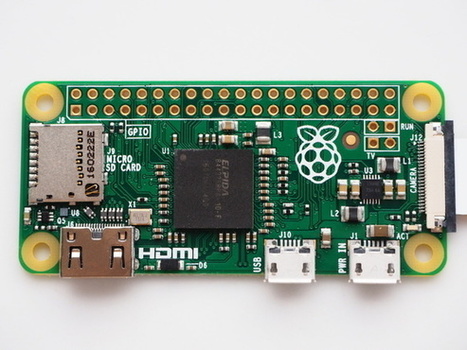
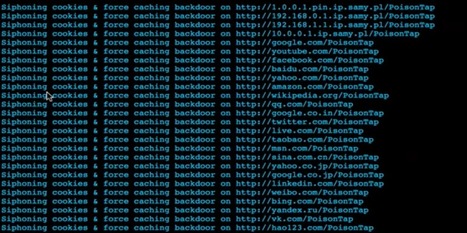
A proof of concept from security researcher and software developer Samy Kamkar shows that macOS, Windows, and Linux computers can have any previously active Web logins hijacked merely by plugging in a tiny Unix device via USB or Thunderbolt, even if the computer is locked and password protected, and possibly even when it seems to be asleep. It can also hijack many router brands on the same network.
PoisonTap exploits several interlocked network and browser design features, rather than relying on an operating system, hardware, or browser flaw. This will make it harder to root out and resolve. Kamkar said in an interview, “The interesting attacks to me are by design: how do you exploit the protocol rather than a single buffer overflow that gets patched the next day.”
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Samy+KAMKAR
http://www.scoop.it/t/securite-pc-et-internet/?tag=Raspberry+PI



 Your new post is loading...
Your new post is loading...







Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Samy+KAMKAR
http://www.scoop.it/t/securite-pc-et-internet/?tag=Raspberry+PI