The Federal Trade Commission (FTC) is aware we live in a connected world. Americans wear Fitbits, have Nest thermostats, use automated light systems from companies like Belkin and Philips, even have televisions that predict what they want to watch. But in a new report, the FTC has a warning: Existing privacy regulations don’t really cover the Internet of Things, and the Commission doesn’t really trust device manufacturers to do the right thing—or even be aware of the risks of collecting all that data.
In a staff report issued this week, the FTC warned that makers of connected health, home, and transportation devices could potentially leave their users vulnerable to data hacks. Most of all, the FTC is concerned that private information will be used to jack up users' insurance rates or deny them access to loans.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=wearables
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
Via Gust MEES



 Your new post is loading...
Your new post is loading...







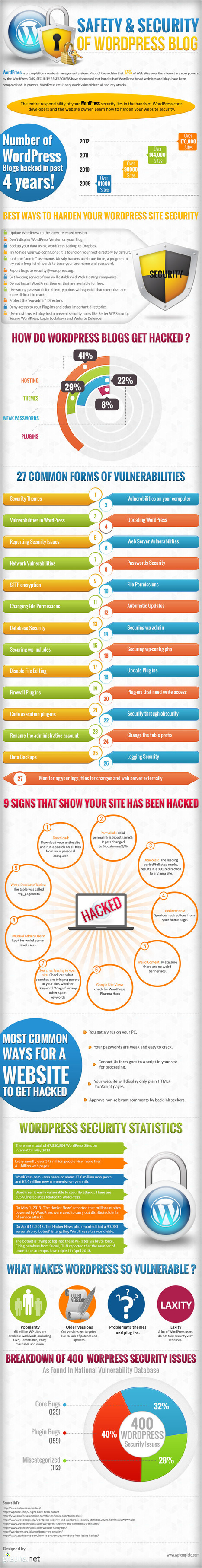

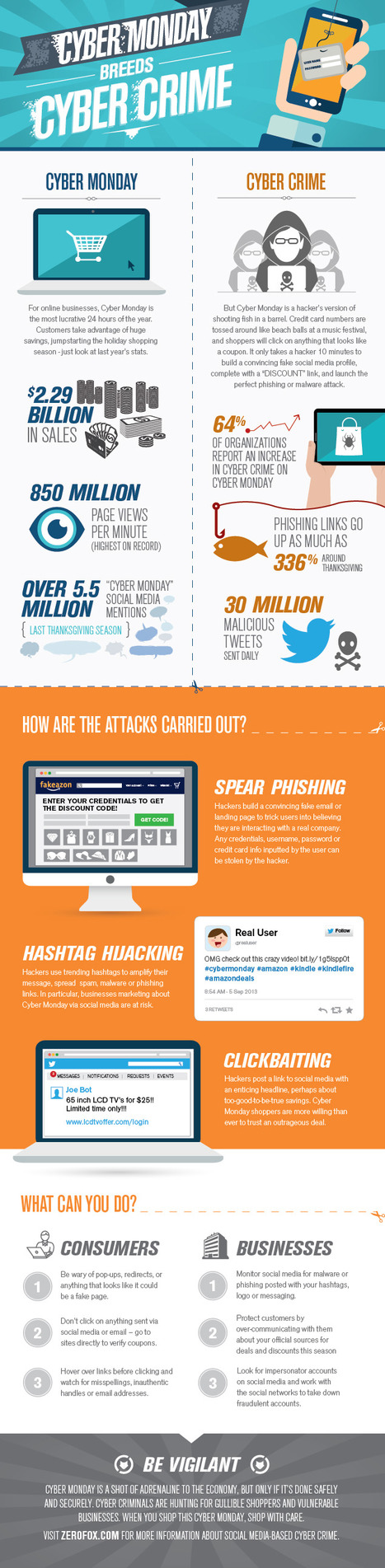

![Digital Attacks! Protect Yourself Against Cyber Threats [Infographic] | Daily Magazine | Scoop.it](https://img.scoop.it/B7yQuqAc8MxFKtFlLhEWMTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)






Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=wearables
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
- http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/
उत्तर प्रदेश और किसान :
उत्तर प्रदेश राज्य के लिए राजनितिक सर्वे मे हमने पाया है कि अब तक उत्तर
प्रदेश में ज्यादा विकास नही हो पाया है| जैसे: कृषि,शिक्षा,उधोग आदि क्षैत्र में|
यह राज्य कृषि उत्पादन मे भारत मे सर्व श्रेठ है| यहाँ की भूमि बहुँत उपजाऊ है
जिससे हमे बहुँत फसल प्राप्त होती है जैसे गैहू, धान ,सरसो ,दाले आदि| जिनहे
हम विदेश में निर्यात करे तो अच्छा धन कमा सकते हैं पर इस राज्य में शासन
करने वाले इसे कम कीमत पर खरीद कर अच्छी कीमत पर बेच देते है | लाभ
राशि यहाँ के लोग नही बल्कि यहाँ की भ्रष्ट सरकार की साहयता से पूंजीपति उठा
लेते है
जिस्से किसान अच्छी कीमत नही कमा पाते है और किसान आर्थिक रूप से ग्रस्त
होते जा रहे है
उत्तर प्रदेश की इन सभी कमियो को मध्यनजर रखते हुए भारतीय जनता पार्टी
विकास के लिए कुछ जरूरी कदम उठाएगी |
1. सभी किसानो के लिए कृषि धन योजना खाते खोले जाएँगे | जिससे वह
गन्ना अदि फसल का भुगतान अपने खाते में पा सकते है |
2. किसानो के लिए लोन की सुविधा कम दर पर रखी जाएंगी | जिस्से वह
ज्यादा समय में आसानी से चुका सके |
3. फसल के बारे मे शिक्षा प्रदान करने के लिए कृषि विशेषज्ञयो को भेजा जाय
जाएंगा |
4. शिक्षा का स्तर बाल व बालिकाओ का निगमन साक्षरता की ओर होगा
जिस्मे नए प्राइमरी व इंटर तक के स्कूल खोले जायंगे |
5. सभी व्यावसायिक को व्यवसाय प्रदान किये जायंगे वो भी एक अच्छी प्रति
दिन कीमत पर |
6. उत्तर प्रदेश वासियों को कम यूनिट दर पर बिजली परदान की जाएगी |
संजय सिंह जी को भारतीय जनता पार्टी दुआर जेवर छेत्र के लिए चुने गये है
जो इस छेत्र मे काफी सुधार करने के इच्छुक है |
1. किसानो का गन्ना तथा आदि कृषि सम्बन्धी मुद्दा सुलझेंगे |
2. किसानो को आर्थिक सहायताए देंगे |
3. जेवर में सड़क सम्बन्धि तथा आदि कार्य कराएंगे |