 Your new post is loading...
 Your new post is loading...
On pourrait croire que depuis les scandales liés à Superfish et Edellroot, les fabricants d’ordinateurs ont renforcé les contrôles sur les logiciels préinstallés vendus avec leurs machines. Mais si l’on croit les chercheurs des équipes de Duo Security, la lutte contre les bloatwares n’est pas prête de se terminer.
Rappelons que les constructeurs proposent effet tous leurs machines avec des logiciels préinstallés, généralement qualifiés de bloatware ou crapware. Ces utilitaires à l’utilité parfois relative permettent généralement de contrôler l’état de la machine ou proposent certains services annexes à l’utilisateur.
L’étude menée par Duo Security porte sur une dizaine de machines achetées dans le commerce auprès de différents constructeurs : Lenovo, Dell, HP ainsi que Acer et Asus. Toutes sont livrées avec des logiciels préinstallés, que les chercheurs ont analysés afin de déterminer lesquels pouvaient présenter des failles de sécurité.
La conclusion est sans appel « Tous les constructeurs livraient leurs machines avec un logiciel présentant au moins une faille de sécurité permettant à une attaque de type man in the middle d’exécuter du code sur la machine avec un haut niveau de privilège » expliquent ainsi les chercheurs dans un post de blog. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Bloatware
Via Gust MEES
La CNPD prévient d’une fuite de données d’une grande envergure au départ des jouets VTech, en raison d’une faille de sécurité. 9.204 profils sont touchés pour le Grand-Duché. Mode d’emploi pour les parents concernés.
La protection des données et, à l’inverse, les fuites possibles en cas de lacune des installations informatiques peuvent prendre des proportions importantes. La Commission nationale de protection des données (CNPD) indique en effet mercredi soir, dans un communiqué commun avec Securitymadein.lu, qu’une importante fuite de données a été détectée auprès de la société VTech.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Vtech
http://www.scoop.it/t/securite-pc-et-internet/?tag=DATA-BREACHES
Via Gust MEES
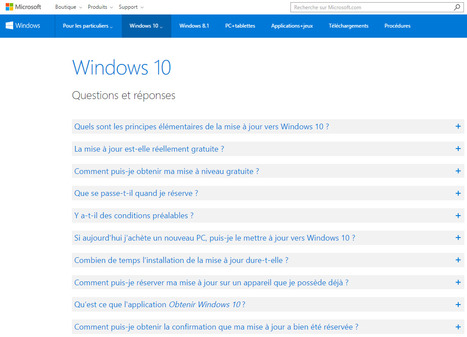
Trouvez les réponses aux questions fréquemment posées sur la mise à jour gratuite vers Windows 10 et le processus de mise à jour.
Via Gust MEES
The fact that a company called Hacking Team was hacked, combined with the disclosure of their shady clientele, has several diminished the credibility of previous denials the company has made about their engaging in this kind of profiteering. It also validates criticisms that groups like the EFF and Reporters Without Borders have thrown at Hacking Team – basically, that they provide agents around the globe with cyberweapons used for the suppression of democracy and the violation of human rights.
Hacking Team offers their clients a “Remote Control System” (RCS) that combines a variety of spyware technologies into one comprehensive surveillance suite. According to The Citizen Lab, this RCS product essentially allows users to do things like turn the microphones and cameras of their targets’ mobile phones on/off, monitor and record communications, and copy files and passwords.
While Hacking Team sells exclusively to governments, companies are designing products and services to give them similar capabilities.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Hacking+Team+breach
- https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/
Via Gust MEES
A new year begins at midnight and Threatpost highlights seven things you're bound to contend with in 2015.
===> Forewarned is Forearmed!!! <===
Via Gust MEES
40 years of the microprocessor: a look back at the most significant microprocessor developments that have shaped the IT Industry (Infographic)...
Via Gust MEES
|
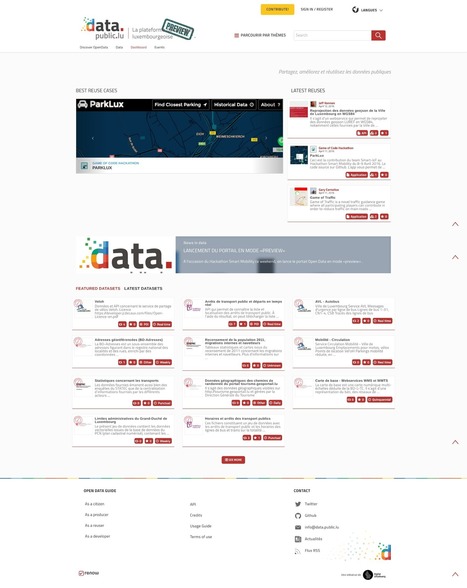
A l’occasion de l’événement Game of Code, les 8, 9 et 10 avril derniers, Digital Lëtzebuerg en collaboration avec le Centre des Technologies de l’Information de l’Etat Luxembourgeois et l’administration du Cadastre et de la topographie lançait en version bêta son portail de données ouvertes data.public.lu. Développé à partir de udata, le moteur de la plateforme data.gouv.fr, ce site est le fruit d’une collaboration initiée il y a quelques mois entre la France et le Luxembourg.
Un lancement marqué par l’importance des réutilisations open data Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/luxembourg-europe/?tag=Digital+L%C3%ABtzebuerg
Via Gust MEES, juandoming
Des chercheurs de Check Point ont identifié de nouvelles vulnérabilités dans les dispositifs Android. Certifi-gate permet à des hackers de prendre le contrôle d'un appareil.
«Certifi-gate», tel est le nom donné à un vulnérabilité découverte par des chercheurs de Check Point au sein du système d'exploitation Android. Elle permet à des applications pour offrir aux pirates un accès sans restriction à l'appareil et ainsi, selon Check Point, «dérober des données personnelles, localiser les appareils, activer le microphone pour enregistrer des conversations, et plus encore».
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Certifi-gate
http://www.scoop.it/t/securite-pc-et-internet/?tag=Android
Via Gust MEES
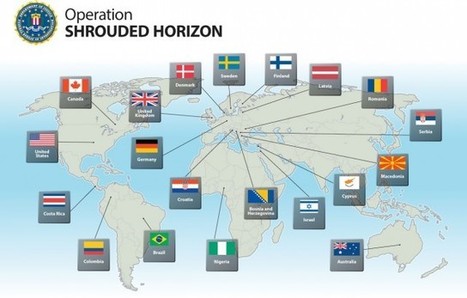
A joint operation by the FBI and the law enforcement agencies of 19 other countries has led to the takedown of the notorious discussion forum for criminal hackers, Darkode.me. It was the most central English-speaking hub for the sale of credit card numbers, criminal hacking hardware, and malware written for commercial sale. Originally called Darkode.com, the forum had shifted several times in response to pressure from authorities and the “white hat” hacking community, adding layers upon layers of security.
It was a highly encrypted, invite-only forum hosted by true paranoiacs, and featuring a tiered access system designed to keep any unavoidable infiltrators away from the most sensitive discussions. With an air of true satisfaction, the FBI announcement makes the implication clear as day: if we can get Darkode, we can get anybody.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cybercrime
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Darkode
Via Gust MEES
If you're an avid video gamer, chances are that you know of Epic Games. They're the developers of popular games such as Infinity Blade, Gears of War, Unreal Tournament… and – if you’re as old as me – you might even remember their founder Tim Sweeney’s classic DOS era shareware gameZZT.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Phishing
Via Gust MEES
As a competitive intelligence manager, you’ve probably grappled with multiple challenges over the years. Common challenges include, how do we develop our company’s internal competitive intelligence network; how can we gain insights in a broad range of specialized topics; how do we share market signals with key stakeholders effectively; how can we maximize the output from internal resources, and more. These are questions we help our clients address with the Intelligence Plaza all the time. here is a quick 10 point checklist for an efficient and trusted competitive intelligence program:
Via ismokuhanen, Gust MEES
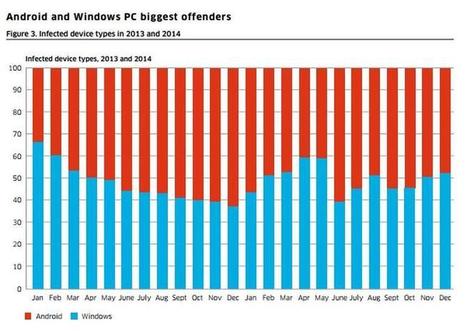
Around 16 million mobile devices worldwide was hit by malware as at the end of 2014, while attacks on communications networks rose during the year, according to new research by Alcatel-Lucent. . Less than 1 percent of infections came from iPhone and Blackberry smartphones. Although, new vulnerabilities, such as the 'Find My iPhone' exploit discovered last year, have emerged in the past 12 months, showing that they are not immune from malware threats.
Via Gust MEES
It’s always nice to get something for free. Or is it? There are really some free lunches on the net. But what appears to be free can have a hidden price, which often is paid by other means than money. Internet did for a long time lack payment models and everything on the net was truly free. This was fine on a net that was an academic tool and playground for enthusiasts. Our Internet of today is totally different, and to a large extent business driven. But the culture of getting stuff for free on the net is deeply rooted. People are used to free stuff, or are hesitant to use payment on the net in fear of fraud. This has created a lot of new business models based on free products and services. Either genuinely free or with a hidden compensation. One of the important skills for today’s cybercitizens is to recognize these business models and understand the hidden risks and compensations. Read on to learn how.
Via Gust MEES
Set up a longer passkey and change or hide the SSID, suggests Rick Maybury (Useful tip - How can I stop my wireless router getting hacked?
Via TechinBiz, THE OFFICIAL ANDREASCY
UNESCO in partnership with industry leaders and global subject experts has elaborated the ICT Competency Framework for Teachers which sets out the competencies required to teach effectively.
Via Dr. Susan Bainbridge
|



 Your new post is loading...
Your new post is loading...





























Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Bloatware