 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Die ISS kreist in rund 400 Kilometern Höhe über der Erde. Diese Distanz reicht offenbar aber nicht aus, um von irdischen Problemen Abstand zu nehmen. Eine Astronautin wird nun verdächtigt, von der Raumstation aus ein Verbrechen begangen zu haben. Es wäre der erste Fall von Weltraum-Kriminalität.
Eine Nasa-Astronautin soll von der internationalen Raumstation ISS aus illegalerweise auf das Bankkonto ihrer Ex-Partnerin zugegriffen haben. Wie die "New York Times" berichtete, könnte es sich dabei um den ersten Vorwurf eines Verbrechens vom Weltraum aus handeln.
Demnach gab Anne McClain, die im Juni nach einem sechsmonatigen Aufenthalt im All auf die Erde zurückgekehrt war, gegenüber Ermittlern zu, auf besagtes Konto mit dem ihr bekannten Passwort zugegriffen zu haben. Sie habe sich vergewissern wollen, dass mit den - noch immer miteinander verwobenen - Finanzen des Ex-Paares alles in Ordnung sei, schrieb das Blatt. Die Sache flog dann auf, weil die Bank auf Nachfrage der Ex-Partnerin herausfand, dass Zugriffe auf das Konto von einem Nasa-Netzwerk vorgenommen worden waren - und zwar in der Zeit, in der McClain sich im All befunden hatte. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=cybercrime

|
Scooped by
Gust MEES
|
Over a million fiber routers can be remotely accessed, thanks to an authentication bypass bug that's easily exploited by modifying the URL in the browser's address bar.
The bug lets anyone bypass the router's login page and access pages within -- simply by adding "?images/" to the end of the web address on any of the router's configuration pages, giving an attacker near complete access to the router. Because the ping and traceroute commands on the device's diagnostic page are running at "root" level, other commands can be remotely run on the device, too.
The findings, published Monday, say the bug is found in routers used for fiber connections. These routers are central in bringing high-speed fiber internet to people's homes.
At the time of writing, about 1.06 million routers marked were listed on Shodan, the search engine for unprotected devices and databases. Half the vulnerable routers are located on the Telmex network in Mexico, and the rest are found on in Kazakhstan and Vietnam. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Router

|
Scooped by
Gust MEES
|
A critical flaw in electronic locks left millions of hotel rooms worldwide vulnerable to hackers. Now, the security researchers who developed the attack are helping hotels patch the problem, literally door to door.
Tomi Tuominen and Timo Hirvonen, who both work for the international cybersecurity firm F-Secure, uncovered a design flaw in the software of electronic keys produced by VingCard, a global provider of hotel locking systems. By F-Secure’s count, the vulnerable software, Vision, is deployed in as many as 166 countries at over 40,000 buildings—millions of doors, in other words.
While hijacking and cloning hotel room keys is nothing new, the attack designed by Hirvonen and Tuominen is exceptional for a few reasons: First off, it allows the attacker to produce a master key for the entire building within a matter of minutes. All that’s needed is a regular hotel room key. It can even be expired.
“It can be your own room key, a cleaning staff key, even to the garage or workout facility,” Tuominen told Gizmodo. “We can even do it in an elevator if you have your key in your front pocket; we can just clone it from there.” Tuominen compared the following step to a scene in Terminator 2, in which John Connor brute forces open a safe open with (movie trivia alert!) an Atari Portfolio palmtop computer, circa 1989. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Traveling

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
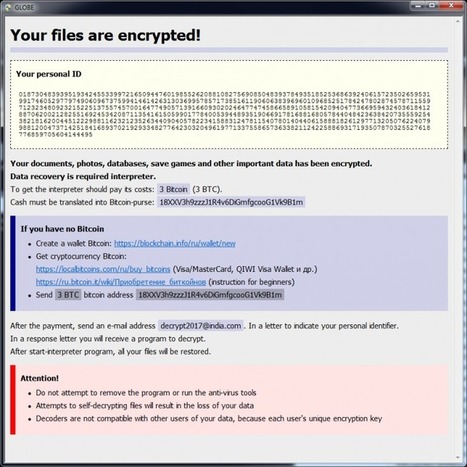
Another site in the booming cryptocurrency wallet sector has been hacked after what looks like a DNS hijacking attack.
The victim this time is BlackWallet, whose users reportedly lost 670,000 of a currency called Stellar Lumens (XLMs) worth around $425,000 at the point they were stolen on the afternoon of 13 January.
News that something was amiss first emerged in a Reddit posting claiming to be from the site’s admin:
BlackWallet was compromised today, after someone accessed my hosting provider account. I am sincerely sorry about this and hope that we will get the funds back.
A security researcher who took a look at blackwallet.co before it was taken down tweeted:
The DNS hijack of Blackwallet injected code, if you had over 20 Lumens it pushes them to a different wallet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
A newly uncovered form of Android malware aims to steal data from over 40 popular apps including Facebook, WhatsApp, Skype and Firefox - and the trojan has been actively engaging in in this illicit activity for almost two years.
Dubbed SpyDealer by the Palo Alto Networks researchers who discovered it, the malware harvests vast accounts of personal information about compromised users, including phone numbers, messages, contacts, call history, connected wi-fi information and even the location of the device.
The espionage capabilities of the trojan also enable it to record phone calls and videos, along with surrounding audio and video, take photos with both front and rear cameras, take screenshots of sensitive information and monitor the devices location at all times.
Described as an advanced form of Android malware, SpyDealer is able to open a backdoor onto compromised devices by abusing a commercially available Android accessibility service feature in order to root phones into providing superuser privileges.
Samples of the malware analysed by researchers suggests that the malware reuses root exploits used by commercial rooting app "Baidu Easy Root" in order to maintain itself on the compromised device while it harvests personal information and spies on communications from the apps with root privilege. According to the researchers, SpyDealer attempts to steal data from apps including WeChat, Facebook, WhatsApp, Skype, Line, Viber, QQ, Tango, Telegram, Sina Weibo, Tencent Weibo, Android Native Browser, Firefox Browser, Oupeng Brower, QQ Mail, NetEase Mail, Taobao, and Baidu Net Disk. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
ZDNet / Sicherheit / Virus
WannaCry: Microsoft kritisiert US-Geheimdienste
Microsoft will Regierungsbehörden verpflichten, Sicherheitslücken zu melden statt zu bevorraten. Es verspricht Hilfe für Kunden "unabhängig von ihrer Nationalität". Aber auch Microsoft kommt in die Kritik, nachdem es erst jetzt einen Patch für das vorwiegend betroffene Windows XP lieferte.
Microsoft-Chefjustiziar Brad Smith hat die US-Geheimdienste kritisiert und ihnen eine erhebliche Mitschuld an der Ransomware-Attacke WannaCrypt oder WannaCry vorgeworfen, die inzwischen weltweit schon über 200.000 Windows-PCs befallen hat. Er forderte erneut eine Digitale Genfer Konvention und rief zu gemeinsamem Handeln auf. Regierungsbehörden sollte nicht erlaubt sein, Sicherheitslücken zu bevorraten und auszunutzen.
Gleichzeitig versprach er, Microsoft werde Kunden unabhängig von ihrer Nationalität unterstützen und verteidigen, wenn sie Cyberangriffen ausgesetzt sind. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing

|
Scooped by
Gust MEES
|
Worms are a malware tactic from back in the day - but they still remain tricky to mitigate against... “It’s pretty aggressive, and it’s replicating very quickly.” That reads like the words of stressed system administrator affected by last week’s WannaCry (Wanna Decryptor) ransomware – but actually, that’s the reaction of a security expert from 13 years ago to a new variant of the Sasser worm. WannaCry’s ransomware high jinks apart, the echoes with last Friday’s events are intriguing. Just as WannaCry targets an oft-unpatched Windows SMB flaw, so in 2004 Sasser picked on the scab of unpatched Windows exploit in Local Security Authority Subsystem Service (LSASS – hence “Sasser”), which is – ironically – a bit of the OS used to manage security settings. If you think WannaCry’s victim count is impressive, Sasser’s included not-to-be-sniffed-at names such as Deutsche Post, the European Commission and Delta Airlines, to name only a selection. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing

|
Scooped by
Gust MEES
|
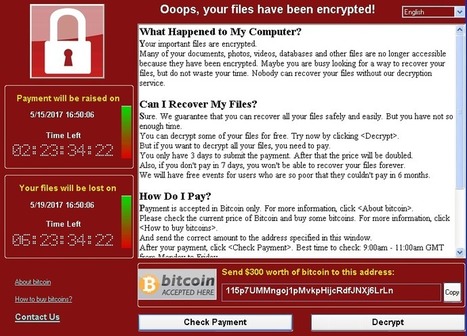
New ransomware samples of WannaCrypt variants have been discovered in the wild but it is yet to be seen if they pose the same threat as the first ransomware attack wave.
On Friday, at least 47 trusts across England and 13 National Health Service (NHS) services in Scotland were faced with severe disruption as IT services went into lockdown due to the Wanna Decryptor ransomware, also known as WannaCrypt, WanaCrypt0r and WannaCry.
Appointments were cancelled, the general public was urged to not visit NHS Accident & Emergency departments unless absolutely necessary and in some cases, patients were reportedly turned away or moved to other medical establishments as staff were forced to resort to pen-and-paper to try and maintain some order.
IT system provider NHS Digital said in a statement that the attack "was not specifically targeted at the NHS and is affecting organizations from across a range of sectors," words that soon rung true. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
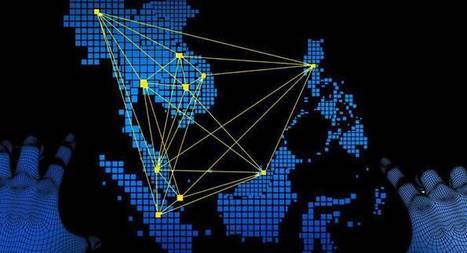
Investigators from seven Southeast Asian nations collaborated on a joint Interpol operation that identified approximately 8,800 command-and-control servers in eight countries and nearly 270 compromised websites, including government portals that may have contained personal data on citizens.
According to an Interpol press release, the exposed threats included malware attacks against banks and other institutions, ransomware, distribute denial of service attacks, and spam campaigns.
The operation, which focused specifically on the ASEAN (Association of Southeast Asian Nations) region, also uncovered several phishing website operators, "including one with links to Nigeria, with further investigations into other suspects still ongoing,” the press release announced. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Cybercrime...

|
Scooped by
Gust MEES
|
2016 was a tense and turbulent year in cyberspace – from the massive IoT botnets and ransomware to targeted cyberespionage attacks, financial theft... Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/
|

|
Scooped by
Gust MEES
|
A form of malware which uses fake Facebook Messenger messages to spread has suddenly surged back into life and has developed new tricks to steal passwords, steal cryptocurrency and engage in cryptojacking.
First uncovered in August last year, the malware used phishing messages over Facebook Messenger to direct victims to fake versions of websites like YouTube, at which point they are encouraged to download a malicious Chrome extension.
The malware has remained under the radar since then, at least until April when it appears to have suddenly spiked in activity, targeting Facebook users around the world.
Analysis by researchers at security company Trend Micro - which has dub the malware FacexWorm - said that while the malware is still spread via Facebook and exploits Google Chrome, many of its capabilities have been completely reworked.
New abilities include the capability to steal account credentials from selected websites, including Google as well as cryptocurrency websites. It also pushes cryptocurrency scams of its own and mines infected systems for additional currency.
But in order to conduct any of this activity, the malware needs to be installed on the system of a victim. Victims received a link out of the blue from a Facebook contact which directs to a fake YouTube page. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Facebook

|
Scooped by
Gust MEES
|
Die Schlösser von Millionen Hotelzimmern können Recherchen zufolge geknackt werden. Finnische IT-Experten fanden heraus, dass dazu eine einzige Hotelkarte ausreicht.
26. April 2018, 2:18 Uhr Quelle: ZEIT ONLINE, dpa, Reuters, ces
IT-Experte Timo Hirvonen hat das Rätsel um den Diebstahl eines Computers aus einem Hotelzimmer gelöst: diese Chipkarten. © Attila Cser/Reuters
Die elektronischen Schlösser in mehr als einer Million Hotelzimmertüren auf der ganzen Welt sind finnischen Sicherheitsexperten zufolge selbst mit alten Zugangskarten zu knacken. Zwei Mitarbeiter des Sicherheitsunternehmens F-Secure haben am Mittwoch eine Untersuchung zu der Schwachstelle veröffentlicht und damit wohl auch das Rätsel eines Laptop-Diebstahls 2003 in Berlin gelöst. Betroffen sind die Schlösser des Weltmarktführers Assa Abloy, eines schwedischen Unternehmens.
Timo Hirvonen und Tomi Tuominen zeigten Reportern von WDR, NDR und Süddeutscher Zeitung, wie der Einbruch ins Hotelzimmer gelingen kann, ohne Spuren zu hinterlassen. Lediglich eine einzige Hotelkarte reichte aus, um einen Generalschlüssel zu erstellen und damit alle Gästezimmer des jeweiligen Hotels zu öffnen. Der Vorgang dauert nur ein paar Sekunden. Darüber hinaus gelang es den IT-Experten über das Netzwerk der betroffenen Hotels auch Kundendaten auszulesen. Die beiden Finnen hatten sich zunächst in ihrer Freizeit damit beschäftigt, den ungeklärten Laptop-Diebstahl aufzuklären. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Traveling

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Ransomware-Attacke: 4000 Server und 45.000 PCs neu installiert
In zehn Tagen erneuerte Møller-Maersk seine gesamte IT-Infrastruktur. Die Folgekosten von Petya/NotPetya beziffert der Reederei-Konzern mit 250 bis 300 Millionen Dollar. Er strebt jetzt mehr Cybersicherheit als Wettbewerbsvorteil an.
Der Reederei-Konzern Møller-Maersk hat durch die Ransomware Petya/NotPetya einen Schaden zwischen 250 und 300 Millionen Dollar erlitten. Es gelang ihm jedoch, innerhalb von zehn Tagen 4000 Server, 45.000 PCs und 2500 Anwendungen neu zu installieren. Das berichtete auf dem Weltwirtschaftsgipfel in Davos Jim Hagemann Snabe, Chairman von Møller-Maersk.
„Stellen Sie sich ein Unternehmen vor, bei dem alle 15 Minuten ein Schiff mit 10.000 bis 20.000 Containern in einen Hafen einläuft, und Sie haben zehn Tage lang keine IT“, sagte Hagemann. „Man kann sich das fast gar nicht vorstellen.“ Der Maersk-Chef attestierte den Mitarbeitern und Partnern eine „heroische Leistung“ für die schnelle Erneuerung der IT-Infrastruktur. Der dänische Konzern hat Niederlassungen in 130 Ländern und fast 90.000 Mitarbeiter. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE https://www.scoop.it/t/securite-pc-et-internet/?&tag=Costs-of-Cybercirme

|
Scooped by
Gust MEES
|
Phishing, Trojans, Ransomware and Viruses: Hardly a day goes by without hacker attacks against companies or private individuals. This huge LUCY Infographic shows the explosion of internet crime State of Cyber Crime 2018 – Numbers in detail In the United States by Internet crime caused damage in 2001:17.8 million USD. In the United …

|
Scooped by
Gust MEES
|
Microsoft says the outbreak of WannaCry ransomware on 12 May reveals why governments shouldn't stockpile software vulnerabilities.
Microsoft's president and chief legal officer Brad Smith thinks governments' hoarding of flaws is a "problem."
These bugs might be valuable to the CIA and NSA, government agencies which can and do exploit flaws to advance the national security interests of the United States government.
But bad guys invariably find and leak these security holes, which places ordinary users at risk of attackers using exploit code to target unpatched systems. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
The account details of millions of subscribers to the education platform Edmodo have not only been stolen but witnessed to be for sale on the dark web, according to a post on Motherboard. The platform is used by more than 78 million teachers, students and parents to compose lesson plans, make homework assignments and other tasks.
Breach notification website LeakBase provided Motherboard with a sample of more than two million records, which included usernames, email addresses and hashed passwords.
The good news is that the passwords apparently are hashed with the stealthy bcrypt algorithm, and a string of random characters known as a salt, which likely will make it more difficult for hackers to obtain users' login credentials. And, when staffers at Motherboard attempted to open Edmodo accounts using some of the purloined data, they were unsuccessful as the address was already linked to an Edmodo account, the report explained.
The bad news is that at least a portion of the database is up for sale on the dark web marketplace Hansa for $1,000. The seller, going under the name nclay, said s/he was in possession of 77 million accounts. LeakBase reported that 40 million of those come with an email address.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES http://www.scoop.it/t/securite-pc-et-internet/?&tag=Edmodo+Insecurity

|
Scooped by
Gust MEES
|
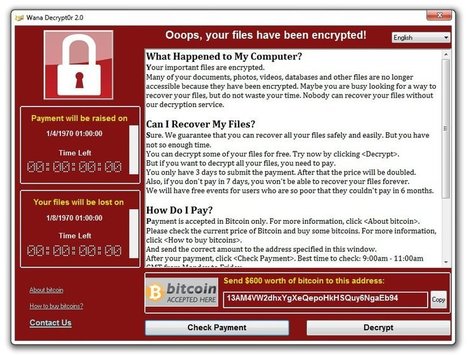
Das Drehbuch für diesen denkwürdigen Freitag, an dem innerhalb von Stunden 45.000 Computer in aller Welt lahmgelegt wurden, entstand am 15. April. Es beinhaltet Aussagen wie: "Dies ist ein Ein-Knopf-Hack. Du drückst den Knopf und der Server gehört dir. Alles, was du willst. Es ist superböse. Verrückt böse." Oder auch: "Du hast keine Ahnung, wie schlimm das ist, wenn du nicht in der IT eines Unternehmens arbeitest. Diese Sicherheitslücke wird zehn Jahre lang bestehen, oder länger."
Geschrieben hat das alles die Person, die sich auf Twitter @SwiftOnSecurity nennt. Wer dahinter steckt, ist unbekannt. Aber der einstige Satire-Account mit seiner schrägen Mischung aus Taylor-Swift-Songzeilen und Tipps zur IT- und Informationssicherheit wird in der Fachwelt längst ernst genommen. Denn wer auch immer dahinter steckt, hat offensichtlich eine Menge Ahnung vom Thema. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing

|
Scooped by
Gust MEES
|
What is a ransomware attack?
Ransomware is one of the biggest problems on the web right now. It's a form of malware which encrypts documents on a PC or even across a network. Victims can often only regain access to their files and PCs by paying a ransom to the criminals behind it. A ransomware infection often starts with someone clicking on what looks like an innocent attachment, and it can be a headache for companies of all sizes.
Cybercriminals didn't use to be so obvious. If hackers infiltrated your corporate network, they would do everything possible to avoid detection. It was in their best interests not to alert a victim that they'd fallen victim to cybercrime.
But now, if you are attacked with file-encrypting ransomware, criminals will brazenly announce they're holding your corporate data hostage until you pay a ransom in order to get it back. It might sound too simple, but it's working: cybercriminals pocketed over $1bn from ransomware attacks during 2016 alone. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Russian hackers are stealing between $3 million to $5 million per day from US brands and media companies in one of the most lucrative botnet operations ever discovered.
On December 20, researchers from White Ops said the scheme, dubbed "Methbot," is a Russian operation set up to watch up to 300 million video-based adverts automatically every day.
These adverts, displayed on legitimate domains owned by companies including the Huffington Post, Economist, Fortune, ESPN, Vogue, CBS Sports, and Fox News, are used to generate additional revenue through advertising sponsors which help keep these businesses afloat.
However, White Ops says Methbot capitalizes on this revenue generation by targeting the most expensive advertising on the web -- such as full-blown video adverts on branded websites -- and is programmed to show signs of "engagement" to fool ad providers into thinking the content is being watched legitimately.
Faked clicks, mouse movements, social network login information, and typical "working hours" are all methods to keep the operation under wraps. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=cybercrime
|



 Your new post is loading...
Your new post is loading...
















![State of Cyber Attacks 2018 – A big Overview about Cybercrime [Infographic] - LUCY Phishing, Social Hacking and Security Awareness | #CyberSecurity | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/dH0qjTsuLei_pVSG-kbkczl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)









Die ISS kreist in rund 400 Kilometern Höhe über der Erde. Diese Distanz reicht offenbar aber nicht aus, um von irdischen Problemen Abstand zu nehmen. Eine Astronautin wird nun verdächtigt, von der Raumstation aus ein Verbrechen begangen zu haben. Es wäre der erste Fall von Weltraum-Kriminalität.
Eine Nasa-Astronautin soll von der internationalen Raumstation ISS aus illegalerweise auf das Bankkonto ihrer Ex-Partnerin zugegriffen haben. Wie die "New York Times" berichtete, könnte es sich dabei um den ersten Vorwurf eines Verbrechens vom Weltraum aus handeln.
Demnach gab Anne McClain, die im Juni nach einem sechsmonatigen Aufenthalt im All auf die Erde zurückgekehrt war, gegenüber Ermittlern zu, auf besagtes Konto mit dem ihr bekannten Passwort zugegriffen zu haben. Sie habe sich vergewissern wollen, dass mit den - noch immer miteinander verwobenen - Finanzen des Ex-Paares alles in Ordnung sei, schrieb das Blatt. Die Sache flog dann auf, weil die Bank auf Nachfrage der Ex-Partnerin herausfand, dass Zugriffe auf das Konto von einem Nasa-Netzwerk vorgenommen worden waren - und zwar in der Zeit, in der McClain sich im All befunden hatte.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=cybercrime