Why go to all the bother of writing ransomware that demands victims pay a Bitcoin ransom? If all you want is cryptocurrency, why not use the infected computers to mine the crypto coins themselves?
That way you don’t have to rely on a human victim buying some Bitcoin, and nervously making their way onto the dark web to make their ransom payment.
According to security researchers at Proofpoint, that’s exactly the reasoning shown by online criminals who are moving from regular ransomware to cryptomining.
A Monero-mining botnet called Smominru is said to have infected 526,000 Windows PCs since May 2017 – mostly in Russia, India, and Taiwan – and is earning millions of dollars for its operators.
In fact, the biggest clue that most users will have that their computers may be affected by a cryptominer is if they found the PC is slowing down, its battery running out at a quicker rate, or the fan blowing at full blast.
Don’t make the mistake of thinking that this is a victimless crime. If your computers get recruited into a cryptomining botnet like Smominru, it’s your electricity and computer power that is being stolen.
Keep your computers up-to-date with security patches, defended with layered security solutions, and your wits about you.
Learn more / En savoir plus / mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive
https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency
https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking



 Your new post is loading...
Your new post is loading...




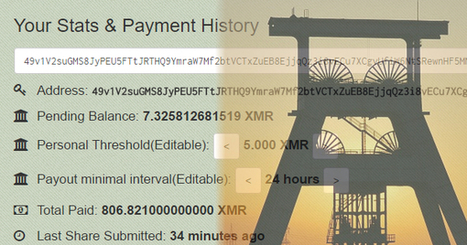

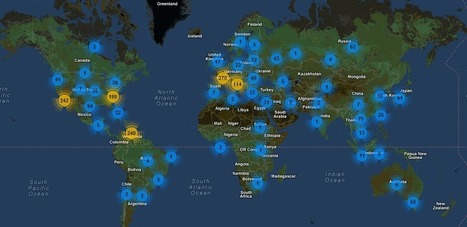






In fact, the biggest clue that most users will have that their computers may be affected by a cryptominer is if they found the PC is slowing down, its battery running out at a quicker rate, or the fan blowing at full blast.
Don’t make the mistake of thinking that this is a victimless crime. If your computers get recruited into a cryptomining botnet like Smominru, it’s your electricity and computer power that is being stolen.
Keep your computers up-to-date with security patches, defended with layered security solutions, and your wits about you.
Learn more / En savoir plus / mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive
https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency
https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking