 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
March 13, 10:23 AM
|
A high-severity vulnerability was discovered and patched in the All-in-One WP Migration and Backup plugin, which has over five million installations. The vulnerability requires no user authentication, making it easier for an attacker to compromise a website, but this is mitigated by a restricted attack method.
The vulnerability was assigned a severity rating of 7.5 (High), which is below the highest severity level, labeled Critical. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
December 22, 2020 9:57 AM
|
Eine Sicherheitslücke im beliebten Plug-in Contact Form 7 ermöglicht es Angreifern, Dateien jeglichen Typs hochzuladen. Ein Sicherheitsupdate ist verfügbar.
Eine gefährliche Sicherheitslücke im WordPress-Plug-in Contact Form 7 gefährdet Millionen von Word-Press-Webseiten. Gefunden wurde die Schwachstelle von Sicherheitsforschern von Astra, wie «Heise Online» berichtet.
Contact Form 7 ermöglicht es Nutzern, mehrere Kontaktformulare auf einer Webseite hinzuzufügen und ist nach Angaben des Astra-Research-Teams eines der beliebtesten WordPress-Plugins. Auf der entsprechenden WordPress-Seite sind über 5 Millionen aktive Installationen ausgewisen und das Plug-in ist in 62 Sprachen verfügbar.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
October 22, 2020 12:41 PM
|
L'équipe de sécurité de WordPress a pris une mesure qu'elle utilise rarement la semaine dernière, en utilisant une capacité interne peu connue qui permet de forcer une mise à jour de sécurité pour un plug-in populaire.
Les sites WordPress utilisant le plug-in Loginizer ont donc été mis à jour de force cette semaine, avec la version 1.6.4 de Loginizer. Cette version contient un correctif de sécurité pour un dangereux bug d'injection SQL, qui aurait pu permettre à des pirates de s'emparer de sites WordPress utilisant des versions plus anciennes du plug-in Loginizer.
Loginizer est l'un des plug-in WordPress les plus populaires aujourd'hui, avec une base d'installation de plus d'un million de sites. Il fournit des améliorations de sécurité pour la page de connexion à WordPress. Selon sa description officielle, Loginizer peut mettre sur liste noire ou blanche les adresses IP visant à accéder à la page de connexion de WordPress, ajouter la prise en charge de l'authentification à deux facteurs, ou ajouter de simples CAPTCHA pour bloquer les tentatives de connexion automatisées, parmi de nombreuses autres fonctionnalités. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
August 15, 2020 8:15 AM
|
The recently patched flaws could be abused by an unauthenticated, remote attackers to take over vulnerable websites.
A plugin that is designed to add quizzes and surveys to WordPress websites has patched two critical vulnerabilities. The flaws can be exploited by remote, unauthenticated attackers to launch varying attacks – including fully taking over vulnerable websites.
The plugin, Quiz and Survey Master, is actively installed on over 30,000 websites. The two critical flaws discovered by researchers include an arbitrary file-upload vulnerability, ranking 10 out of 10 on the CVSS scale; as well as an unauthenticated arbitrary file deletion error, ranking 9.9 out of 10. A patch is available for both issues in version 7.0.1 of the plugin, said the researchers with Wordfence who discovered the flaws, in a Thursday post. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
February 15, 2020 9:24 AM
|
Critical security issues caused by improper access controls in a WordPress plugin designed for GDPR cookie compliance have been resolved, but hundreds of thousands of websites may still be vulnerable to attack.
The GDPR Cookie Consent plugin, offered by developer Cookie Law Info through WebToffee, has been designed to help ensure websites are compliant with the EU's General Data Protection Regulation (GDPR); specifically, obtaining consent for cookies from visitors, the creation of a Privacy & Cookies Policy page and the enablement of banners showing compliance.
The plugin accounts for over 700,000 active installs according to the WordPress library.
On January 28, NinTechNet researcher Jerome Bruandet discovered a vulnerability affecting GDPR Cookie Consent version 1.8.2 and below. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress https://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?&tag=Cybersecurity

|
Scooped by
Gust MEES
August 1, 2018 3:41 PM
|
Check Point hat rund 10.000 gehackte WordPress-Websites entdeckt, die Teil einer Strategie zur großflächigen Malware-Verbreitung über Werbenetzwerke sind.
Das IT-Sicherheitsunternehmen Check Point hat eine umfangreiche Malware-Kampagne entdeckt, die auf Malvertising – also dem Missbrauch von Werbeanzeigen zur gezielten Schadcode-Verbreitung – basiert. Gegenüber The Register berichteten die Forscher am vergangenen Montag von mehr als 40.000 wöchentlichen Infektionsversuchen über die präparierten Anzeigen. Sie sagten auch, dass die Kampagne noch aktiv sei.
(Bild: blog.checkpoint.com)
Beim Malvertising kaufen Kriminelle als "Advertiser" Werbeflächen auf den Websites von "Publishern" über den Umweg spezieller Werbenetzwerke ein. Die eingekauften Flächen nutzen sie dann, um Website-Besucher mittels Umleitungen auf Malware-Sites zu manövrieren. Meist läuft ein solcher Einkauf über automatisierte Online-Auktionen: Der Höchstbietende erhält den Zuschlag. Oft sind auch noch Zwischenhändler ("Reseller") beteiligt. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress https://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?&tag=Cybersecurity

|
Scooped by
Gust MEES
January 26, 2018 12:20 PM
|
A new report from researchers at Sucuri reveals that websites are once again being found infected by cryptomining code – stealing the resources of visiting computers to mine for the Monero cryptocurrency.
Many web surfers almost certainly don’t realise that the reason that their laptop’s fan is running at full blast is because the website they are viewing is tied up with the complex number-crunching necessary to earn the digital currency.
But, in a twist, this particular attack isn’t just interested in mining Monero. While the website’s front-end is digging for cryptocurrencies, the back-end is secretly hosting a keylogger designed to steal unsuspecting users’ login credentials.
With the keylogger in place, any information entered on any of the affected websites’ web forms will be surreptitiously sent to the hackers.
And yes, that includes the site’s login form. We’ve said it before, and we’ll no doubt say it again. And again. If your website is powered by the self-hosted edition of WordPress, it’s essential that you keep both it, and any third-party plugins, updated. Self-hosting your WordPress site is attractive in many ways, but you have to acknowledge that security is now your responsibility (or find yourself a managed wordpress host who is prepared to take it on for you). New vulnerabilities are found in the software and its many thousands of third-party plugins all the time. In short, if you don’t know what you’re doing, there’s a chance that your WordPress-running website has security holes which a malicious hacker could exploit. Such security weaknesses could potentially damage your brand, scam your website visitors, and help online criminals to make their fortune. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
December 21, 2017 5:10 PM
|
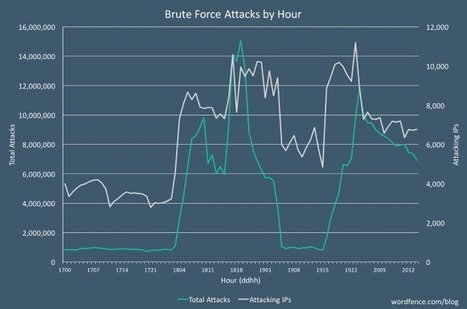
Over the course of the current week, WordPress sites around the globe have been the targets of a massive brute-force campaign during which hackers attempted to guess admin account logins in order to install a Monero miner on compromised sites.
The brute-force attack started on Monday morning, 03:00 AM UTC and is still going strong at the time of writing.
Brute-force attack targets over 190,000 WordPress sites/hour
To get an idea of the size of the campaign, WordPress security firm Wordfence says this was the biggest brute-force attack the company was forced to mitigate since its birth in 2012. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
December 21, 2017 12:11 PM
|
Un plugin WordPress vérolé a ouvert les portes de plus de 300 000 sites !
L'un des intérêts de WordPress est qu'il suffit de télécharger des plugins pour ajouter rapidement des fonctionnalités à son site. Une simplicité apparente qui peut aussi être source de vulnérabilités.
C'est ce qui s'est passé pour les utilisateurs d'un plugin ajoutant un captcha. L'entreprise qui le maintenait a vendu ce produit à une autre société, qui y a discrètement ajouté une porte dérobée. Plus de 300 000 sites utilisent cet outil et sont donc concernés par cette brèche, estime The Hacker News.
Le plugin, ainsi que quelques autres publiés par le même auteur et présentant la même porte dérobée, ont été supprimés de la boutique d'éléments de WordPress.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
June 18, 2015 8:40 AM
|
Digital Constitution - a dedicated website Microsoft set up to keep users informed of its efforts to counter US government's attempts to access customer emails the company stores in its data center located in Dublin, Ireland - has been compromised.
Unexpectedly, the attackers are not disgruntled privacy-minded hacktivists with a bone to pick with the company, but apparently scammers trying to push "amazing" offers from online casinos.
The site's code was apparently modified to include gambling-themed keywords so that it pops up in online gambling-related searches, and new pages like this one (which is still available as I write this) have been created on the site:
ZDNet's Zack Whittaker posits that the compromise was executed by leveraging vulnerabilities in the WordPress CMS used to run the site.
The site is running on WordPress 4.0.5, while the latest version is 4.2.2.

