 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Das Tracking wird über die US-Firma Laserlike abgewickelt. Damit die Empfehlungen in der Seitenleiste auch passen, ist der umfangreiche Zugriff auf Daten, etwa den Browser-Verlauf und die aktuell geöffneten Seiten, nötig. Außerdem sammelt Laserlike IP-Adresse, Zugriffszeiten und Verweildauer auf Webseiten.
Im Rahmen von Test-Pilot tracken Laserlike und Mozilla noch Daten zur Nutzung von Advance, etwa Verweildauer auf empfohlenen Seiten oder Informationen zum Betriebssystem. Was man Mozilla zugute halten muss: Sie verschweigen das Thema Tracking nicht und bauen einen Schalter ein, um Advance pausieren zu lassen.
Auch im Privatmodus oder mit eingeschaltetem Tracking-Schutz funktioniert die Erweiterung nicht. Wer möchte, kann die übermittelten Daten einsehen und löschen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=tracking

|
Scooped by
Gust MEES
|
Public Wi-Fi is a great convenience that most of us – if not all of us – utilize regularly. There is little doubt, however, that using public Wi-Fi creates serious cybersecurity risks. At the same time, cybersecurity practitioners who preach that people should refrain from using public Wi-Fi are about as likely to succeed in their effort as someone telling people to abandon insecure computers and instead use un-hackable typewriters. As such, here are 9 suggestions as to how to use public Wi-Fi safely: Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/05/27/dangers-of-wifi-in-public-places/

|
Scooped by
Gust MEES
|
Opfer des Erpresser-Trojaners LockCrypt können aufatmen. Bitdefender ist es gelungen, eine der Ransomware-Varianten zu knacken. Das Tool steht ab sofort zum kostenlosen Download bereit.
Seit Mitte des vergangenes Jahres treibt die Ransomware LockCrypt ihr Unwesen. Die Malware schleicht sich auf fremden Rechnern ein, verschlüsselt dort wichtige Dateien und Dokumente und verlangt anschließend ein Lösegeld. Nach Angaben des Sicherheitsanbieters Bitdefender konzentrieren sich die Urheber von LockCrypt dabei weniger auf Privatanwender, sondern vor allem auf Unternehmen als Ziel. Zur Verbreitung nutzen sie meist Lücken im RDP-Protokoll (Remote Desktop Protocol).
Auch der Antiviren-Hersteller Eset hat sich immer wieder mit LockCrypt beschäftigt. Nach seinen Erkenntnissen verlangt der Erpresser-Trojaner in der Regel zwischen einem halben und einem ganzen Bitcoin für eine Wiederherstellung der verschlüsselten Daten und pro in einem Unternehmen betroffenem Server. Bei den in den vergangenen Monaten teilweise sehr hohen Bitcoin-Preisen kommen so schnell hohe Summen zusammen, die anfallen, wenn eine Wiederherstellung angestrebt wird. Laut Eset hat ein Unternehmen rund 19.000 US-Dollar gezahlt, um wieder an die Daten auf drei verseuchten Maschinen zu kommen.
Kostenloses Entschlüsselungs-Tool
Bitdefender stellt nun ein kostenloses Decryption-Tool zum Download bereit, mit dem sich zumindest bei einer LockCrypt-Variante die verschlüsselten Daten wiederherstellen lassen sollen. Nach Angaben des Anbieters funktioniert das Tool bei der LockCrypt-Version, die mit der Dateiendung „.1btc“ arbeitet. Andere Varianten wie „.lock“, „.2018“ und „.mich“ seien zwar ebenfalls entschlüsselbar, aber noch nicht in dem Tool enthalten. Opfer der LockCrypt-Variante, die die Dateiendung „.bi_d“ erzeugt, müssen ebenfalls weiter auf ein Entschlüsselungswerkzeug warten, da diese Version bislang noch nicht geknackt werden konnte.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/ict-security-tools/?&tag=Ransomware https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
Eine Nachlässigkeit beim Pairing erlaubt es Angreifer, sich in die Verbindung einzuklinken. Betroffen sind etliche Hersteller, darunter Apple und Qualcomm.
Durch eine Sicherheitslücke in der Bluetooth-Implementierung können sich Angreifer in die Funkverberbindung einklinken, Datenverkehr im Klartext mitlesen und manipulieren. Die Schwachstelle betrifft zahreiche Hersteller, darunter Apple, Broadcommm, Intel und Qualcomm – demnach dürften etliche Millionen Geräte betroffen sein.
Das Problem steckt im kryptografisch abgesicherten Pairing-Mechanismus, bei dem ein Schlüsselaustausch nach Elliptic-Curve Diffie-Hellman (ECDH) stattfindet. Das ist erst mal gut und richtig, allerdings zeigte sich, dass einige Bluetooth-Implementierungen die eingesetzten ECDH-Parameter nicht oder nicht ausreichend überprüfen. Ein Angreifer kann diese Nachlässigkeit nutzen, um die Verschlüsselung der Verbindung zu schwächen und letztlich als Man-in-the-Middle den Datenverkehr zu kontrollieren. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=BlueBorne http://www.scoop.it/t/securite-pc-et-internet/?&tag=Bluetooth

|
Scooped by
Gust MEES
|
So praktisch SaaS ist. Das Konzept birgt auch große Risiken, wenn wie jetzt etwa Typeform ein SaaS-Provider das Opfer eines Datendiebstahls wird. Dann sind meist auch die Kunden des Anbieters betroffen.
Viele Unternehmen binden heutzutage immer wieder diverse Online-Umfragen in ihre Web-Seiten ein. Dabei greifen sie gerne auf vorgenerierte Formulare von externen Anbietern zu. Eines dieser Unternehmen, der spanische Software-as-a-Service-Spezialist (SaaS) Typeform, musste nun einen Datendiebstahl eingestehen, bei dem auch zahlreiche Datensätze von Kunden des Unternehmens geklaut worden sein sollen.
Der oder die Angreifer konnten sich laut Typeform Zugriff auf ein Backup von Anfang Mai dieses Jahres verschaffen. Darin enthalten waren API-Keys, Token zum Zugriff auf die von Typeform angebotenen Dienste und Zugangsdaten zu OAuth-Applikationen, aber auch Daten von Kunden, die Online-Formulare ausgefüllt hatten. Um welche Informationen es sich dabei genau handelte, teilte Typeform nicht mit. Laut Medienberichten meldeten sich aber bereits mehrere betroffene Unternehmen wie Fortnum & Mason.
Wie das Londoner Kaufhaus mitteilte, wurden ihm etwa 23.000 Datensätze gestohlen. Sie enthielten E-Mail-Adressen, Antworten auf Fragen und teilweise auch Postadressen sowie andere private Informationen der Nutzer. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Data breaches are always bad news, and this one is peculiarly bad.
Gentoo, a popular distribution of Linux, has had its GitHub repository hacked.
Hacked, as in “totally pwned”, taken over, and modified; so far, no one seems to be sure quite how or why.
That’s the bad news.
Fortunately (we like to find silver linings here at Naked Security):
The Gentoo team didn’t beat around the bush, and quickly published an unequivocal statement about the breach.
The Gentoo GitHub repository is only a secondary copy of the main Gentoo source code.
The main Gentoo repository is intact.
All changes in the main Gentoo repository are digitally signed and can therefore be verified.
As far as we know, the main Gentoo signing key is safe, so the digital signatures are reliable.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Hacker erlangen Zugriff auf Gentoo-Code in Github
Der Quellcode der Linux-Distribution Gentoo könnte kompromittiert sein: Das Entwicklerteam berichtet von einem Hack der gesamten Github-Organisation, in der Repositories abgelegt sind. Davon unberührt sein sollen die Backup-Dateien, die das Team auf eigener Infrastruktur hostet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Forscher der Sicherheitsfirma Appthority haben 2,7 Millionen Apps für Android und iOS untersucht, berichtet The Hacker News. Bei mehr als 3.000 Anwendungen stellten die Experten fest, dass die verwendeten Firebase-Datenbanken nicht geschützt waren. Über 80 Prozent der Apps gibt es für die Android-Plattform. Die Forscher spürten Tausende von Datenbanken mit mehr als 100 Millionen Datensätzen auf, darunter viele geheime Informationen wie Kennwörter, Standorte und sogar Gesundheitsdaten. COMPUTER BILD fasst die Fakten für Sie zusammen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Apps

