 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
It's all gone. All the passwords, all the user names, all the credit card numbers, the selfies, the fingerprints, the emails.
The state of tech security is currently so dire that it feels like anything you have ever stored on a computer, or a company or government has ever stored about you, has already been hacked into by somebody.
It's become so bad that it's already generated a mirthless cliché -- that there are only two types of companies: the ones that have been hacked and the ones that don't yet know they've been hacked. So what can we do? I'd suggest three decent starting points. First, as consumers we need to stop shrugging and accepting data leaks as business as usual. Security should influence our buying decisions: the organisations we deal with won't take security seriously unless customers and the public do, too. Our behaviour should signal to companies that good security can be a competitive differentiator. At the moment our apathy too often lets them off the hook. We as consumers need to understand the value of our data and then hold those that store it to account. Second, companies should design security as a fundamental part of the services we use, not a nice-to-have addition. Few hackers will give a new service time to implement security before attacking it, yet too many innovations (the IoT, I'm looking at you) seem to think security is a secondary consideration until they make it big. Until that changes, security will always be an afterthought. Third, the use of strong encryption should be the standard, not the exception. The digital services we use are now too intimate, too important, to be left unencrypted. The revelations of the last few years have shown us that no stream of data on the internet will go untapped by crooks or government. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching?tag=Proactive+Thinking

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Or, relève Adam Reeve, dans le second cas « Pokémon Go » peut quasiment tout faire :
Lire vos e-mails.
Vous en envoyer.
Accéder à votre Google Drive (qui permet de stocker des fichiers – que « Pokémon Go » peut supprimer !).
Lire vos historiques de recherche sur Google et Google Maps.
Et regarder vos photos.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Who Will Own Your Data If the Tech Bubble Bursts?
Corporations, data brokers, and even criminals might buy failed companies just for their users’ personal information. Desperate companies will resort, if they can, to selling the detailed data they’ve meticulously collected about their users—whether it’s personally identifiable information, data about preferences, habits, and hobbies, or national-security files. That data, formerly walled-off and spoon-fed only to paying advertisers, would be attractive to both licit and criminal buyers. Easily searchable datasets could generate new innovations and investments—but it would be difficult to know who’s buying up sensitive datasets, and why. If contracts and privacy policies prevent a floundering company from selling user data, there’s still another way to profit. Most privacy policies that promise not to sell user data include a caveat in case of bankruptcy or sale. In fact, a New York Times analysis of the top 100 websites in the U.S. last year found that 85 of them include clauses in their privacy policies like this one from Facebook: If the ownership or control of all or part of our Services or their assets changes, we may transfer your information to the new owner.
Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Password Day is a day for "taking our passwords to the next level" - here are five traditions the crooks really don't want us to start.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
LinuxCon 2015 Security guru Bruce Schneier says there's a kind of cold war now being waged in cyberspace, only the trouble is we don't always know who we're waging it against.
Schneier appeared onscreen via Google Hangouts at the LinuxCon/CloudOpen/Containercon conference in Seattle on Tuesday to warn attendees that the modern security landscape is becoming increasingly complex and dangerous.
"We know, on the internet today, that attackers have the advantage," Schneier said. "A sufficiently funded, skilled, motivated adversary will get in. And we have figure out how to deal with that."
Using the example of last November's crippling online attack against Sony Pictures, Schneier said it was clear that many of these new attacks were the work of well-funded nation-states.
"Many of us, including myself, were skeptical for several months. By now it does seem obvious that it was North Korea, as amazing as that sounds," he said.
But what's troubling about many of these new attacks, he added, is that they can be hard to spot when they don't come in the form that security experts typically expect.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack
http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
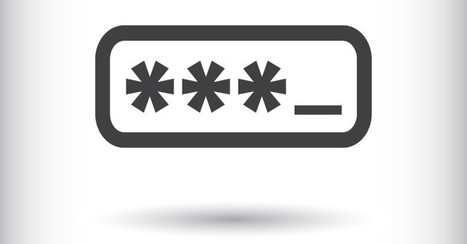
Just days after Microsoft released its latest operating system, hackers have begun targeting soon-to-be Windows 10 users with an emerging kind of malware.
Cisco security researchers are warning users against opening email attachments purporting to be from the software giant. The "ransomware" malware, which encrypts files until a ransom is paid, is being sent as part of an email spam campaign.

|
Scooped by
Gust MEES
|
Sur le site du projet OpenSSL, il est conseillé aux administrateurs de se tenir prêts à appliquer un correctif de sécurité très important, qui sera diffusé le 9 juillet.
« Ce correctif sera diffusé le 9 juillet. Il va combler une faille de sécurité jugée hautement critique ». Voici ce qu’on peut lire dans l’annonce de la diffusion de ce futur patch, sur le site du projet OpenSSL.

|
Scooped by
Gust MEES
|
Beim Hackerangriff auf die oberste Personalbehörde der US-Regierung sind Millionen sensibler Daten kopiert worden. Ein Jahr lang hatten die Angreifer Zugriff - auch wegen gewaltiger Schlamperei in dem Amt.
Netzwerk schon seit einem Jahr unterwandert Wer im Besitz eines dieser 127 Seiten langen Formulare ist, weiß über den entsprechenden Bewerber wohl mehr als jeder andere - vorausgesetzt, es wurde wahrheitsgemäß ausgefüllt. Für Vertreter eines ausländischen Geheimdienstes dürften diese Daten von unschätzbarem Wert sein, immerhin betreffen sie Menschen, die sich um Arbeitsplätze in Geheimdiensten, beim Militär oder in Behörden bemühen. Diese Daten wurden offenbar kopiert, aus den Beständen des Office of Personnel Management (OPM), gewissermaßen der Personalabteilung der US-Behörden.
Der "Washington Post" zufolge war das Netzwerk schon im Juni oder Juli 2014 erfolgreich unterwandert worden. Ein zweiter erfolgreicher Angriff,der im April bekannt wurde und bei dem 4,1 Millionen Personaldatensätze kopiert worden sein sollen, begann dem Bericht zufolge im Dezember 2014. Mittlerweile scheinen sich die Ermittler sicher zu sein: Die Täter sollen aus China stammen. "Es geht hier um die sensibelsten Informationen ohne Sicherheitseinstufung, auf die die Chinesen überhaupt Zugriff bekommen konnten", zitiert die "Washington Post" Stewart Baker, der früher einmal der Chefjustiziar der NSA war.
Mehr erfahren / Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack
|

|
Scooped by
Gust MEES
|
Über das Unternehmen Geofeedia konnten US-Behörden Standortdaten von Facebook- und Twitter-Nutzern sammeln.
Facebook, Instagram und Twitter kennen viele Details ihrer Nutzer. Dies hat offenbar auch die US-Regierung erkannt und die Datenströme der Dienste über die Analytics-Plattform Geofeedia angezapft . Laut der Bürgerrechtsorganisation American Civil Liberties Union (ACLU) nutzte unter anderem die Polizei diese Informationen, um die Rassenproteste in Oakland und Baltimore zu überwachen.
Die Sammlung der Daten wurde von dem in Chicago ansässigen Unternehmen Geofeedia übernommen, das die Informationen dann an rund 500 Strafverfolgungs- und Sicherheitsbehörden weitergereicht haben soll. Neben persönlichen Informationen wurden auch Standortdaten von Nutzern gesammelt.
Facebook und Twitter beteuern, dass es sich bei dem abgegriffenen Daten um öffentlich zugängliche Informationen handeln würde. Als Reaktion auf die Vorwürfe schränkten beide Unternehmen den Zugriff von Geofeedia auf die Datenströme der sozialen Netzwerke ein oder sperrten den Anbieter sogar. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ http://www.scoop.it/t/securite-pc-et-internet/?tag=Privacy

|
Scooped by
Gust MEES
|
Yes, hackers did manage to steal millions of account credentials back in 2012.
Make sure you have protected your account, and enabled two-step verification. At the time, security commentators such as Brian Krebs, Troy Hunt and myselfurged internet users to be wary of the claims - as they had not been verified. After all, it seemed possible that the data had been collected from heavily-reported mega breaches at Tumblr, LinkedIn and MySpace. Now, however, Dropbox has confirmed to the media that a 5GB archive of files, containing the email addresses and hashed passwords for some 68,680,741 accounts, is genuine.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Dropbox

|
Scooped by
Gust MEES
|
Pokemon Go hat ganze Städte weltweit in seinen Bann gezogen. Aber hat es auch Hackern ermöglicht, auf Ihr Telefon zuzugreifen?

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Ever felt like you were being watched online? You know, like when you read something about New York, and the next site you visit shows you ads for New York hotels? As it turns out, on my computer, there were more than 130 companies tracking my every move (check yours here, then install this plug-in).
These companies are basically engaging in mass surveillance. Just as governments justify tracking us to prevent terrorist attacks, these companies are tracking us online, without our consent, because a marginal 0.7 percent of the population clicks on their ads.
And it’s not just online advertisers. From e-commerce websites to physical retail stores, everyone is now racing to capture more data about us. Don’t be surprised if your insurance company starts charging you more because of how it thinks you should live your life!
Don’t get me wrong, I use Facebook, Google and all those other services. I use them because I find them useful, fun or because I don’t have an alternative. But I do it knowing very well that I am partly giving away my right to privacy. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Anybody who walks or drives past new tracking billboards with a mobile phone in their pocket can be spied on without their knowledge or consent: a potential invasion of privacy that US Senator Charles E. Schumer wants the US Federal Trace Commission (FTC) to investigate.
Schumer, a Democrat from New York, delivered a briefing in Times Square on Sunday, electronic billboards blinking and scrolling behind him.
From his remarks:
A person’s cell phone should not become a James Bond-like personal tracking device for a corporation to gather information about consumers without their consent.
No one wants to be followed or tracked throughout their day, electronically or otherwise.
These new “spying” billboards raise serious questions about privacy, Schumer said. They should be investigated by the feds, and the companies behind them should be required to offer an opt-out option for consumers who feel that they violate their privacy. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Cisco publie une étude portant sur un groupe de cybercriminels ayant intensivement eu recours à l’Angler Exploit Kit, une suite logicielle servant à infecter les machines via de multiples failles de sécurité. Sans surprise, les données récoltées par Cisco et Talos révèlent que le cybercrime paie plutôt bien.
En savoir plus / Mehr erfahren / Learn more:
http://www.scoop.it/t/securite-pc-et-internet/?tag=cybercrime

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
NICE Goals
NICE is a public-private partnership between government, academia, and the private sector. The mission of NICE is: “Cultivating an integrated cybersecurity workforce that is globally competitive from hire to retire, with the knowledge, skills, and ability to protect our nation from existing and emerging challenges.”

|
Scooped by
Gust MEES
|
Das European Institute for Computer Antivirus Research (Eicar) arbeitet an einem Qualitätssiegel, dem „Eicar Minimum Standard“, der das verloren gegangene Vertrauen in Antiviren-Software wiederherstellen soll. In der jüngeren Vergangenheit gab es immer wieder Berichte, dass Virenscanner und andere Sicherheitsprodukte durch Geheimdienste manipuliert worden seien.
Eicar-Testdatei für Virenscanner: Mit dieser harmlosen Testdatei ist das Eicar-Institut bekannt geworden.
Auch gibt es immer wieder Vermutungen, dass manche Sicherheitsprodukte staatliche Trojaner bewusst nicht erkennen und blockieren. Das Eicar-Siegel soll die Vertrauenswürdigkeit einer Lösung belegen. Für besonders hohe Erkennungsraten steht es dagegen nicht. Um dieses Themenfeld kümmern sich andere Organisationen wie etwa AV-Test, die gerade Enterprise-Virenscanner und Sicherheits-Apps für Android-Geräte getestet haben.
Laut Medienberichten interessieren sich bislang G Data, F-Secure, Kaspersky Lab und Trend Micro für das „Eicar Minimum Standard“-Gütesiegel. Auffällig ist, dass keines dieser Unternehmen aus den USA beziehungsweise aus Großbritannien stammt.

|
Scooped by
Gust MEES
|
Symantec has issued a warning about a successful scam being perpetrated against users of webmail services such as Gmail, Outlook and Yahoo.
The scam is explained in the following short video made by Symantec.
|



 Your new post is loading...
Your new post is loading...

























Emsisoft lässt Sie auch in der Weihnachtszeit nicht im Stich: Mit unserer Aufstellung der zwölf häufigsten Weihnachtsbetrügereien zeigen wir Ihnen, worauf Sie...
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Naivety