.7 million children, was found by security company vpnMentor.
The massive cache of data was found on an unsecured Amazon cloud server almost anyone could look at.
Access to the server has now been restricted thanks to Ecuador’s computer emergency security team.
SERIOUS BREACH
“The data breach involves a large amount of sensitive personally identifiable information at the individual level,” wrote Noam Rotem and Ran Locar, from vpnMentor.
As well as basic identity data, the exposed files include:
official government ID numbers
phone numbers
family records
marriage dates
education histories
work records Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
September 10, 2019 5:02 PM
|
A series of vulnerabilities have been discovered in some implemenations of Real-Time Operating System (RTOS) VxWorks whose systems are used in more than two billion devices including sectors such as health care, transportation, aviation and other industrial operations. Dubbed Urgent/11, these could lead to a WannaCry-like situation if exploited by malicious actors, say researchers.
"Urgent/11 vulnerabilities affects several devices we can find in our daily lives, especially in healthcare. In fact VxWorks is an operating system commonly used in real-time devices like MRI machines and patient monitors. Attacking these kinds of devices can lead to critical impacts like changing the behaviour of those devices and providing wrong information to doctors/patients," Alessandro Di Pinto, security research manager at Nozomi Networks, told SC Media UK.
First reported and analysed by Armis and further probed by Wind River, the vulnerabilities are particularly notable because they allow attackers to take over devices without user interaction.
"Urgent/11 is serious as it enables attackers to take over devices with no user interaction required, and even bypass perimeter security devices such as firewalls and NAT solutions. These devastating traits make these vulnerabilities ‘wormable,’ meaning they can be used to propagate malware into and within networks," said the Armis report, adding: "Such an attack has a severe potential, resembling that of the EternalBlue vulnerability, used to spread the WannaCry malware." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Urgent11 https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
September 9, 2019 4:40 PM
|
The team behind Exim revealed that a bug in its email server software is currently exposing millions of email servers around the world to potential attacks. Exim is a mail transfer agent (MTA) that runs in the background of email servers. It aids in the sending and receiving of email messages and helps servers act as relays for other users’ emails. All versions of Exim up to and including version 4.92.1 are affected.
The Exim team said in a recent advisory that anyone who is currently running Exim over TLS connections is vulnerable. According to the developers, the bug is unrelated to the TLS libraries (usually a source of similar bugs), so all Exim email servers are impacted, regardless of the TLS library they use.
If the server uses TLS, then an attacker could send a Server Name Identification (SNI) ending in a backslash-null sequence during the initial TLS handshake. This would allow both local or remote attackers to run malicious code with root privileges. Exim vulnerability lets attackers run commands as root on remote email servers. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Exim https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Vulnerabilities

|
Scooped by
Gust MEES
September 8, 2019 5:01 PM
|
The spyware poses as a legitimate application, spreading via SMS messages to victims’ contact lists.
An Android malware dubbed “FunkyBot” has started making the scene in Japan, operated by the same attackers responsible for the FakeSpy malware. It intercepts SMS messages sent to and from infected devices.
According to FortiGuard Labs, the malware (named after logging strings found in the persistence mechanism of the payload) masquerades as a legitimate Android application. The payload thus consists of two .dex files: One is a copy of the original legitimate application that the malware is impersonating, and the other is malicious code.
As for the kill chain, a packer first determines which version of Android the phone is running on, in order to generate the proper payload. After that, the payload is started by calling the method `runCode` class through Java reflection. This starts a class called KeepAliceMain, which is used as persistence mechanism by the malware. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
September 6, 2019 4:03 PM
|
Thousands of web servers have been infected and had their files encrypted by a new strain of ransomware named Lilocked (or Lilu).
Infections have been happening since mid-July, and have intensified in the past two weeks, ZDNet has learned.
Based on current evidence, the Lilocked ransomware appears to target Linux-based systems only.
First reports date to mid-July, after some victims uploaded the Lilocked ransom note/demand on ID Ransomware, a website for identifying the name of the ransomware that infected a victim's system. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux https://www.scoop.it/topic/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
September 6, 2019 9:30 AM
|
In an online world infested with hackers, we need more hackers.
No, that’s not an oxymoron. While hacking remains a generally pejorative term (“Don’t respond to any Facebook invites from me! I got hacked!), the reality is that it’s all about the motivation. To have a chance of blocking or defeating malicious hackers, organizations need “good” or ethical hackers on their side—people who know how to think like the bad guys.
It’s like anything—the best detectives know how to think like criminals. The best sports teams get that way in part by figuring out what their opponents are likely to do before the game starts. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
September 4, 2019 6:55 PM
|
Facebook is staring down yet another security blunder, this time with an incident involving an exposed server containing hundreds of millions of phone numbers that were previously associated with accounts on its platform.
The situation appears to be pinned to a feature no longer enabled on the platform but allowed users to search for someone based on their phone number. TechCrunch’s Zack Whittaker first reported Wednesday that a server—which did not belong to Facebook but was evidently not password protected and therefore accessible to anyone who could find it—was discovered online by security researcher Sanyam Jain and found to contain records on more than 419 million Facebook users, including 133 records on users based in the U.S. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook

|
Scooped by
Gust MEES
August 25, 2019 3:16 PM
|
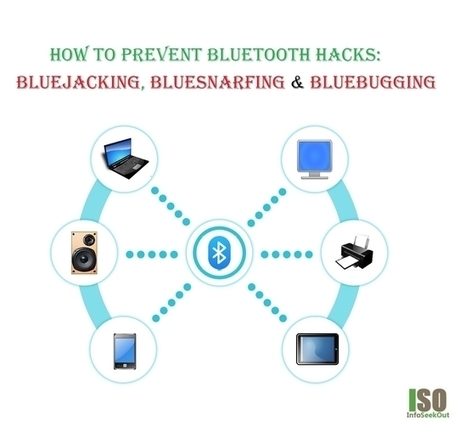
Bluetooth Hacks: The way devices communicate with each other is changing every day. Earlier, they used to communicate by using a range of electrical wires and optical cables. This type of communication is not so preferred due to limitations. Limitations can be like lack of sensors and weather conditions impact etc. Nowadays, devices are communicating with Bluetooth Technology.
Bluetooth: It is one of the features found in millions of devices we use in our day to day life. Some of them are like mobile phones, headphones, laptops and portable speakers. In this article, we will take a look at Bluetooth and Bluetooth Hacks. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Bluetooth

|
Scooped by
Gust MEES
August 25, 2019 11:29 AM
|

|
Scooped by
Gust MEES
August 24, 2019 4:16 PM
|
Die ISS kreist in rund 400 Kilometern Höhe über der Erde. Diese Distanz reicht offenbar aber nicht aus, um von irdischen Problemen Abstand zu nehmen. Eine Astronautin wird nun verdächtigt, von der Raumstation aus ein Verbrechen begangen zu haben. Es wäre der erste Fall von Weltraum-Kriminalität.
Eine Nasa-Astronautin soll von der internationalen Raumstation ISS aus illegalerweise auf das Bankkonto ihrer Ex-Partnerin zugegriffen haben. Wie die "New York Times" berichtete, könnte es sich dabei um den ersten Vorwurf eines Verbrechens vom Weltraum aus handeln.
Demnach gab Anne McClain, die im Juni nach einem sechsmonatigen Aufenthalt im All auf die Erde zurückgekehrt war, gegenüber Ermittlern zu, auf besagtes Konto mit dem ihr bekannten Passwort zugegriffen zu haben. Sie habe sich vergewissern wollen, dass mit den - noch immer miteinander verwobenen - Finanzen des Ex-Paares alles in Ordnung sei, schrieb das Blatt. Die Sache flog dann auf, weil die Bank auf Nachfrage der Ex-Partnerin herausfand, dass Zugriffe auf das Konto von einem Nasa-Netzwerk vorgenommen worden waren - und zwar in der Zeit, in der McClain sich im All befunden hatte. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=cybercrime

|
Scooped by
Gust MEES
August 14, 2019 1:49 PM
|
Gadgets wie intelligente Lautsprecher, Laptops oder Handys sind meist nicht nur mit dem Internet verbunden, sondern auch in der Lage, Schallwellen wiederzugeben. Doch was im Alltag dafür sorgt, dass wir Musik streamen oder ein Telefonat führen können, kann dazu verwendet werden, Nutzer zu verletzen.
Wie das geht, hat ein Sicherheitsforscher auf der Hackerkonferenz Defcon in Las Vegas gezeigt. Matt Wixey, der für die Firma PWC UK arbeitet, brachte mithilfe von Computerviren diverse Geräte dazu, gefährliche Geräusche oder Töne von sich zu geben.
Cyber- vs. reale Welt
«Ich habe mich schon immer für Schadsoftware interessiert, die den Sprung von der digitalen in die physische Welt schaffen kann», sagte Wixey laut einem Bericht von Wired.com. Mit seiner Forschung hat er nun bewiesen, dass Lautprecher so manipuliert werden können, dass sie das menschliche Gehör schädigen oder Tinnitus verursachen.
Für die Arbeit griff er eine Handvoll Geräte – unter anderem einen intelligenten Lautsprecher und einen Kopfhörer – an. Mit einer einfachen Schadsoftware gelang es ihm, Töne außerhalb des sicheren Spektrums abzuspielen. Im Smart Speaker konnte sogar eine so große Hitze erzeugt werden, dass das Gerät zu schmelzen begann. Learn more / En savooir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet
|

|
Scooped by
Gust MEES
October 6, 2019 5:30 PM
|
The US Department of Homeland Security and the US Food and Drug Administration (FDA) have published advisories this week warning about a much broader impact of the Urgent/11 vulnerabilities, which impact more operating systems than initially thought.
The Urgent/11 security flaws were initially disclosed over the summer by cyber-security firm Armis. They allow attackers to run malicious code and take over a wide range of devices, from routers to firewalls, and from printers to industrial equipment.
Security researchers initially believed Urgent/11 only impacted devices using VxWorks, a real-time operating system (RTOS) created by Wind River.
The actual issue was tracked down to IPnet, a TCP/IP networking library that was part of VxWorks. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Urgent11 https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
September 16, 2019 11:01 AM
|
Password manager LastPass has released an update last week to fix a security bug that exposes credentials entered on a previously visited site.
FIX AVAILABLE
LastPass, believed to be the most popular password manager app today, fixed the reported issue in version 4.33.0, released last week, on September 12.
If users have not enabled an auto-update mechanism for their LastPass browser extensions or mobile apps, they're advised to perform a manual update as soon as possible.
This is because yesterday, Ormandy published details about the security flaw he found. The security researcher's bug report walks an attacker through the steps necessary to reproduce the bug. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Password+Managers https://www.scoop.it/t/securite-pc-et-internet/?&tag=Passwords

|
Scooped by
Gust MEES
September 13, 2019 5:32 PM
|
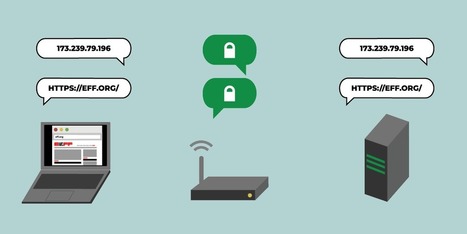
Thanks to the success of projects like Let’s Encrypt and recent UX changes in the browsers, most page-loads are now encrypted with TLS. But DNS, the system that looks up a site’s IP address when you type the site’s name into your browser, remains unprotected by encryption.
Because of this, anyone along the path from your network to your DNS resolver (where domain names are converted to IP addresses) can collect information about which sites you visit. This means that certain eavesdroppers can still profile your online activity by making a list of sites you visited, or a list of who visits a particular site. Malicious DNS resolvers or on-path routers can also tamper with your DNS request, blocking you from accessing sites or even routing you to fake versions of the sites you requested. Learn more / en Savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=EFF https://www.scoop.it/topic/securite-pc-et-internet/?&tag=DNS

|
Scooped by
Gust MEES
September 9, 2019 4:59 PM
|

|
Scooped by
Gust MEES
September 9, 2019 4:32 PM
|
Security researchers have found another instance of a malware strain abusing the Windows Background Intelligent Transfer Service (BITS).
The malware appears to be the work of a state-sponsored cyber-espionage group that researchers have been tracking for years under the name of Stealth Falcon.
The first and only report on this hacking group has been published in 2016 by Citizen Lab, a non-profit organization focusing on security and human rights.
According to the Citizen Lab report, the Stealth Falcon group has been in operation since 2012 and was seen targeting United Arab Emirates (UAE) dissidents. Previous tools included a very stealthy backdoor written in PowerShell. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage

|
Scooped by
Gust MEES
September 6, 2019 6:53 PM
|
Die deutsche Version des Online-Lexikons Wikipedia war am Freitagabend zeitweise unerreichbar. Die Betreibergesellschaft geht von einem gezielten Angriff aus. Auch weitere europäische Ausgaben sind betroffen.
Die deutsche Ausgabe der offenen Internetenzyklopädie Wikipedia war am Freitagabend zeitweise nicht aufrufbar. Hintergrund sei ein "massiver und sehr breit angelegter DDoS-Angriff", teilte die Betreibergesellschaft Wikimedia Deutschland via Twitter mit.
Angriffe des Typs DDoS (Distributed Denial of Service, in etwa "systematische Lahmlegung" eines Diensts) überfluten die Server einer Internetseite so lange mit sinnlosen Anfragen, bis sie zusammenbricht und nicht mehr angezeigt werden kann. Große Netzportale haben meist Schutzmechanismen dagegen.
Ich bin damit einverstanden, dass mir Inhalte von Twitter angezeigt werden.
Der Nachrichtenagentur dpa zufolge sind auch weitere europäische Wikipedia-Versionen betroffen. Unter anderem berichten Nutzer der französischen und der englischen Wikipedia von Problemen. Learn more / En savoir plus / #Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Wikipedia

|
Scooped by
Gust MEES
September 6, 2019 3:53 PM
|
The developers of the Metasploit penetration testing framework have released today a weaponized exploit for the BlueKeep Windows vulnerability.
While other security researchers have released defanged BlueKeep proof-of-concept code in the past, this exploit is advanced enough to achieve code execution on remote systems, infosec experts who reviewed the Metasploit module have told ZDNet.
WHAT IS BLUEKEEP?
BlueKeep, also known as CVE-2019-0708, is a vulnerability in the Remote Desktop Protocol (RDP) service in older versions of the Windows operating system (Windows XP, Windows 2003, Windows 7, Windows Server 2008, and Windows Server 2008 R2).
Microsoft patched BlueKeep in the May 2019 Patch Tuesday security fixes released on May 14, and warned users to apply the patches as soon as possible.
At the time, to spur users into patching faster, the OS maker described BlueKeep as a "wormable" vulnerability that can self-propagate in a similar manner similar to how the EternalBlue exploit helped the WannaCry ransomware propagate to millions of computers in 2017.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Metasploit

|
Scooped by
Gust MEES
September 5, 2019 4:40 AM
|
Millions of phone numbers associated with Facebook users have been found online in an unsecured database.
The database contained the phone numbers of more than 419 million Facebook users from across the world and included the real name, country and gender for many users.
The records leaked included 133 million records on Facebook users from the US, 18 million records associated with UK users - which will invite an investigation by the Information Commissioner's Office (ICO) under GDPR - and another 50 million records on users in Vietnam.
No password was used to protect the exposed server. TechCrunch said it verified some of the phone numbers existing in the database by matching known Facebook users' phone number against their listed Facebook ID.
The database was spotted by Sanyam Jain, a security researcher and a member of the GDI foundation, according to TechCrunch.

|
Scooped by
Gust MEES
September 2, 2019 11:04 AM
|
A hacker group is exploiting vulnerabilities in more than ten WordPress plugins to create rogue admin accounts on WordPress sites across the internet.
The attacks are an escalation part of a hacking campaign that started last month. During previous attacks, the hackers exploited vulnerabilities in the same plugins to plant malicious code on the hacked sites. This code was meant to show popup ads or to redirect incoming visitors to other websites.
However, two weeks ago, the group behind these attacks changed its tactics. Mikey Veenstra, a threat analyst with cybersecurity firm Defiant, told ZDNet today that starting with August 20, the hacker group modified the malicious code planted on hacked sites.
Instead of just inserting pop-ups and redirects, the malicious code also ran a function in order to test if the site visitor had the ability to create user accounts on the site, a feature only available for WordPress admin accounts. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
August 25, 2019 11:40 AM
|
Everyone uses Bluetooth. Perhaps they shouldn't.
The technology that we've come to rely on to connect our phones, smart speakers, cars, vibrators, and toasters is problematic for reasons more serious than pairing issues. Bluetooth has been shown time and time again to be a security and privacy nightmare — albeit one that can be mostly solved with a simple toggling of an off switch.
You just have to decide to flip that switch.
Bluetooth has long been a dirty word for security professionals. So much so, in fact, that one of the most common pieces of advice given to attendees of the annual DEF CON hacker conference in Las Vegas is to make sure Bluetooth is disabled on their phones.
This is not just paranoia. In fact, at this year's DEF CON researchers showed off the ability to use Bluetooth to identify vulnerable digital speakers. Once identified, hackers could take control of the devices and force them to play "dangerous" sounds that could lead to hearing loss in anyone unfortunate enough to be nearby. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Bluetooth

|
Scooped by
Gust MEES
August 25, 2019 5:02 AM
|
Security researchers at Sophos have warned of a new phishing campaign targeting Instagram users. And this is a phishing campaign with a devious twist. The attackers mock up what's intended to look like two-factor authentication (2FA) in an attempt to appear legitimate. But it's obviously not 2FA. It's a standard attempt to steal login credentials, to amass usernames and passwords.
The initial phishing attack emails include what looks like a 2FA code. The user is instructed to enter the code when they login to prove their identity. The premise of the attack is that there has been an unauthorized login. The login warning, the email and of course the 2FA code are completely fake—the code just a clever twist to suggest some form of security. The whole thing it spurious, but people will be tricked.
The email link takes users to a fake Instagram login page, described by Sophos as "much more believable" than many of the standard email phishing campaigns uncovered. "We don't like to admit it," the research team reports, "but the crooks thought this one through." Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Instagram

|
Scooped by
Gust MEES
August 24, 2019 11:31 AM
|
Big data is the lynchpin ofnew advances in cybersecurity. Unfortunately, predictive analytics and machine learning technology is a double-edged sword for cybersecurity. Hackers are also exploiting this technology, which means that there is a virtual arms race between cybersecurity companies and black hat cybercriminals.
Datanami has talked about the ways that hackers use big data to coordinate attacks. This should be a wakeup call to anybody that is not adequately prepared.
Black Hat Hackers Exploit Machine Learning to Avoid Detection
Jathan Sadowski wrote an article in The Guardian a couple years ago on the intersection between big data and cybersecurity. Sadowski said big data is to blame for a growing number of cyberattacks.
In the evolution of cybercrime, phishing and other email-borne menaces represent increasingly prevalent threats. FireEye claims that email is the launchpad for more than 90 percent of cyber attacks, while a multitude of other statistics confirm that email is the preferred vector for criminals.
This is largely because of their knowledge of machine learning. They use machine learning to get a better understanding of customers, choose them them more carefully and penetrate defenses more effectively. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=tracking https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy https://www.scoop.it/t/securite-pc-et-internet/?&tag=Big+Data
|



 Your new post is loading...
Your new post is loading...






























Dank einer Sicherheitslücke in WhatsApp können Angreifer mittels manipulierter GIF-Bilddateien via Fernzugriff auf Android-Smartphones zugreifen.
Ein Fehler im beliebten Messenger WhatsApp sorgt mal wieder für Aufsehen. Die Sicherheitslücke betrifft die Verarbeitung von GIF-Dateien. Wie der Blog Hackernews vermeldet, liegt das Problem im Speziellen in der Programmbibliothek Android GIF Drawable. Diese wird dafür benutzt, GIF-Vorschauen anzuzeigen.
Mit einem entsprechend manipulierten GIF-File kann auf unbemerkte Weise der Zugriff auf das Smartphone erlangt werden. Dabei greift der Exploit erst, wenn das besagte GIF geöffnet wurde und man danach ein eigenes GIF verschicken will. In der Vorschau wird daraufhin das manipulierte GIF ausgespielt.
Der Angreifer erhält hierdurch per Remote-Zugriff die Rechte, die der User WhatsApp gewährt hat – unter Umständen also vollständigen Daten-, Chatlog- und Kamerazugriff.
Betroffen von der Sicherheitslücke ist die WhatsApp-Version 2.19.230 auf Android 8.1 und 9. Das Leck wurde mit dem Update auf Version 2.19.244 geschlossen.
Learn more / En savoir plus / Mehr erfahren:
https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Apps
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=WhatsApp...