|
Scooped by
Gust MEES
|
The latest Facebook privacy SNAFU (Situation Normal, All Facebooked Up) is a bug that changed settings on some accounts, automatically suggesting that their updates be posted publicly, even though users had previously set their updates as “private”.
On Thursday, Facebook asked 14 million users to review posts made between 18 May and 22 May: that’s when the bug was changing account settings. Not all of the 14 million users affected by the bug necessarily had their information publicly, mistakenly shared, but best to check.
Facebook Chief Privacy Officer Erin Egan said in a post that as of Thursday, the company had started letting those 14 million people know about the situation. She stressed that the bug didn’t affect anything people had posted before that time, and even then, they could still have chosen their audience like they always have.
Normally, the audience selector is supposed to be sticky: every time you share something, you get to choose who sees it, and the suggestion is supposed to be based on who you shared stuff with the last time you posted. Friends only? Fine, that’s what should be automatically suggested for the next post, and the one after that, until you change it… or a weird little glitch like this pops up. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook

|
Scooped by
Gust MEES
|
Des chercheurs danois et suédois en sciences informatiques et systèmes autonomes ont décortiqué la sécurité du robot Pepper de Softbank Robotics utilisé notamment au Japon dans des points de vente Nestlé. Utilisation de logiciels non mis à jour et exposition à des attaques XSS, par force brute et élévation de privilèges font partie des vulnérabilités de sécurité recensées. Depuis quelques années, les études relatives à la sécurité des objets connectés se suivent et se ressemblent. Toutes - ou presque - pointent leurs lacunes en termes de sécurité, un phénomène qui ne remonte pas à hier. Parmi la ribambelle de périphériques reliés au réseau, certains sont plus emblématiques que d'autres, notamment ceux appartenant à la catégorie des robots parmi lesquels Pepper, propriété de SoftBank Robotics suite au rachat du français Aldebaran Robotics. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot https://www.scoop.it/t/luxembourg-europe/?&tag=Pepper

|
Scooped by
Gust MEES
|
A company that collects the real-time location data on millions of cell phone customers across North America had a bug in its website that allowed anyone to see where a person is located -- without obtaining their consent.
US cell carriers are selling access to your real-time phone location data
The company embroiled in a privacy row has "direct connections" to all major US wireless carriers, including AT&T, Verizon, T-Mobile, and Sprint -- and Canadian cell networks, too.
Earlier this week, we reported that four of the largest cell giants in the US are selling your real-time location data to a company that you've probably never heard about before.
The company, LocationSmart, is a data aggregator and claims to have "direct connections" to cell carriers to obtain locations from nearby cell towers. The site had its own "try-before-you-buy" page that lets you test the accuracy of its data. The page required explicit consent from the user before their location data can be used by sending a one-time text message to the user. When we tried with a colleague, we tracked his phone to a city block of his actual location.
But that website had a bug that allowed anyone to track someone's location silently without their permission.
"Due to a very elementary bug in the website, you can just skip that consent part and go straight to the location," said Robert Xiao, a PhD student at the Human-Computer Interaction Institute at Carnegie Mellon University, in a phone call.
"The implication of this is that LocationSmart never required consent in the first place," he said. "There seems to be no security oversight here."
The "try" website was pulled offline after Xiao privately disclosed the bug to the company, with help from CERT, a public vulnerability database, also at Carnegie Mellon.
Xiao said the bug may have exposed nearly every cell phone customer in the US and Canada, some 200 million customers. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=tracking https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy https://www.scoop.it/t/securite-pc-et-internet/?&tag=Big+Data

|
Scooped by
Gust MEES
|
Mozilla has released Firefox 60 with support for a new option to sign in to websites without using a password.
That's thanks to an emerging W3C standard called Web Authentication or WebAuthn, which is enabled by default in Firefox 60 and is coming later this month to Chrome 67, and Microsoft Edge. It's also under consideration for Safari.
By removing passwords, the WebAuthn API will make phishing attacks a lot harder and gives users more convenient authentication choices, including hardware security key dongles such as a YubiKey device, fingerprint readers on smartphones, or facial-recognition systems like the iPhone X's Face ID.
A key advantage, like the FIDO Alliance's predecessor U2F standard for security keys, is that WebAuthn generates cryptographic public-private pairs for signing in, which means no shared secrets that could be leaked if a site is hacked.
Though the standard is currently only rolling out to desktop browsers, in future mobile browsers are likely to support it too.
Beyond signing into websites, WebAuthn combined with another WC3 standard in development, the Payment Request API, will one day make it possible to authorize online purchases from a mobile browser using a fingerprint. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers

|
Scooped by
Gust MEES
|
The US Food and Drug Administration (FDA) last month approved a firmware patch for pacemakers made by Abbott’s (formerly St Jude Medical) that are vulnerable to cybersecurity attacks and which are at risk of sudden battery loss.
Some 465,000 patients are affected. The FDA is recommending that all eligible patients get the firmware update “at their next regularly scheduled visit or when appropriate depending on the preferences of the patient and physician. At the time, cryptographic expert Matthew Green, an assistant professor at John Hopkins University, described the pacemaker vulnerability scenario as the fuel of nightmares. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Pacemakers+Hacking
|

|
Scooped by
Gust MEES
|
A new way to compromise the WPA/WPA2 security protocols has been accidentally discovered by a researcher investigating the new WPA3 standard.
The attack technique can be used to compromise WPA/WPA2-secured routers and crack Wi-Fi passwords which have Pairwise Master Key Identifiers (PMKID) features enabled.
Security researcher and developer of the Hashcat password cracking tool Jens "Atom" Steube made the discovery and shared the findings on the Hashcat forum earlier this month.
At the time, Steube was investigating ways to attack the new WPA3 security standard. Announced in January by industry body the Wi-Fi Alliance, WPA3 is the latest refresh of the Wi-Fi standard.
WPA3 aims to enhance user protection, especially when it comes to open Wi-Fi networks and hotspots commonly found in public spaces, bars, and coffee shops. The new standard will utilize individualized data encryption to scramble connections -- as well as new protections against brute-force attempts to crack passwords.
However, the aging WPA2 standard has no such protection. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/05/27/dangers-of-wifi-in-public-places/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=WiFi

|
Scooped by
Gust MEES
|
Check Point hat rund 10.000 gehackte WordPress-Websites entdeckt, die Teil einer Strategie zur großflächigen Malware-Verbreitung über Werbenetzwerke sind.
Das IT-Sicherheitsunternehmen Check Point hat eine umfangreiche Malware-Kampagne entdeckt, die auf Malvertising – also dem Missbrauch von Werbeanzeigen zur gezielten Schadcode-Verbreitung – basiert. Gegenüber The Register berichteten die Forscher am vergangenen Montag von mehr als 40.000 wöchentlichen Infektionsversuchen über die präparierten Anzeigen. Sie sagten auch, dass die Kampagne noch aktiv sei.
(Bild: blog.checkpoint.com)
Beim Malvertising kaufen Kriminelle als "Advertiser" Werbeflächen auf den Websites von "Publishern" über den Umweg spezieller Werbenetzwerke ein. Die eingekauften Flächen nutzen sie dann, um Website-Besucher mittels Umleitungen auf Malware-Sites zu manövrieren. Meist läuft ein solcher Einkauf über automatisierte Online-Auktionen: Der Höchstbietende erhält den Zuschlag. Oft sind auch noch Zwischenhändler ("Reseller") beteiligt. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress https://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?&tag=Cybersecurity

|
Scooped by
Gust MEES
|
Neue Versionen der 7er-, 8er- und 9er-Reihe des Anwendungsservers Apache Tomcat bringen unter anderem zwei dringliche Security-Fixes mit.
Die Apache Software Foundation hat Updates für mehrere Versionen des Open-Source-Webservers und Webcontainers Apache Tomcat veröffentlicht. Laut einem Sicherheitshinweis des US-CERT schließen sie unter anderem zwei Lücken, deren Schweregrad die Apache-Entwickler als "Important" einstufen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Tomcat

|
Scooped by
Gust MEES
|
Another day, another Linux community with malware woes.
Last time it was Gentoo, a hard-core, source-based Linux distribution that is popular with techies who like to spend hours tweaking their entire operating sytem and rebuilding all their software from scratch to wring a few percentage points of performance out of it.
That sort of thing isn’t for everyone, but it’s harmless fun and it does give you loads of insight into how everything fits together.
That sets it apart from distros such as ElementaryOS and Mint, which rival and even exceed Windows and macOS for ease of installation and use, but don’t leave you with much of a sense of how it all actually works.
This time, the malware poisoning happened to Arch Linux, another distro we’d characterise as hard-core, though very much more widely used than Gentoo.
Three downloadable software packages in the AUR, short for Arch User Respository, were found to have been rebuilt so they contained what you might (perhaps slightly unkindly) refer to as zombie downloader robot overlord malware.
Bots or zombies are malware programs that call home to fetch instructions from the crooks on what to do next.

|
Scooped by
Gust MEES
|
Wi-Fi devices have been using the same security protocol for over a decade. But today, that’ll begin to change: the Wi-Fi Alliance, which oversees adoption of the Wi-Fi standard, is beginning to certify products that support WPA3, the successor to the WPA2 security protocol that’s been in use since 2004.
The new protocol provides a number of additional protections for devices connected over Wi-Fi. One big improvement makes it harder for hackers to crack your password by guessing it over and over again, and another limits what data hackers can see even once they’ve uncovered the passcode. Nothing will change as far as users see it; you’ll still just type in your password and connect to the network.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WiFi https://www.scoop.it/t/securite-pc-et-internet/?&tag=WPA2

|
Scooped by
Gust MEES
|
Sportswear maker Adidas announced a data breach yesterday evening, which the company says it impacted shoppers who used its US website.
The company says it became aware of the breach on Tuesday, June 26, when it learned that an unauthorized party was claiming to have acquired the details of Adidas customers.
"According to the preliminary investigation, the limited data includes contact information, usernames and encrypted passwords," an Adidas spokesperson said.
"Adidas has no reason to believe that any credit card or fitness information of those consumers was impacted," he added.
The company said it's still investigating the breach with law enforcement and security firms.
A few millions impacted Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=wearables

|
Scooped by
Gust MEES
|
A little-known, Florida-based marketing firm called Exactis may be responsible for a significant amount of personal data being exposed. According to a report from Wired, the firm left 340 million individual records on a publicly accessible server that any person could have gotten ahold of.
The leak was discovered earlier this month by security researcher Vinny Troia, founder of the New York-based security firm Night Lion Security. He reported his find to the FBI and Exactis earlier this week, and while the company has since protected the data, it’s unclear just how long it sat exposed.
So just how bad is the leak? It’s pretty bad! The data stored on the server amounts to about two terabytes worth of personal information.
Troia told Wired the database from Exactis appears to have data from “pretty much every US citizen” in it, with approximately 230 million records on American adults and 110 million records on US business contacts. That falls in line with Exactis’ own claim on its website that it has data on 218 million individuals. If the leak is truly as big as estimated, it would make for one of the largest exposures of personal information in recent memory. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Android Google Playstore Trickbetrüger versuchen mit gefälschten Installationszahlen unwissende Smartphone User dazu zu animieren, fragwürdige Apps zu installieren. Wir zeigen, wie man den Schwindel aufdeckt. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
MyHeritage, an Israeli DNA, and genealogy website has suffered a massive data breach in which email accounts and hashed passwords of 92 million users (92,283,889) who signed up to the service up to October 26, 2017, have been stolen.
The compromised MyHeritage data was discovered by a security researcher on a private server outside of MyHeritage and reported the incident to the company who after an in-depth analysis acknowledged the breach and published an official statement on June 4, 2018. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyber-Attacks