|
Scooped by
Gust MEES
November 24, 2014 2:30 PM
|
Security researchers have released a report examining a social engineering operation designed to trick admins into installing backdoor malware called CrytoPHP by way of of tainted CMS plugins and themes for WordPress, Joomla and Drupal.
The attackers lure targets into publishing the pirated themes and plugins by providing them for free, offerings that usually incur a fee for use.
“After being installed on a webserver the backdoor has several options of being controlled which include command and control server communication, mail communication as well as manual control,” the researchers revealed.

|
Rescooped by
Gust MEES
from Social Media and its influence
December 6, 2013 7:10 AM
|
Mit einer kostenlosen Version eines beliebten SEO-Plugins für WordPress versuchen Spammer, Administratoren zu ködern. Das Plugin entpuppt sich als Malware, dass eine Hintertür im Server öffnet und Besucher der Seite infiziert.
Researchers have concluded that 73% of the 40,000 most popular websites that use WordPress software are vulnerable to attack. But they admit they might be wrong. Even so, they still highlight an im...
|

|
Scooped by
Gust MEES
January 20, 2022 11:51 AM
|
The WordPress WP HTML Mail plugin, installed in over 20,000 sites, is vulnerable to a high-severity flaw that can lead to code injection and the distribution of convincing phishing emails.
'WP HTML Mail' is a plugin used for designing custom emails, contact form notifications, and generally tailored messages that online platforms send to their audience.
The plugin is compatible with WooCommerce, Ninja Forms, BuddyPress, and others. While the number of sites using it isn't large, many have a large audience, allowing the flaw to affect a significant number of Internet users.

|
Scooped by
Gust MEES
November 2, 2020 7:54 PM
|
WordPress bungles critical security 5.5.2 fix and saves face next day with 5.5.3 update.
The day after WordPress pushed out a critical 5.5.2 security update, patching a remote code execution bug and nine additional flaws, it was forced push out a second update and then a third 5.5.3 update.
The hiccup is tied to the WordPress auto-update feature that accidentally started sending 455 million websites a WordPress update (5.5.2) that caused new WordPress installs to fail. After realizing the error, it put the brakes on the rollout, and inadvertently triggered an Alpha version of WordPress to be downloaded to some customers.
The issue was corrected quickly on Oct. 30, but not before WordPress site operators reported new WordPress installs failing and others grousing over broken administration login pages. WordPress said a final 5.5.3 update is now available. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
September 7, 2020 7:18 AM
|
Millions of WordPress sites are being probed in automated attacks looking to exploit a recently discovered plugin vulnerability, according to security researchers.
Wordfence, which itself produces a plugin for the platform, revealed news of the zero-day bug at the start of September. It affects File Manager which, as the name suggests, is a plugin that helps users to manage files on their WordPress sites.
The plugin is installed on around 700,000 WordPress sites, and although Wordfence estimates that only around 37%, or 262,0000, are still running a vulnerable version, this hasn’t stopped attackers from trying their luck against a much larger number of users.
“Attacks against this vulnerability have risen dramatically over the last few days. Wordfence has recorded attacks against over one million sites today, September 4, 2020. Sites not using this plugin are still being probed by bots looking to identify and exploit vulnerable versions of the File Manager plugin, and we have recorded attacks against 1.7 million sites since the vulnerability was first exploited,” explained Wordfence’s Ram Gall.
“Although Wordfence protects well over three million WordPress sites, this is still only a portion of the WordPress ecosystem. As such, the true scale of these attacks is larger than what we were able to record.”
The vulnerability itself could allow a remote, unauthenticated user to execute commands and upload malicious files on a target site. Gall therefore urged users to patch the issue promptly by installing the latest version of the plug, v6.9. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
August 7, 2020 4:30 PM
|
Die beliebten Themes Divi und Extra von Elegant Themes sowie deren Divi Builder enthielten kritische Sicherheitslücken. Wenige Tage nachdem das Team von Wordfence diese entdeckt und gemeldet hat, stellt der Anbieter Updates bereit, die das Problem beseitigen. Betreiber von WordPress-Sites, die die Plugins nutzen, sollten diese zügig installieren, da mit flächendeckenden Angriffen zu rechnen ist.
Das Problem liegt in einer mangelhaften Dateityp-Prüfung der Upload-Funktion und führt dazu, dass bösartige Benutzer beliebige Dateien hochladen können – also etwa PHP-Dateien mit einer Webshell. Der Angreifer benötigt dazu allerdings bereits einen Zugang zur Site, etwa als registrierter Benutzer. Wordfence beschreibt in seinem Advisory die Ursachen des Problems genauer. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
September 2, 2019 11:04 AM
|
A hacker group is exploiting vulnerabilities in more than ten WordPress plugins to create rogue admin accounts on WordPress sites across the internet.
The attacks are an escalation part of a hacking campaign that started last month. During previous attacks, the hackers exploited vulnerabilities in the same plugins to plant malicious code on the hacked sites. This code was meant to show popup ads or to redirect incoming visitors to other websites.
However, two weeks ago, the group behind these attacks changed its tactics. Mikey Veenstra, a threat analyst with cybersecurity firm Defiant, told ZDNet today that starting with August 20, the hacker group modified the malicious code planted on hacked sites.
Instead of just inserting pop-ups and redirects, the malicious code also ran a function in order to test if the site visitor had the ability to create user accounts on the site, a feature only available for WordPress admin accounts. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
March 12, 2018 9:47 AM
|

|
Scooped by
Gust MEES
December 27, 2017 9:15 AM
|
Hundreds of WP sites continued to use backdoored plugins
These past attacks came into the spotlight again when recently, the WordPress Plugin Directory was changed so that the pages for old plugins that have been closed remain visible, albeit with the download option disabled. Previously, these pages were not accessible to the public.
Pages for all the former plugins that featured the intentional malicious code show that even after almost three years after the WordPress team removed the plugins from public download, there are hundreds of sites that still use them. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
December 21, 2017 1:17 PM
|
Ein Captcha-Plugin mit eingebauter Hintertür ist auf 300.000 WordPress-Seiten aktiv. Mittlerweile ist eine bereinigte Version erschienen. Das Vertrauen in den Entwickler bröckelt weiter.
Das WordPress-Plugin Captcha hatte eine Backdoor eingebaut, über die Betrüger auf WordPress-Seiten zugreifen können. Davor warnen Sicherheitsforscher von WordFence. Die Version 4.4.5 von Captcha soll die Hintertür nicht mehr enthalten.
Captcha kommt auf 300.000 WordPress-Seiten aktiv zum Einsatz. Nutzer sollten sicherstellen, dass sie die aktuelle Ausgabe installiert haben – den Sicherheitsforschern zufolge ist die Backdoor seit der Version 4.3.7 mit an Bord. Nun darf der Entwickler das Plugin nur noch mit vom WordPress-Team abgesegneten Updates aktualisieren. Die verseuchte Version wurde automatisch an Nutzer ausgespielt. Betrachtet man den Entwickler Simplywordpress näher, schrumpft das Vertrauen weiter und es liegt nahe, das Plugin dauerhaft zu entfernen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
December 21, 2017 10:18 AM
|
Sicherheitsforscher haben weltweit 14 Millionen Angriffe pro Stunde auf WordPress-Webseiten registriert. Die Angreifer wollen sich Zugang zu den Seiten verschaffen.
Derzeit erschüttert eine Angriffswelle gegen WordPress-Webseiten das Internet. Sicherheitsforscher von Wordfence haben dokumentiert, dass unbekannte Angreifer pro Stunde 190.000 Seiten via Brute Force attackieren. Als Spitzenwert haben sie stündlich 14 Millionen Angriffe beobachtet.
Dabei probieren sie im großen Stil Kombinationen von Nutzernamen und Passwörtern aus, um Admin-Zugriff auf Webseiten zu bekommen. Dabei sollen sie zum Teil organisiert vorgehen und versuchen, die möglichen Zugangsdaten von der URL und dem Inhalt der Webseite abzuleiten.
Malware schürft Kryptowährung
Ziel der Angriffe ist es Wordfence zufolge, auf gekaperten Seiten Software zum Schürfen der Kryptowährung Monero zu installieren oder diese als Ausgangspunkt für weitere Brute-Force-Attacken zu missbrauchen. Mittlerweile sollen die Angreifer dabei Monero im Wert von 100.000 US-Dollar geschürft haben.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency
Legitimate sites forced to aid criminals' illicit botnet operations
Hackers have hijacked more than 162,000 legitimate WordPress sites, connecting them to a criminal botnet and forcing them to mount distributed denial-of-service (DDoS) attacks, according to security firm Sucuri.
Sucuri CTO Daniel Cid said the company uncovered the botnet when analysing an attack targeting one of its customers. Cid said Sucuri managed to trace the source of the attack to legitimate WordPress sites. "The most interesting part is that all the requests were coming from valid and legitimate WordPress sites. Yes, other WordPress sites were sending random requests at a very large scale and bringing the site down," read the blog.
Via Gust MEES
|



 Your new post is loading...
Your new post is loading...































A high-severity vulnerability was discovered and patched in the All-in-One WP Migration and Backup plugin, which has over five million installations. The vulnerability requires no user authentication, making it easier for an attacker to compromise a website, but this is mitigated by a restricted attack method.
The vulnerability was assigned a severity rating of 7.5 (High), which is below the highest severity level, labeled Critical.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress