 Your new post is loading...
 Your new post is loading...
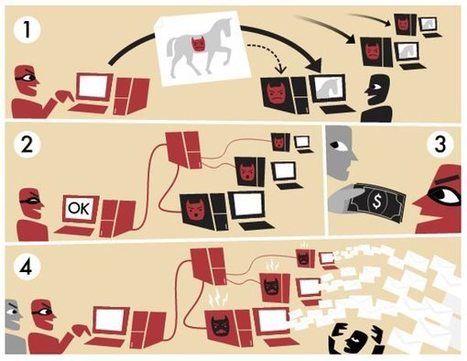
Successfully hiding messages in images has already been done, but is it possible to deliver an exploit in one - and run it?
Saumil Shah, founder and CEO of Net-Square, has demonstrated at the Hack in the Box Amsterdam 2015 that it's possible, and has posited that such attacks are more than likely to crop up in the near future, as he can't be the only one who thought about this, tried it and succeeded.
He is not the first one to try and hide exploits in images. But he created Stegosploit, a technology that lets attackers deliver executable JavaScript code via images, and trigger them, too.
The technology opens the door for attacks executed as simply as pointing users to sites containing a booby-trapped image or delivering the image via email. By virtue of simply viewing the image, the exploit code is triggered and can deliver malware on the victim's computer.
"A single file can be rendered as a perfectly valid HTML file, executed as a perfectly valid Javascript file, and displayed as a perfectly valid image, all at the same time," he explains.
"Stegosploit is the result of malicious exploit code hidden within pixels of the image carrying it. The image however, is a multi format container, which also contains the code required to decode the steganographically encoded pixels to execute the exploit."
This type of attack won't show in network traffic, he pointed out, be invisible to the naked eye, and the image will "autorun" in the browser.
In order to make the attack payload look harmless and not trigger defenses, Shah split it into two: dangerous pixel data (exploit code), and a safe decoder.
Via Gust MEES
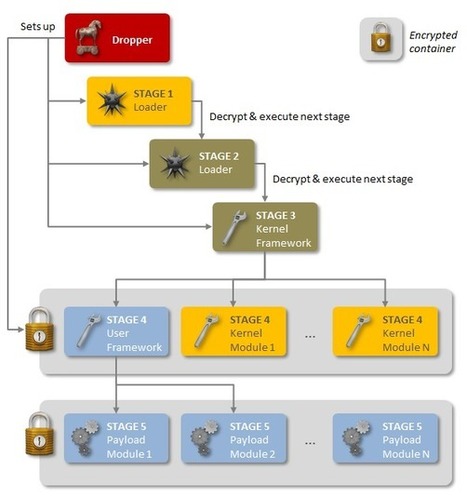
An advanced piece of malware, known as Regin, has been used in systematic spying campaigns against a range of international targets since at least 2008. A back door-type Trojan, Regin is a complex piece of malware whose structure displays a degree of technical competence rarely seen. Customizable with an extensive range of capabilities depending on the target, it provides its controllers with a powerful framework for mass surveillance and has been used in spying operations against government organizations, infrastructure operators, businesses, researchers, and private individuals.
It is likely that its development took months, if not years, to complete and its authors have gone to great lengths to cover its tracks. Its capabilities and the level of resources behind Regin indicate that it is one of the main cyberespionage tools used by a nation state.
As outlined in a new technical whitepaper from Symantec, Backdoor.Regin is a multi-staged threat and each stage is hidden and encrypted, with the exception of the first stage. Executing the first stage starts a domino chain of decryption and loading of each subsequent stage for a total of five stages. Each individual stage provides little information on the complete package. Only by acquiring all five stages is it possible to analyze and understand the threat.