|
Scooped by
Gust MEES
|
The Z-Wave wireless communications protocol used for some IoT/smart devices is vulnerable to a downgrade attack that can allow a malicious party to intercept and tamper with traffic between smart devices.
The attack —codenamed Z-Shave— relies on tricking two smart devices that are pairing into thinking one of them does not support the newer S-Wave S2 security features, forcing both to use the older S0 security standard.
The problem, as security researchers from Pen Test Partners have explained this week, is that all S0 traffic is secured by default with an encryption key of "0000000000000000."
An attacker that can trick a smart device into pairing with another device, a PC, or a smartphone app via the older S0 standard, can later decrypt all traffic exchanged between the two because the decryption key is widely known.
The Pen Test crew say they identified three methods that can be used to trick two devices into pairing via the old S0 instead of S2, even if both support the newer security standard.
Z-Shave attack is pretty dangerous
The Z-Shave attack is dangerous because devices paired via an older version of Z-Wave can become a point of entry for an attacker into a larger network, or can lead to the theft of personal property.
While this flaw might prove frivolous for some devices in some scenarios, it is a big issue for others —such as smart door locks, alarm systems, or any Z-Wave-capable device on the network of a large corporation. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|
A bug that allowed two researchers to gain access to the backend systems of a popular internet-connected vehicle management system could have given a malicious hacker everything they needed to track the vehicle's location, steal user information, and even cut out the engine.
In a disclosure this week, the researchers Vangelis Stykas and George Lavdanis detailed a bug in a misconfigured server run by Calamp, a telematics company that provides vehicle security and tracking, which gave them "direct access to most of its production databases."
Car hacking has become a major focus in the security community in recent years, as more vehicles are hooked up to the cellular internet. But while convenient to control your car from your phone, it's also opened up new points for attack -- which could have real-world consequences.
You might not even realize you're a Calamp user. Many apps, including the vehicle tracking app Viper SmartStart, which lets users locate, start, and control their car from their phone, connects to the outside world using a Calamp modem to its cloud-based servers.
The researchers found that the Viper mobile app, while secure, was connecting to two different servers -- one used by Viper, and another run by Calamp.
Using the same credentials as the app, the researchers were also able to log in and gain complete access to the Calamp server, the researchers said in their write-up.
"You could easily exploit it and as we had full access to the database," said Stykas in an email. "We could do a lot of stuff -- pretty much any scenario that we could think of was disastrous, like mass stealing cars or turning off vehicle via panic button when going with a high speed," he said.
By querying the database, Stykas said it was possible to find a car by looking up nearby latitude and longitude coordinates, reset the password, unlock the driver's side door, start the engine, and drive away. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cars

|
Scooped by
Gust MEES
|
Ein Buffer Overflow ermöglicht es Hackern, eine in Infrastrukturanlagen viel genutzte Software anzugreifen - per Ddos oder Fremdcode. Die Lücken seien auch bereits ausgenutzt worden. Mittlerweile soll ein Patch zur Verfügung stehen.
Die Software im Kraftwerk anzugreifen, kann große Schäden verursachen.
IT-Security-Forscher des Unternehmens Tenable Security haben eine Sicherheitslücke entdeckt, die in essentieller Infrastruktursoftware auftritt. Über einen Buffer Overflow könnten Angreifer Zugriff auf ein Netzwerk erhalten, eine Denial-of-Sevice-Attacke starten oder böswilligen Code ausführen. Betroffen sind die Programme Indusoft Web Studio und Intouch Machine Edition vom Entwickler Schneider Electric. Beide werden beispielsweise in Wasserwerken, Gaskraftwerken oder Ölraffinerien eingesetzt, um die dortige Maschinerie zu verwalten und zu steuern - kritische Anlagen, bei denen Fehlfunktionen große Schäden anrichten können. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=GRID
|



 Your new post is loading...
Your new post is loading...

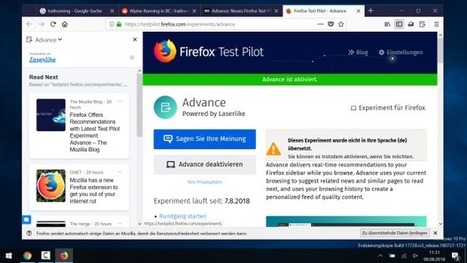



























Das Tracking wird über die US-Firma Laserlike abgewickelt. Damit die Empfehlungen in der Seitenleiste auch passen, ist der umfangreiche Zugriff auf Daten, etwa den Browser-Verlauf und die aktuell geöffneten Seiten, nötig. Außerdem sammelt Laserlike IP-Adresse, Zugriffszeiten und Verweildauer auf Webseiten.
Im Rahmen von Test-Pilot tracken Laserlike und Mozilla noch Daten zur Nutzung von Advance, etwa Verweildauer auf empfohlenen Seiten oder Informationen zum Betriebssystem. Was man Mozilla zugute halten muss: Sie verschweigen das Thema Tracking nicht und bauen einen Schalter ein, um Advance pausieren zu lassen.
Auch im Privatmodus oder mit eingeschaltetem Tracking-Schutz funktioniert die Erweiterung nicht. Wer möchte, kann die übermittelten Daten einsehen und löschen.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=tracking