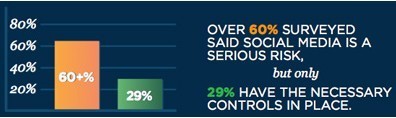
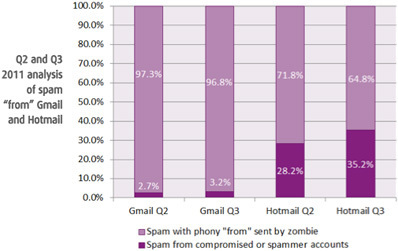
63 percent of more than 4,000 respondents in a new Ponemon Institute survey said that social media in the workplace represents a serious security risk — yet only 29 percent report having the necessary security controls in place to mitigate it.
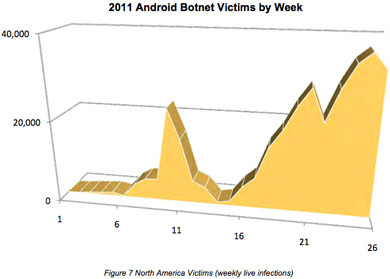
More than 50 percent of respondents report an increase in malware due to social media use.



 Your new post is loading...
Your new post is loading...