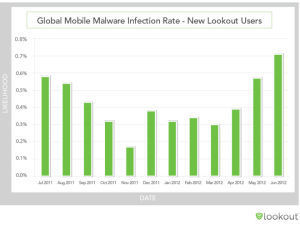
Principal Security experts are confident that in the next months we will assist to the explosion for Android botnets and in general of mobile cyber threats.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Gust MEES's curator insight,
June 19, 2013 12:03 PM
For the first time, mobile spammers can use such information as the subscriber’s first name, zip code, income level, and ethnicity to make attacks personalized and more effective. A MUST read!!!

Zhao KQiang's curator insight,
March 27, 2014 7:23 AM
give some opinions of that why teachers and education should learn network secutity 
Dean J. Fusto's curator insight,
July 31, 2015 10:12 AM
In the 21st Century, Education has a BIG responsibility to adapt to the very quick change in the world and to teach the students the knowledge they need and which are required to fulfill the market’s needs!
The market’s needs are ALSO to employ people with the basics of Cyber-Security knowledge as a modern company needs to protect its online reputation and a data loss could be lethal to them, their ruin eventually! SO, the new employees is the students coming out of school, College, High school, Universities; ALL of them need to have the basic knowledge of Cyber-Security to be competitive in a working market where there is more and more unemployment worldwide…
===> A company would take advantage of a new employee who as already the necessary knowledge of Cyber-Security as the company doesn’t need to train him, which saves it a lot of money! <===
===============================================
There has been a lot of talk both in the U.S. and internationally about a shortage in skilled IT professionals - with a predicted 864,000 IT vacancies in Europe alone by 2015.
What are these skills that organizations are looking for? This infographic by via resource highlights the top skills that make a successful information security professional and skills the future workforce will need to tackle emerging threats.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic
- http://www.scoop.it/t/21st-century-learning-and-teaching?tag=Infographi
- http://www.scoop.it/t/ict-security-tools
Check also:
- https://gustmees.wordpress.com/
- https://gustmeesen.wordpress.com/
- https://gustmeesfr.wordpress.com/

Jean-Pierre Blanger's curator insight,
August 1, 2015 4:19 PM
In the 21st Century, Education has a BIG responsibility to adapt to the very quick change in the world and to teach the students the knowledge they need and which are required to fulfill the market’s needs!
The market’s needs are ALSO to employ people with the basics of Cyber-Security knowledge as a modern company needs to protect its online reputation and a data loss could be lethal to them, their ruin eventually! SO, the new employees is the students coming out of school, College, High school, Universities; ALL of them need to have the basic knowledge of Cyber-Security to be competitive in a working market where there is more and more unemployment worldwide…
===> A company would take advantage of a new employee who as already the necessary knowledge of Cyber-Security as the company doesn’t need to train him, which saves it a lot of money! <===
===============================================
There has been a lot of talk both in the U.S. and internationally about a shortage in skilled IT professionals - with a predicted 864,000 IT vacancies in Europe alone by 2015.
What are these skills that organizations are looking for? This infographic by via resource highlights the top skills that make a successful information security professional and skills the future workforce will need to tackle emerging threats.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic
- http://www.scoop.it/t/21st-century-learning-and-teaching?tag=Infographi
- http://www.scoop.it/t/ict-security-tools
Check also:
- https://gustmees.wordpress.com/
- https://gustmeesen.wordpress.com/
- https://gustmeesfr.wordpress.com/
|

Gust MEES's curator insight,
February 4, 2013 8:13 AM
A MUST have Infographic to understand the risks!!! SHOULD be pinned in any schools!

Nqobile Martha's curator insight,
May 29, 2014 9:05 AM
PRIVACY AND ICT The whys and wherefores of privacy
Privacy is a sensitive subject to which people attach great importance. The only problem is that they do not know exactly why. Still, if it is so important then it is also necessary to establish why that is the case. It is therefore the task of ethicists to clarify the relevant theoretical arguments and practical implications. Any topics that touch on privacy, such as the electronic files on patients (efp) and cameras in public spaces therefore soon become topics of heated social and political debate. People appreciate the advantages of new information technology but are at the same time alarmed to realize that so much is known about them. It is often emotions that play a decisive role because the relevant arguments are difficult to formulate not to mention weigh up. 
Nqobile Martha's curator insight,
May 29, 2014 9:08 AM
PRIVACY AND ICT The whys and wherefores of privacy
Privacy is a sensitive subject to which people attach great importance. The only problem is that they do not know exactly why. Still, if it is so important then it is also necessary to establish why that is the case. It is therefore the task of ethicists to clarify the relevant theoretical arguments and practical implications. Any topics that touch on privacy, such as the electronic files on patients (efp) and cameras in public spaces therefore soon become topics of heated social and political debate. People appreciate the advantages of new information technology but are at the same time alarmed to realize that so much is known about them. It is often emotions that play a decisive role because the relevant arguments are difficult to formulate not to mention weigh up. |








![Flaws in Samsung Phones Allow Hackers to Make Calls, Install Apps and Change Settings [Video] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/uDdxb_6-EHFa_IicUrmCETl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
![Why You Should Care About Mobile Security [INFOGRAPHIC] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/bCDzCBQu4qMgWJAbygdm2jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








![Managing Mobile Privacy | Security Intelligence Blog [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/m8EBNAOuN5Zr7PdORj8fTDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



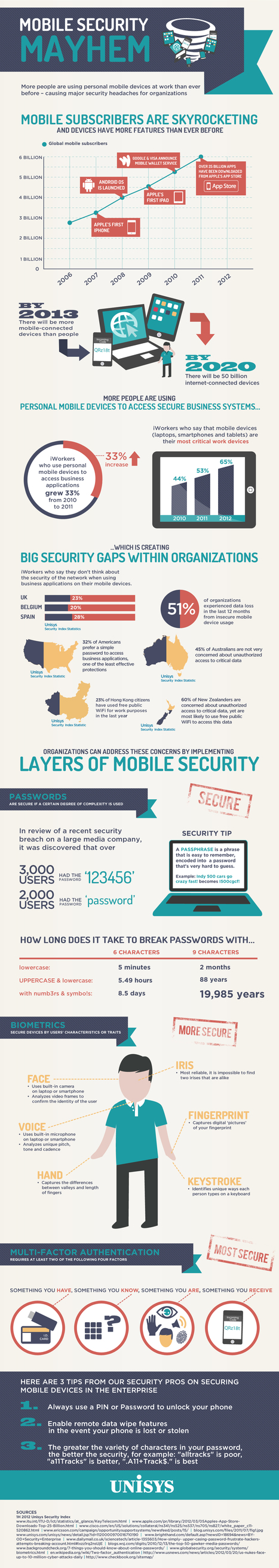






Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnets