The official Microsoft Security Blog provides in-depth discussion of security, cybersecurity and technology trends affecting trust in computing, as well as timely security news, trends, and practical security guidance.
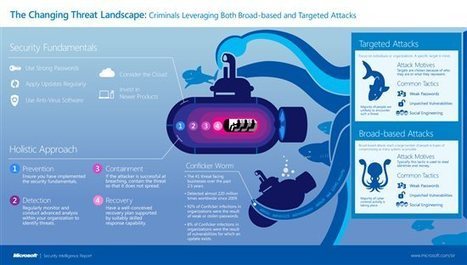
Today we released the latest volume of the Microsoft Security Intelligence Report (SIR) containing a large body of new data and analysis on the threat landscape. This volume of the SIR includes:
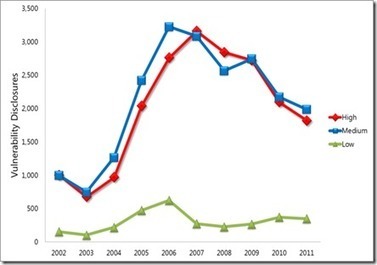
- Latest industry vulnerability disclosure trends and analysis
- Latest data and analysis of global vulnerability exploit activity
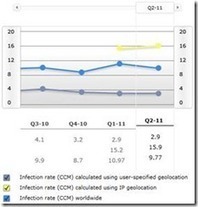
- Latest trends and analysis on global malware and potentially unwanted software
- Latest analysis of threat trends in more than 100 countries/regions around the world
- Latest data and insights on how attackers are using spam and other email threats
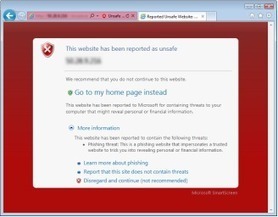
- Latest global and regional data on malicious websites including phishing sites, malware hosting sites and drive-by download sites
Read more...



 Your new post is loading...
Your new post is loading...