WhatsApp has filed a suit in federal court accusing Israeli mobile surveillance maker NSO Group of creating an exploit that was used hundreds of times to hack into target’s phone.
The lawsuit, filed in a California federal court, said the mobile surveillance outfit “developed their malware in order to access messages and other communications after they were decrypted” on target devices.
The attack worked by exploiting an audio-calling vulnerability in WhatsApp. Users may appear to get an ordinary call, but the malware would quietly infect the device with spyware, giving the attackers full access to the device.
In some cases it happened so quickly, the target’s phone may not have rung at all.
Because WhatsApp is end-to-end encrypted, it’s near-impossible to access the messages as they traverse the internet. But in recent years, governments and mobile spyware companies have begun targeting the devices where the messages were sent or received. The logic goes that if you hack the device, you can obtain its data.
That’s what WhatsApp says happened.
WhatsApp, owned by Facebook, quickly patched the vulnerability. Although blame fell fast on NSO Group, WhatsApp did not publicly accuse the company at the time — until now.
In an op-ed posted shortly after the suit was filed, WhatsApp head Will Cathcart said the messaging giant “learned that the attackers used servers and Internet-hosting services that were previously associated” with NSO Group, and that certain WhatsApp accounts used during the attacks were traced back to the company.
“While their attack was highly sophisticated, their attempts to cover their tracks were not entirely successful,” said Cathcart.
The attack involved disguising the malicious code as call settings, allowing the surveillance outfit to deliver the code as if it came from WhatsApp’s signaling servers. Once the malicious calls were delivered to the target’s phone, they “injected the malicious code into the memory of the target device — even when the target did not answer the call,” the complaint read. When the code was run, it sent a request to the surveillance company’s servers, and downloaded additional malware to the target’s device.
In total, some 1,400 targeted devices were affected by the exploit, the lawsuit said.
Most people were unaffected by the WhatsApp exploit. But WhatsApp said that more than 100 human rights defenders, journalists and “other members of civil society” were targeted by the attack.
Other targets included government officials and diplomats.
In a statement, NSO Group said: “In the strongest possible terms, we dispute today’s allegations and will vigorously fight them.”
 Your new post is loading...
Your new post is loading...
 Your new post is loading...
Your new post is loading...




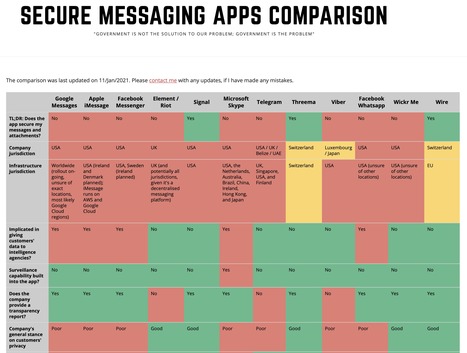









In the midst of #WhatsAppGate, @Telegram announced 25 million new registrations in the past 72 hours, and more than half a billion active users.
Beyond simplistic comparisons buzzing through the #Kommentariat, the offer is much more abundant. Besides, Skype or Viber were not born out of the last rain.
While solutions seems to focus on #privacy enforcement, the question of interoperability is another possible avenue : after all, a large number of these apps are based on the open source #XMPP protocol from Jabber (and therefore Orange). Why not enforce some level of interconnection ?
Simplicity is the other issue, and there WhatsApp has a huge advantage, given how easy it is to set up a group, whether for a family, project, or circumstantial powwow, and share photos and comments.
But simplicity also means not having to remember the application I was using in my last conversation with you !
WhatsApp and Facebook bend the knee following customer backlash. #WhatsAppGate
https://techcrunch.com/2021/01/15/whatsapp-delays-new-data-sharing-policy-enforcement-to-may-15/