Flaws in Samsung Phones Allow Hackers to Make Calls, Install Apps and Change Settings
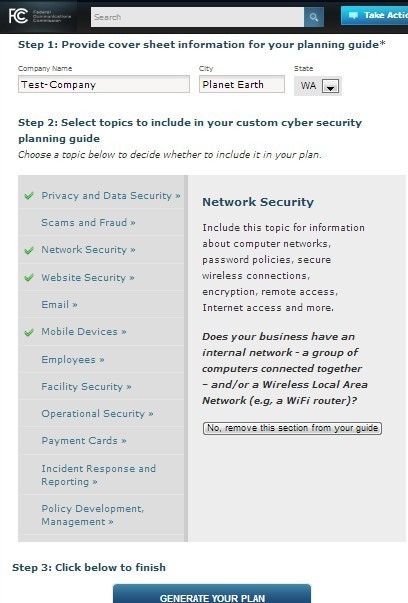
Two of the vulnerabilities can be leveraged to silently install highly privileged apps without requiring any user interaction. A different issue can be exploited by an attacker to send SMS messages without requiring the android.permission.SEND_SMS permission.
Another vulnerability can be used to silently make phone calls, send emails and SMSs, and perform “almost any action.”



 Your new post is loading...
Your new post is loading...

![Flaws in Samsung Phones Allow Hackers to Make Calls, Install Apps and Change Settings [Video] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/uDdxb_6-EHFa_IicUrmCETl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)












![Managing Mobile Privacy | Security Intelligence Blog [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/m8EBNAOuN5Zr7PdORj8fTDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



![Why You Should Care About Mobile Security [INFOGRAPHIC] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/bCDzCBQu4qMgWJAbygdm2jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
![Why You Should Care About Mobile Security [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/eCYKbrsHLFNXs4GayRTQ8zl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








Two of the vulnerabilities can be leveraged to silently install highly privileged apps without requiring any user interaction. A different issue can be exploited by an attacker to send SMS messages without requiring the android.permission.SEND_SMS permission.
Another vulnerability can be used to silently make phone calls, send emails and SMSs, and perform “almost any action.”