 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
September 15, 2015 5:28 PM
|

|
Scooped by
Gust MEES
August 31, 2015 12:26 PM
|
The draft guide provides detailed example solutions using multiple products that achieve the same result, and instructions for implementers and security engineers, including examples of all the necessary components and installation, configuration and integration.
NIST notes that the draft guide also maps security characteristics to guidance and best practices from NIST and other standards organizations, and to North American Electric Reliability Corporation’s Critical Infrastructure Protection standards. The guide is modular and suitable for organizations of all sizes, including corporate and regional business offices, power generation plants and substations. They can adopt this solution or one that adheres to these guidelines in whole, or use the guide as a starting point for tailoring and implementing parts of a solution.
The draft guide can be found on the NCCoE Web site.
Learn more:
https://nccoe.nist.gov/projects/use_cases/idam

|
Scooped by
Gust MEES
August 19, 2015 6:56 PM
|

|
Scooped by
Gust MEES
August 19, 2015 8:27 AM
|
NICE Goals
NICE is a public-private partnership between government, academia, and the private sector. The mission of NICE is: “Cultivating an integrated cybersecurity workforce that is globally competitive from hire to retire, with the knowledge, skills, and ability to protect our nation from existing and emerging challenges.”

|
Scooped by
Gust MEES
August 3, 2015 2:43 PM
|
Just days after Microsoft released its latest operating system, hackers have begun targeting soon-to-be Windows 10 users with an emerging kind of malware.
Cisco security researchers are warning users against opening email attachments purporting to be from the software giant. The "ransomware" malware, which encrypts files until a ransom is paid, is being sent as part of an email spam campaign.

|
Scooped by
Gust MEES
July 17, 2015 7:12 PM
|
A joint operation by the FBI and the law enforcement agencies of 19 other countries has led to the takedown of the notorious discussion forum for criminal hackers, Darkode.me. It was the most central English-speaking hub for the sale of credit card numbers, criminal hacking hardware, and malware written for commercial sale. Originally called Darkode.com, the forum had shifted several times in response to pressure from authorities and the “white hat” hacking community, adding layers upon layers of security.
It was a highly encrypted, invite-only forum hosted by true paranoiacs, and featuring a tiered access system designed to keep any unavoidable infiltrators away from the most sensitive discussions. With an air of true satisfaction, the FBI announcement makes the implication clear as day: if we can get Darkode, we can get anybody.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cybercrime
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Darkode

|
Scooped by
Gust MEES
July 17, 2015 6:33 PM
|
Darkode, a notorious cybercrime marketplace for malware, zero-day exploits, and botnets, was permanently shut down by a massive law enforcement operation coordinated between agencies in the US, Europe and elsewhere.
Learn more about Cybercrime:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cybercrime

|
Scooped by
Gust MEES
June 23, 2015 6:39 PM
|
The U.S. Navy is paying Microsoft millions of dollars to keep up to 100,000 computers afloat because it has yet to transition away from Windows XP.

|
Scooped by
Gust MEES
June 23, 2015 3:31 PM
|
Senior U.S. officials have said that the Chinese have begun in the last 12 to 18 months to build vast databases of Americans’ personal information for counterintelligence purposes. They have gone after such data contained not only in federal networks, but in systems belonging to health-insurance giants such as Anthem.
The breach details come as OPM leadership is under fire for its handling of a succession of network hacks over the last year and a half. The chairman of the House Oversight and Government Reform Committee, Rep. Jason Chaffetz (R-Utah), has called for the resignation of the agency’s director, Katherine Archuleta.
Under Archuleta, Wagner said, the agency in February 2014 began a program to identify vulnerabilities in the agency’s aging computer systems — some date to 1985 — and to modernize the network.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack

|
Scooped by
Gust MEES
June 22, 2015 11:27 AM
|

|
Scooped by
Gust MEES
May 27, 2015 4:46 PM
|

|
Scooped by
Gust MEES
May 26, 2015 9:41 AM
|
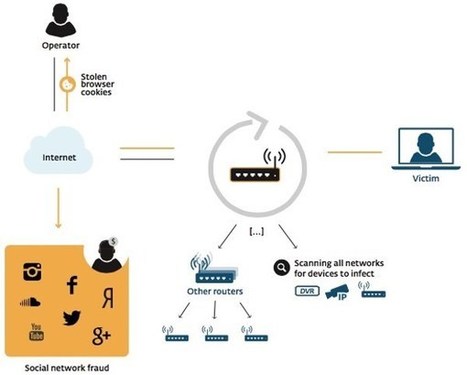
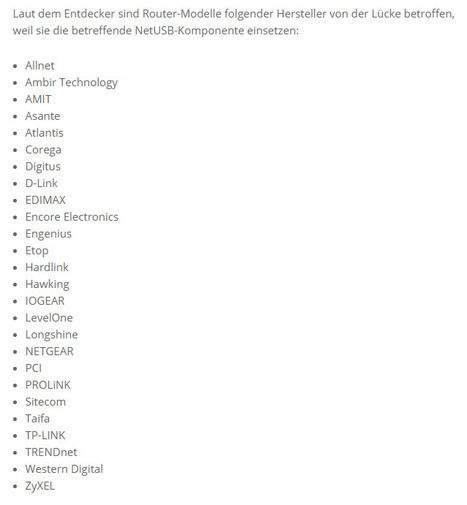
ESET researchers have issued a technical paper today, analysing a new worm that is infecting routers in order to commit social networking fraud, hijacking victims’ internet connections in order to “like” posts and pages, “view” videos and “follow” other accounts.
The malware, dubbed Linux/Moose by researchers Olivier Bilodeau and Thomas Dupuy, infects Linux-based routers and other Linux-based devices, eradicating existing malware infections it might find competing for the router’s limited resources, and automatically finding other routers to infect.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Router
|

|
Scooped by
Gust MEES
September 3, 2015 9:37 PM
|

|
Scooped by
Gust MEES
August 30, 2015 8:40 AM
|
Picture the scene: you've had to hire a data protection officer, you've got a strict plan in place to notify all of your customers about breaches as soon as they happen, all of your data is encrypted and your company now has an insurance plan to help guard against data fines. This scene is in stark contrast to the security and compliance measures that many businesses currently operate under, yet this is expected to become standard practice, and the deadline to comply is fast approaching.
The European Union's Global Data Protection Regulation (EU GDPR) is expected to come into effect in 2017 and will transform how businesses approach compliance and data security. This newly proposed legislation will impact all organisations that process the personal data of EU citizens. So what does the compliant organisation of the not-so-distant future look like, and how can organisations ensure they meet these standards in time?
Mehr erfahren / En savoir plus / Learn more:
http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
August 19, 2015 6:44 PM
|
LinuxCon 2015 Security guru Bruce Schneier says there's a kind of cold war now being waged in cyberspace, only the trouble is we don't always know who we're waging it against.
Schneier appeared onscreen via Google Hangouts at the LinuxCon/CloudOpen/Containercon conference in Seattle on Tuesday to warn attendees that the modern security landscape is becoming increasingly complex and dangerous.
"We know, on the internet today, that attackers have the advantage," Schneier said. "A sufficiently funded, skilled, motivated adversary will get in. And we have figure out how to deal with that."
Using the example of last November's crippling online attack against Sony Pictures, Schneier said it was clear that many of these new attacks were the work of well-funded nation-states.
"Many of us, including myself, were skeptical for several months. By now it does seem obvious that it was North Korea, as amazing as that sounds," he said.
But what's troubling about many of these new attacks, he added, is that they can be hard to spot when they don't come in the form that security experts typically expect.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack
http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
August 3, 2015 8:07 PM
|
Eight years ago researcher Dan Egerstad demonstrated how useful having your own Tor exit nodes can be if you want to spy on people by setting up five of his own.
He used them to harvest thousands of emails and messages from embassies in Australia, Japan, Iran, India and Russia, as well as the Iranian Foreign Ministry and the Indian Ministry of Defence.
He was running exit nodes rather than entry guards but his conclusion applies to both - he was convinced (although he provided no proof of it) that governments would surely be running or spying on Tor relays too:
I am absolutely positive that I am not the only one to figure this out ... I'm pretty sure there are governments doing the exact same thing. There's probably a reason why people are volunteering to set up a node.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
July 28, 2015 8:30 PM
|
What about malware on Linux?
Here's how the argument might go if you were to ask that question:
Malware is impossible on Linux because Linux is secure by design, unlike Windows.
Even if Linux malware were possible, users would have to agree to run it, so that wouldn't count.
Even if users agreed to run it, they wouldn't be root, so that wouldn't count.
Even if they were root, who cares? There isn't any malware for Linux, so there.
The simple truth, of course, is that Linux is much more similar to Windows – in design, implementation and real-world security – than it is different.
As a result: there is malware for Linux; it can do plenty of harm even if you aren't root; and it may be able to infect without you realising.
Just like on Windows.
For all that, the "malware scene" on Linux simply never unfolded like it did on Windows, because the vast
Learn more:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
July 17, 2015 6:39 PM
|
The fact that a company called Hacking Team was hacked, combined with the disclosure of their shady clientele, has several diminished the credibility of previous denials the company has made about their engaging in this kind of profiteering. It also validates criticisms that groups like the EFF and Reporters Without Borders have thrown at Hacking Team – basically, that they provide agents around the globe with cyberweapons used for the suppression of democracy and the violation of human rights.
Hacking Team offers their clients a “Remote Control System” (RCS) that combines a variety of spyware technologies into one comprehensive surveillance suite. According to The Citizen Lab, this RCS product essentially allows users to do things like turn the microphones and cameras of their targets’ mobile phones on/off, monitor and record communications, and copy files and passwords.
While Hacking Team sells exclusively to governments, companies are designing products and services to give them similar capabilities.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Hacking+Team+breach
- https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
June 25, 2015 9:17 AM
|
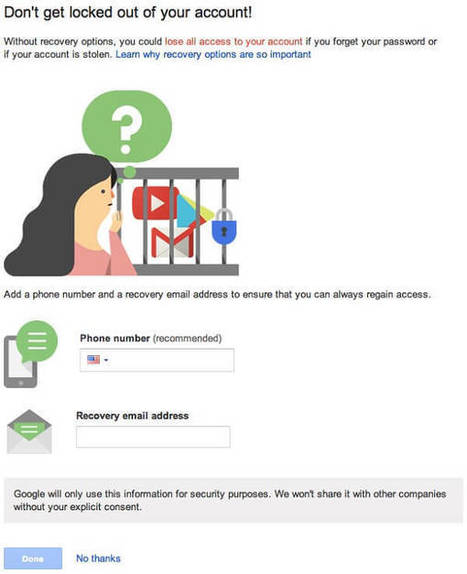
Symantec has issued a warning about a successful scam being perpetrated against users of webmail services such as Gmail, Outlook and Yahoo.
The scam is explained in the following short video made by Symantec.

|
Scooped by
Gust MEES
June 23, 2015 4:09 PM
|
Beim Hackerangriff auf die oberste Personalbehörde der US-Regierung sind Millionen sensibler Daten kopiert worden. Ein Jahr lang hatten die Angreifer Zugriff - auch wegen gewaltiger Schlamperei in dem Amt.
Netzwerk schon seit einem Jahr unterwandert Wer im Besitz eines dieser 127 Seiten langen Formulare ist, weiß über den entsprechenden Bewerber wohl mehr als jeder andere - vorausgesetzt, es wurde wahrheitsgemäß ausgefüllt. Für Vertreter eines ausländischen Geheimdienstes dürften diese Daten von unschätzbarem Wert sein, immerhin betreffen sie Menschen, die sich um Arbeitsplätze in Geheimdiensten, beim Militär oder in Behörden bemühen. Diese Daten wurden offenbar kopiert, aus den Beständen des Office of Personnel Management (OPM), gewissermaßen der Personalabteilung der US-Behörden.
Der "Washington Post" zufolge war das Netzwerk schon im Juni oder Juli 2014 erfolgreich unterwandert worden. Ein zweiter erfolgreicher Angriff,der im April bekannt wurde und bei dem 4,1 Millionen Personaldatensätze kopiert worden sein sollen, begann dem Bericht zufolge im Dezember 2014. Mittlerweile scheinen sich die Ermittler sicher zu sein: Die Täter sollen aus China stammen. "Es geht hier um die sensibelsten Informationen ohne Sicherheitseinstufung, auf die die Chinesen überhaupt Zugriff bekommen konnten", zitiert die "Washington Post" Stewart Baker, der früher einmal der Chefjustiziar der NSA war.
Mehr erfahren / Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack

|
Scooped by
Gust MEES
June 23, 2015 3:14 PM
|
Die kampfstarke US-Marine setzt nach wie vor auf Windows XP. Und zahlt dafür extra einige Millionen Dollar an Microsoft.
Erst kürzlich machte die Meldung die Runde, dass deutsche Behörden wie die Verwaltung von Berlin noch auf Windows XP setzen. Und mit der Benutzung des von Microsoft nicht mehr unterstützten Betriebssystems entweder gravierende Sicherheitslücken in Kauf nehmen oder aber Riesensumme für Extra-Support an Microsoft bezahlen.
Doch dieser Sonderweg einiger deutscher Bundesbehörden ist noch nichts gegen die Kriegsmarine der Vereinigten Staaten von Amerika, die sogar über U-Boote mit Atomwaffen verfügt. Denn auch die US-Marine setzt immer noch Computer mit Windows XP ein.

|
Scooped by
Gust MEES
June 11, 2015 11:14 AM
|
Often times it's not the fact that your business has been hacked that will lose your customers' confidence, but the way your company responds.
Kaspersky isn't the first anti-virus company to have suffered at the hands of hackers, and it certainly won't be the last. And it shows that even the most security-conscious organisations can fall victim to determined hackers.
The truth is that most companies have probably been hacked to some extent or another - although most of the time they won't have been specifically targeted like Kaspersky probably was.
What's important is for companies to consider testing their own defences, and put effort into hacking themselves, finding vulnerabilities and weaknesses *before* the bad guys strike.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
May 27, 2015 4:40 PM
|
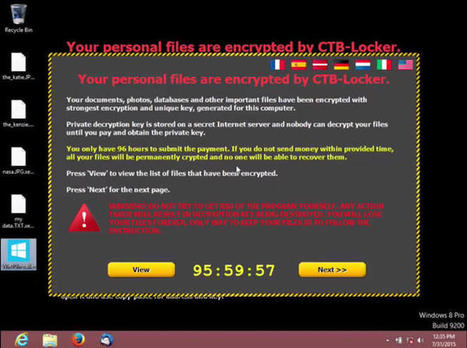
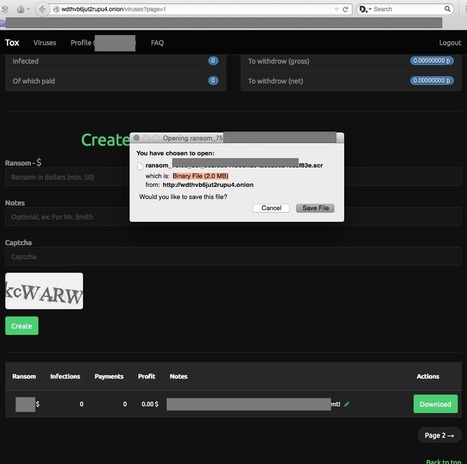
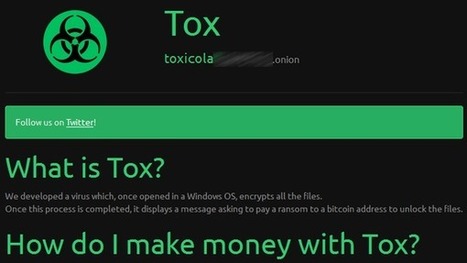
Die Einstiegshürde für angehende Online-Erpresser ist erneut gesunken: Ein Dienst im Tor-Netz erstellt nach wenigen Klicks den individuellen Erpressungs-Trojaner. Falls ein Opfer das geforderte Lösegeld zahlt, verdienen die Betreiber mit.
Die Einstiegshürde für angehende Online-Erpresser ist erneut gesunken: Ein Dienst im Tor-Netz erstellt nach wenigen Klicks den individuellen Erpressungs-Trojaner. Falls ein Opfer das geforderte Lösegeld zahlt, verdienen die Betreiber mit.
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
May 20, 2015 4:11 PM
|
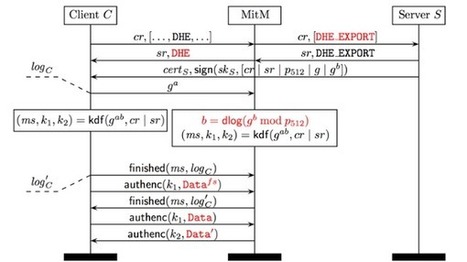
Unzählige Web-, Mail-, SSH- und VPN-Server sind durch einen neuen Angriff auf den Diffie-Hellmann-Schlüsseltausch verwundbar. Angreifer können so die Verschlüsselung aufbrechen. Vermeintlich vertrauenswürdig übertragene Daten wären dann nicht mehr sicher.
|



 Your new post is loading...
Your new post is loading...

























.
Learn more:
.
http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
.
https://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/
.