Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
ICT Security + Privacy + Piracy + Data Protection - Censorship - Des cours et infos gratuites sur la"Sécurité PC et Internet" pour usage non-commercial... (FR, EN+DE)...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|

Gust MEES's curator insight,
May 25, 2013 9:12 AM
A MUST watch!!! The video is in English with German subtitles...
|








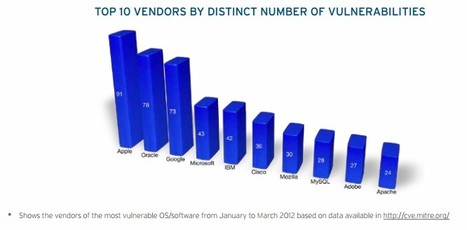

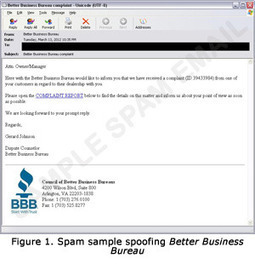







A MUST READ!!!