 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
July 7, 2015 4:00 PM
|

|
Scooped by
Gust MEES
July 7, 2015 9:51 AM
|
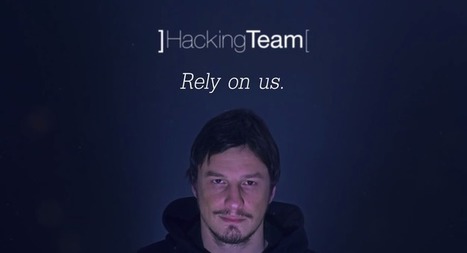
Hacking Team has been hacked and its social media account hijacked, the news is shocking the IT security industry because privacy advocated have always accused the company to sell surveillance products and hacking tools to repressive regimes. The unknown attackers have exfiltrated some 400Gbs of data that have been uploaded to BitTorrent, the stolen information includes a huge number of directories containing source code, emails, list of clients (including the FBI), and also audio recordings.
The Hacking Team restored the control of its Twitter account late on Monday morning, meanwhile the website is offline at the time I’m writing.
Mehr erfahren / Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Hacking+Team+breach

|
Scooped by
Gust MEES
July 6, 2015 10:30 AM
|
Over the weekend, hackers who remain unnamed posted a .torrent file linking to over 400GB of company data belonging to Hacking Team. The file, which contains emails, client lists, revenue reports, client history and marketing materials -- just to name some of the most interesting aspects -- appears to show Hacking Team has a healthy client list worldwide.
According to the data -- which has not been independently verified at the time of writing -- Hacking Team counts customers in countries including Italy, the US, Spain, Singapore, Malaysia, Saudi Arabia, Mexico, Luxembourg, Egypt, Oman, Panama, Turkey, the UAE, Nigeria, Ethiopia, Poland, Thailand, Denmark and Israel, among others.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Hacking+Team+breach

|
Scooped by
Gust MEES
July 5, 2015 5:50 AM
|
Revelations from WikiLeaks published this week show how boundlessly and comprehensively American intelligence services spied on the German government. It has now emerged that the US also conducted surveillance against SPIEGEL.
Mehr erfahren / En savoir plus / Learn more: - http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberespionage

|
Scooped by
Gust MEES
June 25, 2015 9:27 AM
|
Facebook baut sein Portfolio an Entfernungstools für Viren aus und verkündet einen Erfolg: Im vergangenen Quartal habe man zwei Millionen mit Malware befallene Computer erkannt und bereinigt.
Facebook verkündet einen Erfolg im Kampf gegen Malware: Dank verschiedener Sicherheitstools von Facebook habe man in den vergangenen drei Monaten über zwei Millionen mit Malware infizierte Computer erkannt und bereinigt.
Neben ESET, F-Secure und Trend Micro ist jetzt auch Kaspersky mit an Bord, die einen weiteren Malware-Scanner zur Verfügung stellen. Facebook will so noch effizienter kompromittierte Rechner, die zum sozialen Netzwerk Kontakt aufnehmen, erkennen und anschließend untersuchen beziehungsweise von Schädlingen befreien.

|
Scooped by
Gust MEES
June 23, 2015 6:39 PM
|
The U.S. Navy is paying Microsoft millions of dollars to keep up to 100,000 computers afloat because it has yet to transition away from Windows XP.

|
Scooped by
Gust MEES
June 23, 2015 3:14 PM
|
Die kampfstarke US-Marine setzt nach wie vor auf Windows XP. Und zahlt dafür extra einige Millionen Dollar an Microsoft.
Erst kürzlich machte die Meldung die Runde, dass deutsche Behörden wie die Verwaltung von Berlin noch auf Windows XP setzen. Und mit der Benutzung des von Microsoft nicht mehr unterstützten Betriebssystems entweder gravierende Sicherheitslücken in Kauf nehmen oder aber Riesensumme für Extra-Support an Microsoft bezahlen.
Doch dieser Sonderweg einiger deutscher Bundesbehörden ist noch nichts gegen die Kriegsmarine der Vereinigten Staaten von Amerika, die sogar über U-Boote mit Atomwaffen verfügt. Denn auch die US-Marine setzt immer noch Computer mit Windows XP ein.

|
Scooped by
Gust MEES
June 23, 2015 9:46 AM
|
Newly-published documents from the Snowden trove show GCHQ asking for and obtaining special permission to infringe on the copyright of software programs that it wished to reverse-engineer for the purpose of compromising them. GCHQ wanted a warrant that would give it indemnity against legal action from the companies owning the software in the unlikely event that they ever found out.
The legal justification for this permission is dubious. As the new report in The Intercept explains: "GCHQ obtained its warrant under section 5 of the 1994 Intelligence Services Act [ISA], which covers interference with property and 'wireless telegraphy' by the Security Service (MI5), Secret Intelligence Service (MI6) and GCHQ." Significantly, Section 5 of the ISA does not mention interference in abstractions like copyright, but in 2005 the intelligence services commissioner approved the activity anyway.
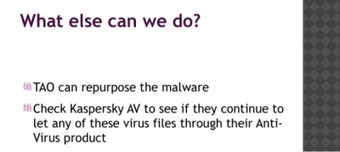
The Intercept story provides details of the software that GCHQ wanted to compromise: online bulletin board systems, commercial encryption software, and anti-virus programs. It needed to prevent the last of these from revealing the presence of other GCHQ malware that was used for spying: "Personal security products such as the Russian anti-virus software Kaspersky continue to pose a challenge to GCHQ’s CNE [computer network exploitation] capability and SRE [software reverse engineering] is essential in order to be able to exploit such software and to prevent detection of our activities."
Learn more / En savoir plus / Mehr erfahren:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberespionage

|
Scooped by
Gust MEES
June 22, 2015 7:17 PM
|
Die Geheimdienste wollen erfahren, wie sie beim Angriff auf Rechner den Virenschutz umgehen können. Auch der deutsche Hersteller Avira wurde offenbar bespitzelt.
Fast zwei Wochen nachdem bekannt wurde, dass Anti-Viren-Hersteller Kaspersky Ziel eines Hackerangriffs geworden war, scheint jetzt wahrscheinlich, dass die NSA und ihr britisches Gegenstück GCHQ dahinter steckten. Auch war der Angriff wohl kein Einzelfall, wie die Snowden-Dokumente nahelegen. Konkurrenten von Kaspersky wie Avast, AVG, Eset, F-Secure und der deutsche Hersteller Avira sollen ebenfalls ausspioniert worden sein.
Dabei ging es den Geheimdiensten wohl gezielt darum, zu erfahren, wie der Virenschutz der einzelnen Hersteller beim Angriff auf Zielrechner umgangen werden kann.
Learn more / En savoir plus / Mehr erfahren:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberespionage

|
Scooped by
Gust MEES
June 18, 2015 8:40 AM
|
Digital Constitution - a dedicated website Microsoft set up to keep users informed of its efforts to counter US government's attempts to access customer emails the company stores in its data center located in Dublin, Ireland - has been compromised.
Unexpectedly, the attackers are not disgruntled privacy-minded hacktivists with a bone to pick with the company, but apparently scammers trying to push "amazing" offers from online casinos.
The site's code was apparently modified to include gambling-themed keywords so that it pops up in online gambling-related searches, and new pages like this one (which is still available as I write this) have been created on the site:
ZDNet's Zack Whittaker posits that the compromise was executed by leveraging vulnerabilities in the WordPress CMS used to run the site.
The site is running on WordPress 4.0.5, while the latest version is 4.2.2.

|
Scooped by
Gust MEES
June 14, 2015 9:01 AM
|
Hackers linked to China appear to have stolen security-clearance records with sensitive data about millions of American military and intelligence personnel.
What’s particularly stunning about this development is how quickly it grew into something so severe. Last week, officials estimated that the personal data of 4 million current and former federal employees had been compromised. Then that figure ballooned to as many as 14 million.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack

|
Scooped by
Gust MEES
June 5, 2015 7:04 AM
|
The agency tasked with recruiting workers for the US government has fessed up to allowing the personal details of 4 million people to be stolen by hackers.
The US Office of Personnel Management (OPM) has sent out an alert to current and former government employees warning of the data breach.
"Beginning June 8 and continuing through June 19, OPM will be sending notifications to approximately 4 million individuals whose Personally Identifiable Information was potentially compromised in this incident," the OPM said.
The OPM alert does not disclose just what information was lost but said that it would provide credit monitoring and identity monitoring to all those who had their information swiped.

|
Scooped by
Gust MEES
May 29, 2015 3:39 PM
|
Entdeckt haben sie Wissenschaftler der Technischen Universität Darmstadt und Experten des Fraunhofer-Institut für Sichere Informationstechnologie SIT. Die Daten landeten dort – etwa in Facebooks Parse und Amazons AWS - weil App-Entwickler Authentifizierungen für Cloud Services falsch verwenden. Betroffen sind E-Mail-Adressen, Passwörter, Gesundheitsdaten und andere persönliche Informationen von App-Nutzern.
Wissenschaftler der Technischen Universität Darmstadt und das Fraunhofer-Institut für Sichere Informationstechnologie SIT haben mehrere Cloud-Datenbanken untersucht und dabei rund 56 Millionen ungeschützte Datensätze gefunden. Dazu gehören neben E-Mail-Adressen auch Passwörter, Gesundheitsdaten und andere persönliche Informationen. Den Experten zufolge sind dadurch viele Nutzerkonten durch Identitätsdiebstahl und andere Internetverbrechen bedroht.
|

|
Scooped by
Gust MEES
July 7, 2015 10:04 AM
|
A security researcher conducted an experiment to demonstrate that someone is sniffing passing traffic from Tor network exit nodes.
When talking about Tor network, normally everyone assumes that you have an end-to-end security, but someone believes it may be wrong as it was discovered by the security researcher Chloe.
Tor network is free and it is the safest way to be anonymous since it hides your original IP from the destination server, to do that Tor uses relays to redirect traffic, but now the security researcher Chloe concludes that traffic is being sniffed in the exit nodes.

|
Scooped by
Gust MEES
July 7, 2015 9:38 AM
|

|
Scooped by
Gust MEES
July 5, 2015 5:55 AM
|
Ein geheimer Vermerk aus dem Kanzleramt legt nahe, dass der SPIEGEL im Jahr 2011 ins Visier von US-Geheimdiensten geriet. Die Bundesregierung tat nichts, um den Fall aufzuklären - und verschwieg dem Parlament die Hintergründe.

|
Scooped by
Gust MEES
July 4, 2015 10:56 AM
|

|
Scooped by
Gust MEES
June 25, 2015 9:17 AM
|
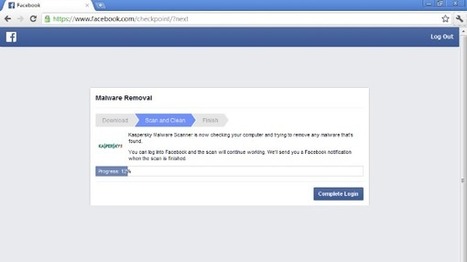
Symantec has issued a warning about a successful scam being perpetrated against users of webmail services such as Gmail, Outlook and Yahoo.
The scam is explained in the following short video made by Symantec.

|
Scooped by
Gust MEES
June 23, 2015 3:31 PM
|
Senior U.S. officials have said that the Chinese have begun in the last 12 to 18 months to build vast databases of Americans’ personal information for counterintelligence purposes. They have gone after such data contained not only in federal networks, but in systems belonging to health-insurance giants such as Anthem.
The breach details come as OPM leadership is under fire for its handling of a succession of network hacks over the last year and a half. The chairman of the House Oversight and Government Reform Committee, Rep. Jason Chaffetz (R-Utah), has called for the resignation of the agency’s director, Katherine Archuleta.
Under Archuleta, Wagner said, the agency in February 2014 began a program to identify vulnerabilities in the agency’s aging computer systems — some date to 1985 — and to modernize the network.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack

|
Scooped by
Gust MEES
June 23, 2015 10:49 AM
|
Viele Nutzer wissen aber laut Avast nicht, dass Hola sie selbst zu einem Exit Node für andere Hola-User macht. Das heißt, wenn etwa jemand über Hola auf illegale Inhalte zugreift, dann ist er eventuell mit Ihrer IP-Adresse im Internet unterwegs. Strafverfolgungsbehörden würden dann zuerst bei Ihnen anklopfen.
Des Weiteren verweist Avast auf eine Analyse von Vectra Research, laut der die Hola-Erweiterung weitere Programme auf Ihrem PC installieren kann – ohne dass Sie es bemerken.
„Browser-Erweiterungen sehen alles, was Sie im Browser sehen, inklusive aller Eingaben und Passwörter“, warnt Thomas Salomon von Avast. „Nicht vertrauenswürdige Erweiterungen können diese Daten leicht missbrauchen. Sie sollten deswegen sehr vorsichtig dabei sein, welche Erweiterungen Sie installieren“, so Salomon weiter.
Der Sicherheitsexperte empfiehlt Avast Browser Cleanup, um den Browser zu bereinigen.
Mehr erfahren / Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=VPN

|
Scooped by
Gust MEES
June 23, 2015 9:16 AM
|
Edward Snowden, the former NSA contractor and whistleblower, has leaked documents that claim the US National Security Agency (NSA) and UK Government Communications Headquarters (GCHQ) have actively reverse engineered security and anti-virus software to obtain intelligence, according to a report by The Intercept.
The documents obtained reportedly highlight the Russian software security firm, Kaspersky Lab, as one of the main targets, with GCHQ reverse-engineering Kaspersky's anti-virus software looking for vulnerabilities that could be subverted.
The Intercept posted an NSA document titled "Project Camberdada" that lists at least 23 antivirus and security firms that were in that spy agency's sights -- none of the companies were of U.K. or U.S. origin, but there was more than one firm from the country in which Snowden now calls home.
Earlier this month, Eugene Kaspersky said in a blog post that his firm had recently discovered an advanced attack on its software. The security mogul said that his company was quite confident that there was a nation state behind the attack, but made it clear that he did not wish to attribute it.
Learn more / En savoir plus / Mehr erfahren:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberespionage

|
Scooped by
Gust MEES
June 22, 2015 9:33 AM
|
LOT Polish Airlines was forced to cancel 10 flights scheduled to depart from Warsaw’s Chopin airport on Sunday after hackers attacked its ground computer systems.
The IT attack, which was not described in detail, left the company unable to create flight plans for outbound flights, grounding around 1,400 passengers.
The company said that plane systems were not affected and aircraft that were already in the air were able to continue their flight or to land. The incident only affected the ability of planes to depart from the airport for several hours.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack

|
Scooped by
Gust MEES
June 14, 2015 10:18 AM
|
Beim Cyber-Angriff auf den Bundestag soll auch ein Rechner im Bundestagsbüro von Kanzlerin Angela Merkel (CDU) infiziert worden sein. Das berichtet die "Bild am Sonntag".
Der Rechner sei einer der ersten gewesen, bei dem der Trojaner festgestellt wurde. Ein Sprecher der Unionsfraktion sagte der Zeitung lediglich: "Ich kann das weder bestätigen noch dementieren." Auch zu der Frage, ob Daten von Merkels Rechner abgesaugt wurden, wollte sich dem Bericht zufolge niemand aus Merkels Umfeld äußern.
Die unbekannten Hacker hätten den Namen von Merkel auch für das Versenden von infizierten E-Mails benutzt. Bei Bundestagsabgeordneten sei vor einigen Tagen eine Mail im Postfach aufgetaucht, deren Absender sich "Angela Merkel" genannt habe. Im Betreff sei es um eine Einladung zu einer Telefonkonferenz gegangen, der Link dazu infiziert gewesen. Die Bundestagsverwaltung warne deshalb die Parlamentarier im Intranet davor, die Links in den falschen Merkel-Mails anzuklicken.
Laut "BamS" soll bis Freitagnachmittag bei insgesamt 15 Computern, die an das Bundestagsnetzwerk angeschlossen sind, der Trojaner festgestellt worden sein. Bei fünf Computern sei Datenabfluss nachgewiesen worden.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack

|
Scooped by
Gust MEES
June 11, 2015 8:43 PM
|
WASHINGTON (AP) — Hackers stole personnel data and Social Security numbers for every federal employee, a government worker union said Thursday, asserting that the cyber theft of U.S. employee information was more damaging than the Obama administration has acknowledged.
Sen. Harry Reid, the Democratic leader, said on the Senate floor that the December hack into Office of Personnel Management data was carried out by "the Chinese" without specifying whether he meant the Chinese government or individuals. Reid is one of eight lawmakers briefed on the most secret intelligence information. U.S. officials have declined to publicly blame China, which has denied involvement.
J. David Cox, president of the American Federation of Government Employees, said in a letter to OPM director Katherine Archuleta that based on the incomplete information the union received from OPM, "We believe that the Central Personnel Data File was the targeted database, and that the hackers are now in possession of all personnel data for every federal employee, every federal retiree, and up to one million former federal employees.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack

|
Scooped by
Gust MEES
June 2, 2015 3:51 AM
|
F-Secure's acquisition of nSense bolsters the company's expansion into the enterprise segment by offering businesses complete defensive solutions and services for modern threats. Helsinki, Finland - June 2, 2015: F-Secure announced today that it has acquired nSense - a privately held Danish company providing security consultations, vulnerability assessment services and related products to large enterprises. The acquisition strengthens F-Secure's position as a prominent security vendor in Europe, and lays a foundation for the company's growth as a cybersecurity leader in the region. nSense provides protection services to financial institutions, service providers and other large enterprises, and F-Secure's acquisition of the company will add these services to its own leading security solutions. According to F-Secure CEO Christian Fredrikson, the combined portfolio will allow F-Secure to provide top-tier incident response and forensic expertise, comprehensive vulnerability assessment, and threat intelligence and security management services to enterprises and businesses with critical IT infrastructure.
|



 Your new post is loading...
Your new post is loading...


















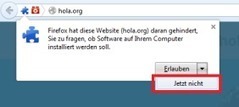










Mehr erfahren / Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Hacking+Team+breach