 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Scam artists have taken advantage of a contract migration initiative to swindle NFTs out of users in an opportunistic phishing attack.
Last week, NFT marketplace OpenSea announced the rollout of contract migrations and an upgrade to make sure inactive, old NFT listings on Ethereum expire safely and to allow OpenSea to "offer new safety features in the future."
The contract migration timeline was set from February 18 to February 25.
NFT holders are required to make the change, and OpenSea published a guide to assist them. After the deadline, any listings that were not migrated would expire, although they could be re-listed after this window without further fees.
However, an attacker saw an opportunity to cash in. Check Point Research has suggested that phishing emails were sent to users, linking them to fraudulent websites. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=blockchain https://www.scoop.it/topic/securite-pc-et-internet/?&tag=WEB3 https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
The malware also mines Monero & Ethereum cryptocurrency on targeted devices.
We’re seeing new variants of malware being deployed every day. just yesterday we covered a skimmer funneling funds through Telegram and today we’re back with a new report by WeLiveSecurity.
Shedding light on a new malware family named KryptoCibule; the researchers report on 3 main tasks that it seeks to perform:
Mining Monero and Ethereum cryptocurrencies using a CPU and GPU respectively
Stealing funds by replacing legitimate wallet addresses with attacker-controlled ones with the help of the clipboard
Steal and extract cryptocurrency-related files
See: Best legal, safe & free online streaming sites – 2020
Alongside this, a remote administration tool (RAT) is also used to maintain access to the victim’s machine in order to control it. Furthermore, both the TOR Network and BitTorrent protocol is used for transmitting data and communication in general. This is yet another example of how legitimate services can be used by attackers for their own nefarious motives. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/topic/securite-pc-et-internet/?&tag=TOR

|
Scooped by
Gust MEES
|
Was haben die Netzauftritte von Fußballstar Cristiano Ronaldo und der gemeinnützigen Organisation Make-a-Wish mit indischen Behörden-Websites gemeinsam? Sie alle wurden schon einmal von Kriminellen so manipuliert, dass sie die Rechenleistung der Computer und Smartphones ihrer Besucher kaperten. Bis die Betreiber der Angebote merkten, was los war, schürften die Geräte der Website-Besucher nach der Digitalwährung Monero - immer solange, wie die Seiten im Browser geöffnet waren.
Internetsurfer werden ohne ihr Wissen Krypto-Schürfer: Diese Betrugsmasche, die auch mit anderen Digitalwährungen funktioniert, heißt Cryptojacking - kombiniert aus "Cryptocurrency" (Kryptowährung) und "Hijacking" (Entführung). Der Angriff über den Browser schadet dem Gerät in der Regel nicht unmittelbar, davon abgesehen, dass es wegen der Rechenvorgänge oft heiß oder lauter wird. Er ist aber doch ärgerlich, weil Dritte hier quasi Akkuleistung oder Strom sowie Bandbreite von ihren Opfern abgreifen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
A new form of cryptocurrency mining malware uses a leaked NSA-exploit to spread itself to vulnerable Windows machines, while also disabling security software and leaving the infected computer open to future attacks.
The Python-based malicious Monero miner has been uncovered by researchers at security company Fortinet who've dubbed it PyRoMine. It first appeared this month and spreads using EternalRomance, a leaked NSA-exploit which takes advantage of what until a year ago had been an undisclosed SMB vulnerability to self-propagate through networks.
EternalRomance helped spread BadRabbit ransomware and is similar in many ways to EternalBlue, a second leaked NSA exploit which helped fuel WannaCry and NotPetya. Both exploits look for public-facing SMB ports, allowing them to deliver malware to networks.
Researchers discovered the malware was downloadable from a particular web address as a zip file, bundled with Pyinstaller, a program which packages programs written in Python into stand alone executables, meaning there's no need for Python to be installed on the compromised machine.
The malicious code behind PyRoMine appears to have been directly copied from a publicly shared EternalRomance implementation. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
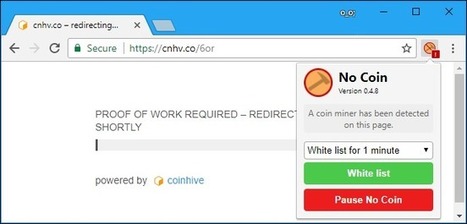
A cryptojacking attack hit thousands of websites, including government ones.
Surreptitious mining of cryptocurrency by hackers is spreading very, very fast.
The news: Over 4,000 websites, including those of the US federal judiciary and the UK National Health Service, have been weaponized by hackers to mine the cryptocurrency Monero on their behalf.
How it worked: Hackers injected malware into a widely used plug-in called Browsealoud that reads web pages our loud as a way of helping partially sighted people navigate the internet. The malware is based on the popular app Coinhive, a piece of software that uses processing power on someone’s device to mine cryptocurrency. The malicious version of the app does this without people's knowledge, coopting their computing power to enrich hackers.
Why it matters: Cryptojacking is rapidly becoming one of the world’s biggest cyberthreats. This news shows how easy it is for crooks to spread the trick, by infecting a single product used across multiples sites with a single hack.
Learn more / En savoir plus / mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Ransomware has caused little more than heartache and disruption for the enterprise and consumers alike, but it may soon lose its lucrative appeal in favor of cryptocurrency miners.
Over the last few years, ransomware, which targets systems, encrypts files, and demands a blackmail payment in return for a potential decryption key, has hit the spotlight time and time again.
The UK's National Health Service (NHS), major shipping companies, utilities, private businesses, and consumers at large have all fallen prey to variants including Petya, WannaCry, GoldenEye, and CryptoLocker.
This type of malware capitalizes on unpatched PCs, legacy operating systems, and vulnerabilities both old and new.
However, according to Cisco Talos researchers, cryptocurrency miners may soon take the top spot as a way for fraudsters to generate income. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
Zum heimlichen Krypto-Mining im Browser hat sich jüngst eine neue Masche gesellt: Kriminelle schleusen Open-Source-Mining-Tools auf fremde PCs, um dauerhaft von deren Rechenleistung zu profitieren. Millionen von Nutzern sollen betroffen sein.
Eine aktuelle Malware-Kampagne missbraucht das quelloffene Krypto-Mining-Tool XMRig, um auf fremden Rechnern die Kryptowährung Monero zu scheffeln. Sicherheitsforscher von Palo Alto Networks beobachten die auf Windows-Systeme abzielende Schadcode-Verbreitung bereits seit über vier Monaten. Ihren Auswertungen zufolge sollen weltweit mindestens 15 Millionen Rechner mit der Mining-Malware infiziert sein – über 6.5 Millionen davon stehen in Thailand, Vietnam und Ägypten.
Anders als frühere Kryptomining-Kampagnen, die auf JavaScript-Code im Browser setzen, nistet sich der Schadcode im aktuellen Fall dauerhaft auf den Rechnern ein – der Mining-Prozess ist damit zeitlich nicht mehr auf das Surfen im Internet beschränkt. Die Malware nutzt zwei Visual-Basic-Skripte (VBS), die zunächst ermitteln, ob es sich beim Betriebssystem des Zielrechners um eine 32- oder 64-Bit-Windows-Version handelt. Anschließend laden sie aus dem Internet die geeignete XMRig-Version nach, starten diese und beginnen mit dem heimlichen Mining. Die Erträge fließen in die digitalen Geldbeutel der Malware-Macher. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Crypto+Mining https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Another site in the booming cryptocurrency wallet sector has been hacked after what looks like a DNS hijacking attack.
The victim this time is BlackWallet, whose users reportedly lost 670,000 of a currency called Stellar Lumens (XLMs) worth around $425,000 at the point they were stolen on the afternoon of 13 January.
News that something was amiss first emerged in a Reddit posting claiming to be from the site’s admin:
BlackWallet was compromised today, after someone accessed my hosting provider account. I am sincerely sorry about this and hope that we will get the funds back.
A security researcher who took a look at blackwallet.co before it was taken down tweeted:
The DNS hijack of Blackwallet injected code, if you had over 20 Lumens it pushes them to a different wallet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
Cryptocurrency miners are a new scourge on the web. Web pages can now embed JavaScript code that runs in your web browser to mine themselves Bitcoin or other cryptocurrencies using your computer. The website keeps the cryptocurrency, and you get higher electric bills, 100% CPU usage that drags down your computer, and reduced battery life. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/ict-security-tools/?&tag=Coin+Miners
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
It took 24 hours to notice but on the 5th January 2019, Ethereum Classic (ETC), better known as Ethereum’s (ETH) little brother, was hacked using a rare 51% attack.