Via Gust MEES
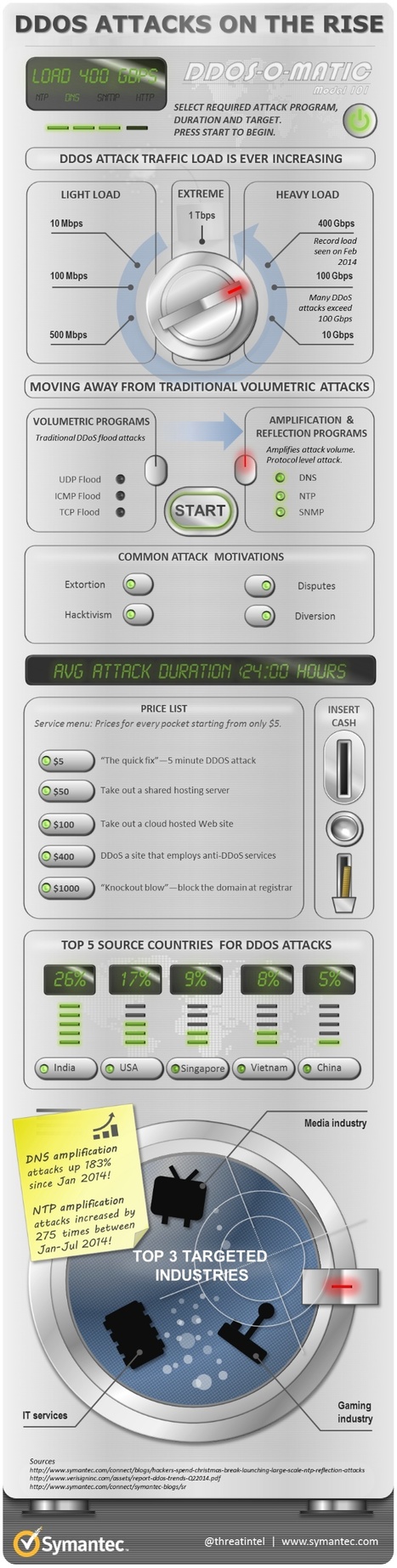
DOS ATTACKS ON THE RISE | Cyber Security | Infographic
Dubbed “AirHopper” by the researchers at Cyber Security Labs at Ben Gurion University, the proof-of-concept technique allows hackers and spies to surreptitiously siphon passwords and other data from an infected computer using radio signals generated and transmitted by the computer and received by a mobile phone. The research was conducted by Mordechai Guri, Gabi Kedma, Assaf Kachlon, and overseen by their advisor Yuval Elovici.
The attack borrows in part from previous research showing how radio signals (.pdf) can be generated by a computer’s video card (.pdf). The researchers in Israel have developed malware that exploits this vulnerability by generating radio signals that can transmit modulated data that is then received and decoded by the FM radio receiver built into mobile phones. FM receivers come installed in many mobile phones as an emergency backup, in part, for receiving radio transmissions when the internet and cell networks are down. Using this function, however, attackers can turn a ubiquitous and seemingly innocuous device into an ingenious spy tool. Though a company or agency may think it has protected its air-gapped network by detaching it from the outside world, the mobile phones on employee desktops and in their pockets still provide attackers with a vector to reach classified and other sensitive data.
Via Gust MEES
|
The Internet has by and large been a cause for good, driving economic growth across developed and emerging economies, connecting individuals and communities to previously unattainable services, and propelling innovation online, as well as offline. Today, all over the world public utilities, banks, and governments use the Internet, cloud services, and mobile technology to enhance their productivity. Unfortunately, the benefits of greater connectivity have also brought about increased information
Via Gust MEES
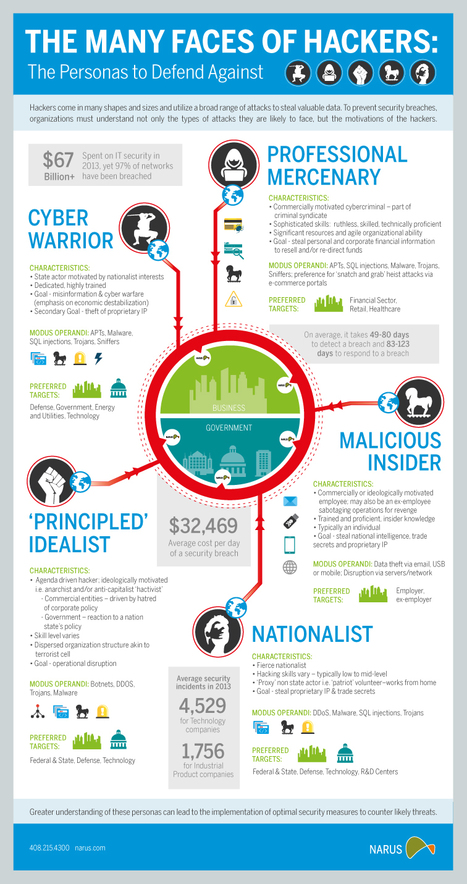
How many of these hacker personas are you dueling with in your organization?
Via Gust MEES, Next Level
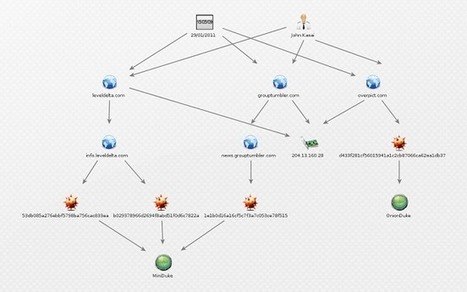
Recently, research was published identifying a Tor exit node, located in Russia, that was consistently and maliciously modifying any uncompressed Windows executables downloaded through it. Naturally this piqued our interest, so we decided to peer down the rabbit hole. Suffice to say, the hole was a lot deeper than we expected! In fact, it went all the way back to the notorious Russian APT family MiniDuke, known to have been used in targeted attacks against NATO and European government agencies.
The malware used in this case is, however, not a version of MiniDuke. It is instead a separate, distinct family of malware that we have since taken to calling OnionDuke.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR
Via Gust MEES
L’ENISA fête cette année ses 10 ans au service de la cyber-sécurité. C’était également l’occasion d’ouvrir le Mois européen de la cyber-sécurité.
Impliquer le citoyen était au cœur du débat mené par François Thill, responsable CASES, membre du conseil d’administration de l’ENISA et coordinateur des activités ECSM pour le Luxembourg.
Le Luxembourg est l’un des pays pilotes en Europe quant à la sensibilisation grand public aux bonnes pratiques des technologies de l’information. Les initiatives telles que CASES, CIRCL et BEE SECURE ont commencé à émerger au Grand-Duché il y a une bonne dizaine d’années déjà. Elles sont aujourd’hui coordonnées par « Security made in Lëtzebuerg » (SMILE), le groupement d'intérêt économique qui a été mandaté en 2010 par le ministère de l'Economie pour renforcer la sécurité de l'information au Grand-Duché de Luxembourg. CASES, CIRCL et BEE SECURE ont pour mission de développer le niveau de savoir-faire de la population en matière d’Internet, en démocratisant les informations, les méthodes et les connaissances existantes. Leur objectif ultime est de faire bénéficier les utilisateurs des opportunités que livre l’Internet dans un climat de confiance et de résilience par rapport aux risques.
Via Gust MEES
F-Secure Security Labs brings you the latest online security news from around the world. Ensure that you are up-to-date with the latest online threats to guarantee your online wellbeing.
Via Gust MEES
I've been asked a lot of times, especially when I was working for an antivirus producer, why can't we simply write a software that always protects the users. Well, there is a short answer and a long answer. Short answer: Because 100% security does not exist and because most people are hackable due to being ignorant on what security is (of course, until he/she is hacked first time, and sometimes not even after such an event). Long answer, which I massively shortened by not touching all areas and not going into details: The reason is the ignorance about everything that might happen but it is not certain that it will happen. I mean, would anyone close an insurance if it would have not been required by law or be afraid of the consequences? By the way, you can use this article to convince your C-level people to pay for that expensive cyber security training for the entire company.
According to Webster.com, the definition of IGNORANCE is: - a lack of knowledge, understanding, or education : the state of being ignorant [noncount] ignorance is bliss — used to say that a person who does not know about a problem does not...
Learn more:
- http://gustmees.wordpress.com/2012/11/05/naivety-in-the-digital-age/
Via Gust MEES
|



 Your new post is loading...
Your new post is loading...





















![H1 2014 Threat Report - F-Secure [Infographic] | E-Learning-Inclusivo (Mashup) | Scoop.it](https://img.scoop.it/3WKggSg7n-Fjl4tKZAeUKDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)







Successfully hiding messages in images has already been done, but is it possible to deliver an exploit in one - and run it?
Saumil Shah, founder and CEO of Net-Square, has demonstrated at the Hack in the Box Amsterdam 2015 that it's possible, and has posited that such attacks are more than likely to crop up in the near future, as he can't be the only one who thought about this, tried it and succeeded.
He is not the first one to try and hide exploits in images. But he created Stegosploit, a technology that lets attackers deliver executable JavaScript code via images, and trigger them, too.
The technology opens the door for attacks executed as simply as pointing users to sites containing a booby-trapped image or delivering the image via email. By virtue of simply viewing the image, the exploit code is triggered and can deliver malware on the victim's computer.
"A single file can be rendered as a perfectly valid HTML file, executed as a perfectly valid Javascript file, and displayed as a perfectly valid image, all at the same time," he explains.
"Stegosploit is the result of malicious exploit code hidden within pixels of the image carrying it. The image however, is a multi format container, which also contains the code required to decode the steganographically encoded pixels to execute the exploit."
This type of attack won't show in network traffic, he pointed out, be invisible to the naked eye, and the image will "autorun" in the browser.
In order to make the attack payload look harmless and not trigger defenses, Shah split it into two: dangerous pixel data (exploit code), and a safe decoder.