LAS VEGAS, Symantec Vision 2013 – April 16, 2013
Symantec Corp.’s (Nasdaq: SYMC) Internet Security Threat Report, Volume 18 (ISTR) today revealed a 42 percent surge during 2012 in targeted attacks compared to the prior year.
Designed to steal intellectual property, these targeted cyberespionage attacks are increasingly hitting the manufacturing sector as well as small businesses, which are the target of 31 percent of these attacks.
Small businesses are attractive targets themselves and a way in to ultimately reach larger companies via “watering hole” techniques.
===> In addition, consumers remain vulnerable to ransomware and mobile threats, particularly on the Android platform. <===



 Your new post is loading...
Your new post is loading...




![7 Cybersecurity Myths Busted [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/B-jkKo7ABgUaxD2BjEN8YDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



![Survey: Despite Security Incidents, BYOD Worth The Risks [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/AmjfVVh3JSRFrcTVEXBUozl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
![Small Businesses are the Path of Least Resistance for Attackers [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/NjtO2WpXNJHqSh0vQPJH4zl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
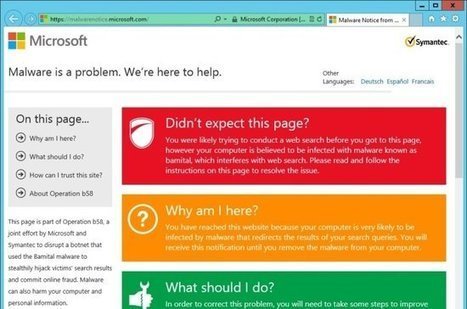






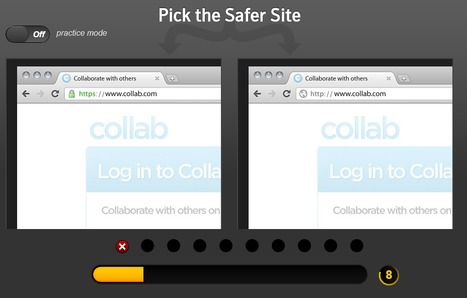
Can you tell the difference between a real site and a fake one?
Do you know how to stay safe online?
See how fast you can recognize the safe site and click on its picture. Learn what to look for when you browse, bank, or shop.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Phishing