 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
International hackers and cyberattackers who launch operations against the UK will be retaliated against, the government has warned, as it sets out plans to protect infrastructure, business, and citizens from online threats.
These tactics form part of the government's National Cyber Security Strategy, an effort to boost defences against a variety of online threats.
The strategy, backed by £1.9bn in funding, was originally set out by the Conservative government under David Cameron.
"Our new strategy, underpinned by £1.9bn of support over five years and excellent partnerships with industry and academia, will allow us to take even greater steps to defend ourselves in cyberspace and to strike back when we are attacked," Philip Hammond, UK Chancellor of the Exchequer, is set to say in a speech in which he argues Britain "must now keep up with the scale and pace of the threats we face". Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
More evidence surfaced this week that computer surveillance tools belonging to the mysterious Equation hacking group are linked to the US National Security Agency.
Cyber-security experts were divided on the origin of the hacking code, which was leaked on Monday by another hacking group called calling itself the "Shadow Brokers." But The Intercept reported on Friday that a specific 16-character string found in a leaked NSA instruction manual also appears in the Shadow Brokers code.
The manual, a 31-page document entitled "FOXACID SOP for Operational Management," describes administrative tools for tracking surveillance targets, including a set of tags used to catalogue servers, according to The Intercept. The tags are used to trick Internet users into thinking they're browsing a safe website when in fact they've been sent a malicious payload from an NSA server.
Although it appears to show a link between the Shadow Brokers hack and the NSA, The Intercept acknowledges its findings don't necessarily mean that the NSA itself was hacked. The code could have been stolen from third-party hackers, a possibility Edward Snowden alluded to on Monday. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Shadow+Brokers http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA

|
Scooped by
Gust MEES
|
Notorious NSA contractor-turned-privacy advocate Edward Snowden warns the recent NSA hacks could have some really "messy" consequences. Notorious NSA contractor-turned-privacy advocate Edward Snowden today took toTwitter to discuss the details of yesterday’s ‘Equation Group’ hack. The Equation Group — allegedly an offshoot of the NSA — saw its defenses penetrated by a group calling itself ‘The Shadow Brokers.’ Eventually this data began to make its way online. The collected data is reported to be a cache of hack tools, known as binaries. According to Snowden, these tools are uploaded onto an NSA staging server as part of on-going operations to target and trace rival malware servers. The practice is known as Counter Computer Network Exploitation, or CCNE — a process that allows NSA hackers to steal tools used by foreign (or domestic rival) hackers in order to fingerprint them. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Shadow+Brokers

|
Scooped by
Gust MEES
|
Last Friday, a mysterious group by the name of “The Shadow Brokers” dumped what appeared to be some of the National Security Agency’s hacking tools online. There was some speculation as to whether the tools were legitimate. According to The Intercept, these tools are mentioned in documents leaked by NSA whistleblower Edward Snowden. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Shadow+Brokers

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
What is cyberwar?
At its core, cyberwarfare is the use of digital attacks by one country or nation to disrupt the computer systems of another with the aim of create significant damage, death or destruction.
What does cyberwarfare look like?
Cyberwar is still an emerging concept, but many experts are concerned that it is likely to be a significant component of any future conflicts. As well as troops using conventional weapons like guns and missiles, future wars will also be fought by hackers using computer code to attack an enemy's infrastructure.
Governments and nation states are now officially training for cyberwarfare: An inside look
Europe, Canada, USA, Australia, and others are now running training exercises to prepare for the outbreak of cyberwar. Locked Shields is the largest simulation and TechRepublic takes you inside.
Read More
Governments and intelligence agencies worry that digital attacks against vital infrastructure -- like banking systems or power grids -- will give attackers a way of bypassing a country's traditional defences. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Der Nachrichtendienst NSA ist offenbar Opfer eines Hackerangriffs geworden. Bereits 2013 erbeutete Überwachungsprogramme wurden jetzt im Internet veröffentlicht. Edward Snowden vermutet russische Hintermänner. Für die NSA könnte der Hack unangenehme Folgen haben.

|
Scooped by
Gust MEES
|
This is surely no frivolous hacker feud, but an incredibly sophisticated attack on the US cyber-security infrastructure — even though it was meant to look like it was carried out by Guy-Fawkes-mask-wearing ideological warriors, at least a bit. It even features a quasi-illiterate intro/rant railing against “the elites.” It’s a familiar refrain in an American political season dominated by anti-establishment politicians, and it fits well with the stereotype of the libertarian hacker — but it also seems to want to convince these elites not to support the sort of offensive hacking on display in their leak. Emphasis added:
We want make sure Wealthy Elite recognizes the danger cyber weapons, this message, our auction, poses to their wealth and control. Let us spell out for Elites. Your wealth and control depends on electronic data. You see what “Equation Group” can do. You see what cryptolockers and stuxnet can do. You see free files we give for free. You see attacks on banks and SWIFT in news. Maybe there is Equation Group version of cryptolocker+stuxnet for banks and financial systems? If Equation Group lose control of cyber weapons, who else lose or find cyber weapons? If electronic data go bye bye where leave Wealthy Elites? Maybe with dumb cattle? Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Shadow+Brokers http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA

|
Scooped by
Gust MEES
|
The number of high-profile hacks demonstrates that a silent cyberwar is already ongoing among countries in the cyberspace.
The recent hacks of the Democratic National Committee and presidential candidate Hillary Clinton’s campaign and the alleged infections spotted by the Russian FSB inside government networks demonstrate the intense activity in the cyberspace.
It is a virtual space crowded of nation-state actors and other threat actors that are threatening the security of Governments worldwide, and the situation is likely to get much worse.
At the recent NATO Warsaw Summit in July, the Alliance recognised the cyberspace as “a domain of operations in which Nato must defend itself as effectively as it does in the air, on land, and at sea”.
Kenneth Geers, a senior research scientist with security firm Comodo, speaking at the BlackHat USA security conference declared that the cyberwar is a real and present danger.
“There is no question cyberwar exists,” he says. “Whether it rises to the level of weapons of mass disruption is another question. We don’t have a decisive answer yet.” Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...





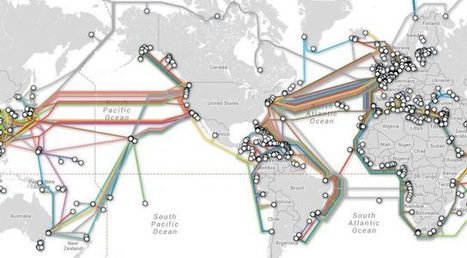








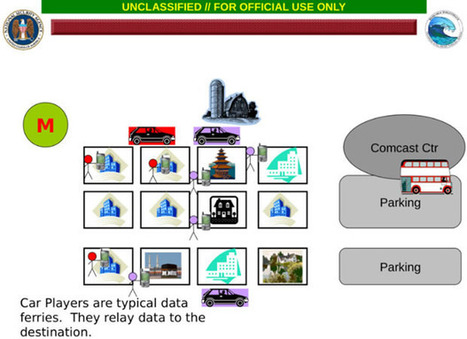







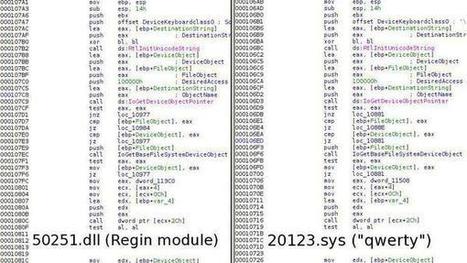







There's an urgent need for NATO and its member countries to address the cybersecurity of space-based satellite control systems because they're vulnerable to cyberattacks - and if left unaddressed, it could have severe consequences for global security, a new paper from a major thinktank on international affairs has warned.
Almost all modern military engagements rely on space-based assets, providing GPS coordinates, telecommunications, monitoring and more.
The newly released Cybersecurity of NATO's Space-based Strategic Assets research paper from Chatham House warns that there's an urgent need to study and address the cybersecurity of these systems and the challenges which could be posed if a network was breached or otherwise attacked.
Learn more / En savoir plus / Mehr erfahren:
https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/
https://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwarfare
https://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberwar...