DARPA postpones release of official solicitation.
Officials at the Defense Advanced Research Projects Agency have decided to postpone briefings and the release of solicitation documents for Plan X, a widely-anticipated funding initiative that will lay the foundation for the government’s push into offensive computer warfare operations.
“Due to an unanticipated and overwhelming response from industry and academia, DARPA has rescheduled the Plan X Proposers’ Day Workshop,” agency officials announced Sept. 5.
Two sessions with researchers and defense contractors—one classified and one non-classified—originally were slated for Sept. 27, but have now been moved to Oct. 15 and 16. “The second day will be a repeat of the first day to accommodate the remaining attendees,” the notice said. The request for proposals, originally scheduled for release at the end of this month, is expected to be published in October instead.
The surge of interest highlights a community emerging around offensive security technology. Plan X is a Pentagon initiative to develop computer architecture that monitors damage in “dynamic, contested, and hostile network environments,” adaptively defends against attacks, and performs “weapon deployment,” contracting documents indicate. The program is not funding malware or tools that hunt down vulnerabilities, but the resulting computer architecture will likely serve as the framework for their deployment.
Read more:
http://www.nextgov.com/defense/2012/09/pentagon-receives-overwhelming-response-plan-x-cyber-offensive/57961/



 Your new post is loading...
Your new post is loading...















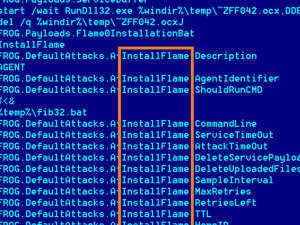






Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA