The Canadian government is continuing their experiments with blockchain to see how the new technology can further help the country. The federal government announced that it will pioneer the testing of the Known Traveller Digital Identity system, a new concept that helps to improve the security and flow of travellers across borders. This new program uses biometrics, cryptography and distributed ledger technology to give travellers more control over how and when they share their information with authorities. This can lead to expedited clearance and build more trust and transparency between travellers and authorities as they look to improve risk detection.
Via Farid Mheir

 Your new post is loading...
Your new post is loading...

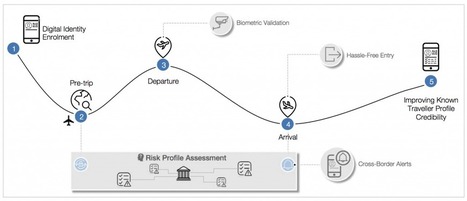














WHY IT MATTERS: article that explains why and how the blockchain technology will be used to facilitate border crossing in Canada. Yé!