 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Twitter has confirmed a recent data breach was caused by a now-patched zero-day vulnerability used to link email addresses and phone numbers to users' accounts, allowing a threat actor to compile a list of 5.4 million user account profiles.
Last month, BleepingComputer spoke to a threat actor who said that they were able to create a list of 5.4 million Twitter account profiles using a vulnerability on the social media site.
This vulnerability allowed anyone to submit an email address or phone number, verify if it was associated with a Twitter account, and retrieve the associated account ID. The threat actor then used this ID to scrape the public information for the account. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Two-factor+authentication https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Twitter

|
Scooped by
Gust MEES
|
A security researcher has published proof-of-concept (PoC) code for a vulnerability in the KDE software framework. A fix is not available at the time of writing.
The bug was discovered by Dominik "zer0pwn" Penner and impacts the KDE Frameworks package 5.60.0 and below.
The KDE Frameworks software library is at the base of the KDE desktop environment v4 and v5 (Plasma), currently included with several Linux distributions such as Kubuntu, openSUSE, OpenMandriva, Chakra, KaOS, and others.
HOW THE VULNERABILITY WORKS
The vulnerability occurs because of the way the KDesktopFile class (part of KDE Frameworks) handles .desktop or .directory files.
Penner discovered that he could create malicious .desktop and .directory files that could be used to run malicious code on a user's computer.
When a user opens the KDE file viewer to access the directory where these files are stored, the malicious code contained within the .desktop or .directory files executes without user interaction -- such as running the file. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
A little-known data firm was able to build 48 million personal profiles, combining data from sites and social networks like Facebook, LinkedIn, Twitter, and Zillow, among others -- without the users' knowledge or consent.
Localblox, a Bellevue, Wash.-based firm, says it "automatically crawls, discovers, extracts, indexes, maps and augments data in a variety of formats from the web and from exchange networks." Since its founding in 2010, the company has focused its collection on publicly accessible data sources, like social networks Facebook, Twitter, and LinkedIn, and real estate site Zillow to name a few, to produce profiles.
But earlier this year, the company left a massive store of profile data on a public but unlisted Amazon S3 storage bucket without a password, allowing anyone to download its contents.
The bucket, labeled "lbdumps," contained a file that unpacked to a single file over 1.2 terabytes in size. The file listed 48 million individual records, scraped from public profiles, consolidated, then stitched together. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/
Twitter’s been combatting harassment for years. The latest effort: quelling its horde of anonymous, hostile egg accounts. But for many users, Twitter’s abuse problem has long since undermined its value as a platform for creative communication. That’s what makes Mastodon—a free, open-source, and increasingly popular six-month-old Twitter alternative—so intriguing.
Mastodon has created a diverse yet welcoming online environment by doing exactly what Twitter won’t: letting its community make the rules. The platform consists of various user-created networks, called instances, each of which determines its own laws. One instance could ban sexist jokes and Nazi logos, while another might practice radically free speech. (In this way, Mastodon is not unlike a network of discretely moderated message boards crossed with a Tweetdeck-like interface.) Users choose for themselves which instance they want to join and select from a host of privacy and anti-harassment settings. Oh, and the character limit is 500, not 140. In essence, Mastodon is an experiment in whether individually moderated communities can make a social network like Twitter more civil. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/social-media-and-its-influence/?&tag=Mastodon

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Forscher von Eset weisen auf ein Android-Botnetz hin, das nicht von einem Kommandoserver, sondern über Twitter gesteuert wird. Diese von PC-Schädlingen seit mindestens 2009 bekannte Verfahren wird damit nach ihrer Einschätzung erstmals für einen Android-Trojaner verwendet.
Aufgrund des für die Koordination verwendeten Kommunikationskanals haben die Forscher den Trojaner Twitoor getauft. Ist er einmal installiert, fragt er regelmäßig ein spezielles Twitter-Konto ab, um eventuelle Befehle zu empfangen. Die Hintermänner können den Trojaner so beispielsweise anweisen, weitere bösartige Anwendungen zu installieren (in der Praxis bisher vor allem solche, die Bankdaten stehlen) oder auch, den Twitter-Kanal zu wechseln.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Android http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnets http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Botnet

|
Scooped by
Gust MEES
|
. . On Monday, June 9th there will be #cyberSAFEchat who will explore the security risks SMBs face during every phase of growth and learn how to best protect against these threats. The hour-long Twitter chat will address the following key questions: - Q1: What security risks do SMBs need to consider when starting a business and why?
- Q2: How do these risks change as the business grows and why?
- Q3: How can lapses in security impact a SMB?
- Q4: What tools and tips would you recommend that SMBs use to secure themselves, their employees and their customers?
...

|
Scooped by
Gust MEES
|
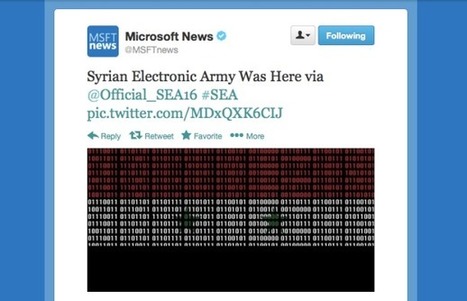
News spread that the hacking group got into the Microsoft News Twitter account, but apparently it also breached Xbox's Twitter and Instagram accounts. Read this article by Dara Kerr on CNET News.
As a result of the growing NSA revelations, the social microblogging site is upping its defenses by planning to encrypt its direct messaging Service.
Via Gust MEES

|
Scooped by
Gust MEES
|
A Reuters news service Twitter account appeared to have been hacked Monday, as the news organization suddenly began tweeting messages supportive of the Syrian president.

|
Scooped by
Gust MEES
|
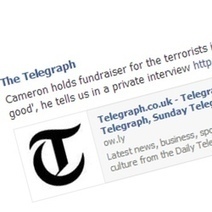
The Telegraph is hacked on Facebook and Twitter by the Syrian Electronic Army.

|
Scooped by
Gust MEES
|
The Syrian Electronic Army struck again over the weekend, hitting another media organization's Twitter account. The latest attack appears to be in retaliation against Twitter for suspending its account.
Symantec helps consumers and organizations secure and manage their information-driven world. The ISTR, which covers the major threat trends observed by Symantec in 2012, reveals that cybercriminals view SMBs as a prime target for stealing information. In fact, the largest growth area for targeted attacks in 2012 was businesses with fewer than 250 employees; 31 percent of all attacks targeted them, representing a threefold increase from 2011. Getting a clear understanding of the dangers is an important step in improving security, and this year’s report is a wake-up call that SMBs are now being specifically targeted by cybercriminals. ===> Mark your calendars to join #SMBchat and learn how to protect your small business from attackers. <===
|

|
Scooped by
Gust MEES
|
In a statement published today, Twitter disclosed a security incident during which third-parties exploited the company's official API (Application Programming Interface) to match phone numbers with Twitter usernames.
In an email seeking clarifications about the incident, Twitter told ZDNet that they became aware of exploitation attempts against this API feature on December 24, 2019, following a report from tech news site TechCrunch. The report detailed the efforts of a security researcher who abused a Twitter API feature to match 17 million phone numbers to public usernames.
Twitter says that following this report it intervened and immediately suspended a large network of fake accounts that had been used to query its API and match phone numbers to Twitter usernames. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Two-factor+authentication https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Twitter

|
Scooped by
Gust MEES
|
Twitter has admitted that user passwords were briefly stored in plaintext and may have been exposed to the company's internal tools.
In a blog post, the microblogging site urged users to change their passwords.
"When you set a password for your Twitter account, we use technology that masks it so no one at the company can see it. We recently identified a bug that stored passwords unmasked in an internal log," said Twitter in a statement.
Twitter didn't say how many accounts were affected, but Reuters reports -- citing a source -- that the number of affected users was "substantial" and that passwords were exposed for "several months."
It's unclear exactly why user passwords were stored in plaintext before they were hashed. Twitter said that it stores user passwords with bcrypt, a stronger password hashing algorithm, but a bug meant that passwords were "written to an internal log before completing the hashing process."
The company said it fixed the bug and that an investigation "shows no indication of breach or misuse" by anyone.
A spokesperson for Twitter reiterated that the bug "is related to our internal systems only," but it did not comment further.
"Since this is not a breach and our investigation has shown no signs of misuse, we are not forcing a password reset but are presenting the information for people to make an informed decision about their account," said the spokesperson. "We believe this is the right thing to do."
The company had 330 million users at its fourth-quarter earnings in February.
Read also: Twitter hopes trolls can be stopped by eradicating ignorance
Twitter is the second company to admit a password-related bug this week.
GitHub on Tuesday said it also exposed some users' plaintext passwords after they were written to an internal logging system.
It's not known if the two incidents are related, and a Twitter spokesperson would not comment in a follow-up email. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet?page=2&tag=Passwords https://www.scoop.it/t/securite-pc-et-internet/?&tag=Password+Managers https://www.scoop.it/t/securite-pc-et-internet/?&tag=Twitter

|
Scooped by
Gust MEES
|
A new social media network named Mastodon popped up a few months ago and is designed to deliver a decentralised, open-source experience, but its this unique structure that may make its members vulnerable to cyber-attacks.
Malwarebyte's researcher Zammis Clark blogged that the decentralised nature of the site's construction, which he said helps eliminate ads, a primary selling point for users, also leaves the social network open to hackers. The site is very different from Facebook, Twitter and other networks.
Instead of being hosted by a corporate entity on its server system Mastodon members can set up their own server if they wish, called in “instance” by the Mastodon community, and then have people join Mastodon through that server. But here is where the problem arises.
Each person's “instance” receives a special domain name, for example mastodon.instance1, and anyone registering on that instance would receive a username like johnsmith.mastodon.instance1.
Where things go awry, Clark said, is the usernames can be replicated across all the "instances", so on mastodon.instance2 there could be a johnsmith.mastodon.instance2. This creates a situation where there are no verified accounts.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Über das Unternehmen Geofeedia konnten US-Behörden Standortdaten von Facebook- und Twitter-Nutzern sammeln.
Facebook, Instagram und Twitter kennen viele Details ihrer Nutzer. Dies hat offenbar auch die US-Regierung erkannt und die Datenströme der Dienste über die Analytics-Plattform Geofeedia angezapft . Laut der Bürgerrechtsorganisation American Civil Liberties Union (ACLU) nutzte unter anderem die Polizei diese Informationen, um die Rassenproteste in Oakland und Baltimore zu überwachen.
Die Sammlung der Daten wurde von dem in Chicago ansässigen Unternehmen Geofeedia übernommen, das die Informationen dann an rund 500 Strafverfolgungs- und Sicherheitsbehörden weitergereicht haben soll. Neben persönlichen Informationen wurden auch Standortdaten von Nutzern gesammelt.
Facebook und Twitter beteuern, dass es sich bei dem abgegriffenen Daten um öffentlich zugängliche Informationen handeln würde. Als Reaktion auf die Vorwürfe schränkten beide Unternehmen den Zugriff von Geofeedia auf die Datenströme der sozialen Netzwerke ein oder sperrten den Anbieter sogar. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ http://www.scoop.it/t/securite-pc-et-internet/?tag=Privacy

|
Scooped by
Gust MEES
|
Twitter has notified 10,000 users that their email address and phone number might have been exposed due to a bug in the website's password recovery feature.

|
Scooped by
Gust MEES
|
CSID's #cyberSAFEchat on June 9th will explore security risks SMBs face during every phase of growth and how to protect against threats.
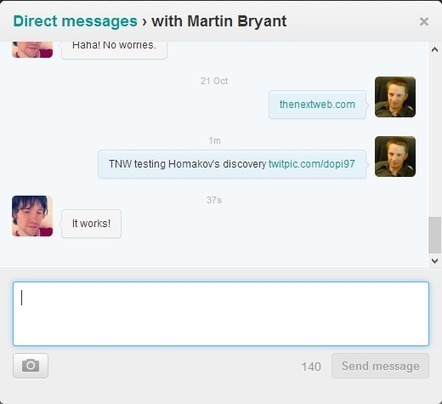
Security researcher Egor Homakov has discovered a Twitter vulnerability which allows apps to send DMs without requiring explicit user permission. TNW has verified the findings and can ...
Via Gust MEES

|
Scooped by
Gust MEES
|
So how come Thomson Reuters wasn't using Twitter two-factor authentication?
Chances are that's because it's just not a good security solution for most media organisations using social media.

|
Scooped by
Gust MEES
|
Earlier, we posted about Twitter's new tailored advertising announcement. We applauded Twitter's commitment to privacy by allowing two opt-out mechanisms—both an internal setting and your browser's Do Not Track capability. To make things easier for you, here's a guide to opt out of Twitter's tailored advertisements and how best to protect yourself from online tracking. Opting out of Twitter's tailored advertisements
The microblogging giant has warned news outlets that "these attacks will continue," particularly against high profile media organizations.
Via Gust MEES
After a widely publicised hack or data breach, you'll often find "password check" sites springing up.
Some of them are legitimate, but other password check sites are as bogus as they sound on th... Short, sweet, and clear. - Don't click login links in emails. - Check the address bar. - And watch out for the HTTPS (secure HTTP) padlock in the address bar whenever you are entering PII of any sort, from passwords to account numbers.
Via Gust MEES
|



 Your new post is loading...
Your new post is loading...




























Twitter has confirmed a recent data breach was caused by a now-patched zero-day vulnerability used to link email addresses and phone numbers to users' accounts, allowing a threat actor to compile a list of 5.4 million user account profiles.
Last month, BleepingComputer spoke to a threat actor who said that they were able to create a list of 5.4 million Twitter account profiles using a vulnerability on the social media site.
This vulnerability allowed anyone to submit an email address or phone number, verify if it was associated with a Twitter account, and retrieve the associated account ID. The threat actor then used this ID to scrape the public information for the account.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Two-factor+authentication
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Twitter