Internet-Aktivitäten von 14.000 Kindern betroffen - Datenschützer empört
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
Aus der Antwort auf eine Anfrage einer amerikanischen Bürgerrechts-Aktivistin geht hervor, dass der Geheimdienst Informationen über aktuelle Schwachstellen von der französischen Sicherheitsfirma erhält.
Gust MEES's insight:
Les documents publiés à la suite de la confiscation il y a trois ans d'appareils électroniques à un défenseur du soldat Manning montrent que les services américains bloquent et fouillent à la frontière, des alertes permettant d'intercepter des...
Gust MEES's insight:
More documents from former security contractor Edward Snowden show that the National Security Agency has been secretly working to gain a back door into all encryption technologies, The New York Times reports.
Gust MEES's insight:

Jesse Garboden's comment,
September 24, 2013 5:37 PM
Why do you think I post and re-post publicly because everything is read any ways.
The NSA's Cryptographic Capabilities
The latest Snowden document is the US intelligence "black budget." There's a lot of information in the few pages the Washington Post decided to publish, including an introduction by Director of National Intelligence James Clapper. In it, he drops a tantalizing hint: "Also, we are investing in groundbreaking cryptanalytic capabilities to defeat adversarial cryptography and exploit internet traffic."
Honestly, I'm skeptical. Whatever the NSA has up its top-secret sleeves, the mathematics of cryptography will still be the most secure part of any encryption system. I worry a lot more about poorly designed cryptographic products, software bugs, bad passwords, companies that collaborate with the NSA to leak all or part of the keys, and insecure computers and networks. Those are where the real vulnerabilities are, and where the NSA spends the bulk of its efforts.
Gust MEES's insight:
A MUST read!!!
WASHINGTON -- The National Security Agency has broken privacy rules or overstepped its legal authority thousands of times each year since Congress granted the agency broad new powers in 2008, The Washington Post reported Thursday.
Most of the infractions involve unauthorized surveillance of Americans or foreign intelligence targets in the United States, both of which are restricted by law and executive order.
They range from significant violations of law to typographical errors that resulted in unintended interception of U.S. emails and telephone calls, the Post said, citing an internal audit and other top-secret documents provided it earlier this summer from NSA leaker Edward Snowden, a former systems analyst with the agency.
Gust MEES's insight:
===> In most cases, the NSA was involved in unauthorized surveillance of Americans or foreign intelligence targets in the U.S., despite these being restricted by law and executive order. <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=PRISM

Gust MEES's curator insight,
August 15, 2013 10:18 PM
===> In most cases, the NSA was involved in unauthorized surveillance of Americans or foreign intelligence targets in the U.S., despite these being restricted by law and executive order. <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=PRISM
Die Off Pocket blockt nahezu alle Funkverbindungen des Smartphones und macht es so unsichtbar für Schnüffler und Ortungsversuche - aber auch immun gegen Anrufe oder Textnachrichten.
Gust MEES's insight:
Condom for Smartphones!
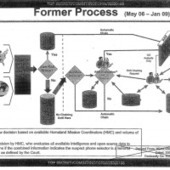
Bei ihren Durchsuchungen von Internetdaten gehen die Mitarbeiter der NSA auch Informationen über Dritte nach, die bereits überwachte Personen erwähnen. Das kann auch US-Bürger betreffen.
Gust MEES's insight:
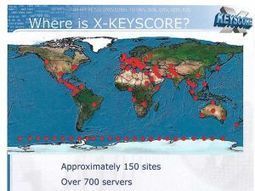
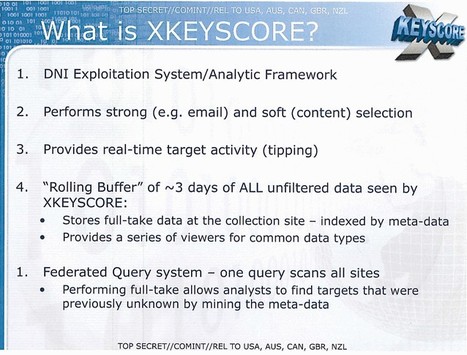
XKeyscore doesn't just turn somebody's Internet life inside out. It's also a blood hound for sniffing out vulnerable systems.
According to Ars Technica's Sean Gallagher, the vulnerability "fingerprints" are added to serve as a filtering criteria for XKeyscore's application engines, comprised of "a worldwide distributed cluster of Linux servers attached to the NSA's Internet backbone tap points."
This turns XKeyscore into a passive port scanner, Gallagher writes, which can be used to search for network behavior on systems that match the NSA TAO's profiles for exploits or for systems already exploited by malware that the TAO can then take advantage of.
Gust MEES's insight:
This turns XKeyscore into a passive port scanner, Gallagher writes, which can be used to search for network behavior on systems that match the NSA TAO's profiles for exploits or for systems already exploited by malware that the TAO can then take advantage of.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=XKeyscore
It’s summer holiday season, when people pack up their smartphones and tablets, sunscreen and tank tops and set off for a change of pace. With connected devices it’s never been easier to find one’s way around, record memories, and stay in touch with friends back home.
But while technology makes traveling easier, a recent F-Secure survey pinpointed digital areas that need special consideration while on the road.
Gust MEES's insight:
Eine im Web veröffentlichte geheime Präsentation beweist: Die NSA überwacht mit der Spionagesoftware Xkeyscore das ganze Internet - und das sogar in Echtzeit.
Gust MEES's insight:
Microsoft has defended claims that detailed deep co-operation with the US government, including the circumvention of encryption in its Outlook.com email and access to its SkyDrive cloud storage service and Skype. A statement issued by Microsoft denied it had provided blanket access of its products to NSA surveillance teams, and reiterated that it only responds to valid requests. "We have clear principles, which guide the response across our entire company to government demands for customer information for both law enforcement and national security issues," the statement said.
Gust MEES's insight:
From
www
Cindy Cohn, legal director and general counsel for the EFF, called the ruling a tremendous victory and a courageous decision by the court, which moves the group's efforts one step closer toward establishing the government surveillance programs as unconstitutional under the First and Fourth Amendments.
Gust MEES's insight:
Cindy Cohn, legal director and general counsel for the EFF, called the ruling a tremendous victory and a courageous decision by the court, which moves the group's efforts one step closer toward establishing the government surveillance programs as unconstitutional under the First and Fourth Amendments.
Learn more:

Gust MEES's curator insight,
July 10, 2013 9:36 AM
Cindy Cohn, legal director and general counsel for the EFF, called the ruling a tremendous victory and a courageous decision by the court, which moves the group's efforts one step closer toward establishing the government surveillance programs as unconstitutional under the First and Fourth Amendments. Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA |
The internet has changed our lives in countless positive ways, but it has a dark side. Personal privacy has been lost, leaving you at risk from shady individuals, companies and security agencies.
Gust MEES's insight:
Belgacom, the largest telecommunications company in Belgium, has been hacked. The company’s representatives said they found a piece of malware o...
“At no point in time has the delivery of our telecommunication services been compromised. Neither has the clean-up caused any disturbance to our customers. All their telecom applications and services have continued to function normally,” it added.
Gust MEES's insight:
The malware used in the Belgacom hack is designed to collect strategic information, not to cause damage.
What happens when a secret U.S. court allows the National Security Agency access to a massive pipeline of U.S. phone call metadata, along with strict rules on how the spy agency can use the information?
Gust MEES's insight:

Jesse Garboden's comment,
September 24, 2013 5:36 PM
If people think it has been only three years think again.
Die NSA hat laut einem Medienbericht Arbeitsgruppen für jedes große mobile Betriebssystem. Die Angreifer können Kontaktlisten, SMS, E-Mail und Aufenthaltsorte auslesen.
Gust MEES's insight:
NSA also bugged more than 80 embassies and consulates, says Der Spiegel.
Gust MEES's insight:
The wide-reaching leak on data surveillance programs by Edward Snowden (who has sought asylum in Russia) is still ongoing. According to the Washington Post, an internal audit and other top-secret documents show that the National Security Agency (NSA) has broken privacy laws or overstepped its legal authority thousands of times each year since it was granted broader powers in 2008.
===> In most cases, the NSA was involved in unauthorized surveillance of Americans or foreign intelligence targets in the U.S., despite these being restricted by law and executive order. <===
Gust MEES's insight:
===> In most cases, the NSA was involved in unauthorized surveillance of Americans or foreign intelligence targets in the U.S., despite these being restricted by law and executive order. <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=PRISM
Revelations of the U.S. government's spying programs could have a massive impact on the U.S. cloud industry, which stands to lose vast sums over the next three years as a result — compounded by other countries bankrolling efforts to combat U.S.
Gust MEES's insight:
"[Government Communications Headquarters] must pull its weight," UK spies wrote. NSA paid $152M over 3 years to British spy agency, new Snowden docs show"[Government Communications Headquarters] must pull its weight," UK spies wrote.
Gust MEES's insight:
NSA paid $152M over 3 years to British spy agency, new Snowden docs show"[Government Communications Headquarters] must pull its weight," UK spies wrote.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=PRISM
The Wall Street Journal is reporting that the FBI employs a number of high-tech hacker tactics in its efforts to round up information on suspects, including the ability to remotely activate microphones on Android devices and notebook computers,...
Gust MEES's insight:
The ten CreepyDOL computers Brendan O'Connor built for his proof-of-concept surveillance system, with his business card shown in the center for scale.
Gust MEES's insight:
A MUST read!!!
Depuis juillet 2012, les agences de renseignement américaines pourraient sans difficulté, et malgré le chiffrement mis en place, écouter des appels Skype.
Gust MEES's insight:

Gust MEES's curator insight,
July 12, 2013 3:26 AM
En savoir plus :
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Skype
|































Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Privacy