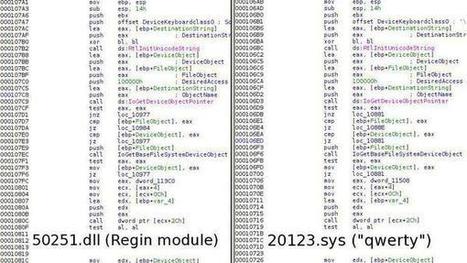
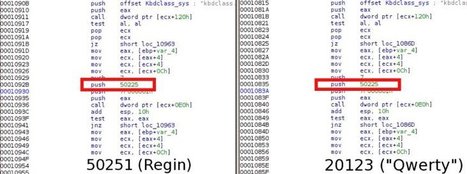
Laut Kaspersky stammen der Staatstrojaner Regin sowie der Keylogger QWERTY von ein und demselben Entwickler - dem US-amerikanischen Geheimdienst NSA.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO



 Your new post is loading...
Your new post is loading...












Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO
- https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/