Vulnerabilities in routers are an easy target for hackers - and attacks are becoming more destructive.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account


|
Security & the Internet of Things: IoT, OT, IIoT
Curated by Judy Curtis / SIPR |
 Your new post is loading...
Your new post is loading...

|
Scooped by
Judy Curtis / SIPR
December 11, 2018 5:46 PM
|
Yes, everything is connected. Great article from Andrew Orlowski in the Register about the December 6 #O2 outage, sparked by an expired software certificate... (shall we call this a "man in the muddle" attack? )
Orlowski writes:
"...While the "Spook Industrial Complex" frets about cybersecurity - rightly, of course, for that's what we pay it to do - it draws attention away from the everyday bugs and bungles that cause the outages that inconvenience millions of people. One is hypothetical, but one is real and an increasingly regular occurrence. And this applies across our national infrastructure. I wonder how much end of life kit is open to years-old vulnerabilities? Or how many routers have 123 as a password? More than you think..."

|
Scooped by
Judy Curtis / SIPR
November 27, 2018 10:34 PM
|
Scalpers use bots to buy out all the best gifts and resell them at much higher prices.
Democratic lawmakers want to shut down shopping bots beloved by scalpers...The proposed "Stopping Grinch Bots Act" would make it illegal to use bots to shop online and also outlaw reselling items purchased by bots.
Lawmakers label them "Grinch" bots because, during the holiday season, resellers use them to buy inventory of highly coveted toys that can be resold at highly inflated prices. These bots are so quick that they can purchase entire stocks of items before people can even add them to their carts.

|
Scooped by
Judy Curtis / SIPR
November 20, 2018 10:32 AM
|
Cyber criminals continue to reshape the threat landscape with updated tactics and escalating attacks.
Corey Nachreiner, Chief Technology Officer at WatchGuard Technologies, warns that the internet itself is vulnerable for takeover by anyone with the resources to DDoS multiple critical points, or to attack the underlying protocols. Eight grim predictions for 2019 include holding large popular websites hostage. The solution? Multi-factor authentication must play a part...

|
Scooped by
Judy Curtis / SIPR
November 6, 2018 4:54 PM
|
California becomes the first state to sign an IoT security law. Signed in September 2018, SB 327 will go into effect on the first day of 2020.
California's new law, SB 327, will go into effect on January 1, 2020 and mandates that any maker of an Internet-connected device must equip it with security features that "protect the device and any information contained therein from unauthorized access, destruction, use, modification, or disclosure."

|
Scooped by
Judy Curtis / SIPR
June 28, 2018 12:24 PM
|
Concerns about IoT and IoT security may seem far-fetched, but the reality is that IoT attacks are happening right now all over the place.
Survey data from IDC found 46 percent of organizations claim to have experienced a breach or security incident associated with IoT.

|
Scooped by
Judy Curtis / SIPR
June 27, 2018 1:45 PM
|
Industrial IoT in the enterprise expands the threat landscape by opening up new vulnerabilities that can be exploited across endpoints, applications, cloud infrastructure and networks.
The benefits of an increasingly connected enterprise are clear, but so are the risks. CISOs spend time and money on data protection strategies, but now its time to ensure they have a robust industrial IoT strategy that matches the investment being made on the business efficiencies these systems can introduce. While protecting data is absolutely critical, it’s equally important that all CISOs think about how to protect industrial infrastructures.

|
Scooped by
Judy Curtis / SIPR
June 27, 2018 11:45 AM
|
Learn the basics of cryptography for IoT: Start with private key authentication, and get signed firmware and secure boot.
Modern cryptography, such as ForceShield's dynamic transformation technology, can help make the IoT a safer, more reliable place.

|
Scooped by
Judy Curtis / SIPR
June 26, 2018 12:34 PM
|
A new whitepaper released by Fairhair Alliance states that organisations must deal with online security risks in a common IP-based infrastructure.
There are significant risks for systems that are always connected and remotely accessible via public Internet. Security architecture should work by specifying device-, network- and application-level protections for systems operating in an open, IP-based environment.

|
Scooped by
Judy Curtis / SIPR
June 26, 2018 12:27 PM
|
Two of the hottest technology trends today are the rise in Internet of Things (IoT) and blockchain adoption. A recent report by the Cloud Security Alliance (CSA) brings these two areas together—in a potentially good way.
“Organizations on the forefront of implementing IoT are understandably encountering challenges in identifying appropriate security technologies that are capable of mitigating the unique threats that IoT presents,” noted Brian Russell, chair of the CSA IoT Working Group.

|
Scooped by
Judy Curtis / SIPR
June 22, 2018 10:25 AM
|
The Internet of Things bears little resemblance to traditional IT systems—and that makes it harder to protect

|
Scooped by
Judy Curtis / SIPR
June 20, 2018 11:29 AM
|
When designing networks and deploying gear for the Industrial Internet of Things, it's important to bring in members of operational technology teams to make sure business goals are met.
According to 451 Research IoT practice director Christian Renaud, approaching IIoT from the operational side – via what he calls “the OT door” as opposed to the IT door – is a much more intelligent way to think about implementation.

|
Scooped by
Judy Curtis / SIPR
June 20, 2018 10:42 AM
|
Toward IIoT Security Standards: What the industrial IoT would look like if it was mature, secure and reliable.
Preventing a breach isn’t a high enough bar to set for a security model that defines maturity. Because the IIoT involves both operational technology and information technology, any maturity model has to include elements of both.

|
Scooped by
Judy Curtis / SIPR
June 18, 2018 5:17 PM
|
The time has come to create an intergovernmental organization whose objective is to deal with cybersecurity, says Northern.tech's Thomas Ryd. World Cybersecurity Organization, where art thou?
The world’s largest economies realize the need for stronger measurements for cybersecurity. The dilemma for the EU and U.S. is that they prefer the industry to come up with a solution. But as industry is failing at this, these nations are now faced with the challenge of how to impose stricter controls without negatively impacting the competition. China can and will continue to operate in its own protectionist way, seeking to knock two birds with one stone.
However, these three economic bastions face the same cybersecurity threat. They all have a common enemy in adversaries seeking to exploit digital vulnerabilities for economic and sometime dogmatic gain. The speed of bits and knowledge travel fast, and no borders can stop them. Adversaries on the world stage probably don’t care if it is the EU, U.S. or China they hurt, or whether they are paid in bitcoins or U.S. dollars.
The time has come to discuss a new international organization to take on cybersecurity. World Cybersecurity Organization where art thou?

|
Scooped by
Judy Curtis / SIPR
June 15, 2018 9:14 AM
|
Malware tied to Russia can attack connected computers and downgrade HTTPS.
what can you do to protect your devices from getting VPNFilter, or any other malicious software? 1) Don't expose administrative interfaces or services to the Internet. Just don't. It's really hard for security professionals to do this, meaning it's basically impossible for regular users. So don't enable remote administration of your router, and don't share your NAS with the Internet. 2) Keep it up to date. Vendors fix vulnerabilities, but that doesn't help you if you don't patch them.

|
Scooped by
Judy Curtis / SIPR
June 8, 2018 10:56 AM
|
Cybersecurity in the internet of things era draws on the same security technologies and best practices that have proven effective for years, giving CISOs a vintage roadmap for IoT security concerns as the number of connected devices multiplies.
The internet of things has drastically expanded the size and scope of what security teams need to protect, adding IoT security concerns to CISOs' responsibilities.
"It's meshing business knowledge with the technical knowledge to develop your risk framework and validate that the security measures you have will work with the operational requirements for IoT initiatives," said Barika L. Pace, a Gartner research director focused on IoT strategy.

|
Scooped by
Judy Curtis / SIPR
June 7, 2018 11:27 AM
|
The Industrial Internet of Things (IIoT or Industrial IoT) explained: place in Industry 4.0 and Industrial Internet, IIoT use cases, benefits & challenges
Security first
While the business outcomes and partnerships with key stakeholders and others are obviously essential, security is at least as important.
Look at security from an end-to-end perspective as there are so many components involved: from connectivity to devices and connected applications. Security by design and embedded security are a must. And as in all transformational projects, involve security early on.

|
Scooped by
Judy Curtis / SIPR
June 6, 2018 12:04 PM
|
A new Bain & Company report says security concerns are slowing IoT adoption. Is this problem fixable — and what if it isn’t?
Publication of a new Bain & Company report, Cybersecurity Is the Key to Unlocking Demand in IoT.
According to the consulting firm’s survey, 45 percent of Internet of Things (IoT) buyers say “concerns about security remain a significant barrier and are hindering the adoption of IoT devices.”

|
Scooped by
Judy Curtis / SIPR
May 31, 2018 2:43 PM
|
Stopping DDoS attacks is not a matter of improving security of IoT devices. Enterprises need to take responsibility and be better at identifying and preventing DDoS attacks as they happen in real time.
Stopping DDoS attacks is not just a matter of improving security of IoT devices. Enterprises need to take responsibility and be better at identifying and preventing DDoS attacks as they happen in real time.

|
Scooped by
Judy Curtis / SIPR
May 30, 2018 11:43 AM
|
Researchers discovered the Wicked botnet, which is a Mirai variant that uses multiple exploits to target vulnerable IoT devices, including Netgear routers and CCTV video cameras.
The Wicked botnet scans ports 8080, 8443, 80 and 81and it will try to exploit the device once a connection is established. The exploits used depend on which port the botnet connects to for specific devices.
Targeted devices include flawed Netgear routers -- some of which were also used by the Reaper botnet -- and closed-circuit video cameras that have a remote code execution flaw. One exploit doesn't target a device, but instead targets compromised web servers with malicious invoker shells that are already installed.

|
Scooped by
Judy Curtis / SIPR
May 27, 2018 2:07 PM
|
Hundreds of thousands of home and office routers have been infected by the malware, which was created by the same group that hacked the Democratic National Committee.
The F.B.I. has several recommendations for any owner of a small office or home office router. The simplest thing to do is reboot the device, which will temporarily disrupt the malware if it is present. Users are also advised to upgrade the devices’ firmware and to select a new secure password. If any remote-management settings are in place, the F.B.I. suggests disabling them.
An analysis by Talos, the threat intelligence division for the tech giant Cisco, estimated that at least 500,000 routers in at least 54 countries had been infected by the malware, which the F.B.I. and cybersecurity researchers are calling VPNFilter.

|
Scooped by
Judy Curtis / SIPR
May 25, 2018 10:11 AM
|
The FBI operation targets a piece of sophisticated malware linked to the same Russian hacking group that hit the Democratic National Committee in 2016.
FBI agents armed with a court order have seized control of a key server in the Kremlin’s global botnet of 500,000 hacked routers. One plug-in lets the hackers eavesdrop on the victim’s Internet traffic; another targets a protocol used in the electric grid. A third lets the attacker cripple any or all of the infected devices at will.

|
Scooped by
Judy Curtis / SIPR
May 23, 2018 11:53 AM
|
What exactly is a DDoS attack and should you be worried?
Denial of Service attacks are costly and disruptive, yet cheap to produce. Kaspersky Labs reckons the average cost to an organization is $106,000 (£85,000) if you take everything from detection through to mitigation and customer churn into account. For the attacker it's less expensive, with DDoS-for-hire services ranging from $5 (£4) for a few minutes to $500 (£400) for a working day.

|
Scooped by
Judy Curtis / SIPR
May 10, 2018 11:05 AM
|
A botnet has been discovered by security researchers which is expected to be the first to survive resets of compromised devices.
To resist IoT botnet attacks, ForceShield recommends changing the IoT device's default credentials, using strong passwords, restricting remote management functions, and making sure the IoT device's software is up to date. But device manufacturers, OEM, system integrators can secure IoT devices by design, by building in security functions that scramble the attack at the point of penetration (incorporating ForceShield's DeviceShield embedded software with the device firmware).

|
Scooped by
Judy Curtis / SIPR
May 8, 2018 12:20 PM
|
On the manufacturer side, many devices run lightweight Linux-based operating systems that open doors for hackers. Consumers who expect IoT devices to act like user-friendly ‘plug-and-play’ conveniences may have sufficient intuition to use the device but insufficient technical knowledge to protect or update it.
Krebs says: "In short, dumb IoT devices are those that don’t make it easy for owners to use them safely without being a nuisance or harm to themselves or others."












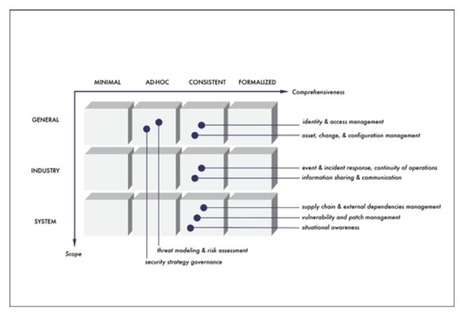


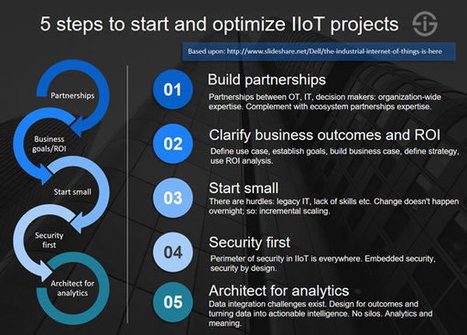












This is still happening everywhere. Meanwhile, In the U.S., the FBI recommends that users change default usernames and passwords, ensure patches are applied when issued and if necessary, to keep connected devices on a segmented network.