Deutsche PC-Nutzer sind ein beliebtes Ziel von Botnetz-Betreibern. Haben Sie wirklich noch die Kontrolle über Ihren PC?
Botnetze werden oft über zentrale Kommando-Server, auch als Mutterschiffe bezeichnet, gesteuert. Die infizierten Rechner, Zombies genannt, halten Kontakt mit einem der Mutterschiffe oder untereinander. Sie geben ausgespähte Daten wie etwa Passwörter für Online-Spiele und Banken-Websites, aber auch gesammelte Mail-Adressen oder Kreditkartendaten weiter. Sie erhalten vom Mutterschiff, teils über zwischen geschaltete Relay-Rechner (Repeater), Instruktionen, etwa Adressen und Inhalte von zu versendenden Spam-Mails.
Learn more / Mehr erfahren:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Botnet
- https://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/



 Your new post is loading...
Your new post is loading...

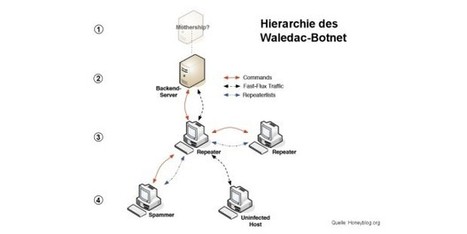

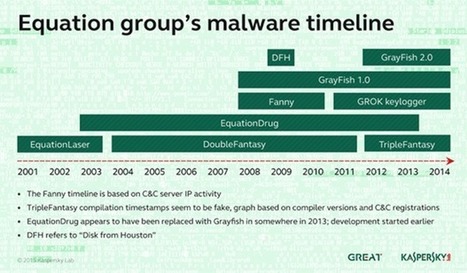
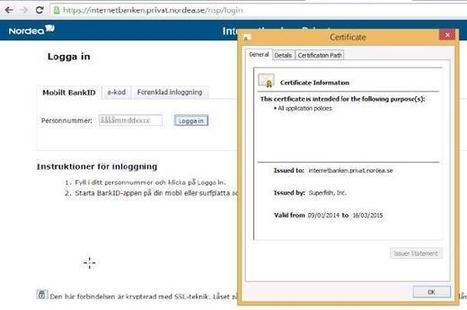










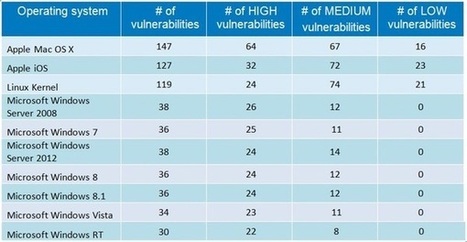















Botnetze werden oft über zentrale Kommando-Server, auch als Mutterschiffe bezeichnet, gesteuert. Die infizierten Rechner, Zombies genannt, halten Kontakt mit einem der Mutterschiffe oder untereinander. Sie geben ausgespähte Daten wie etwa Passwörter für Online-Spiele und Banken-Websites, aber auch gesammelte Mail-Adressen oder Kreditkartendaten weiter. Sie erhalten vom Mutterschiff, teils über zwischen geschaltete Relay-Rechner (Repeater), Instruktionen, etwa Adressen und Inhalte von zu versendenden Spam-Mails.
Learn more / Mehr erfahren:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Botnet
- https://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
- https://gustmees.wordpress.com/2012/11/29/cyber-hygiene-ict-hygiene-for-population-education-and-business/