 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
December 29, 2018 4:13 PM
|
Was haben die Netzauftritte von Fußballstar Cristiano Ronaldo und der gemeinnützigen Organisation Make-a-Wish mit indischen Behörden-Websites gemeinsam? Sie alle wurden schon einmal von Kriminellen so manipuliert, dass sie die Rechenleistung der Computer und Smartphones ihrer Besucher kaperten. Bis die Betreiber der Angebote merkten, was los war, schürften die Geräte der Website-Besucher nach der Digitalwährung Monero - immer solange, wie die Seiten im Browser geöffnet waren.
Internetsurfer werden ohne ihr Wissen Krypto-Schürfer: Diese Betrugsmasche, die auch mit anderen Digitalwährungen funktioniert, heißt Cryptojacking - kombiniert aus "Cryptocurrency" (Kryptowährung) und "Hijacking" (Entführung). Der Angriff über den Browser schadet dem Gerät in der Regel nicht unmittelbar, davon abgesehen, dass es wegen der Rechenvorgänge oft heiß oder lauter wird. Er ist aber doch ärgerlich, weil Dritte hier quasi Akkuleistung oder Strom sowie Bandbreite von ihren Opfern abgreifen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
February 19, 2018 9:40 AM
|
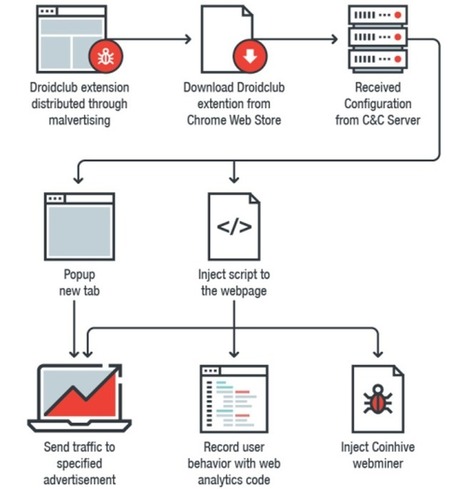
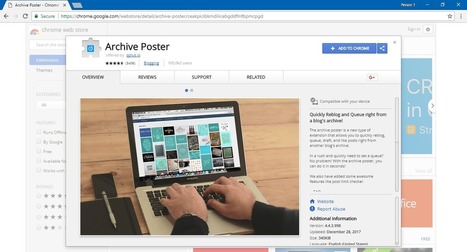
Google has removed 89 malicious extensions from the Chrome Web Store that have been installed on over 420,000 browsers, turning them into Monero-mining slaves and loading a tool to record and replay what their owners do on every website they visit.
Researchers at Trend Micro dubbed the family of malicious extensions Droidclub and discovered they included a software library with so-called "session-replay scripts" used by online analytics firms.
Princeton's Center for Information Technology in November drew attention to the increasing use of session-replay scripts by third-party analytics firms on high-traffic websites.
The study looked at replay services from Yandex, FullStory, Hotjar, UserReplay, Smartlook, Clicktale, and SessionCam, which were found on nearly 500 popular sites.
The scripts allow a site owner to essentially shoulder-surf their visitors by recording and replaying your "keystrokes, mouse movements, and scrolling behavior, along with the entire contents of the pages you visit".
But instead of allowing a site owner to record and play back what users do on one site, Droidclub extensions allow the attacker to see what victims do on every single site they visit. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=Session-Replay+Scripts

|
Scooped by
Gust MEES
February 17, 2018 12:19 PM
|
A cryptojacking attack hit thousands of websites, including government ones.
Surreptitious mining of cryptocurrency by hackers is spreading very, very fast.
The news: Over 4,000 websites, including those of the US federal judiciary and the UK National Health Service, have been weaponized by hackers to mine the cryptocurrency Monero on their behalf.
How it worked: Hackers injected malware into a widely used plug-in called Browsealoud that reads web pages our loud as a way of helping partially sighted people navigate the internet. The malware is based on the popular app Coinhive, a piece of software that uses processing power on someone’s device to mine cryptocurrency. The malicious version of the app does this without people's knowledge, coopting their computing power to enrich hackers.
Why it matters: Cryptojacking is rapidly becoming one of the world’s biggest cyberthreats. This news shows how easy it is for crooks to spread the trick, by infecting a single product used across multiples sites with a single hack.
Learn more / En savoir plus / mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
February 1, 2018 12:15 PM
|

|
Scooped by
Gust MEES
January 26, 2018 7:25 PM
|

|
Scooped by
Gust MEES
January 1, 2018 9:58 AM
|
|

|
Scooped by
Gust MEES
March 12, 2018 9:47 AM
|

|
Scooped by
Gust MEES
February 18, 2018 7:39 AM
|

|
Scooped by
Gust MEES
February 15, 2018 6:30 AM
|
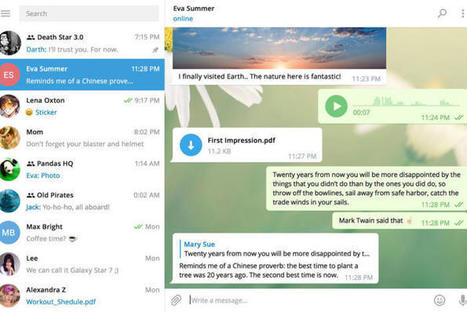
Cyber thugs have been exploiting a zero-day flaw in the Telegram Messenger desktop app in order to mine for cryptocurrencies or to install a backdoor to remotely control victims’ computers.
Kaspersky Lab discovered “in the wild” attacks on Telegram Messenger’s Windows desktop client back in October 2017. The vulnerability in the popular Telegram app had been actively exploited since March 2017 to mine a variety of cryptocurrencies, such as Monero, Zcash, Fantomcoin and others. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Telegram

|
Scooped by
Gust MEES
February 1, 2018 11:22 AM
|
Why go to all the bother of writing ransomware that demands victims pay a Bitcoin ransom? If all you want is cryptocurrency, why not use the infected computers to mine the crypto coins themselves?
That way you don’t have to rely on a human victim buying some Bitcoin, and nervously making their way onto the dark web to make their ransom payment.
According to security researchers at Proofpoint, that’s exactly the reasoning shown by online criminals who are moving from regular ransomware to cryptomining.
A Monero-mining botnet called Smominru is said to have infected 526,000 Windows PCs since May 2017 – mostly in Russia, India, and Taiwan – and is earning millions of dollars for its operators. In fact, the biggest clue that most users will have that their computers may be affected by a cryptominer is if they found the PC is slowing down, its battery running out at a quicker rate, or the fan blowing at full blast. Don’t make the mistake of thinking that this is a victimless crime. If your computers get recruited into a cryptomining botnet like Smominru, it’s your electricity and computer power that is being stolen. Keep your computers up-to-date with security patches, defended with layered security solutions, and your wits about you. Learn more / En savoir plus / mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
January 26, 2018 5:36 PM
|
Stealth cryptocurrency mining in one’s browser, without the user’s permission, is one of our least-favorite trends of the past six months. While there were always questions about whether cryptocurrency mining in-browser could serve as an alternate revenue stream for websites, there was at least an idea that some kind of alternate funding system might emerge — hopefully putting an end to the eternal cycle of invasive ads driving users to deploy ad blockers, which then drives websites to adopt more invasive ads.
But instead of an informed approach in which end users consented to such mining, we’ve seen stealth operations popping up everywhere that steal CPU cycles from users, particularly if more than one crypto mining malware is running simultaneously. While most of these plugins are written to only put a light load on user’s CPUs, that’s only if the miner is running in a single browser instance, and only if it’s running on a single site. Our tests back in 2017 showed that using different browsers can defeat this dubious attempt to sandbox the performance impact. And, of course, even running one site will still drain battery life more quickly than having the CPU properly idled.
It’s like someone figured out how to monetize the awful Flash ads everyone used to hate for eating CPU cycles. A true win-win! And now it’s even hitting YouTube.
TrendMicro has released an updated report, showing a sharp rise in ads served by Google’s DoubleClick service being infested with mining software. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking
|



 Your new post is loading...
Your new post is loading...















Was haben die Netzauftritte von Fußballstar Cristiano Ronaldo und der gemeinnützigen Organisation Make-a-Wish mit indischen Behörden-Websites gemeinsam? Sie alle wurden schon einmal von Kriminellen so manipuliert, dass sie die Rechenleistung der Computer und Smartphones ihrer Besucher kaperten. Bis die Betreiber der Angebote merkten, was los war, schürften die Geräte der Website-Besucher nach der Digitalwährung Monero - immer solange, wie die Seiten im Browser geöffnet waren.
Internetsurfer werden ohne ihr Wissen Krypto-Schürfer: Diese Betrugsmasche, die auch mit anderen Digitalwährungen funktioniert, heißt Cryptojacking - kombiniert aus "Cryptocurrency" (Kryptowährung) und "Hijacking" (Entführung). Der Angriff über den Browser schadet dem Gerät in der Regel nicht unmittelbar, davon abgesehen, dass es wegen der Rechenvorgänge oft heiß oder lauter wird. Er ist aber doch ärgerlich, weil Dritte hier quasi Akkuleistung oder Strom sowie Bandbreite von ihren Opfern abgreifen.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency
https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking