Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
November 1, 2017 10:55 AM
|
Millions of websites running WordPress are being strongly urged to update to the latest version of the popular content management system as soon as possible, after a serious security vulnerability was uncovered.

|
Scooped by
Gust MEES
October 3, 2017 9:39 AM
|
Von wegen Sicherheit: Unter dem Deckmantel eines legitimen WordPress-Plugin richtet X-WP-SPAM-SHIELD-PRO eine Backdoor auf Webseiten ein.
Wer auf seiner WordPress-Webseite das Plugin X-WP-SPAM-SHIELD-PRO installiert hat, sollte dieses schleunigst deinstallieren: Das Fake-Sicherheits-Plugin ist Malware und richtet unter anderem einen Fernzugriff für die Drahtzieher des Zusatzmoduls ein, warnen Sicherheitsforscher von Sucuri.
Die Betrüger missbrauchen dabei den Namen des legitimen Sicherheits-Plugins WP-SpamShield Anti-Spam, welches Spam von WordPress-Seiten fernhalten soll. X-WP-SPAM-SHIELD-PRO ist nicht im offiziellen Plugin-Bereich von WordPress zu finden. Es stammt aus einer von den Sicherheitsforschern nicht näher beschriebenen Quelle. Aus Sicherheitsgründen ist es ratsam, nur Plugins aus der offiziellen Quelle zu installieren. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?&tag=Cybersecurity

|
Scooped by
Gust MEES
March 2, 2017 7:04 AM
|
NextGEN Gallery is an extraordinarily popular plugin for self-hosted WordPress websites, having been downloaded over 16.5 million times.
The software’s widespread popularity (it claims to have been “the industry’s standard WordPress gallery plugin” since 2007) makes it an seemingly obvious choice for website owners looking to add image galleries to their sites.
Researchers at Sucuri uncovered a severe SQL injection vulnerability in NextGEN Gallery’s code which could be used by a malicious attacker to steal sensitive information such as hashed passwords and WordPress secret keys: Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?&tag=Cybersecurity

|
Scooped by
Gust MEES
February 7, 2017 8:14 PM
|

|
Scooped by
Gust MEES
September 8, 2016 12:24 PM
|
With the huge number of sites running WordPress, and the frequency with which attackers exploit vulnerabilities on the platform to launch malicious attacks, it makes sense for self-hosting bloggers to update their systems as soon as possible.
Security vulnerabilities are frequently uncovered in third-party WordPress plugins, but the above fix addresses bugs in the main WordPress content management system itself. Meaning that just about any site running WordPress could be at risk.
Fortunately, updating is pretty easy. Go to your WordPress admin panel and choose Dashboard > Updates.
Of course, it's always good practice to test a new version of the software on a non-live version of your site first (often known as a staging site) - just in case.
Since WordPress 3.7 was released in October 2013, the software has come with the option of automatic security updates - hopefully ensuring that many site admins won't have to worry so much about whether they have kept their software updated or not.
But, of course, there will always be those who don't have automatic updates enabled and may miss the news. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?tag=Cybersecurity

|
Scooped by
Gust MEES
July 23, 2015 7:06 PM
|
The latest version of the software, a security update, is WordPress 4.2.3.

|
Scooped by
Gust MEES
April 8, 2015 7:16 AM
|
The FBI has issued a warning that ISIS-supporting hackers are exploiting vulnerabilities on websites running WordPress.

|
Scooped by
Gust MEES
March 16, 2015 6:18 PM
|
Multiple vulnerabilities in the WPML plugin that could allow attackers to access databases, delete site content, and gain administrative privileges have put as many as 400,000 websites at risk.
WPML is a popular WordPress plugin used for creating multi-lingual websites, and researchers have uncovered four critical vulnerabilities, the most serious being a SQL injection flaw that can allow unauthenticated access to the website’s database, exposing user details and password hashes.

|
Scooped by
Gust MEES
February 25, 2015 9:23 AM
|
A critical security flaw in a plugin called WP-Slimstat is to blame.
Over one million websites running the WordPress content management system are potentially at risk of being hijacked due to a critical vulnerability exposed in the WP-Slimstat plugin. On Tuesday, a security advisory posted by researcher Marc-Alexandre Montpas from security firm Sucuri said the "very high risk" vulnerability found in versions of WP-Slimstat 3.9.5 and lower could lead to cyberattackers being able to break the plugin's "secret" key, perform an SQL injection and take over a target website.
Learn more:
- http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing

|
Scooped by
Gust MEES
August 6, 2014 8:41 PM
|
If your website runs on a self-hosted WordPress installation or on Drupal, update your software now.

|
Scooped by
Gust MEES
June 2, 2014 9:41 AM
|
Do you use the popular All in One SEO Pack plugin on your WordPress website?
===> If so, you need to update the plugin as soon as possible to the latest version!!! <===
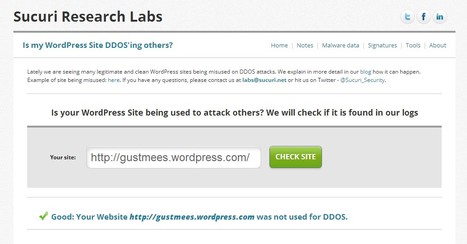
Web site security monitoring and malware removal
Is my WordPress Site DDOS'ing others? Lately we are seeing many legitimate and clean WordPress sites being misused on DDOS attacks. We explain in more detail in our blog how it can happen. . Example of site being misused: here. If you have any questions, please contact us at labs@sucuri.net or hit us on Twitter - @Sucuri_Security. . ===> Check out if YOUR WordPress site is secure! <===

|
Scooped by
Gust MEES
February 10, 2014 9:52 AM
|
Ce bulletin a été rédigé par Vigil@nce : http://vigilance.fr/offre SYNTHÈSE DE LA VULNÉRABILITÉ Un attaquant peut employer plusieurs vulnérabilités de (...)
Gravité : 2/4 Date création : 24/01/2014 DESCRIPTION DE LA VULNÉRABILITÉ Plusieurs vulnérabilités ont été annoncées dans WordPress WP-E-Commerce. Un attaquant peut uploader un fichier illicite via save-data.functions.php, afin par exemple de déposer un Cheval de Troie. [grav:2/4] Un attaquant peut utiliser ajax.php, afin d’exécuter du code. [grav:2/4] Un attaquant peut utiliser display-sales-logs.php, afin d’exécuter du code. [grav:2/4] Un attaquant peut utiliser misc.functions.php, afin d’obtenir des informations sensibles. [grav:2/4] Un attaquant peut provoquer un Cross Site Scripting dans swfupload.swf, afin d’exécuter du code JavaScript dans le contexte du site web. [grav:2/4]
|

|
Scooped by
Gust MEES
October 3, 2017 11:43 AM
|
Outdated versions of three popular WordPress plugins suffer from a "critical" zero-day vulnerability that enables an attacker to take over a website.
The bug is a PHP object injection flaw that affects the following plugins: Appointments (versions prior to 2.2.2), Flickr Gallery (versions prior to 1.5.3), and RegistrationMagic-Custom Registration Forms (versions prior to 3.7.9.3).
Together, those plugins have a combined user base of over 21,000 WordPress customers. All three have already received a fix for the security issue, which is rated "Critical" with a CVSS rating of 9.8. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?&tag=Cybersecurity

|
Scooped by
Gust MEES
September 26, 2017 11:43 AM
|
WordPress 4.8.2 is out, featuring nine security fixes website owners will want to apply, well, now.
All told, there have been six updates this year featuring security fixes, including January’s silent patch for a nasty zero day, this being the first since May’s v4.7.5.
The maintenance side of the update features six other software updates but focussing on the bit that bothers Naked Security readers most, security, we see five Cross-Site Scripting (XSS) flaws (a perennially popular attack vector that refuses to die), two path or directory traversal issues, and one covering an open redirect. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing

|
Scooped by
Gust MEES
February 23, 2017 1:06 PM
|

|
Scooped by
Gust MEES
January 31, 2017 6:41 AM
|
Attention menaces. WordPress a patché trois vulnérabilités, dont une faille de type XSS (cross-site scripting) et un problème d’injection SQL pouvant déboucher sur la création de vulnérabilités supplémentaires.
La semaine dernière, les développeurs du logiciel de CMS annonçaient dans un bulletin de sécurité que les nouveaux correctifs remédiaient à trois importants problèmes de sécurité, tous affectant WordPress versions 4.7.1 et antérieures. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing

|
Scooped by
Gust MEES
January 7, 2016 10:34 AM
|
Über eine Cross-Site-Scripting-Schwachstelle können Angreifer WordPress-Installationen kompromittieren. Betroffen sind alle Versionen bis einschließlich WordPress 4.4.
Mit einem Wartungs-Update beheben die Entwickler des Content-Management-Systems WordPress insgesamt 52 Bugs, die seit erscheinen Version 4.4 gefunden wurden. Admins, die Auto-Updates deaktiviert haben, sollten WordPress 4.4.1 schnellstmöglich manuell installieren, da das Update auch eine Cross-Site-Scripting-Lücke (XSS) behebt, über die Angreifer das CMS kompromittieren können.

|
Scooped by
Gust MEES
April 21, 2015 12:33 PM
|
Vulnerable websites can be exploited via XSS to steal user accounts, change settings or phish passwords from unsuspecting users. In fact, XSS flaws are one of the most commonly encountered security flaws found on websites.
Patching is obviously sensible and should be undertaken at the earliest opportunity, but never forget that additional layers of protection can go beyond patches – and perhaps be proactive in defending your systems from abuse during the time when no official fixes are available.

|
Scooped by
Gust MEES
March 20, 2015 5:59 PM
|
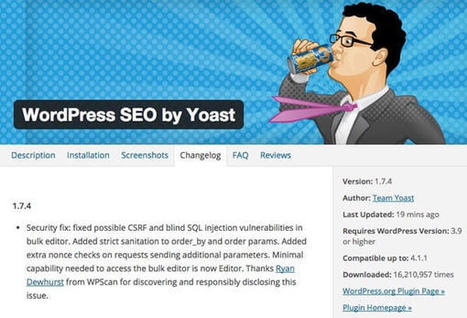
Another popular Yoast Wordpress plugin has been found sporting a critical vulnerability that can be exploited by attackers to take over control of the site.
A week ago it was the WordPress SEO plugin, which is actively used on more than a million of WP sites. This time it's the company's Google Analytics plugin, which has apparently been downloaded around 7 million times.
According to the researcher who discovered the issue, Jouko Pynnönen of Finland-based Klikki Oy, the vulnerability "allows an unauthenticated attacker to store arbitrary HTML, including JavaScript, in the WordPress administrator’s Dashboard on the target system. The JavaScript will be triggered when an administrator views the plug-in’s settings panel. No further user interaction is required."
Learn more:
- http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing

|
Scooped by
Gust MEES
March 12, 2015 12:15 AM
|
A serious vulnerability was found in one of the most popular WordPress plugins, and guess what? It got fixed really quickly. :) All that remains is for you to apply the update on your web server.

|
Scooped by
Gust MEES
February 5, 2015 6:27 PM
|
Thousands of websites are at risk of being exploited by a previously undisclosed vulnerability in a WordPress plugin, which researchers say could be used to inject malicious code into websites.
The flaw exists in Fancybox, a popular image displaying tool, through which Sucuri researchers say malware or any other script can be added to a vulnerable site.
"We can confirm that this plugin has a serious vulnerability," the researchers wrote. "It's being actively exploited in the wild, leading to many compromised websites," the researchers wrote.
A glut of Wordpress sites have fallen victim to both malware infections and a series of brute force attacks that have making the rounds over the past several

|
Scooped by
Gust MEES
April 15, 2014 4:41 PM
|
WordPress.com has taken steps to deal with the Heartbleed vulnerability. Here's what you need to know.
Learn more:

|
Rescooped by
Gust MEES
from 21st Century Learning and Teaching
March 11, 2014 10:47 AM
|
Legitimate sites forced to aid criminals' illicit botnet operations
Hackers have hijacked more than 162,000 legitimate WordPress sites, connecting them to a criminal botnet and forcing them to mount distributed denial-of-service (DDoS) attacks, according to security firm Sucuri.
Sucuri CTO Daniel Cid said the company uncovered the botnet when analysing an attack targeting one of its customers. Cid said Sucuri managed to trace the source of the attack to legitimate WordPress sites. "The most interesting part is that all the requests were coming from valid and legitimate WordPress sites. Yes, other WordPress sites were sending random requests at a very large scale and bringing the site down," read the blog.
|
 Your new post is loading...
Your new post is loading...
 Your new post is loading...
Your new post is loading...