In essence, a single person was able to control around 60% of the mining power, creating a longer blockchain which gave them the ability to double spend. Something that was picked up by Coinbase and led to the index and others freezing Ethereum Classic from trading. Ethereum Classic is the 18th-largest cryptocurrency, according to CoinMarketCap.
Understandably people in the industry are worried, so I asked the experts whether more attacks are likely and if so, could a 51% attack hit the larger cryptocurrencies such as Bitcoin?
Not immutable anymore
Nir Kabessa, President of Blockchain at Columbia University, speculates that while difficult, attacks on the larger cryptocurrencies are no longer out of reach.
With both the hash power securing Ethereum Classic and the market cap of its token supply being less than 1/20th that of the Ethereum main chain, it’s not particularly surprising that Classic was successfully 51% attacked. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
Die in dieser Woche gepatchte Lücke im Bitcoin-Referenzclient Core ist offenbar noch gravierender als gedacht: So wären damit nicht nur Denial-of-Service-Attacken (DoS) gegen Bitcoin-Netzwerkknoten möglich, sondern auch eine Erzeugung von Bitcoins über die definierte Geldmenge von 21 Millionen Einheiten hinaus. Nutzer, die einen Netzwerkknoten mit Bitcoin Core betreiben, sollten also unbedingt auf die Version 0.16.3 updaten.
Die Lücke (CVE-2018-17144) wurde am Dienstag kurz nach Bekanntwerden gefixt, allerdings hielt die Entwickler-Community des Core-Clients das volle Ausmaß der Schwachstelle noch unter Verschluss. Lediglich die DoS-Anfälligkeit machte man publik, gleichzeitig wandten sich die Entwickler an Firmen, Mining-Pools und ähnliche wichtige Player des Netzwerks. Das sollte den großen Netzwerkteilnehmern Aufschub für schnell umgesetzte Updates verschaffen.
DoS und Double Spend möglich!! Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Bitcoin

|
Scooped by
Gust MEES
|
Monero-mining Android malware will exhaust your phone in its quest for cash.
A new strain of Android malware will continuously use an infected device's CPU to mine the Monero cryptocurrency until the device is exhausted or even breaks down.
Security company Trend Micro has named the malware HiddenMiner because of the techniques it uses to protect itself from discovery and removal.
Like most cryptocurrency-mining software, HiddenMiner uses the device's CPU power to mine Monero. But Trend Micro said that because there is no switch, controller, or optimizer in HiddenMiner's code it will continuously mine Monero until the device's resources are exhausted.
"Given HiddenMiner's nature, it could cause the affected device to overheat and potentially fail," the company said. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=Crypto+Mining https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Cyber thugs have been exploiting a zero-day flaw in the Telegram Messenger desktop app in order to mine for cryptocurrencies or to install a backdoor to remotely control victims’ computers.
Kaspersky Lab discovered “in the wild” attacks on Telegram Messenger’s Windows desktop client back in October 2017. The vulnerability in the popular Telegram app had been actively exploited since March 2017 to mine a variety of cryptocurrencies, such as Monero, Zcash, Fantomcoin and others. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Telegram

|
Scooped by
Gust MEES
|
Sicherheitsexperten von Proofpoint untersuchten das Mining-Botnet Smominru, das auf mehr als 500.000 Windows-Maschinen die Kryptowährung Minero schürft.
Nach Erkenntnissen von Sicherheitsexperten der Firma Proofpoint missbrauchen Kriminelle die Rechenleistung von mehr als einer halben Million Windows-Systemen, um die Kryptowährung Minero zu "schürfen". Laut Proofpoint handelt es sich bei den befallenen Maschinen vor allem um Windows-Server, von denen viele in Russland, Indien, Taiwan und der Ukraine laufen. Im Beobachtungszeitraum von Mai 2017 bis Januar 2018 hätten die Angreifer Mineros im Wert von rund 3,6 Millionen US-Dollar ergattert.
