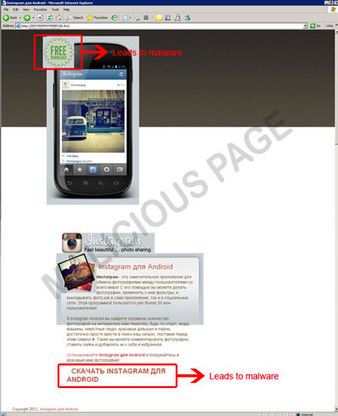
Downloading apps from Google Play, the official online Android app market, is not without its dangers.
Even though Google has been scanning the offered apps for malware by using "Bouncer" - an automated app scanning service that should, in theory, detect malicious software and developers who keep offering it - there are still instances where they aren't booted out of the market soon enough.
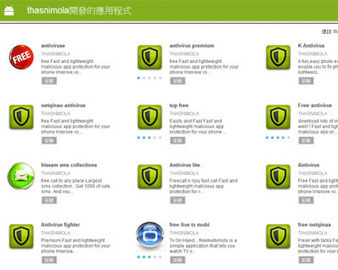
Security researchers from AegisLab have recently discovered over 15 fake AV and "free SMS" apps being offered by the same developer ("thasnimola") that has been flagged for selling fake NQ Mobile apps in April.
Read more and be aware...



 Your new post is loading...
Your new post is loading...