Server unbrauchbar
Auf den Stromkosten bleiben die Geschädigten sitzen, außerdem vermuten die Sicherheitsforscher, dass viele der befallenen Server wegen der zusätzlichen Rechenlast nur noch eingeschränkt funktionieren. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
As Ars Technica reports, YouTube has been spotted pushing ads onto users.
That, in itself, isn't newsworthy of course. But these ads are surreptitiously stealing resources from visiting computers to mine for cryptocurrencies:
On Friday, researchers with antivirus provider Trend Micro said the ads helped drive a more than three-fold spike in Web miner detections. They said the attackers behind the ads were abusing Google's DoubleClick ad platform to display them to YouTube visitors in select countries, including Japan, France, Taiwan, Italy, and Spain.
The ads contain JavaScript that mines the digital coin known as Monero. In nine out of 10 cases, the ads will use publicly available JavaScript provided by Coinhive, a cryptocurrency-mining service that's controversial because it allows subscribers to profit by surreptitiously using other people's computers. The remaining 10 percent of the time, the YouTube ads use private mining JavaScript that saves the attackers the 30 percent cut Coinhive takes. Both scripts are programmed to consume 80 percent of a visitor's CPU, leaving just barely enough resources for it to function.
You should run an ad blocker when you surf the web.
================================================== Not just because ads are invariably ugly and ruin the user experience. Not just because you don't want ads tracking your online behaviour. Not just because ads slow down your online experience and gobble up your bandwidth. Not just because ads can infect your computer with malware, or be secretly sapping your computer resources by mining for cryptocurrencies in the background. ==================================================
But because even Google, one of the world's largest advertising companies (with its own considerable security prowess), seems to be incapable of guaranteeing a stream of safe ads. What hope for the other advertising networks if Google can't get it right? Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
TOKYO (Reuters) - Coincheck, a major cryptocurrency trading exchange in Tokyo, has been hacked into and has lost about 58 billion yen ($534 million) worth of virtual money, national broadcaster NHK reported on Friday. Coincheck posted on its website on Friday afternoon that it had suspended withdrawals of almost all cryptocurrencies. The exchange has already reported the incident to the police and to Japan’s Financial Services Agency, NHK said. In 2014, Tokyo-based Mt. Gox, which once handled 80 percent of the world’s bitcoin trades, filed for bankruptcy after losing some 850,000 bitcoins - then worth around half a billion U.S. dollars - and $28 million in cash from its bank accounts. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
Stealth cryptocurrency mining in one’s browser, without the user’s permission, is one of our least-favorite trends of the past six months. While there were always questions about whether cryptocurrency mining in-browser could serve as an alternate revenue stream for websites, there was at least an idea that some kind of alternate funding system might emerge — hopefully putting an end to the eternal cycle of invasive ads driving users to deploy ad blockers, which then drives websites to adopt more invasive ads.
But instead of an informed approach in which end users consented to such mining, we’ve seen stealth operations popping up everywhere that steal CPU cycles from users, particularly if more than one crypto mining malware is running simultaneously. While most of these plugins are written to only put a light load on user’s CPUs, that’s only if the miner is running in a single browser instance, and only if it’s running on a single site. Our tests back in 2017 showed that using different browsers can defeat this dubious attempt to sandbox the performance impact. And, of course, even running one site will still drain battery life more quickly than having the CPU properly idled.
It’s like someone figured out how to monetize the awful Flash ads everyone used to hate for eating CPU cycles. A true win-win! And now it’s even hitting YouTube.
TrendMicro has released an updated report, showing a sharp rise in ads served by Google’s DoubleClick service being infested with mining software. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...




























Scam artists have taken advantage of a contract migration initiative to swindle NFTs out of users in an opportunistic phishing attack.
Last week, NFT marketplace OpenSea announced the rollout of contract migrations and an upgrade to make sure inactive, old NFT listings on Ethereum expire safely and to allow OpenSea to "offer new safety features in the future."
The contract migration timeline was set from February 18 to February 25.
NFT holders are required to make the change, and OpenSea published a guide to assist them. After the deadline, any listings that were not migrated would expire, although they could be re-listed after this window without further fees.
However, an attacker saw an opportunity to cash in. Check Point Research has suggested that phishing emails were sent to users, linking them to fraudulent websites.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=blockchain
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=WEB3
https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency